「Hiding data in GPU VRAM using Direct3D 11」 / X
http://x.com/i/article/1889093049193795584
Juniper Session Smart Routers Vulnerability Could Let Attackers Bypass Authentication
https://thehackernews.com/2025/02/juniper-session-smart-routers.html
Making a Powershell Shellcode Downloader that Evades Defender (Without Amsi Bypass) | by lainkusanagi | Medium
https://medium.com/@luisgerardomoret_69654/making-a-powershell-shellcode-downloader-that-evades-defender-without-amsi-bypass-d2cf13f18409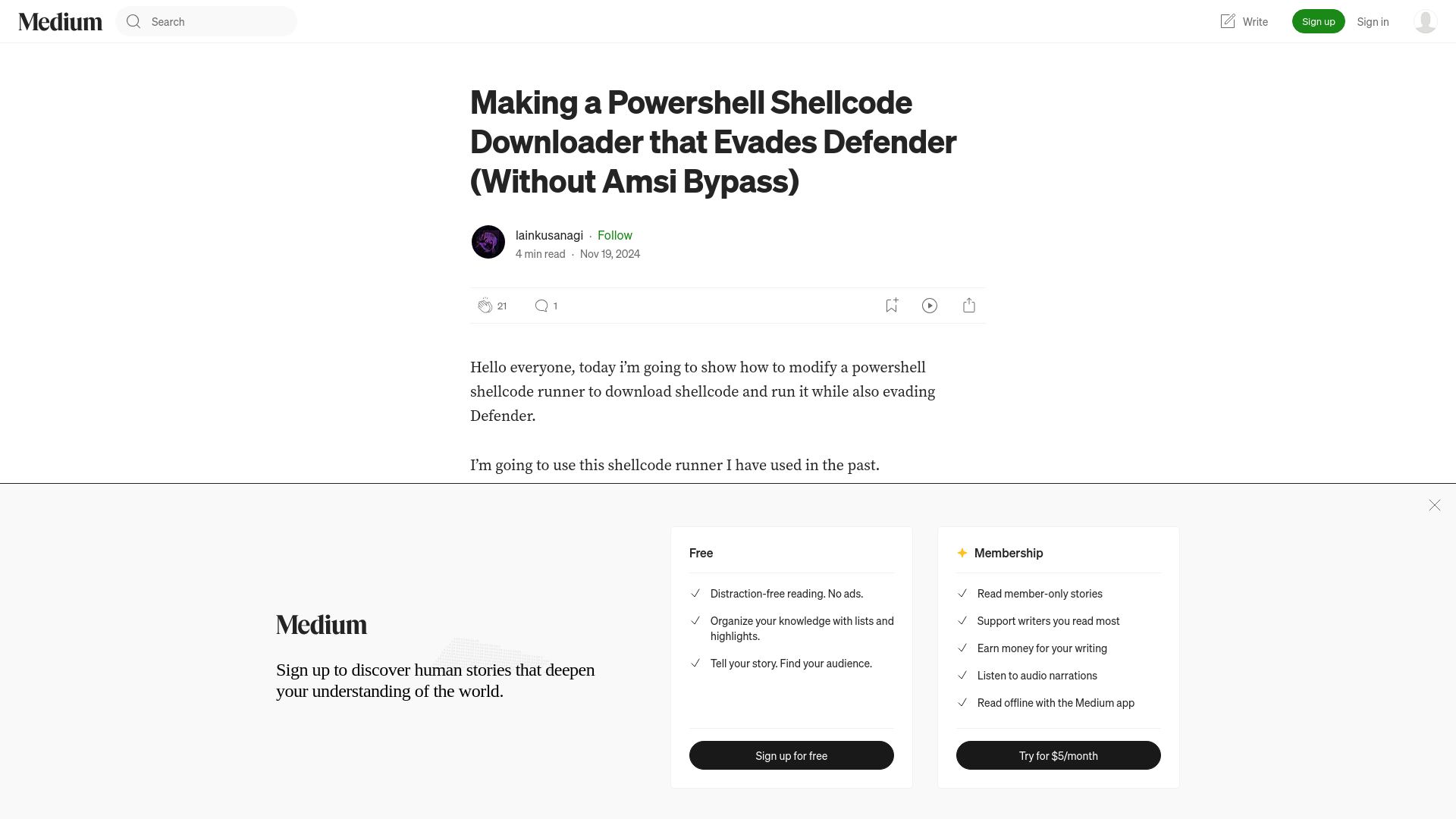
