GitHub - DavidBuchanan314/monomorph: MD5-Monomorphic Shellcode Packer - all payloads have the same MD5 hash
https://github.com/DavidBuchanan314/monomorph
Hackers use PowerPoint files for 'mouseover' malware delivery
https://www.bleepingcomputer.com/news/security/hackers-use-powerpoint-files-for-mouseover-malware-delivery/
WhatsApp Security Advisories
https://www.whatsapp.com/security/advisories/2022/
Semperis on Twitter: "New research from Semperis' Charlie Clark (@exploitph) describes a vulnerability that could open new attack paths, detection bypasses, and potential weakening of security controls, putting orgs at higher risk from #Kerberoasting and other attacks. 👇 https://t.co/Z3dqq3i8EJ https://t.co/SHlPOdyUlm" / Twitter
https://twitter.com/SemperisTech/status/1574840248760246272
Clare O'Neil MP on Twitter: "What happened at Optus wasn't a sophisticated attack. We should not have a telecommunications provider in this country that has effectively left the window open for data of this nature to be stolen. #abc730 https://t.co/KamkiapcZl" / Twitter
https://twitter.com/clareoneilmp/status/1574361824102711296
Quokka: A Fast and Accurate Binary Exporter
https://blog.quarkslab.com/quokka-a-fast-and-accurate-binary-exporter.html
Optus hacker apologizes and allegedly deletes all stolen data
