VirusTotal - File - 591c2cd3a9b902a182fbf05bf5423cae17e3e6874c0d2e09107e914d86f39780
https://www.virustotal.com/gui/file/591c2cd3a9b902a182fbf05bf5423cae17e3e6874c0d2e09107e914d86f39780
Semperis on Twitter: "New research from Semperis' Charlie Clark (@exploitph) describes a vulnerability that could open new attack paths, detection bypasses, and potential weakening of security controls, putting orgs at higher risk from #Kerberoasting and other attacks. 👇 https://t.co/Z3dqq3i8EJ https://t.co/SHlPOdyUlm" / Twitter
https://twitter.com/SemperisTech/status/1574840248760246272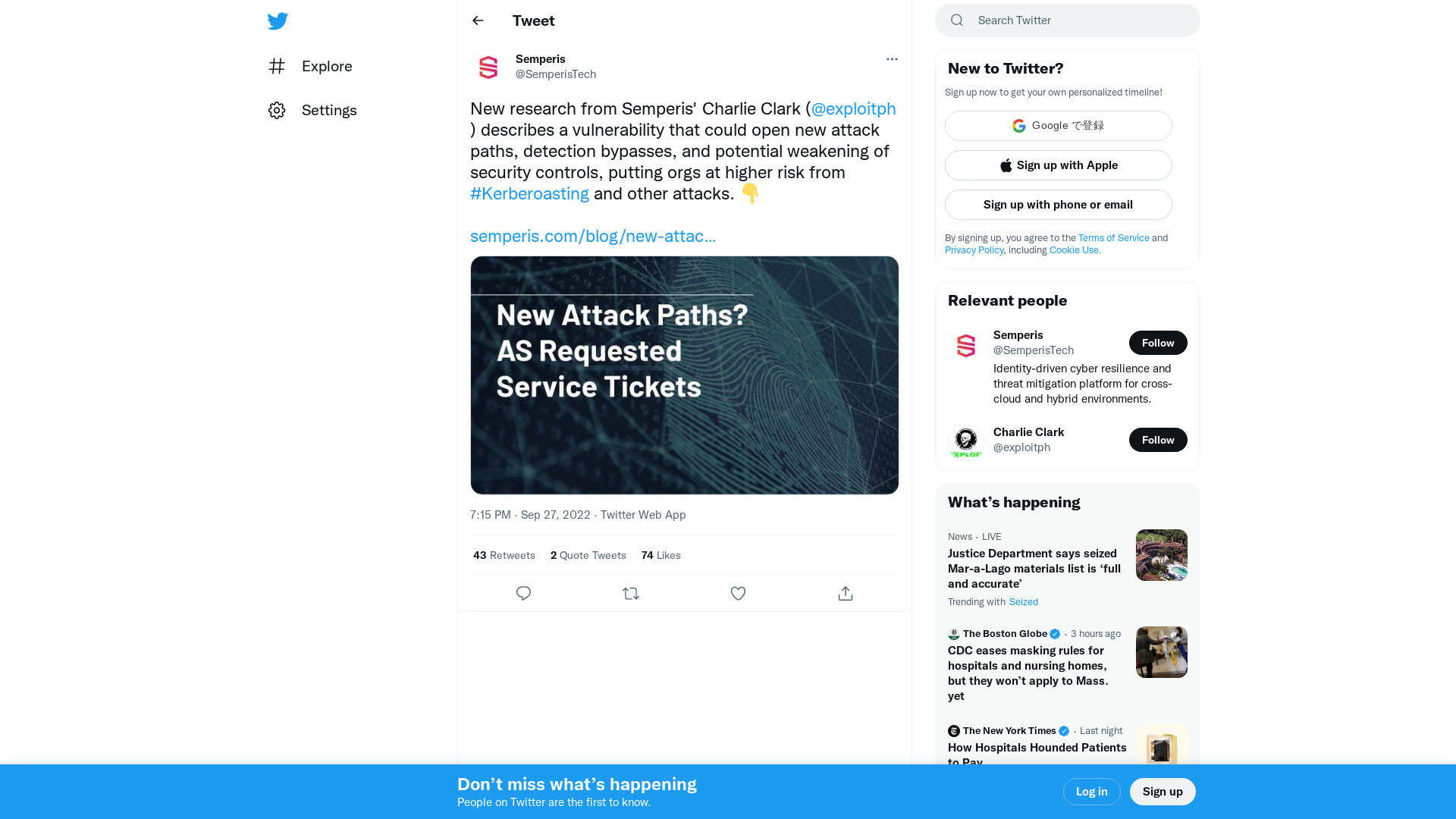
Phoenix CTF on Twitter: "Why does the National Trans Memorial need to be replaced? It's been neglected and misused for years now, but during Manchester Pride something set the monument alight and caused irreparable damage. We'd like something a bit more permanent to remember and mourn our loved ones. https://t.co/jLHj74B6Mg" / Twitter
https://twitter.com/TransCTF/status/1574120553044115457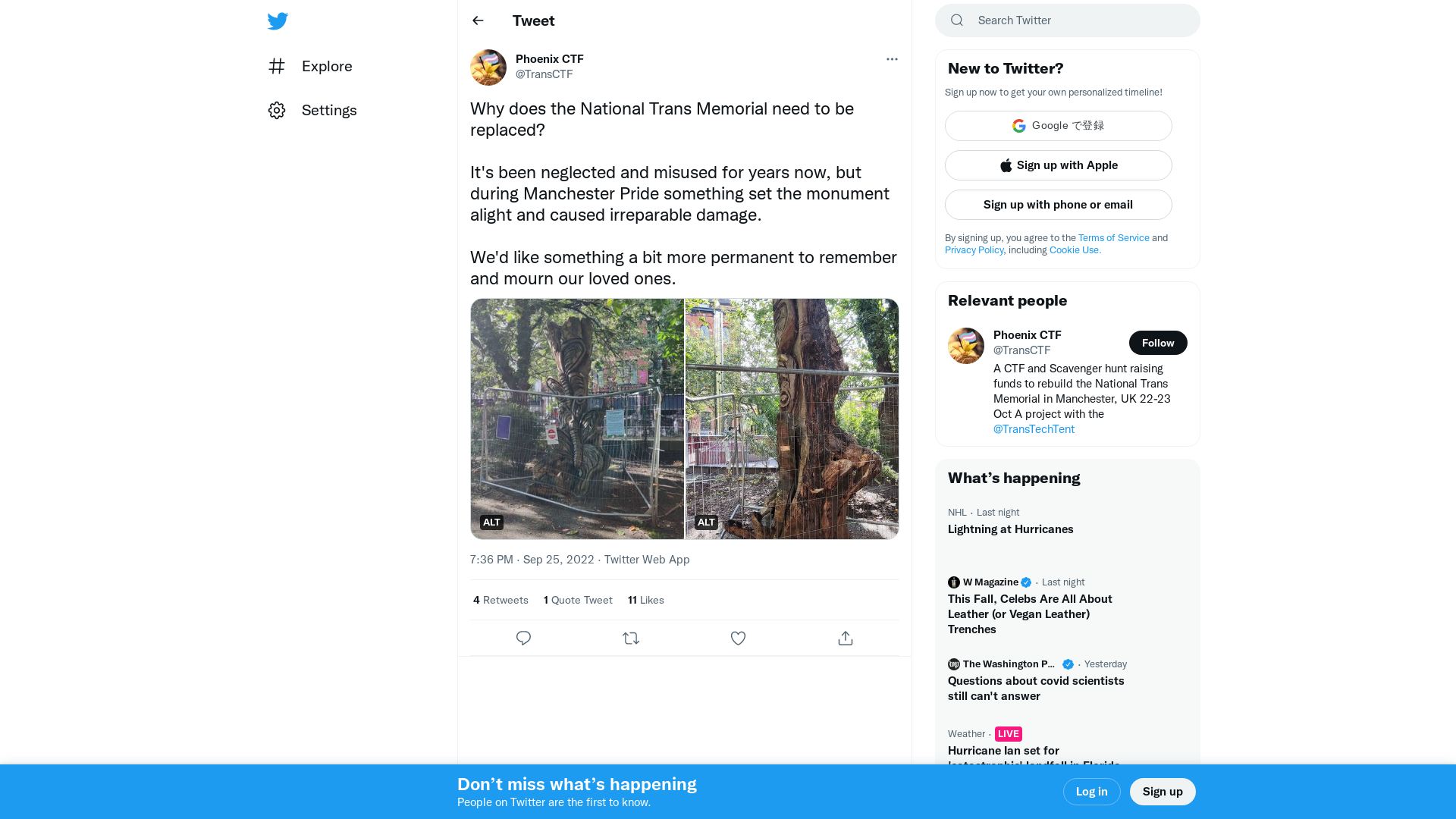
The difference between signature-based and behavioural detections | S3cur3Th1sSh1t