Chinese Hackers Exploit MAVInject.exe to Evade Detection in Targeted Cyber Attacks
https://thehackernews.com/2025/02/chinese-hackers-exploit-mavinjectexe-to.html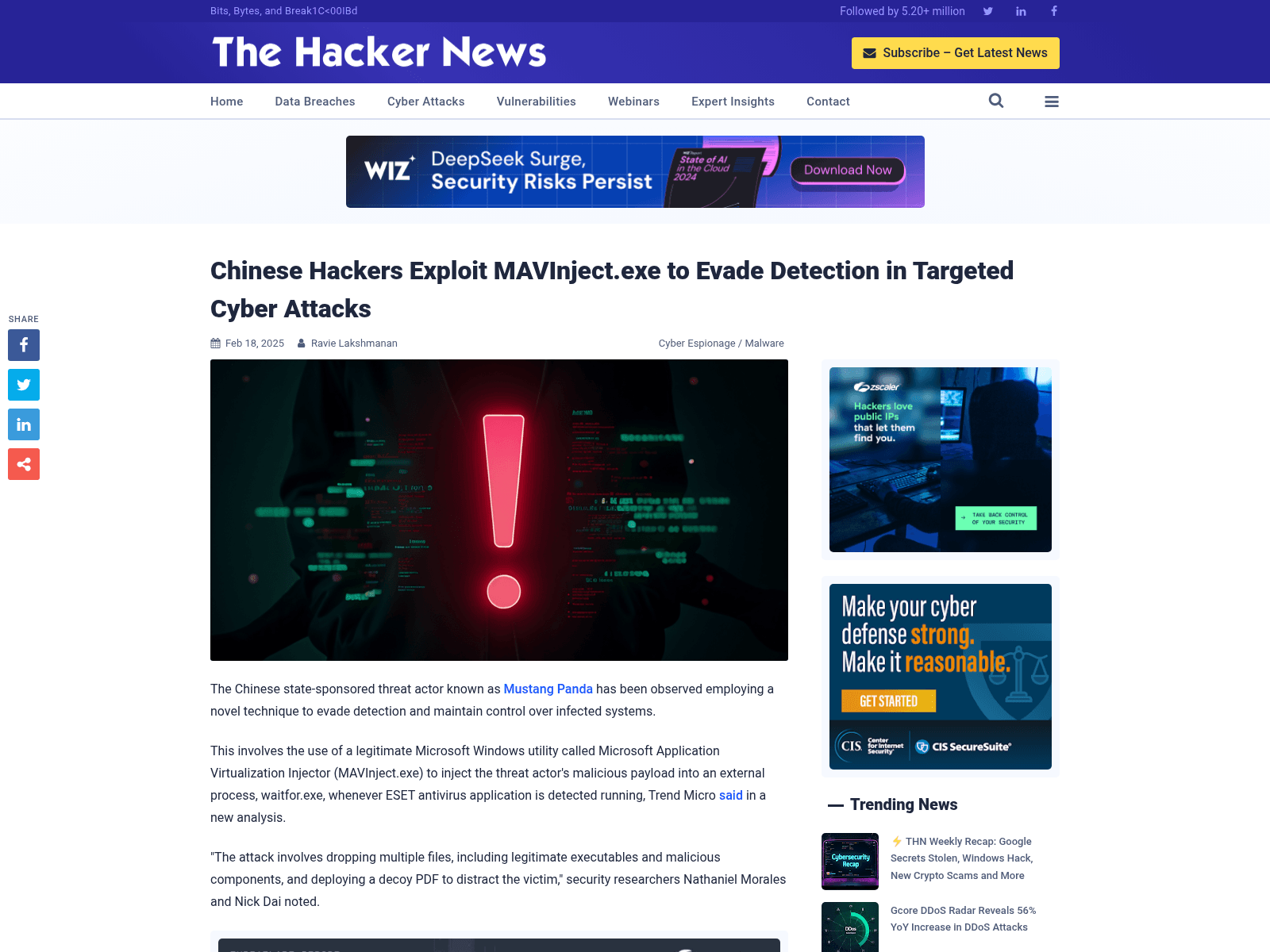
Cybercriminals Exploit Onerror Event in Image Tags to Deploy Payment Skimmers
https://thehackernews.com/2025/02/cybercriminals-exploit-onerror-event-in.html
New Xerox Printer Flaws Could Let Attackers Capture Windows Active Directory Credentials
