Add badsuccessor attack example by fulc2um · Pull Request #2010 · fortra/impacket · GitHub
https://github.com/fortra/impacket/pull/2010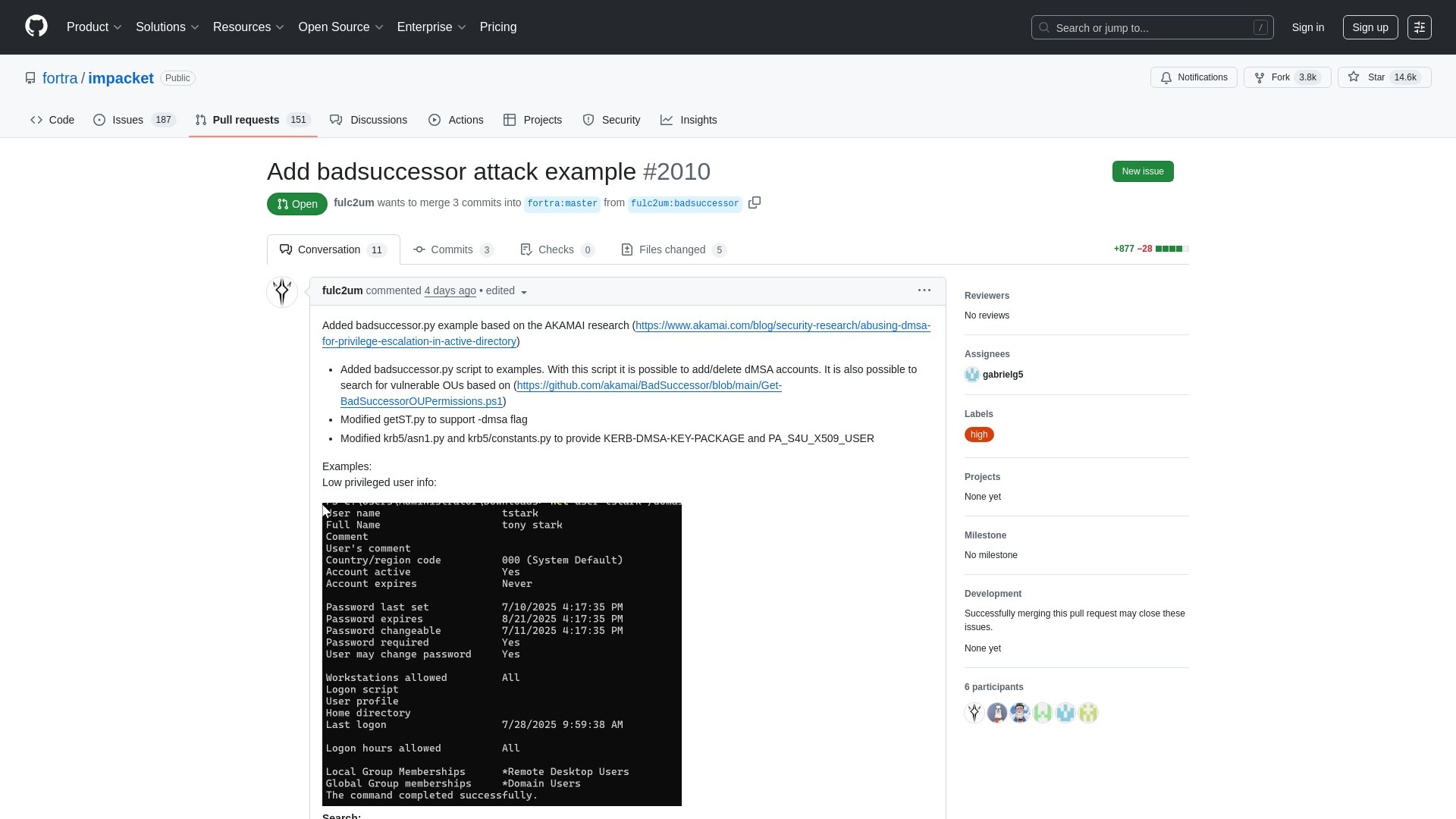
Add V8SandboxFuzzer · googleprojectzero/fuzzilli@675eccd · GitHub
https://github.com/googleprojectzero/fuzzilli/commit/675eccd6b6d0c35ea6c7df24a0a1e513cce45bb3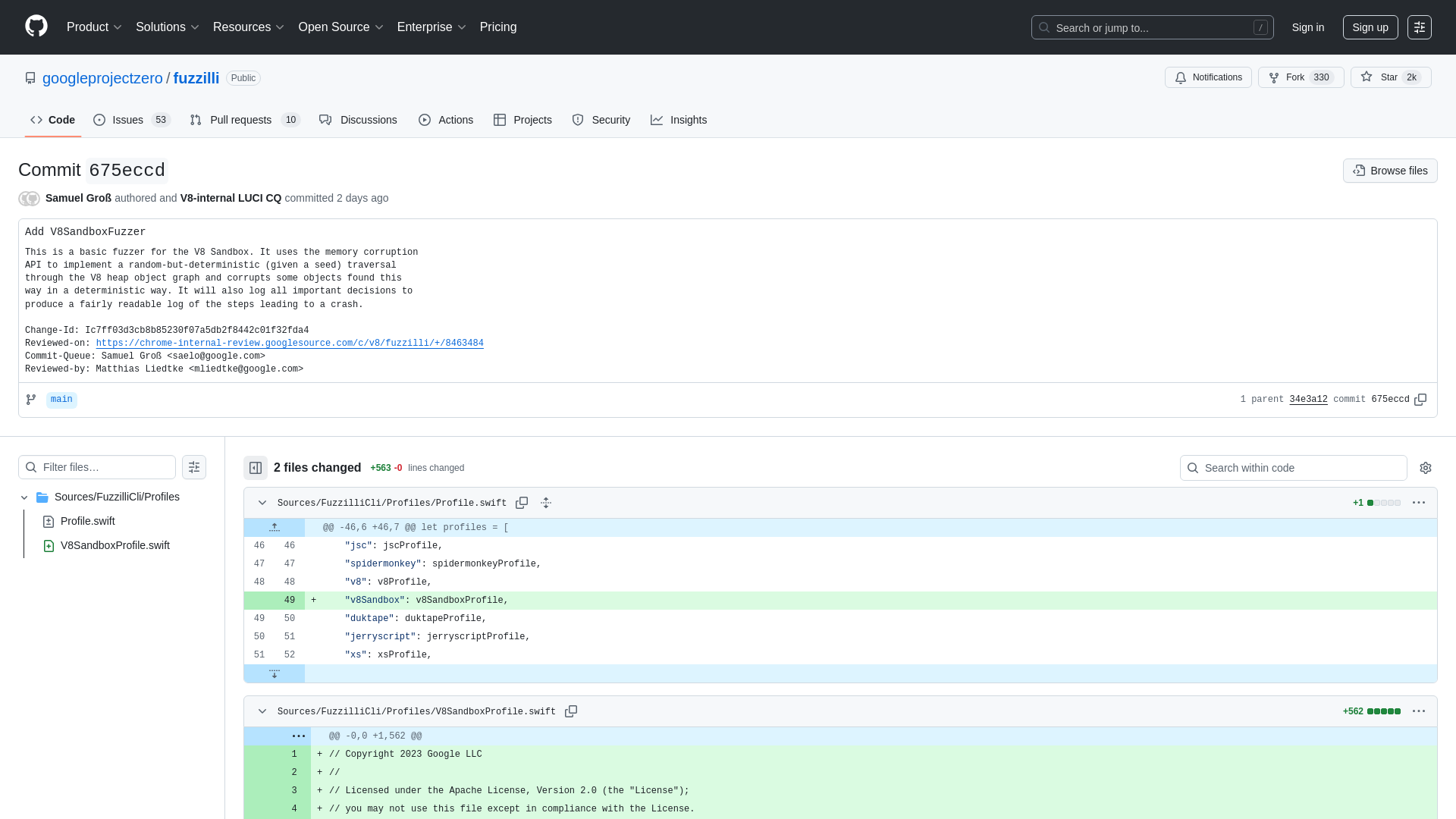
Pwn2Own hacking contest pays $1 million for WhatsApp exploit
https://www.bleepingcomputer.com/news/security/pwn2own-hacking-contest-pays-1-million-for-whatsapp-exploit/
Kali Linux can now run in Apple containers on macOS systems
https://www.bleepingcomputer.com/news/security/kali-linux-can-now-run-in-apple-containers-on-macos-systems/
Full Chain Baseband Exploits, Part 3 - taszk.io labs
https://labs.taszk.io/articles/post/full_chain_bb_part3/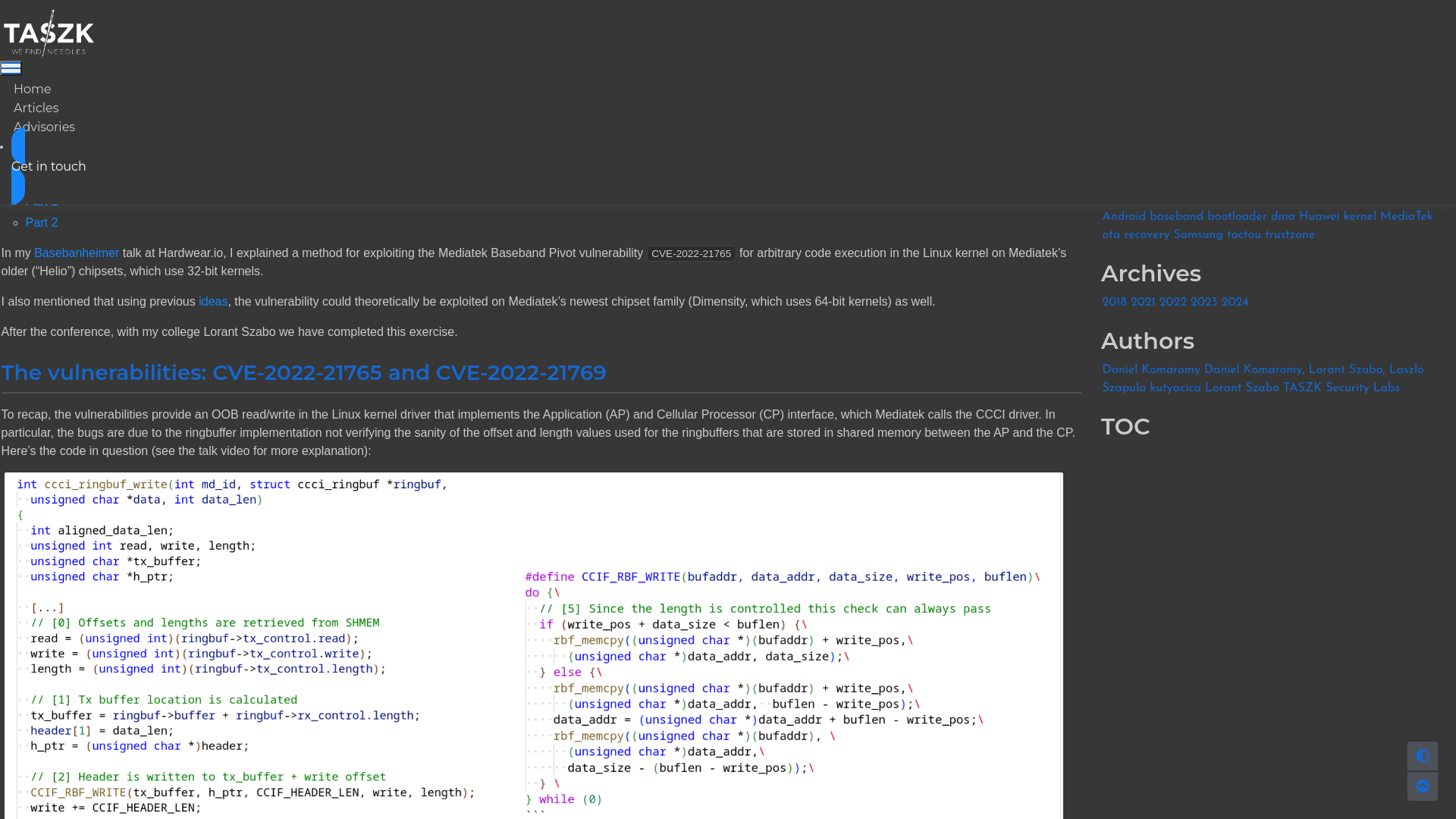
Cybercrooks use Raspberry Pi to steal ATM cash • The Register
https://go.theregister.com/feed/www.theregister.com/2025/08/01/cybercrooks_bribed_lackeys_in_physical/
