First analysis of Apple's USB Restricted Mode bypass (CVE-2025-24200) - Quarkslab's blog
https://blog.quarkslab.com/first-analysis-of-apples-usb-restricted-mode-bypass-cve-2025-24200.html
Google Chrome's AI-powered security feature rolls out to everyone
https://www.bleepingcomputer.com/news/google/google-chromes-ai-powered-security-feature-rolls-out-to-everyone/
Microsoft rolls out BIOS update that fixes ASUS blue screen issues
https://www.bleepingcomputer.com/news/microsoft/microsoft-rolls-out-bios-update-that-fixes-asus-blue-screen-issues/
X now blocks Signal contact links, flags them as malicious
https://www.bleepingcomputer.com/news/security/x-now-blocks-signal-contact-links-flags-them-as-malicious/
The art of fuzzing: Windows Binaries - Bushido Security
https://bushido-sec.com/index.php/2023/06/25/the-art-of-fuzzing-windows-binaries/
New FinalDraft malware abuses Outlook mail service for stealthy comms
https://www.bleepingcomputer.com/news/security/new-finaldraft-malware-abuses-outlook-mail-service-for-stealthy-comms/
Microsoft Uncovers New XCSSET macOS Malware Variant with Advanced Obfuscation Tactics
https://thehackernews.com/2025/02/microsoft-uncovers-new-xcsset-macos.html
GitHub - Network-Sec/CVE-2025-21420-PoC: We found a way to DLL sideload with cleanmgr.exe
https://github.com/Network-Sec/CVE-2025-21420-PoC
Fintech giant Finastra notifies victims of October data breach
https://www.bleepingcomputer.com/news/security/fintech-giant-finastra-notifies-victims-of-october-data-breach/
Making a Mimikatz BOF for Sliver C2 that Evades Defender | by lainkusanagi | Feb, 2025 | Medium