https://thehackernews.com/2025/02/new-xerox-printer-flaws-could-let.html
China-linked APT group Winnti targets Japanese organizations
https://securityaffairs.com/174353/apt/china-linked-apt-group-winnti-targets-japanese-orgs.html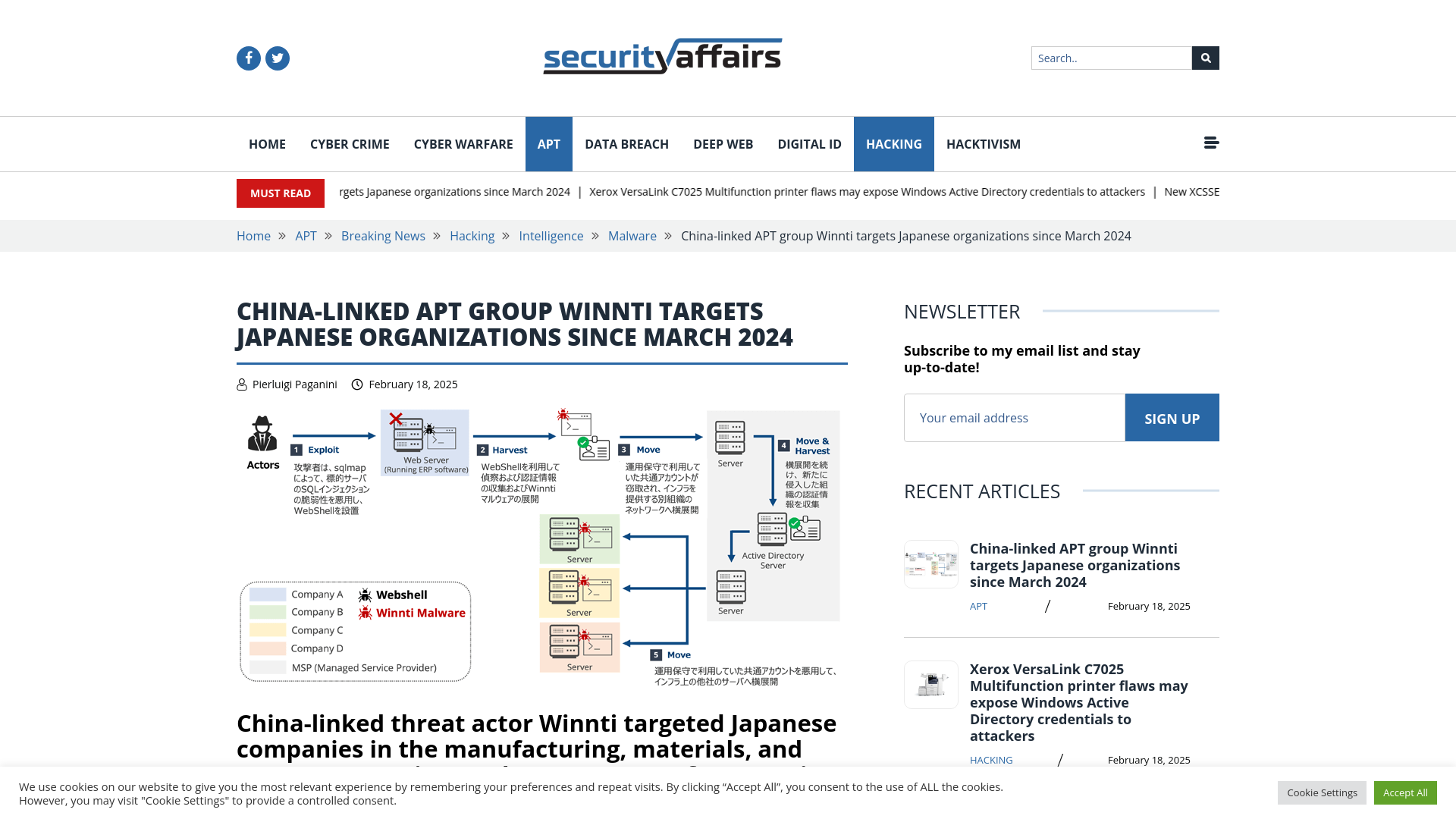
Grok3 Launch / X
https://x.com/i/broadcasts/1gqGvjeBljOGB
Winnti APT41 Targets Japanese Firms in RevivalStone Cyber Espionage Campaign
https://thehackernews.com/2025/02/winnti-apt41-targets-japanese-firms-in.html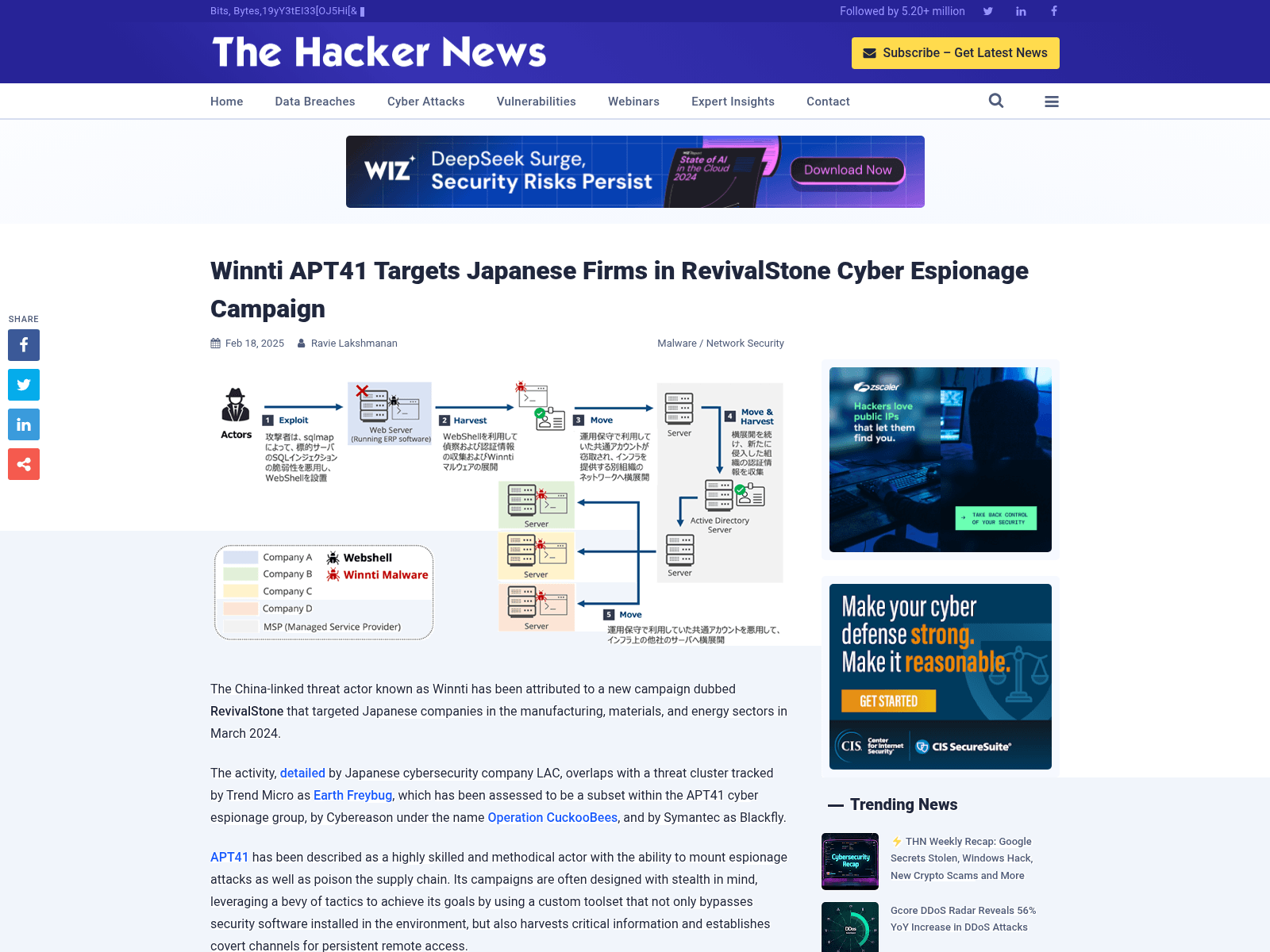