Persistence Techniques That Persist
https://www.cyberark.com/resources/threat-research-blog/persistence-techniques-that-persist
Pi-hole discloses data breach triggered by WordPress plugin flaw
https://www.bleepingcomputer.com/news/security/pi-hole-discloses-data-breach-via-givewp-wordpress-plugin-flaw/
Introducing Unit 42’s Attribution Framework
https://unit42.paloaltonetworks.com/unit-42-attribution-framework/
AI-Generated Malicious npm Package Drains Solana Funds from 1,500+ Before Takedown
https://thehackernews.com/2025/08/ai-generated-malicious-npm-package.html
HTTP Cookies. Cookies are metadata used to keep track… | by Fehzan Vayani | Jul, 2025 | InfoSec Write-ups
https://infosecwriteups.com/b605fc29c058
Attackers Use Fake OAuth Apps with Tycoon Kit to Breach Microsoft 365 Accounts
https://thehackernews.com/2025/08/attackers-use-fake-oauth-apps-with.html
GitHub - mchklt/CVE-2025-30406: CVE-2025-30406 ViewState Exploit PoC
https://github.com/mchklt/CVE-2025-30406
SonicWall firewall devices hit in surge of Akira ransomware attacks
https://www.bleepingcomputer.com/news/security/surge-of-akira-ransomware-attacks-hits-sonicwall-firewall-devices/
N. Korean Hackers Used Job Lures, Cloud Account Access, and Malware to Steal Millions in Crypto
https://thehackernews.com/2025/07/n-korean-hackers-used-job-lures-cloud.html
Storm-2603 Deploys DNS-Controlled Backdoor in Warlock and LockBit Ransomware Attacks
https://thehackernews.com/2025/08/storm-2603-exploits-sharepoint-flaws-to.html
Frozen in transit: Secret Blizzard’s AiTM campaign against diplomats | Microsoft Security Blog
https://www.microsoft.com/en-us/security/blog/2025/07/31/frozen-in-transit-secret-blizzards-aitm-campaign-against-diplomats/
AI-powered Cursor IDE vulnerable to prompt-injection attacks
https://www.bleepingcomputer.com/news/security/ai-powered-cursor-ide-vulnerable-to-prompt-injection-attacks/
HTTP/1.1 Must Die
http://http1mustdie.com