https://www.bleepingcomputer.com/news/security/optus-hacker-apologizes-and-allegedly-deletes-all-stolen-data/
GitHub - avast/yari: YARI is an interactive debugger for YARA Language.
https://github.com/avast/yari
GitHub - quarkslab/quokka: Quokka: A Fast and Accurate Binary Exporter
https://github.com/quarkslab/quokka
YARI: A New Era of YARA Debugging – Avast Engineering
https://engineering.avast.io/yari-a-new-era-of-yara-debugging/
Lazarus ‘Operation In(ter)ception’ Targets macOS Users Dreaming of Jobs in Crypto - SentinelOne
https://www.sentinelone.com/blog/lazarus-operation-interception-targets-macos-users-dreaming-of-jobs-in-crypto/
Rule Info MAL_RANSOM_Lockbit_3_Jul22_1 - Valhalla
https://valhalla.nextron-systems.com/info/rule/MAL_RANSOM_Lockbit_3_Jul22_1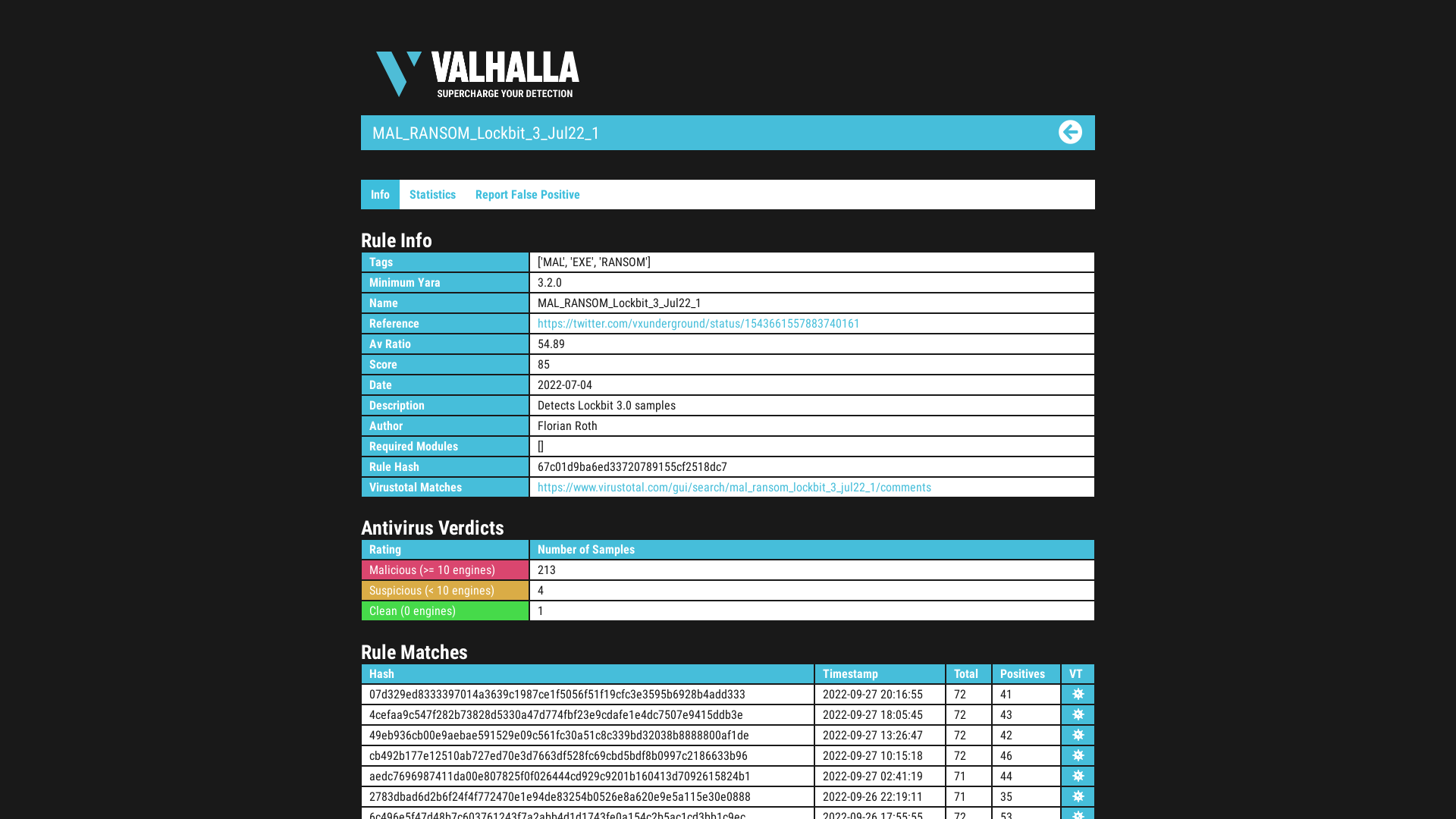
0xToxin on Twitter: "#agenttesla ps1 droppers are being hosted over @Bitbucket https://t.co/SmdsF2b3Nc exfil via FTP to 104.223.118.78 bazaar links: https://t.co/CfUvzUvvgM https://t.co/bydsuN2uoH Triage: https://t.co/P6BB56RGGA https://t.co/oMefQtu4Tn https://t.co/1fsIIidswt" / Twitter
https://twitter.com/0xToxin/status/1571852279581675520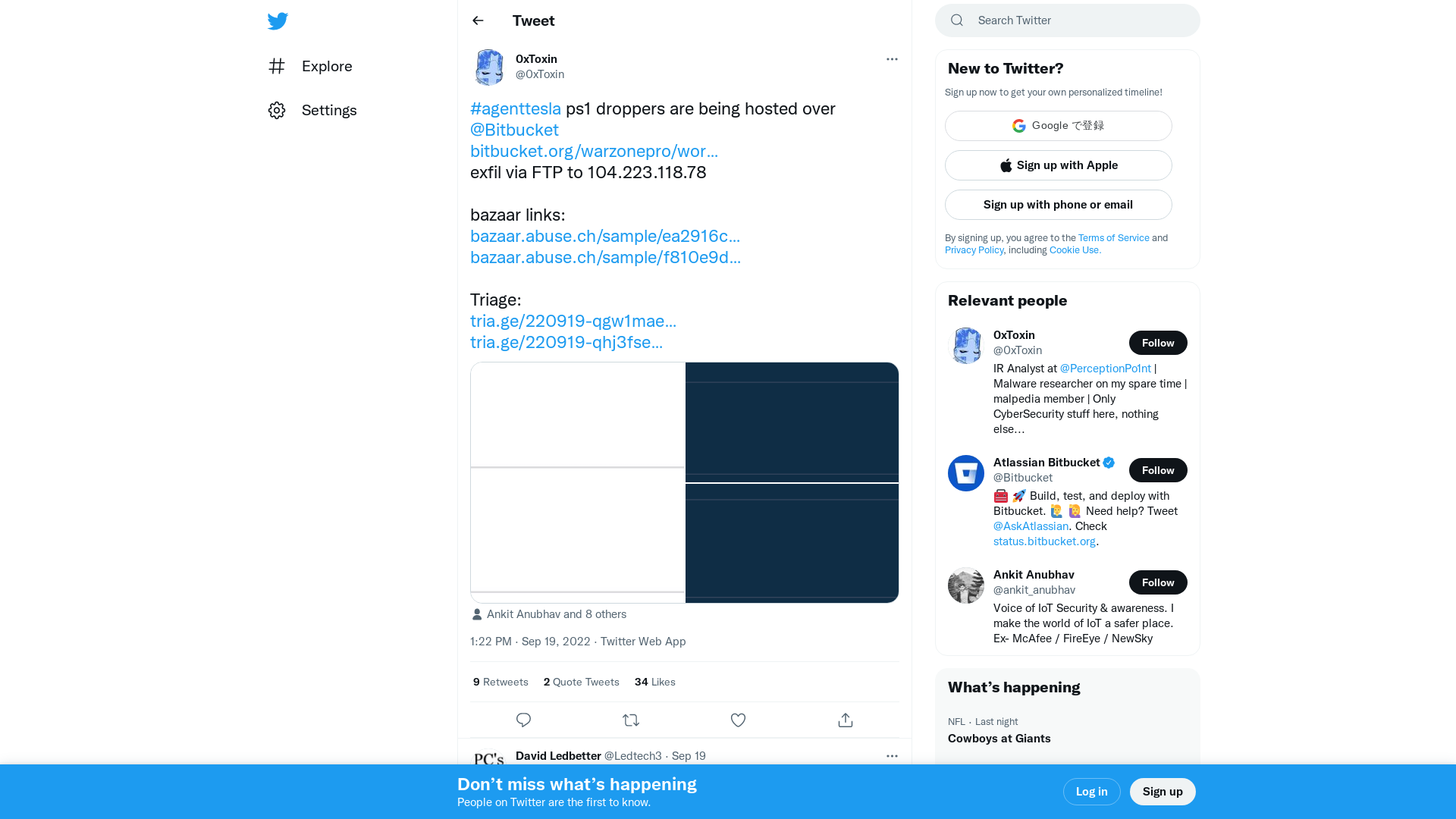
Chinese State-Sponsored Group TA413 Adopts New Capabilities in Pursuit of Tibetan Targets