New FrigidStealer Malware Targets macOS Users via Fake Browser Updates
https://thehackernews.com/2025/02/new-frigidstealer-malware-targets-macos.html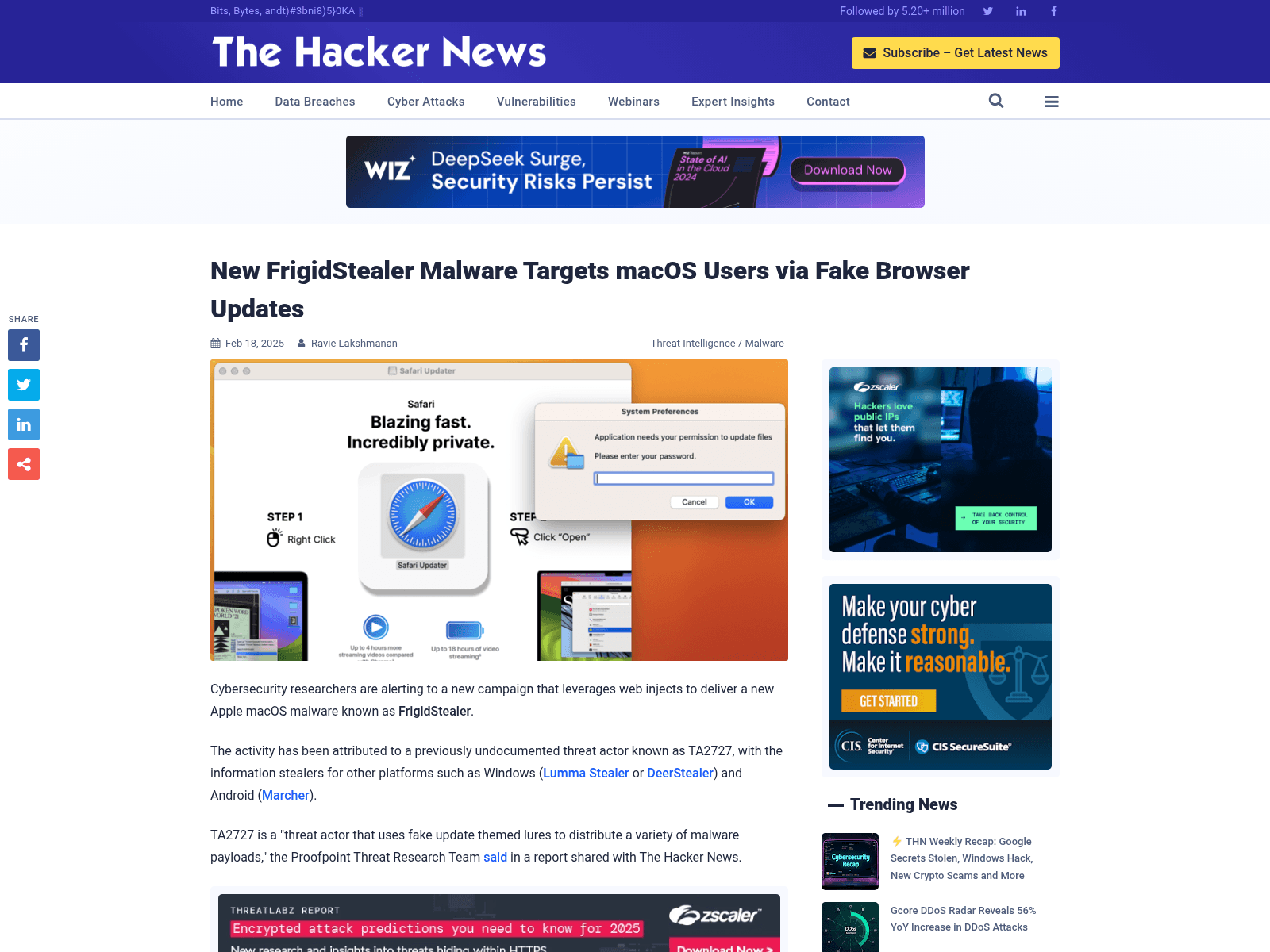
Lee Enterprises newspaper disruptions caused by ransomware attack
https://www.bleepingcomputer.com/news/security/lee-enterprises-newspaper-disruptions-caused-by-ransomware-attack/
Stealth Attack: EarthKapre Leverages Cloud and DLL Sideloading for Data Exfiltration
