BumbleBee: Round Two – The DFIR Report
https://thedfirreport.com/2022/09/26/bumblebee-round-two/
Окупанти готують масовані кібератаки на об’єкти критичної інфраструктури України та її союзників
https://gur.gov.ua/content/okupanty-hotuiut-masovani-kiberataky-na-ob-iekty-krytychnoi-infrastruktury-ukrainy-ta-ii-soiuznykiv.html
TangledWinExec/ProcMemScan at main · daem0nc0re/TangledWinExec · GitHub
https://github.com/daem0nc0re/TangledWinExec/tree/main/ProcMemScan
GitHub - ufrisk/MemProcFS: MemProcFS
https://github.com/ufrisk/MemProcFS
In the footsteps of the Fancy Bear: PowerPoint mouse-over event abused to deliver Graphite implants
https://blog.cluster25.duskrise.com/2022/09/23/in-the-footsteps-of-the-fancy-bear-powerpoint-graphite/
DOCGuard - Detect Maldocs in Seconds! on Twitter: "Strange PPT maldoc with low detection rates since 2022-02-02. MD5: c0060c0741833af67121390922c44f91 PPT file>wscript.exe>powershell.exe>rundll32.exe [+]Exec wscript when user moves mouse [+]Wscript exec powershell [+]PS download the XORed DLL. [+]Exec it using rundll32.exe https://t.co/aIxMEeVqLR" / Twitter