https://www.recordedfuture.com/chinese-state-sponsored-group-ta413-adopts-new-capabilities-in-pursuit-of-tibetan-targets
MalwareBazaar | 9178UTuitA24715UTuitA26909
https://bazaar.abuse.ch/browse/tag/9178UTuitA24715UTuitA26909/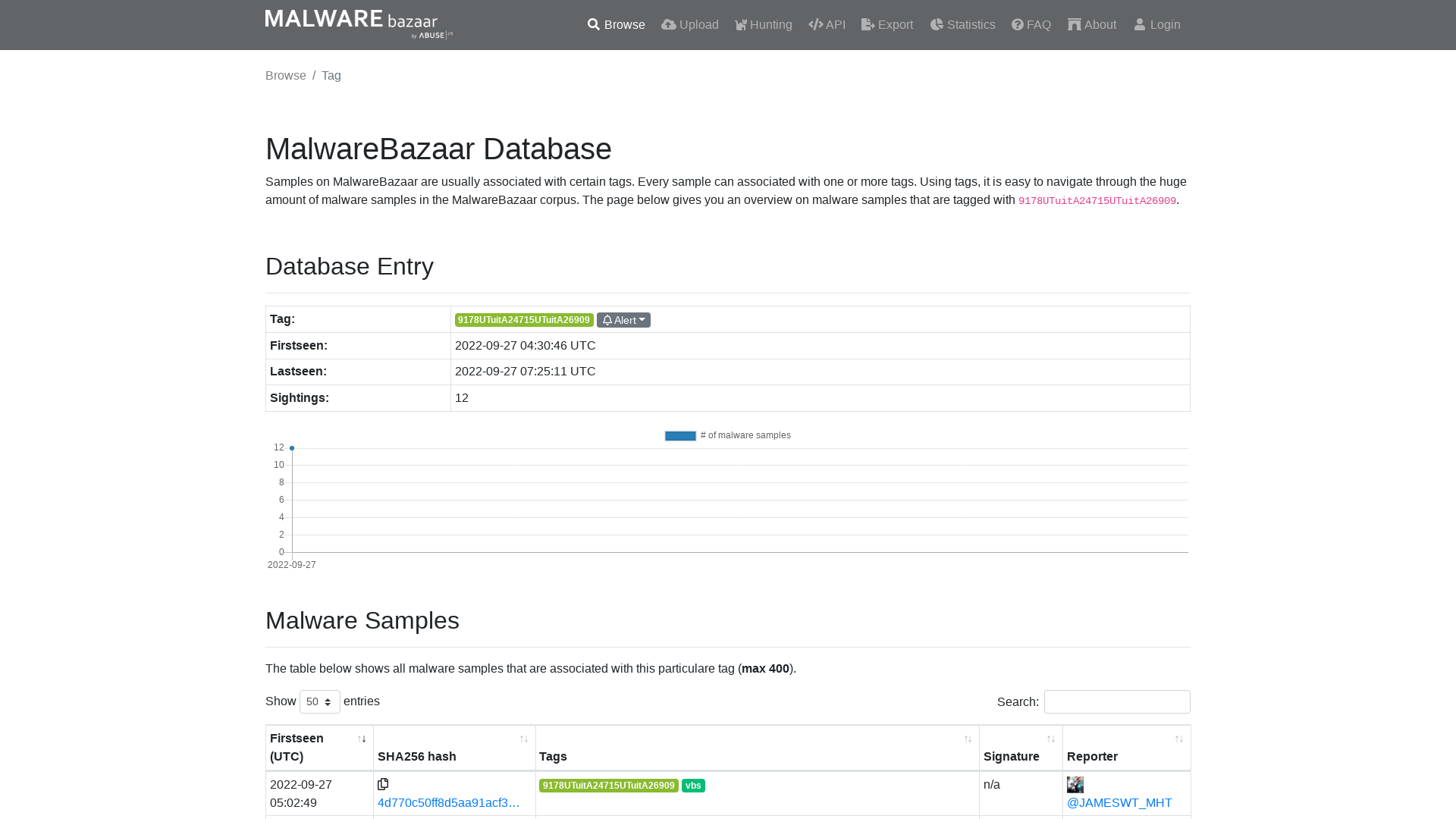
tinypro / Snippets — Bitbucket
https://bitbucket.org/tinypro/workspace/snippets/
Ukraine Says Russia Planning Massive Cyberattacks on its Critical Infrastructures
https://thehackernews.com/2022/09/ukraine-says-russia-planning-massive.html
IOCs/2022-09-27-TA569-Soc-Gholish-IOCs.txt at main · brad-duncan/IOCs · GitHub