https://securityonline.info/stealth-attack-earthkapre-leverages-cloud-and-dll-sideloading-for-data-exfiltration/
MalwareBazaar | CVE-2025-0282
https://bazaar.abuse.ch/browse/tag/CVE-2025-0282/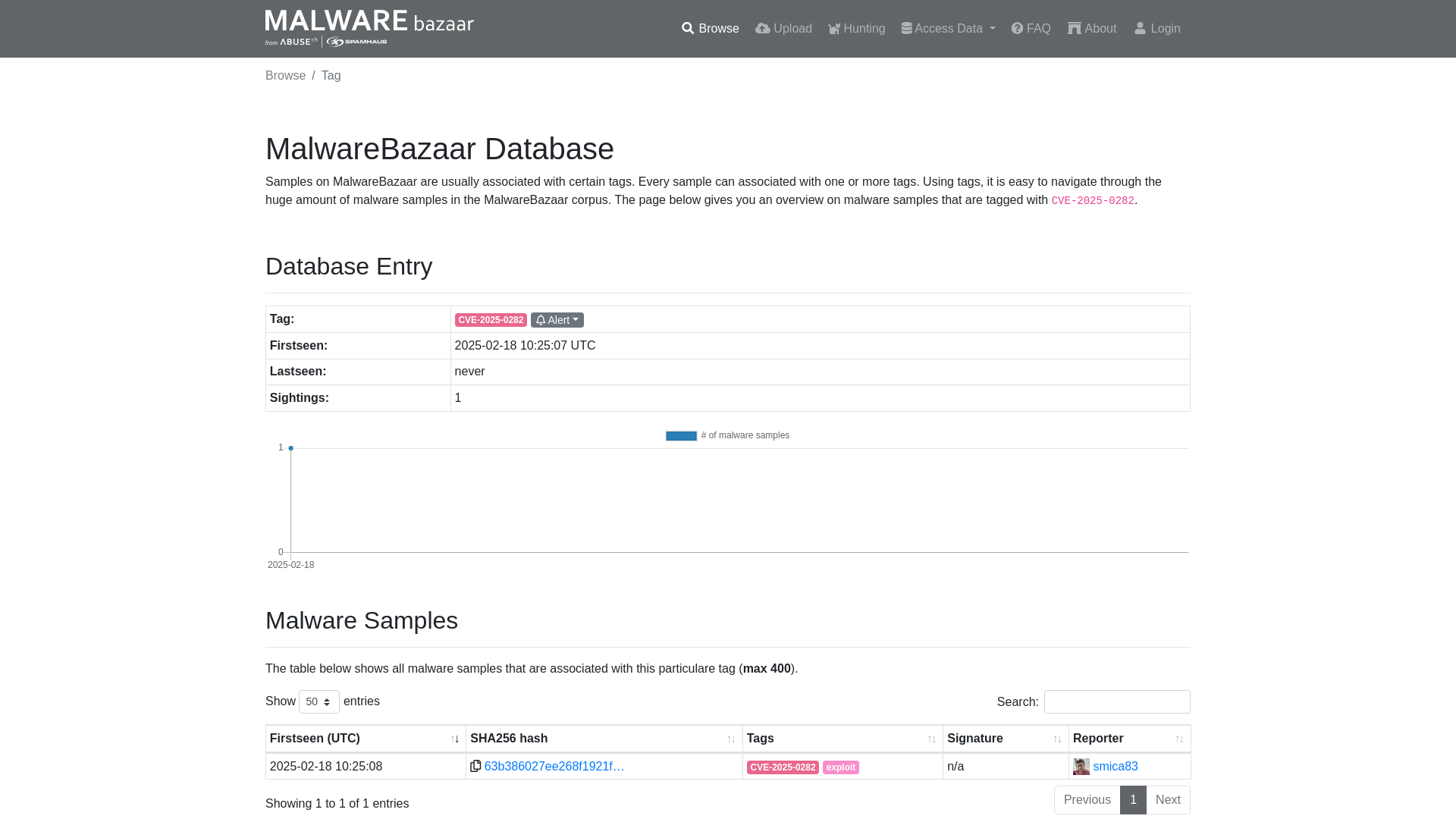
Palo Alto Networks Confirms Exploitation of Firewall Vulnerability - SecurityWeek
https://www.securityweek.com/palo-alto-networks-confirms-exploitation-of-firewall-vulnerability/
VirusTotal - File - cc31bd52386d956ed8cdcadda2ad16a21d0a9a177722465b94c8960092139e08