https://twitter.com/doc_guard/status/1570190610774257665![DOCGuard - Detect Maldocs in Seconds! on Twitter: "Strange PPT maldoc with low detection rates since 2022-02-02. MD5: c0060c0741833af67121390922c44f91 PPT file>wscript.exe>powershell.exe>rundll32.exe [+]Exec wscript when user moves mouse [+]Wscript exec powershell [+]PS download the XORed DLL. [+]Exec it using rundll32.exe https://t.co/aIxMEeVqLR" / Twitter](/image/screenshot/c7ae2ba81b8fe1a3a98f7ad460773e45.png)
John Hultquist🌻 on Twitter: "BREAKING: Ukrainian intel warning of cyberattacks against Ukraine and allies: "The Kremlin plans to carry out massive cyberattacks on critical infrastructure facilities of Ukrainian enterprises and critical infrastructure institutions of Ukraine's allies." https://t.co/XiQpnThv6d" / Twitter
https://twitter.com/JohnHultquist/status/1574398836394823681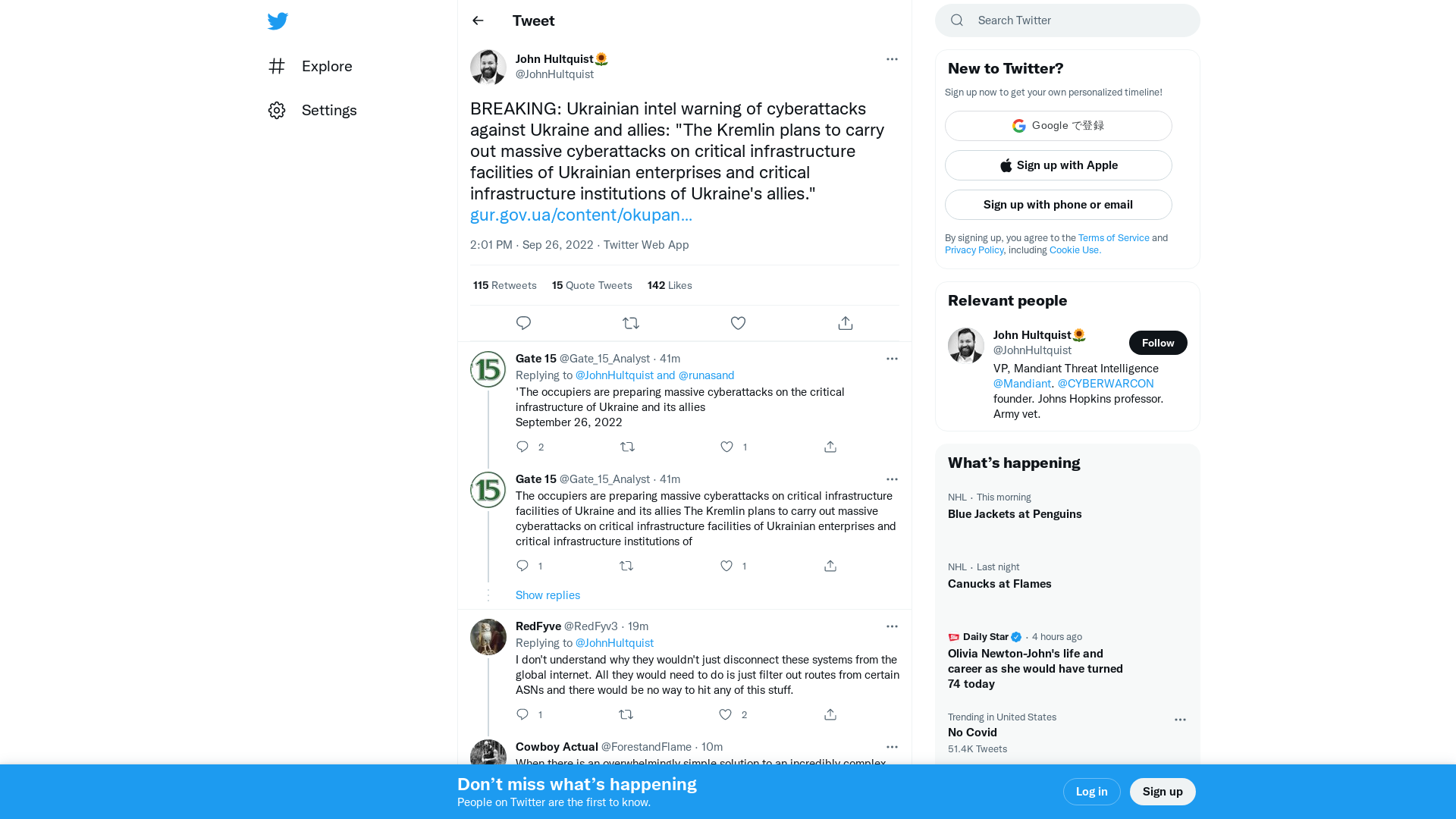
How 3 hours of inaction from Amazon cost cryptocurrency holders $235,000 – Ars Technica
https://arstechnica-com.cdn.ampproject.org/c/s/arstechnica.com/information-technology/2022/09/how-3-hours-of-inaction-from-amazon-cost-cryptocurrency-holders-235000/?amp=1
UNLEASH THE BEAST | THE FUTURE | H O M E
https://devilinside.me/blogs/configuration-extraction-yara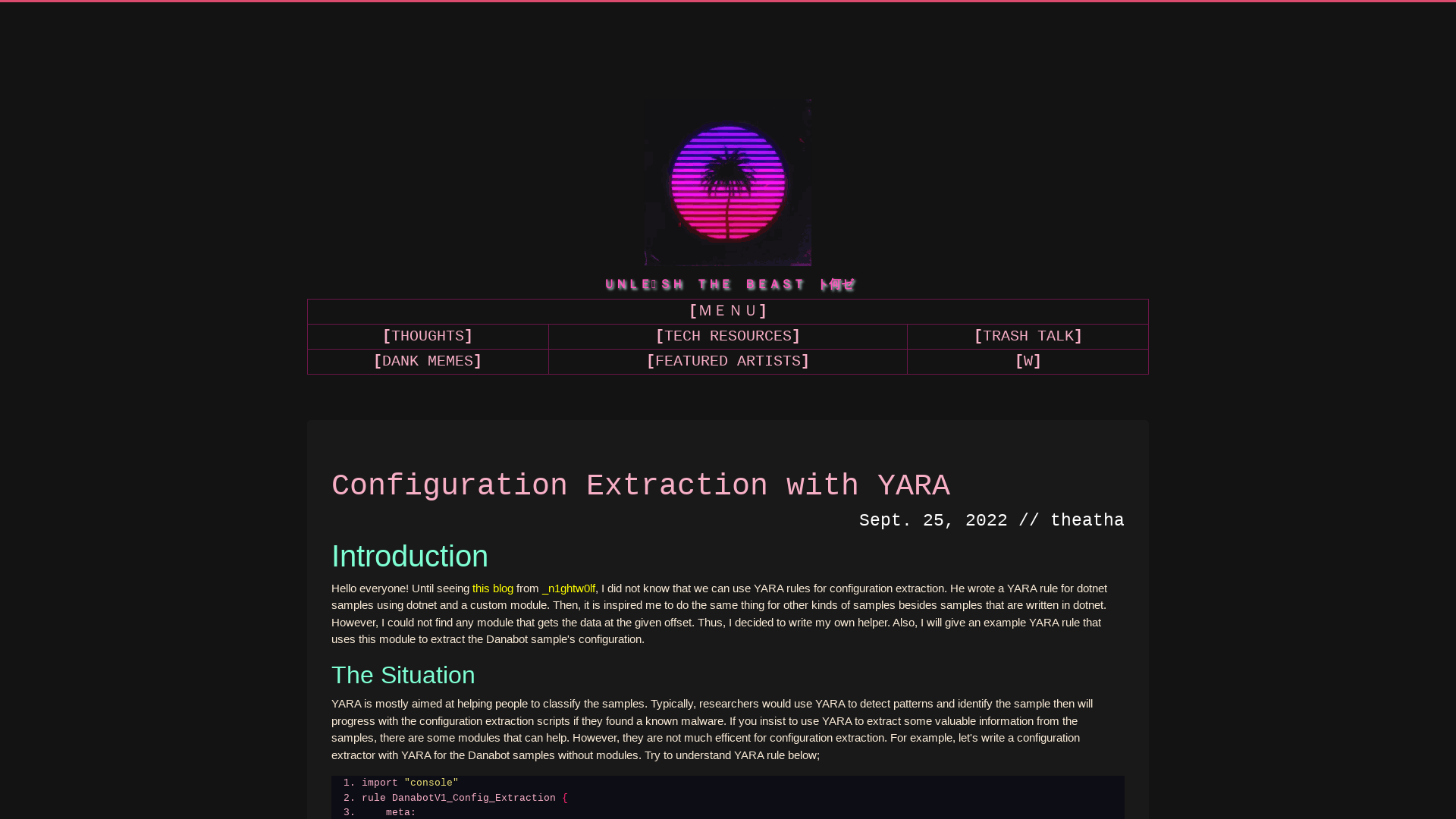