https://s3cur3th1ssh1t.github.io/Signature_vs_Behaviour/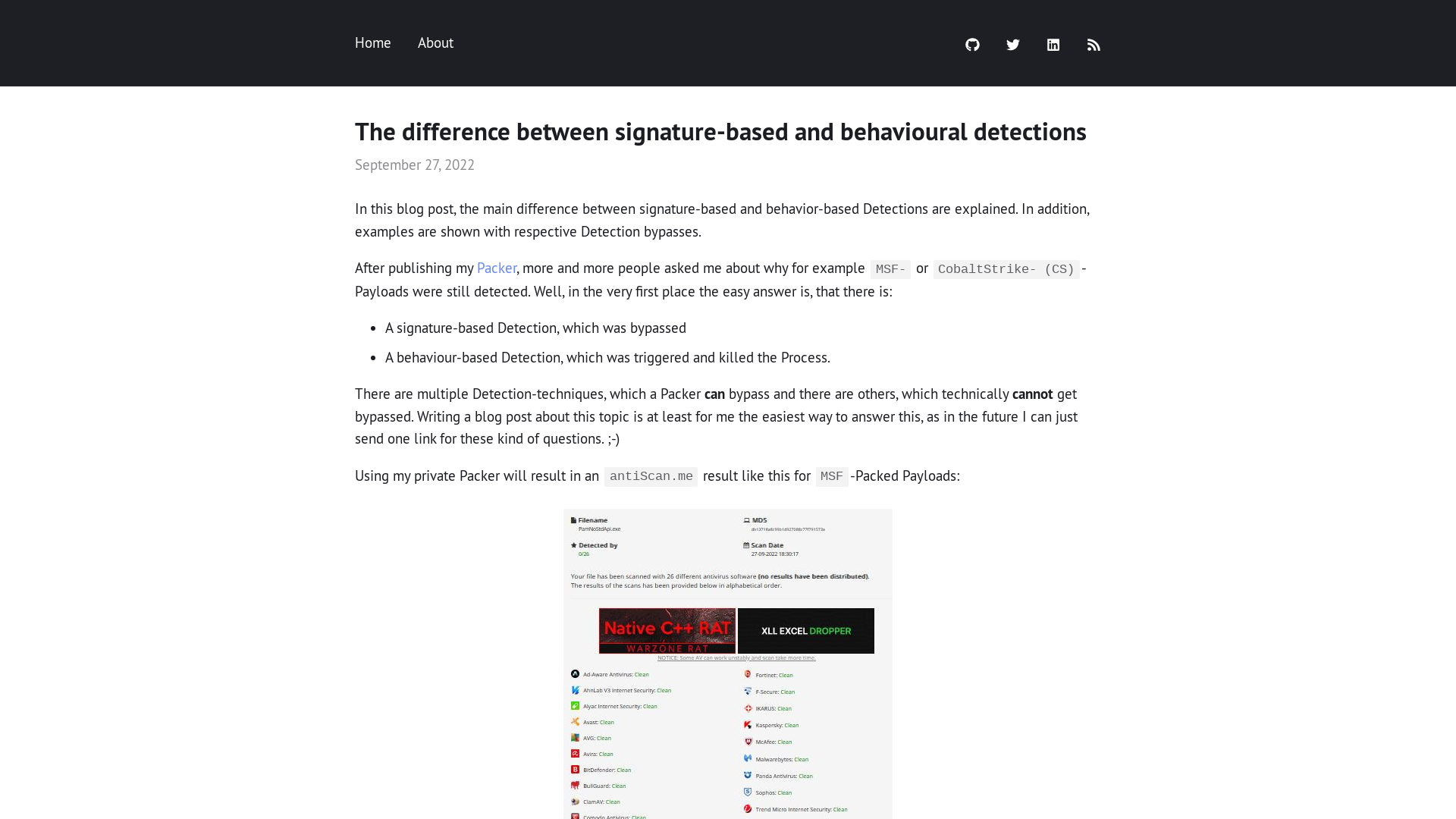
MalwareBazaar | SHA256 8b440ad96f7ed8319419fbae878d48db0ad81107ede8ef862f8f0dc65ea8b527
https://bazaar.abuse.ch/sample/8b440ad96f7ed8319419fbae878d48db0ad81107ede8ef862f8f0dc65ea8b527/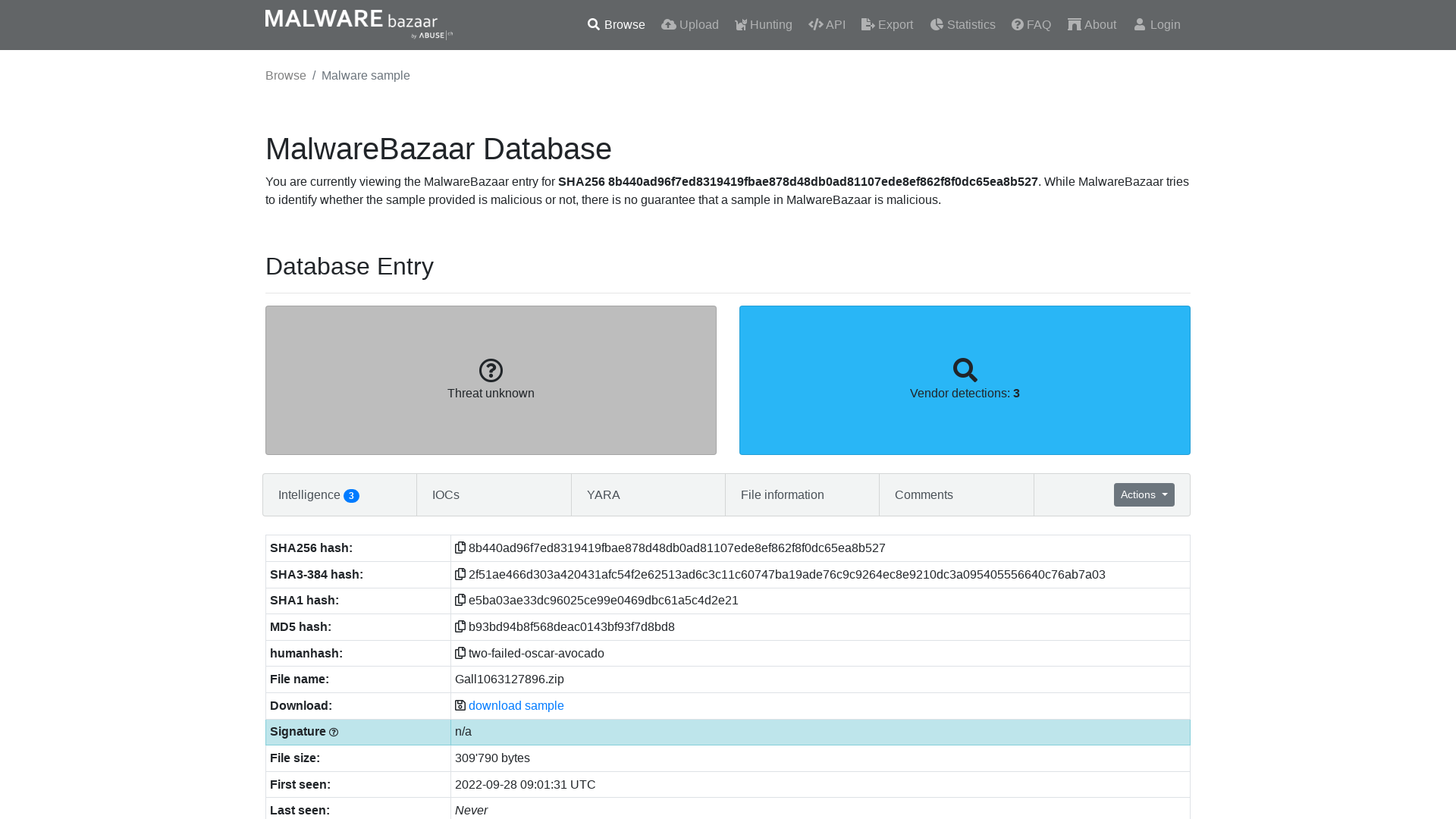
Leaked LockBit 3.0 builder used by ‘Bl00dy’ ransomware gang in attacks
https://www.bleepingcomputer.com/news/security/leaked-lockbit-30-builder-used-by-bl00dy-ransomware-gang-in-attacks/