https://www.virustotal.com/gui/file/cc31bd52386d956ed8cdcadda2ad16a21d0a9a177722465b94c8960092139e08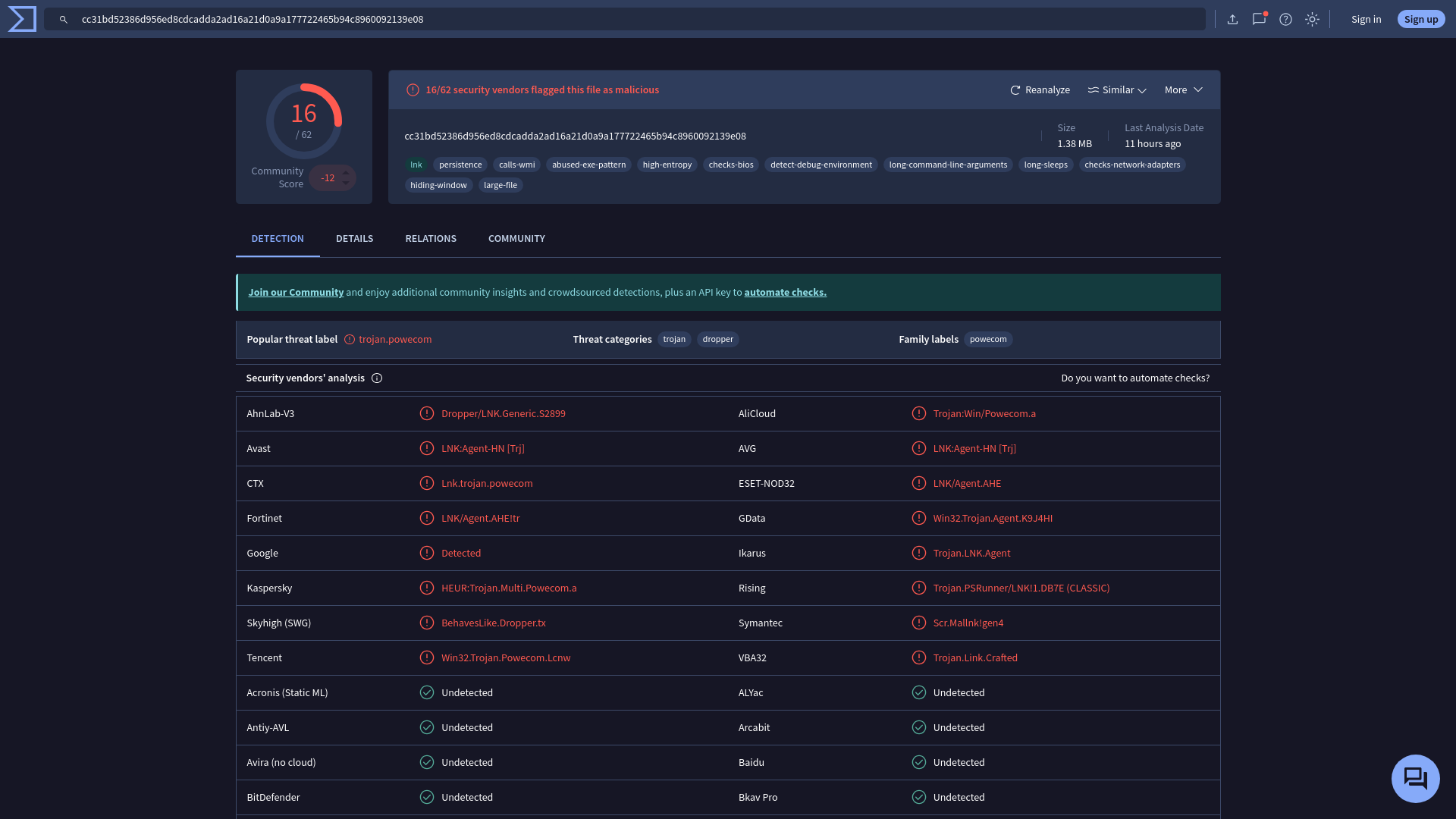
Earth Preta Mixes Legitimate and Malicious Components to Sidestep Detection | Trend Micro (US)
https://www.trendmicro.com/en_us/research/25/b/earth-preta-mixes-legitimate-and-malicious-components-to-sidestep-detection.html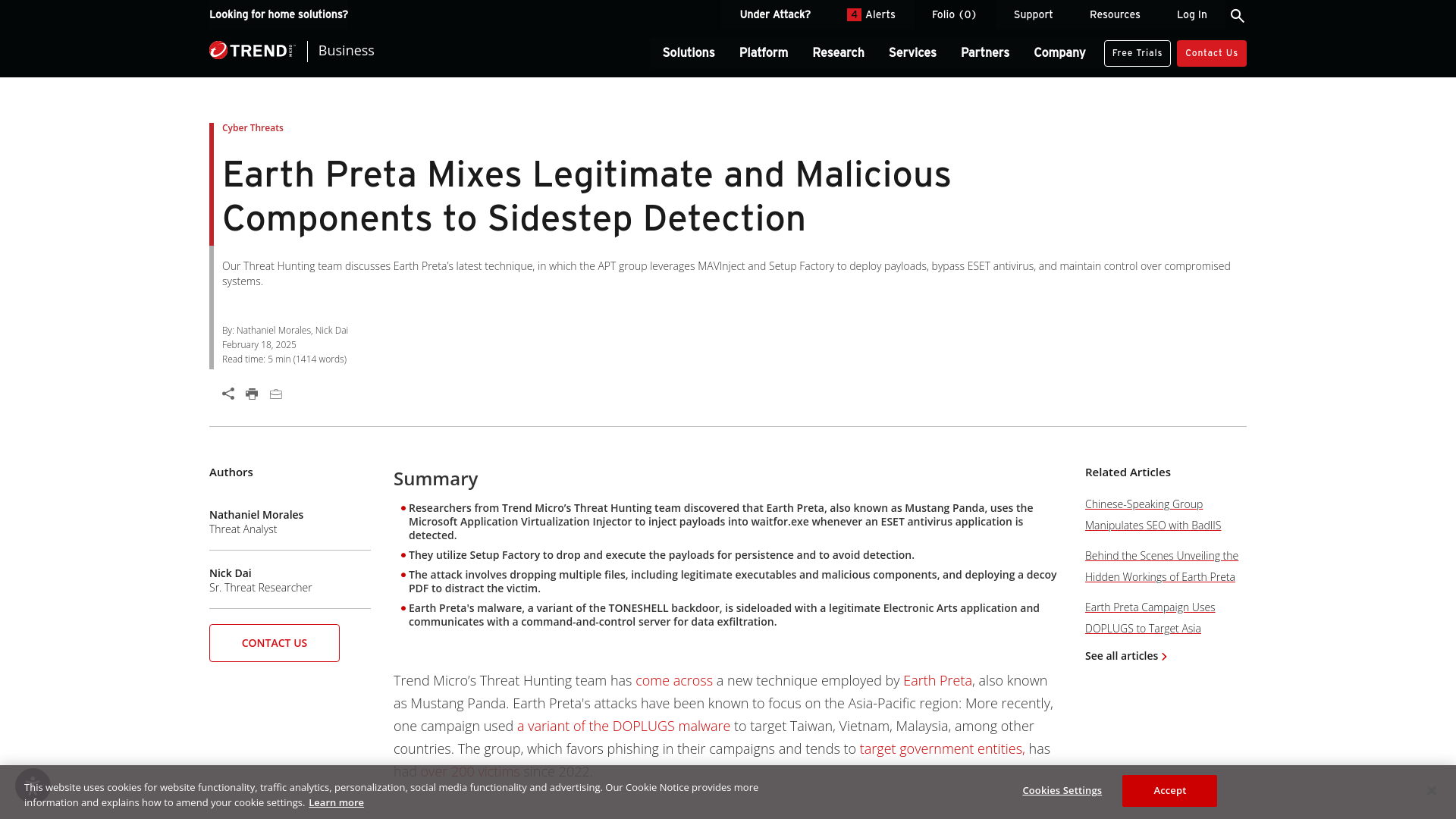
New OpenSSH flaws expose SSH servers to MiTM and DoS attacks