GitHub - jazzpizazz/BloodHound.py-Kerberos: A Python based ingestor for BloodHound
https://github.com/jazzpizazz/BloodHound.py-Kerberos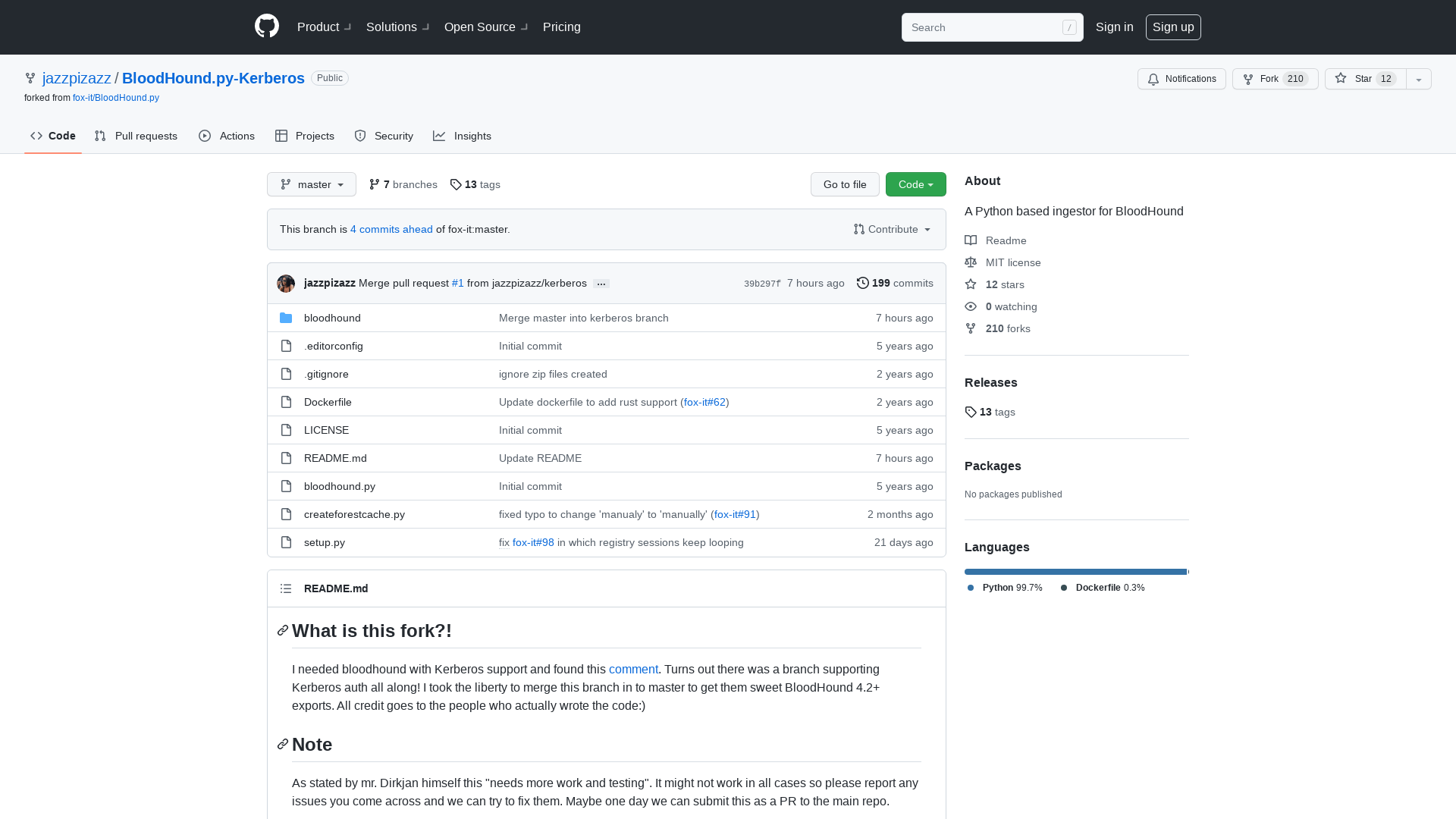
Hackers use PowerPoint files for 'mouseover' malware delivery
https://www.bleepingcomputer.com/news/security/hackers-use-powerpoint-files-for-mouseover-malware-delivery/
GitHub - theatha/YARA_for_config_extraction
https://github.com/theatha/YARA_for_config_extraction
Chinese Espionage Hackers Target Tibetans Using New LOWZERO Backdoor
https://thehackernews.com/2022/09/chinese-espionage-hackers-target.html