Qakbot/Qakbot_BB_28.09.2022.txt at main · pr0xylife/Qakbot · GitHub
https://github.com/pr0xylife/Qakbot/blob/main/Qakbot_BB_28.09.2022.txt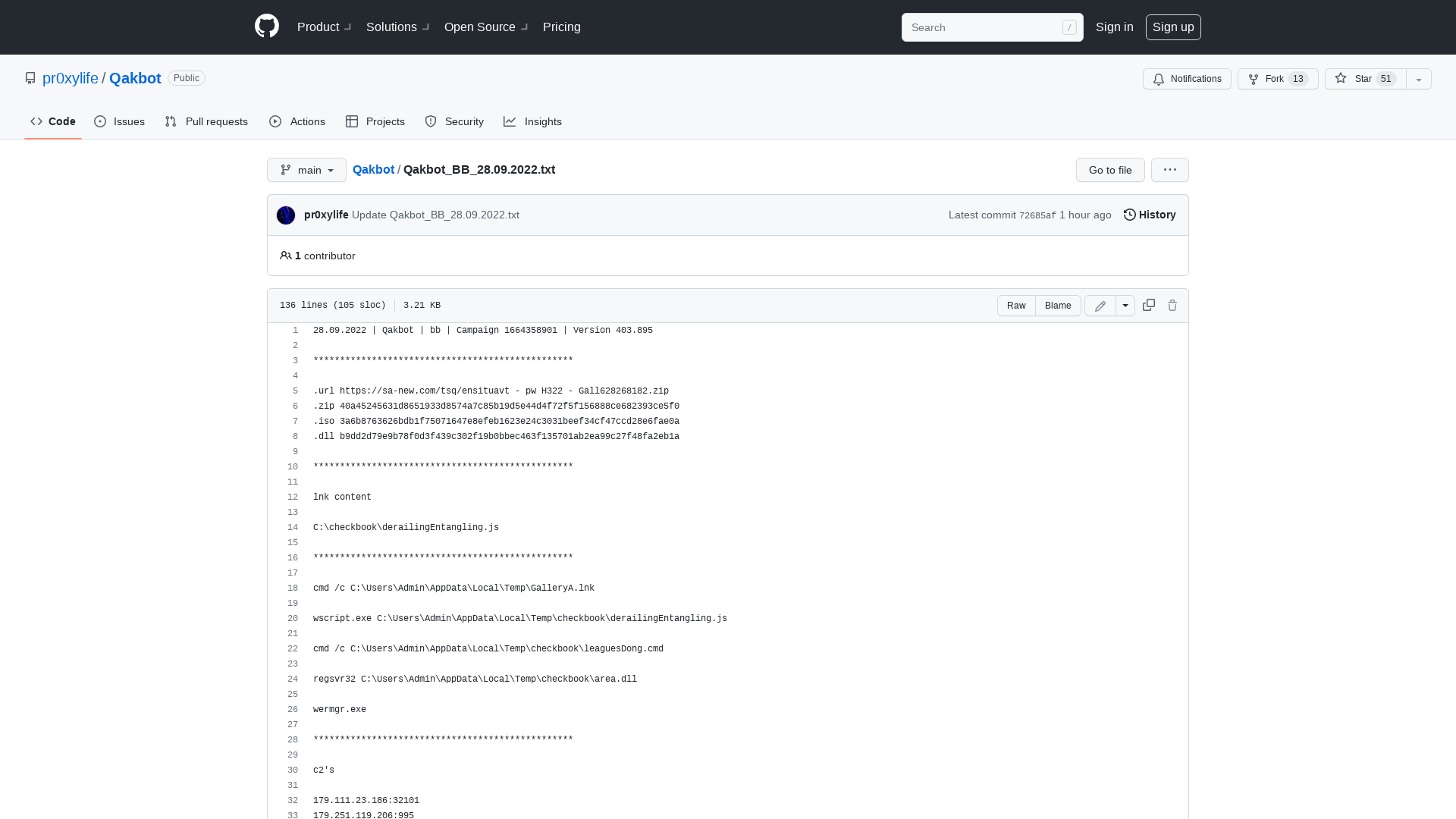
MalwareBazaar | SHA256 ac75ab4c3a8ee0979b4ea982b38ae9eea6c94ab8e3459705fe5529c3653a853f
https://bazaar.abuse.ch/sample/ac75ab4c3a8ee0979b4ea982b38ae9eea6c94ab8e3459705fe5529c3653a853f/
MalwareBazaar | SHA256 466484398eb25d42b0e0b095f10590a566610447eb212d1dc7f7bd342e89fe5a (Quakbot)
https://bazaar.abuse.ch/sample/466484398eb25d42b0e0b095f10590a566610447eb212d1dc7f7bd342e89fe5a/
