Russian phishing campaigns exploit Signal's device-linking feature
https://www.bleepingcomputer.com/news/security/russian-phishing-campaigns-exploit-signals-device-linking-feature/
Signals of Trouble: Multiple Russia-Aligned Threat Actors Actively Targeting Signal Messenger | Google Cloud Blog
https://cloud.google.com/blog/topics/threat-intelligence/russia-targeting-signal-messenger
APT-C-28(ScarCruft)组织利用无文件方式投递RokRat的攻击活动分析
https://mp.weixin.qq.com/s/y3TOGCdDp9Eu3Zqz4QnKxQ
Phishing attack hides JavaScript using invisible Unicode trick
https://www.bleepingcomputer.com/news/security/phishing-attack-hides-javascript-using-invisible-unicode-trick/
Trojanized Game Installers Deploy Cryptocurrency Miner in Large-Scale StaryDobry Attack
https://thehackernews.com/2025/02/trojanized-game-installers-deploy.html
DPRK DriverEasy & ChromeUpdate Deep Dive
https://www.kandji.io/blog/drivereasy
XWorm Cocktail: A Mix of PE data with PowerShell Code - SANS Internet Storm Center
https://isc.sans.edu/diary/31700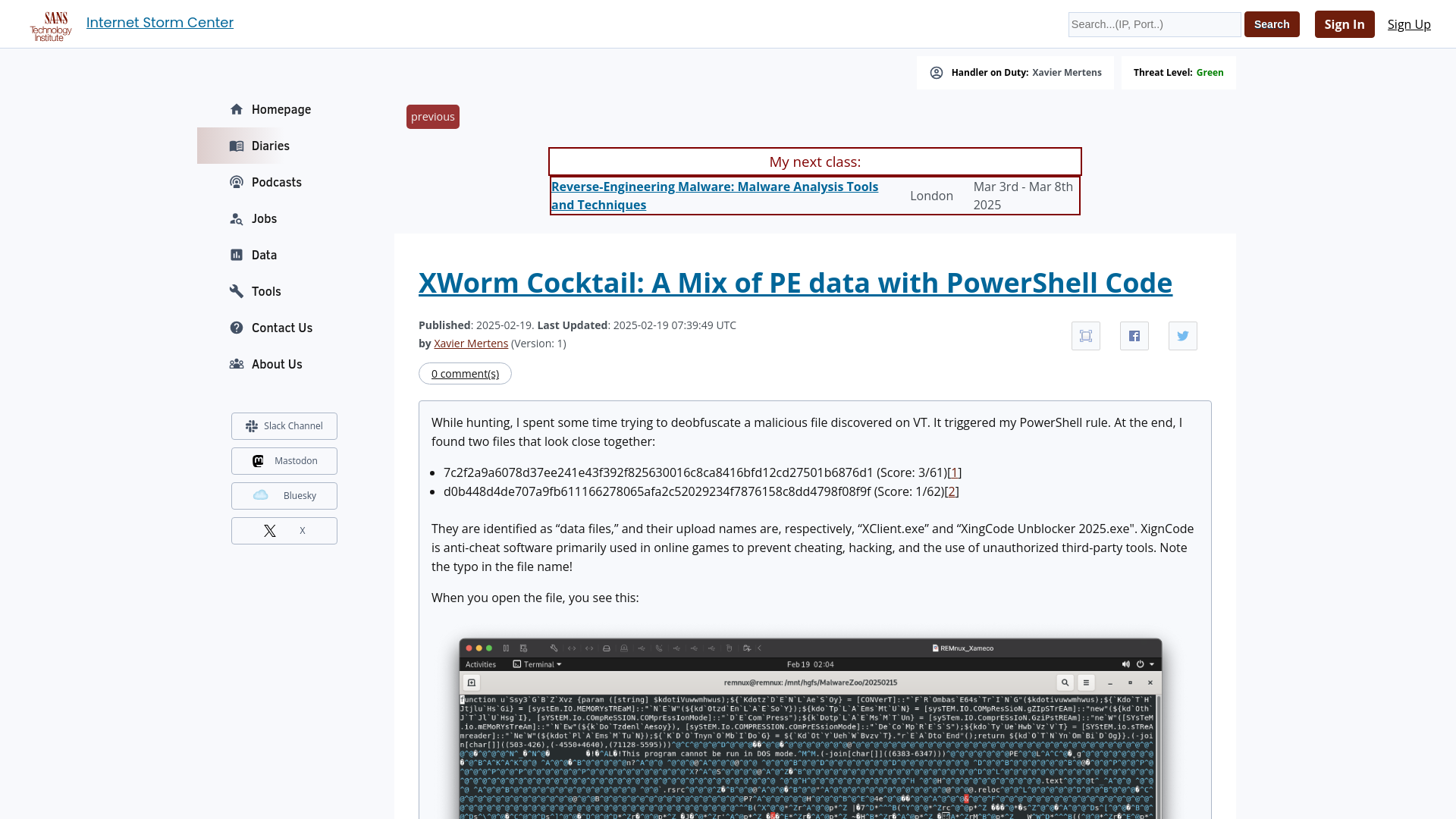
How Russian Hackers Are Exploiting Signal 'Linked Devices' Feature for Real-Time Spying - SecurityWeek
https://www.securityweek.com/how-russian-hackers-are-exploiting-signals-linked-devices-for-real-time-spying/
North Korea's Kimsuky Attacks Rivals' Trusted Platforms
https://www.darkreading.com/cyberattacks-data-breaches/north-koreans-kimsuky-attacks-rivals-trusted-platforms
Palo Alto Networks tags new firewall bug as exploited in attacks
https://www.bleepingcomputer.com/news/security/palo-alto-networks-tags-new-firewall-bug-as-exploited-in-attacks/
Ivanti Endpoint Manager Vulnerabilities: Critical CVEs & Exploit Details
https://www.horizon3.ai/attack-research/attack-blogs/ivanti-endpoint-manager-multiple-credential-coercion-vulnerabilities/
ChatGPT Operator: Prompt Injection Exploits & Defenses · Embrace The Red
https://embracethered.com/blog/posts/2025/chatgpt-operator-prompt-injection-exploits/