Ransomware data theft tool may show a shift in extortion tactics
https://www.bleepingcomputer.com/news/security/ransomware-data-theft-tool-may-show-a-shift-in-extortion-tactics/
APT41 spear-phishing, supply chain campaigns target pharma, healthcare | SC Media
https://www.scmagazine.com/analysis/threat-intelligence/apt41-spear-phishing-supply-chain-campaigns-target-pharma-healthcare
MalwareBazaar | SHA256 8bac7df54648d64d943b80706db9de86ec5787d7cf3b330e860972568d100c4e
https://bazaar.abuse.ch/sample/8bac7df54648d64d943b80706db9de86ec5787d7cf3b330e860972568d100c4e/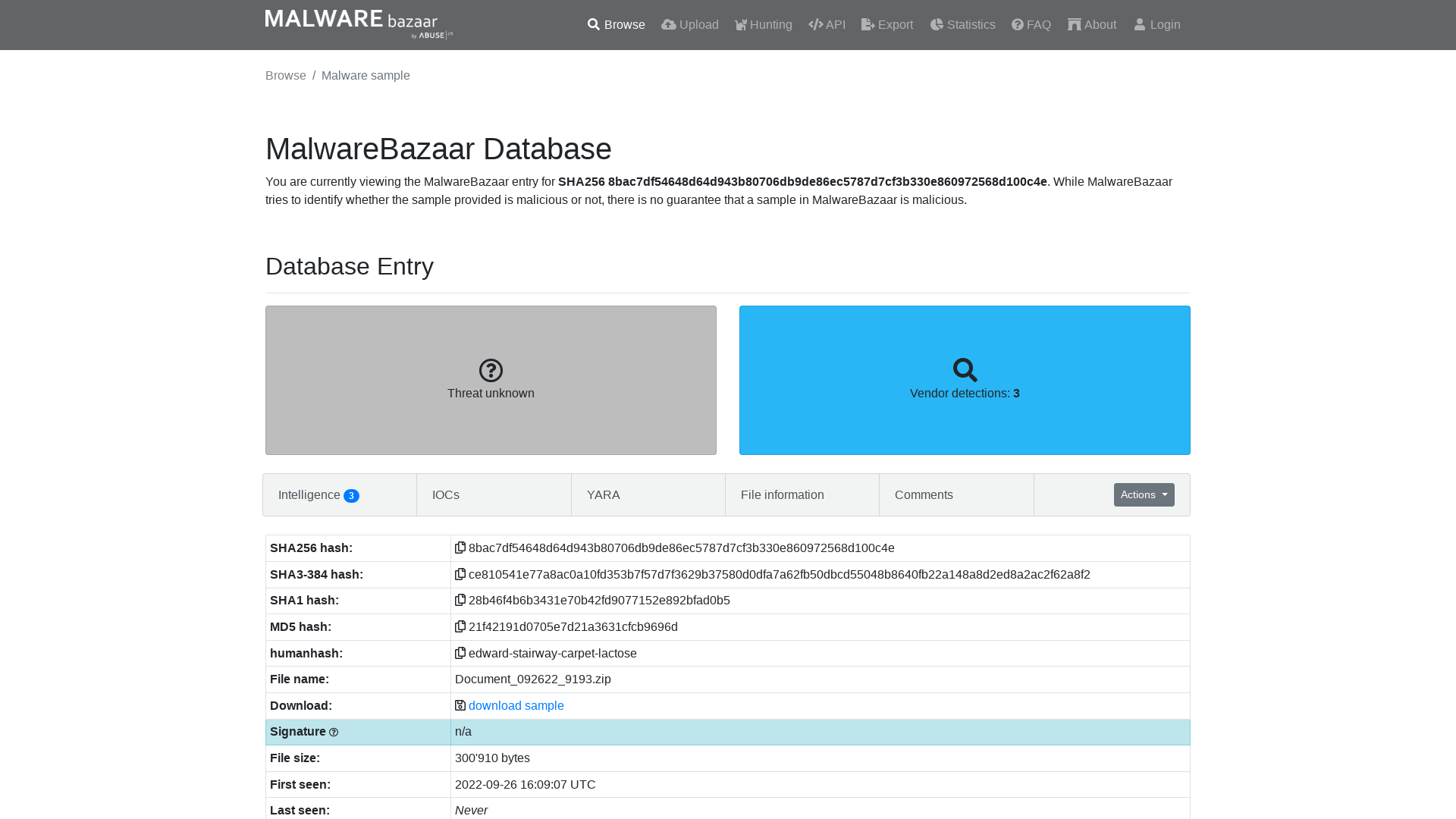