https://medium.com/@luisgerardomoret_69654/making-a-mimikatz-bof-for-sliver-c2-that-evades-defender-fa67b4ea471d
⚡ THN Weekly Recap: Google Secrets Stolen, Windows Hack, New Crypto Scams and More
https://thehackernews.com/2025/02/thn-weekly-recap-google-secrets-stolen.html
macOS Extended Attributes: Case Study | dfir.ch
https://dfir.ch/posts/macos_extended_attributes/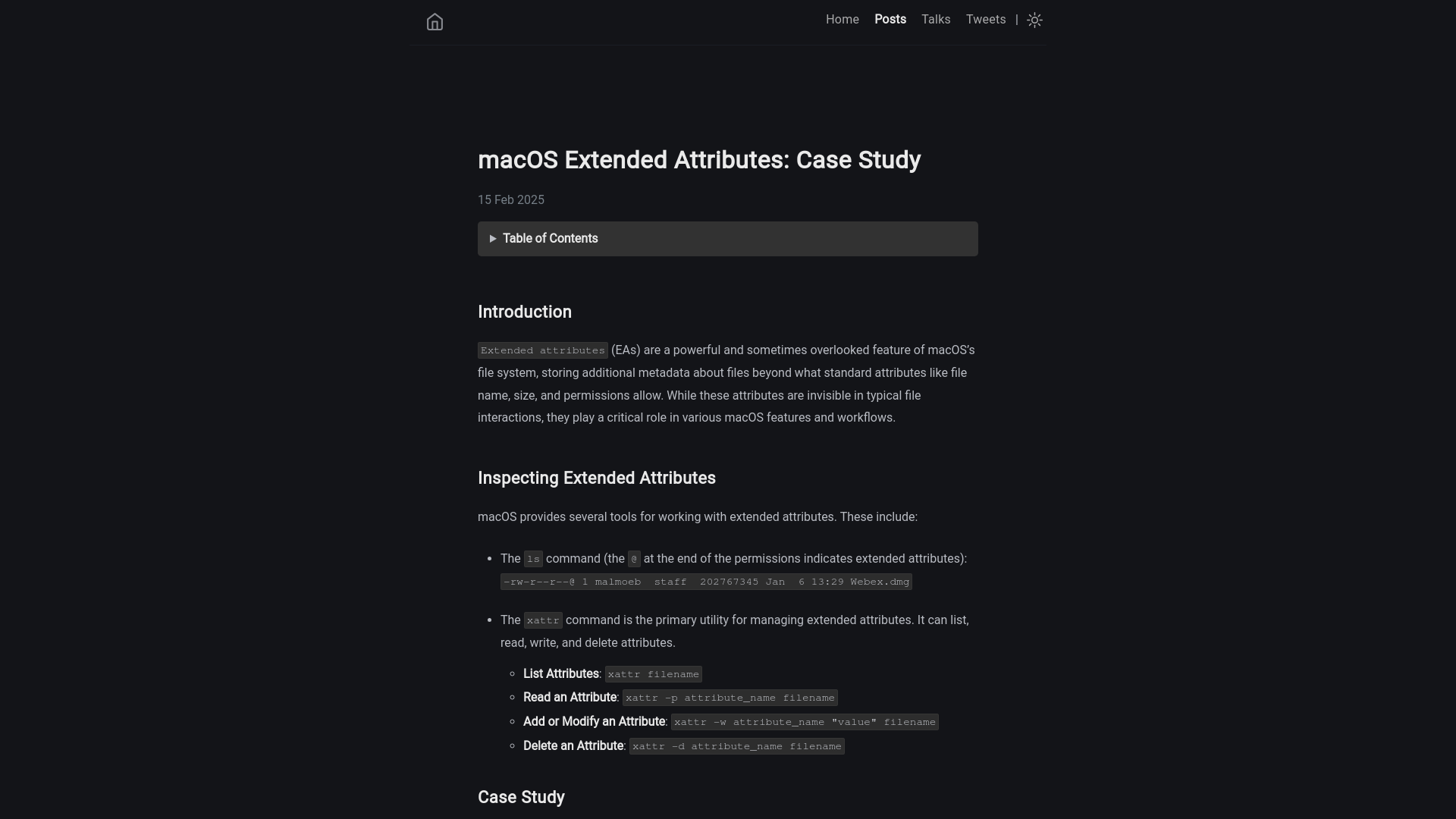
Russian State Hackers Target Organizations With Device Code Phishing - SecurityWeek
https://www.securityweek.com/russian-state-hackers-target-organizations-with-device-code-phishing/
CYBERUK 2023
https://www.cyberuk.uk/
Exploring the DOMPurify library: Hunting for Misconfigurations (2/2) | mizu.re