https://github.com/brad-duncan/IOCs/blob/main/2022-09-27-TA569-Soc-Gholish-IOCs.txt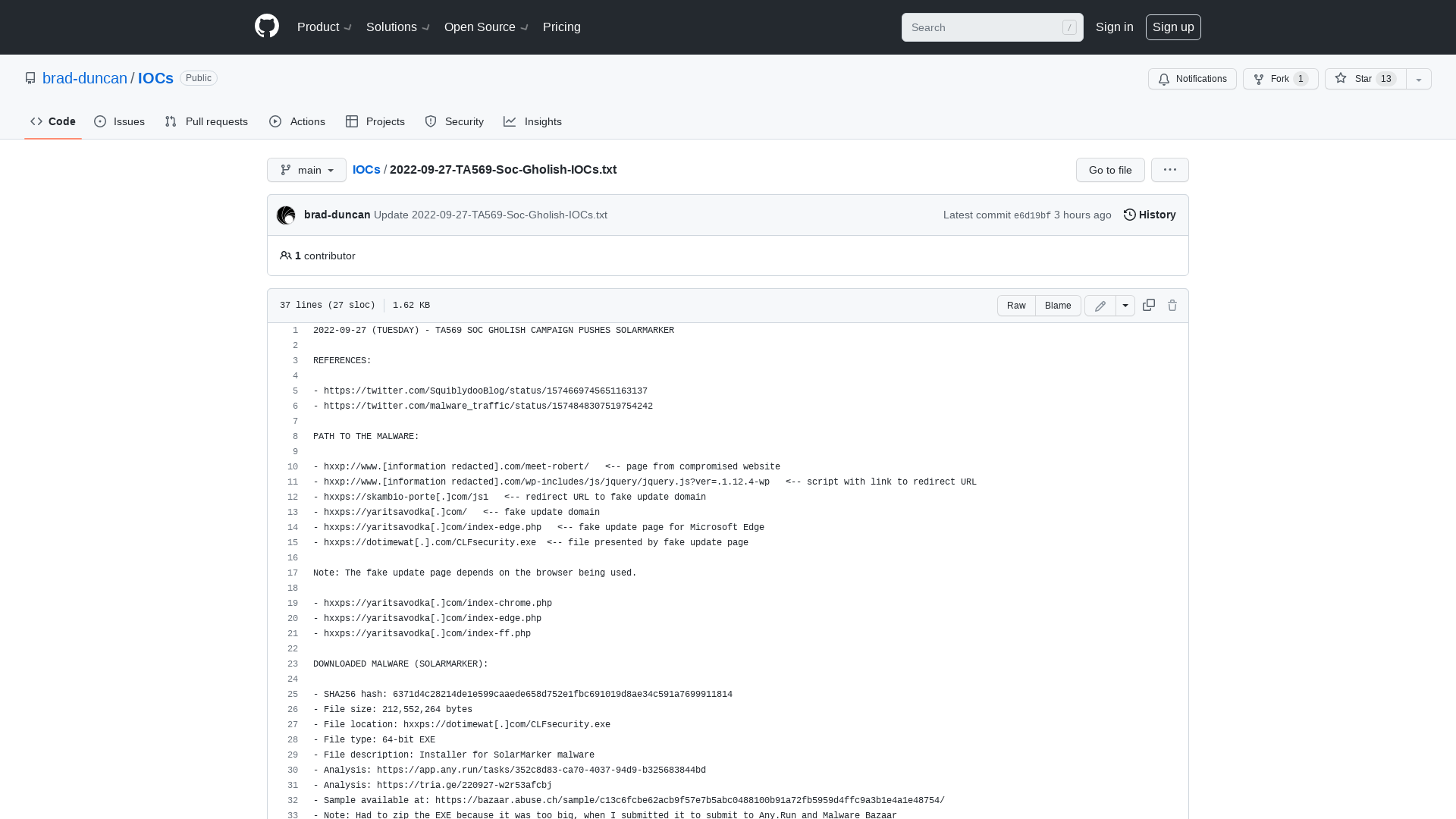
Los Angeles Times on Twitter: "FBI agents drilled and pried their way into 1,400 safe-deposit boxes. 18 months later, newly unsealed court documents show that the FBI and U.S. attorney’s office in Los Angeles got their warrant for that raid by misleading the judge who approved it. https://t.co/zygb4JQG3u" / Twitter
https://twitter.com/latimes/status/1573303672850612224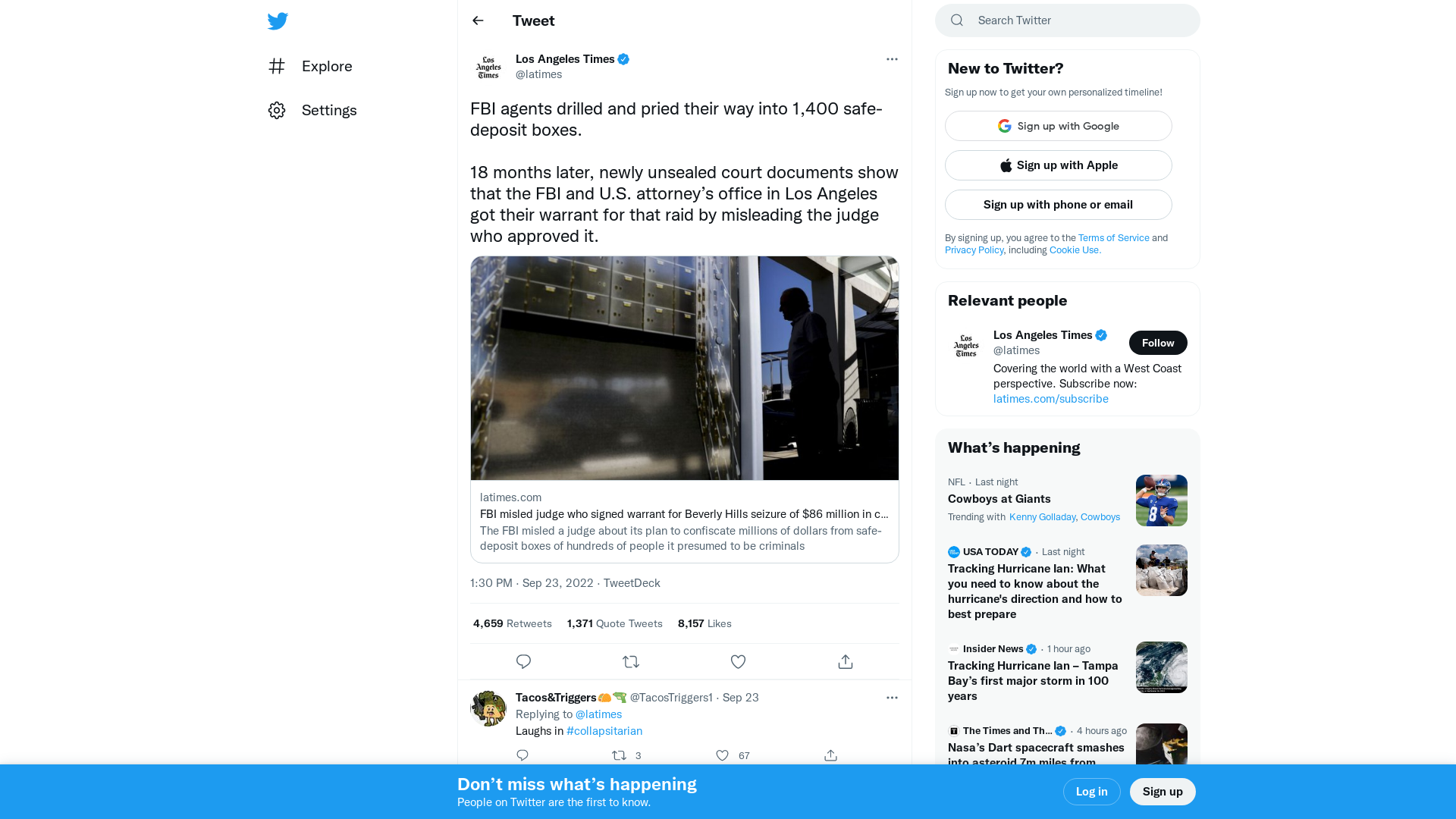
Skype for Business Audit Part 2 - SKYPErimeterleak | Frycos Security Diary
https://frycos.github.io/vulns4free/2022/09/26/skype-audit-part2.html