IcedID/icedID_26.09.2022.txt at main · pr0xylife/IcedID · GitHub
https://github.com/pr0xylife/IcedID/blob/main/icedID_26.09.2022.txt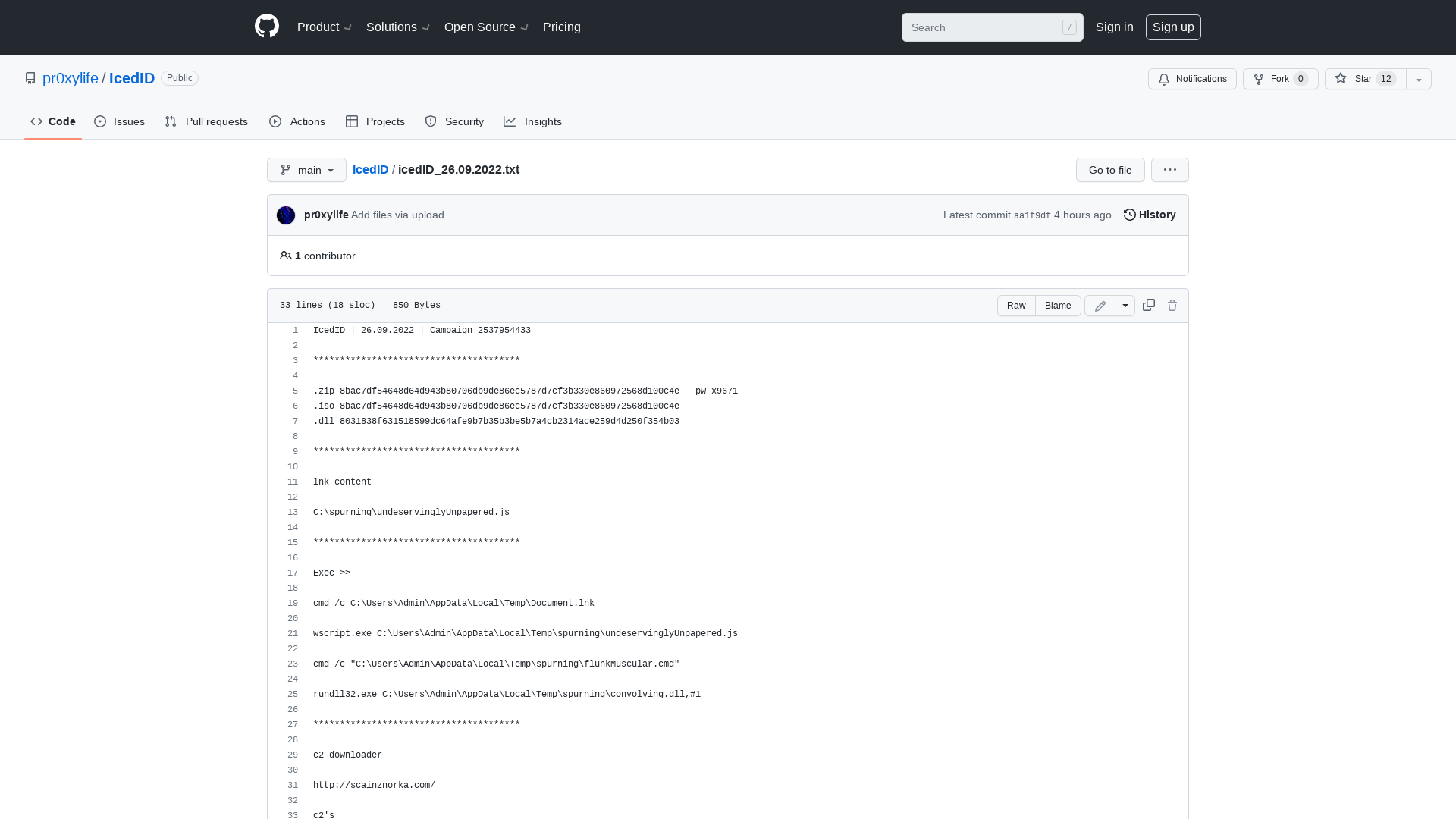
Seung Min Kim on Twitter: "MOSCOW (AP) — President Vladimir Putin grants Russian citizenship to former US security contractor Edward Snowden." / Twitter
https://twitter.com/seungminkim/status/1574430067421286401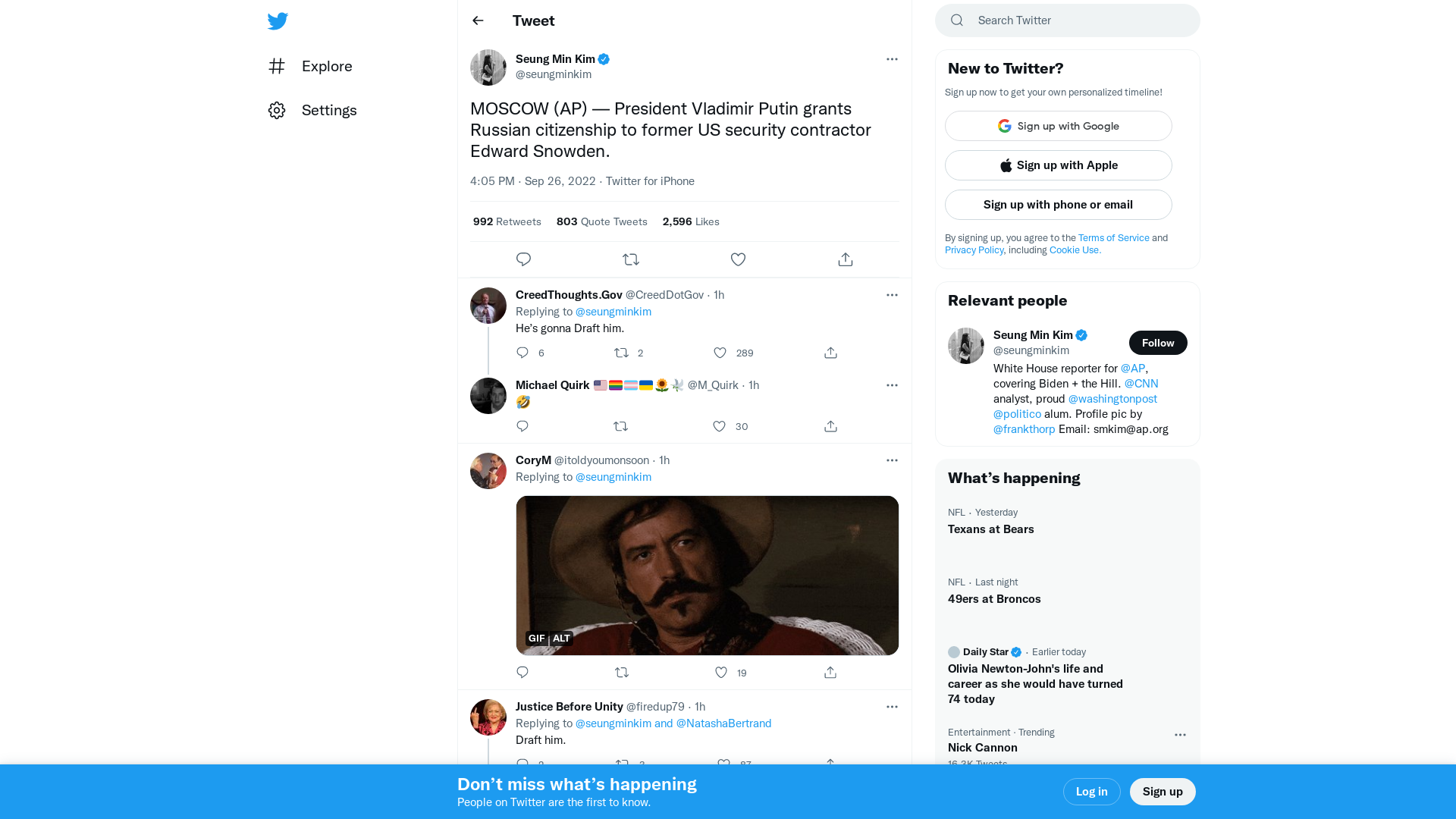
Using Sysmon to Block Unwanted Files and Send Notifications to Slack via Scheduled Task Event Filter - YouTube
https://youtu.be/J9owPmgmfvo