https://mizu.re/post/exploring-the-dompurify-library-hunting-for-misconfigurations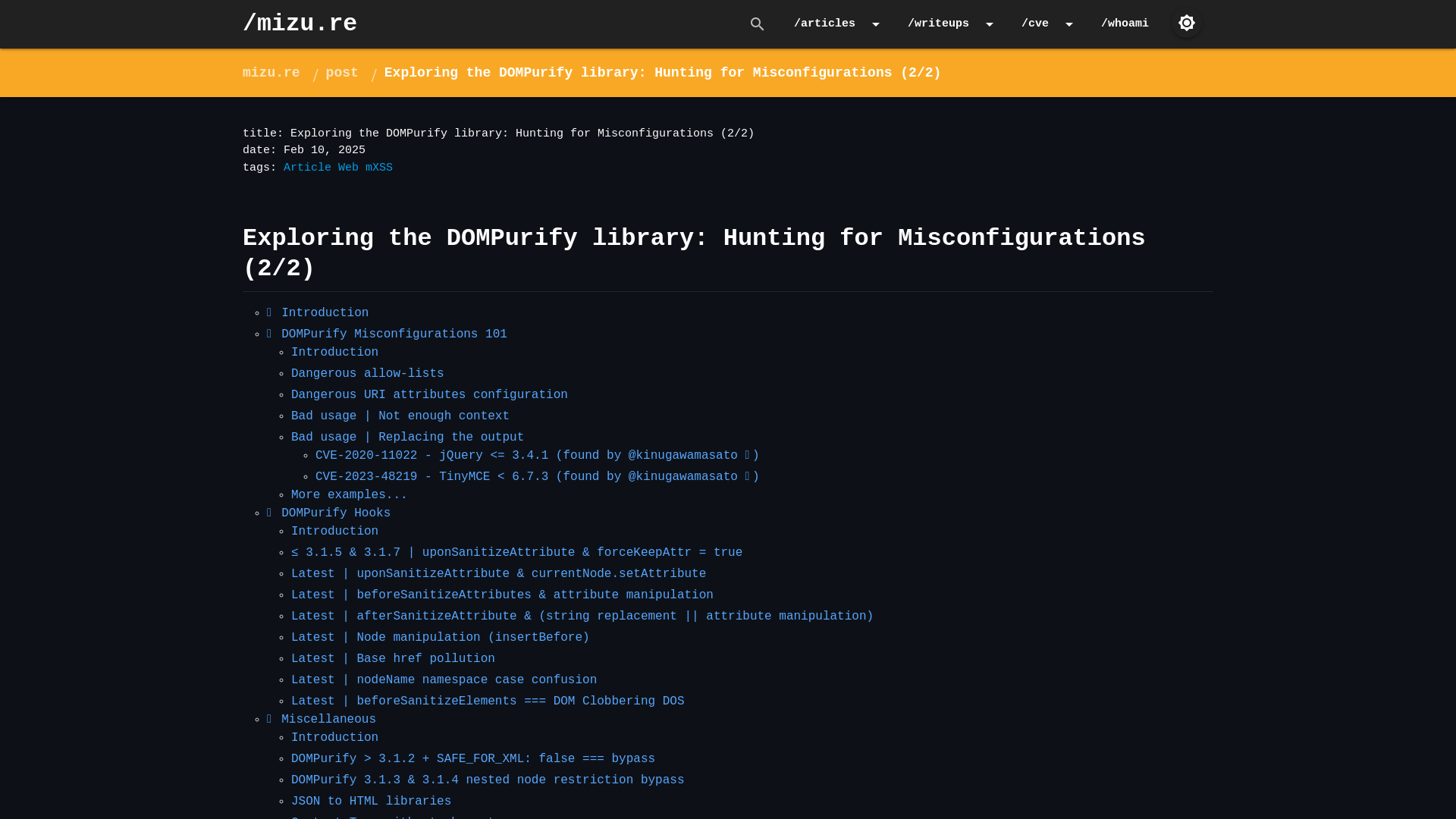
MalwareBazaar | 185-196-11-201
https://bazaar.abuse.ch/browse/tag/185-196-11-201/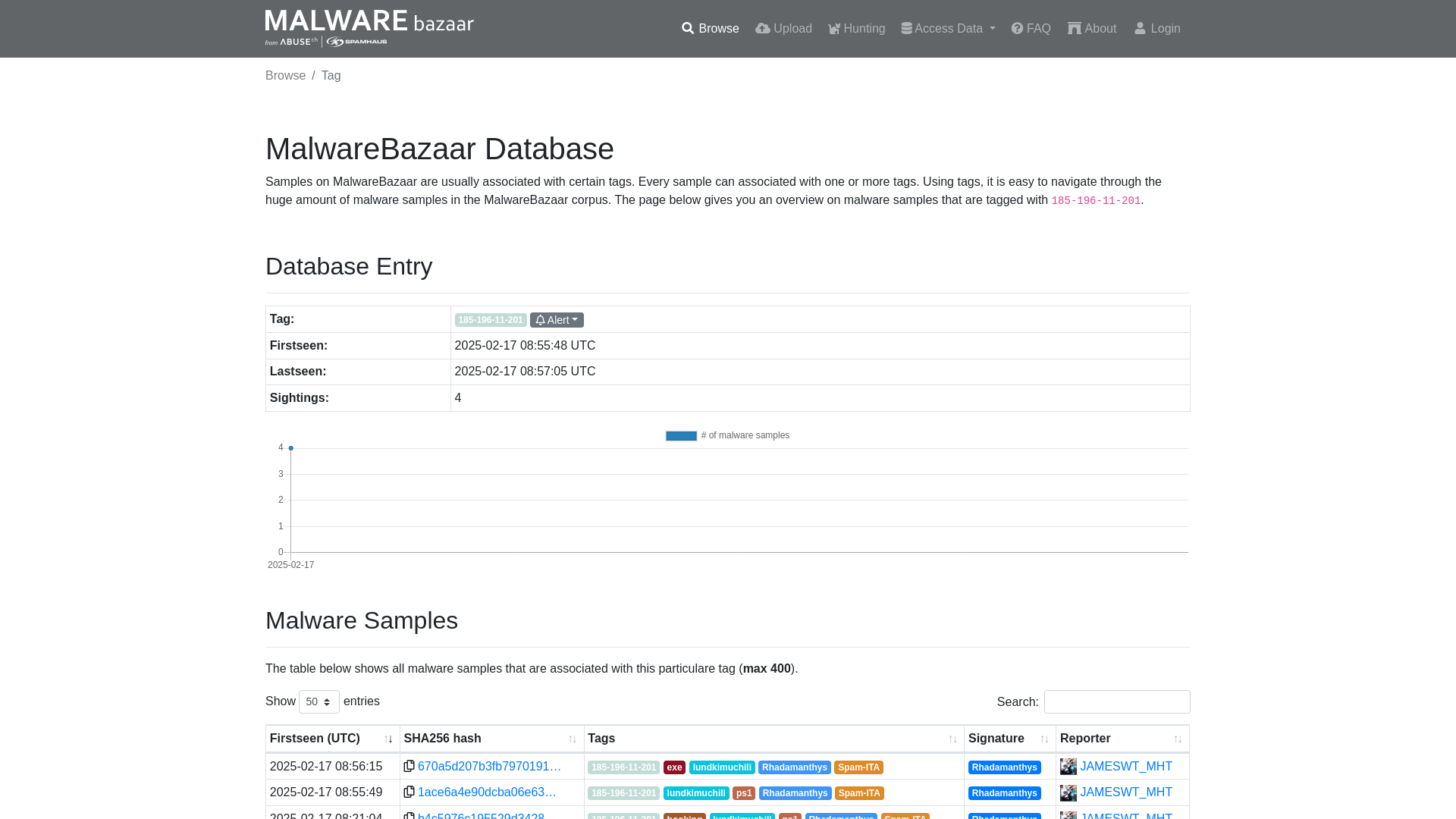
DEF%20CON%2032%20-%20Ken%20Gannon%20Ilyes%20Beghdadi%20-%20Xiaomi%20The%20Money%20Our%20Toronto%20Pwn2Own%20Exploit%20and%20Behind%20The%20Scenes%20Story.pdf
https://media.defcon.org/DEF%20CON%2032/DEF%20CON%2032%20presentations/DEF%20CON%2032%20-%20Ken%20Gannon%20Ilyes%20Beghdadi%20-%20Xiaomi%20The%20Money%20Our%20Toronto%20Pwn2Own%20Exploit%20and%20Behind%20The%20Scenes%20Story.pdf
JavaScript for hackers: Learn to think like a hacker: Heyes, Gareth: 9798371872166: Amazon.com: Books
https://www.amazon.com/JavaScript-hackers-Learn-think-hacker/dp/B0BRD9B3GS/