https://www.bleepingcomputer.com/news/security/new-openssh-flaws-expose-ssh-servers-to-mitm-and-dos-attacks/
Making a Mimikatz BOF for Sliver C2 that Evades Defender | by lainkusanagi | Feb, 2025 | Medium
https://medium.com/@luisgerardomoret_69654/making-a-mimikatz-bof-for-sliver-c2-that-evades-defender-fa67b4ea471d
MalwareBazaar | SHA256 95e45d55e2fc6dd48acddaeed3da271d42f1422fa49f13feeb42016a1a69816e (Formbook)
https://bazaar.abuse.ch/sample/95e45d55e2fc6dd48acddaeed3da271d42f1422fa49f13feeb42016a1a69816e/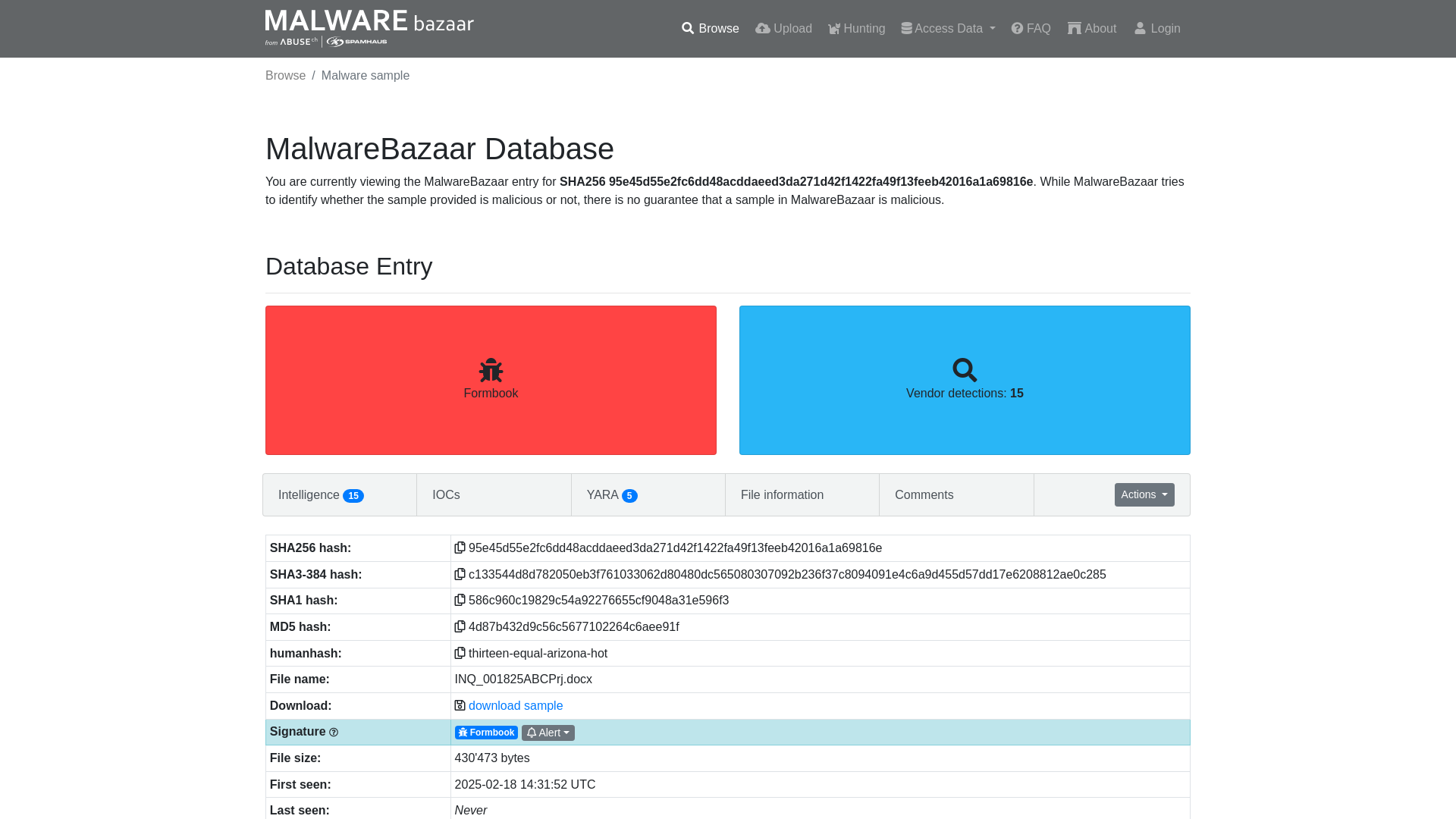
New OpenSSH Flaws Enable Man-in-the-Middle and DoS Attacks — Patch Now
https://thehackernews.com/2025/02/new-openssh-flaws-enable-man-in-middle.html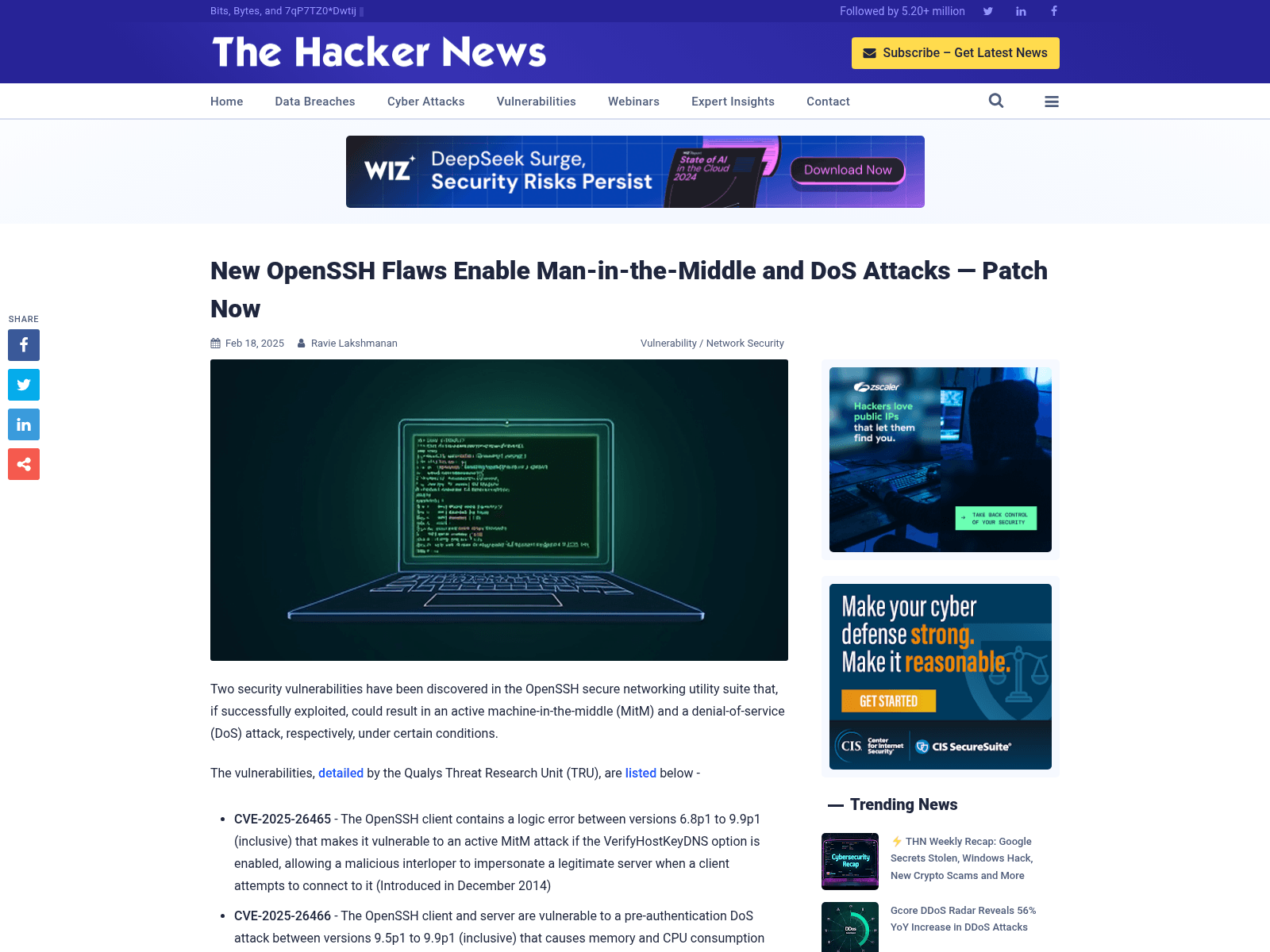
Log in to X / X
https://x.com/deepthivsn
Chinese hackers abuse Microsoft APP-v tool to evade antivirus
https://www.bleepingcomputer.com/news/security/chinese-hackers-abuse-microsoft-app-v-tool-to-evade-antivirus/