Qakbot/Qakbot_obama207_28.09.2022.txt at main · pr0xylife/Qakbot · GitHub
https://github.com/pr0xylife/Qakbot/blob/main/Qakbot_obama207_28.09.2022.txt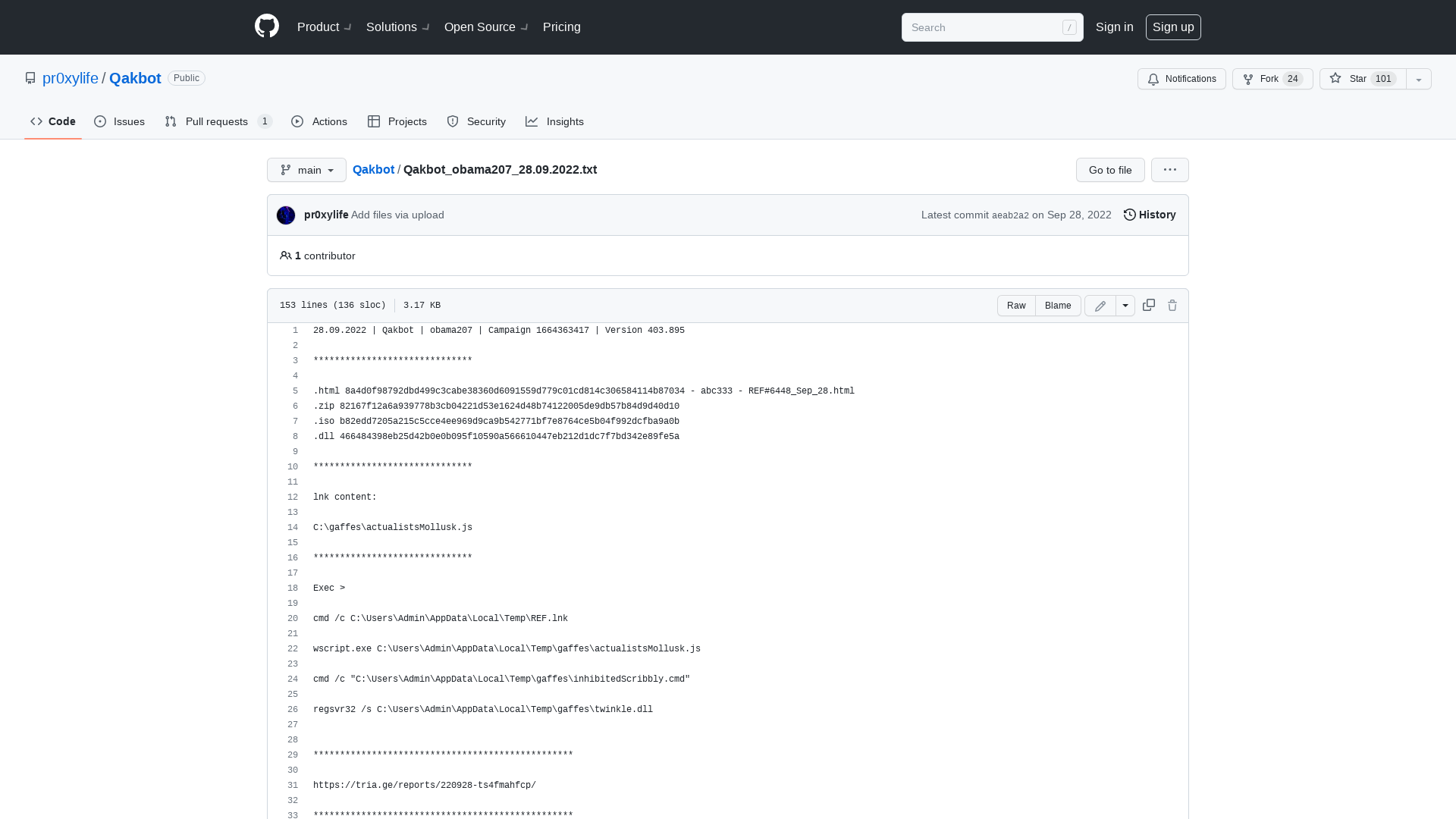
MalwareBazaar | SHA256 8a4d0f98792dbd499c3cabe38360d6091559d779c01cd814c306584114b87034
https://bazaar.abuse.ch/sample/8a4d0f98792dbd499c3cabe38360d6091559d779c01cd814c306584114b87034/
RealSubtitles on Twitter: "Solovyov gets drafted and goes crazy. https://t.co/bd8lMf4zFi" / Twitter
https://twitter.com/R82938886/status/1574865224108220423
Hackers Using PowerPoint Mouseover Trick to Infect System with Malware
https://thehackernews.com/2022/09/hackers-using-powerpoint-mouseover.html
ビジネスメール詐欺(BEC)対策特設ページ:IPA 独立行政法人 情報処理推進機構
https://www.ipa.go.jp/security/bec/index.html
Will on Twitter: "ICYMI, threat actors on multiple underground forums are sharing around a copy of a cracked version of Brute Ratel (aka BRC4), brace for attacks "bruteratel_1.2.2.Scandinavian_Defense.tar.gz" https://t.co/jfWXV8sJbR h/t @darkcoders_mrx for the pic https://t.co/OhfRMZBzVl" / Twitter
https://twitter.com/BushidoToken/status/1575054022784208897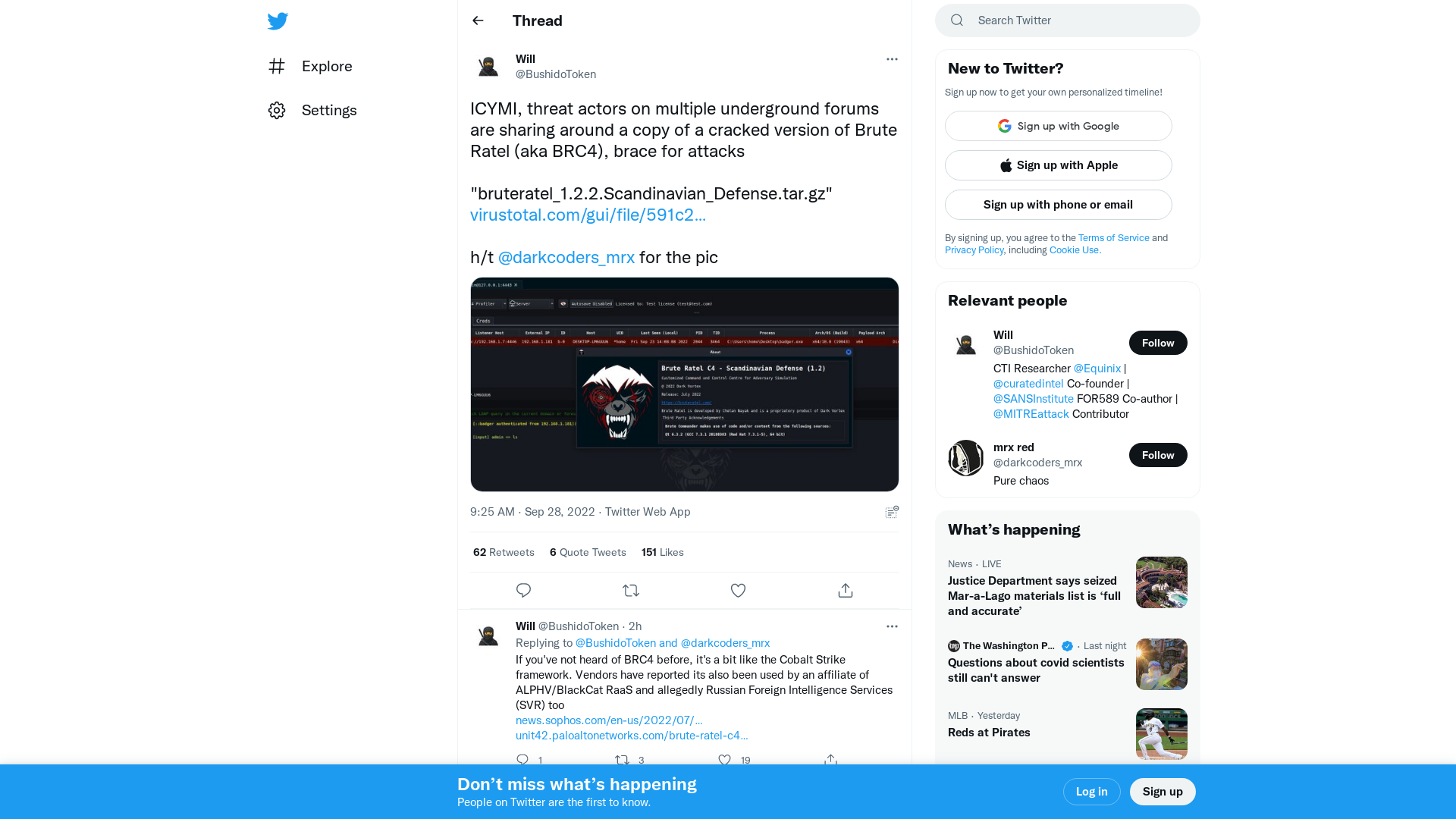
Forensic artifacts in Office 365 and where to find them - Microsoft Tech Community
https://techcommunity.microsoft.com/t5/security-compliance-and-identity/forensic-artifacts-in-office-365-and-where-to-find-them/ba-p/3634865
VT Collections: citius, altius, fortius - communiter ~ VirusTotal Blog
https://blog.virustotal.com/2022/09/vt-collections-citius-altius-fortius.html
RED TEAM Operator: Malware Development Advanced - Vol.1
http://institute.sektor7.net/rto-maldev-adv1
Constrained Language Mode Bypass When __PSLockDownPolicy Is Used - Black Hills Information Security
https://www.blackhillsinfosec.com/constrained-language-mode-bypass-when-pslockdownpolicy-is-used/
Securonix Threat Labs Security Advisory: Detecting STEEP#MAVERICK: New Covert Attack Campaign Targeting Military Contractors - Securonix
https://www.securonix.com/blog/detecting-steepmaverick-new-covert-attack-campaign-targeting-military-contractors/
Threat Report: Illuminating Volume Shadow Deletion - VMware Security Blog - VMware
https://blogs.vmware.com/security/2022/09/threat-report-illuminating-volume-shadow-deletion.html