Censys - Chrome Web Store
https://chromewebstore.google.com/detail/censys/cjcbocemonlaehhhpeaadmgakfofjlll
BloodHound Query Library
https://queries.specterops.io/
Entra Connect Attacker Tradecraft: Part 3 - SpecterOps
https://specterops.io/blog/2025/07/30/entra-connect-attacker-tradecraft-part-3/
Building Hacker Communities - Bug Bounty Village, getDisclosed, and the LHE Squad (Ep. 133) - YouTube
https://youtu.be/NI-eXMlXma4
CrowdStrike Investigates the Threat of Patchless AMSI Bypass Attacks
https://www.crowdstrike.com/en-us/blog/crowdstrike-investigates-threat-of-patchless-amsi-bypass-attacks/
Download the app / X
https://x.com/download
UNC2891 Breaches ATM Network via 4G Raspberry Pi, Tries CAKETAP Rootkit for Fraud
https://thehackernews.com/2025/07/unc2891-breaches-atm-network-via-4g.html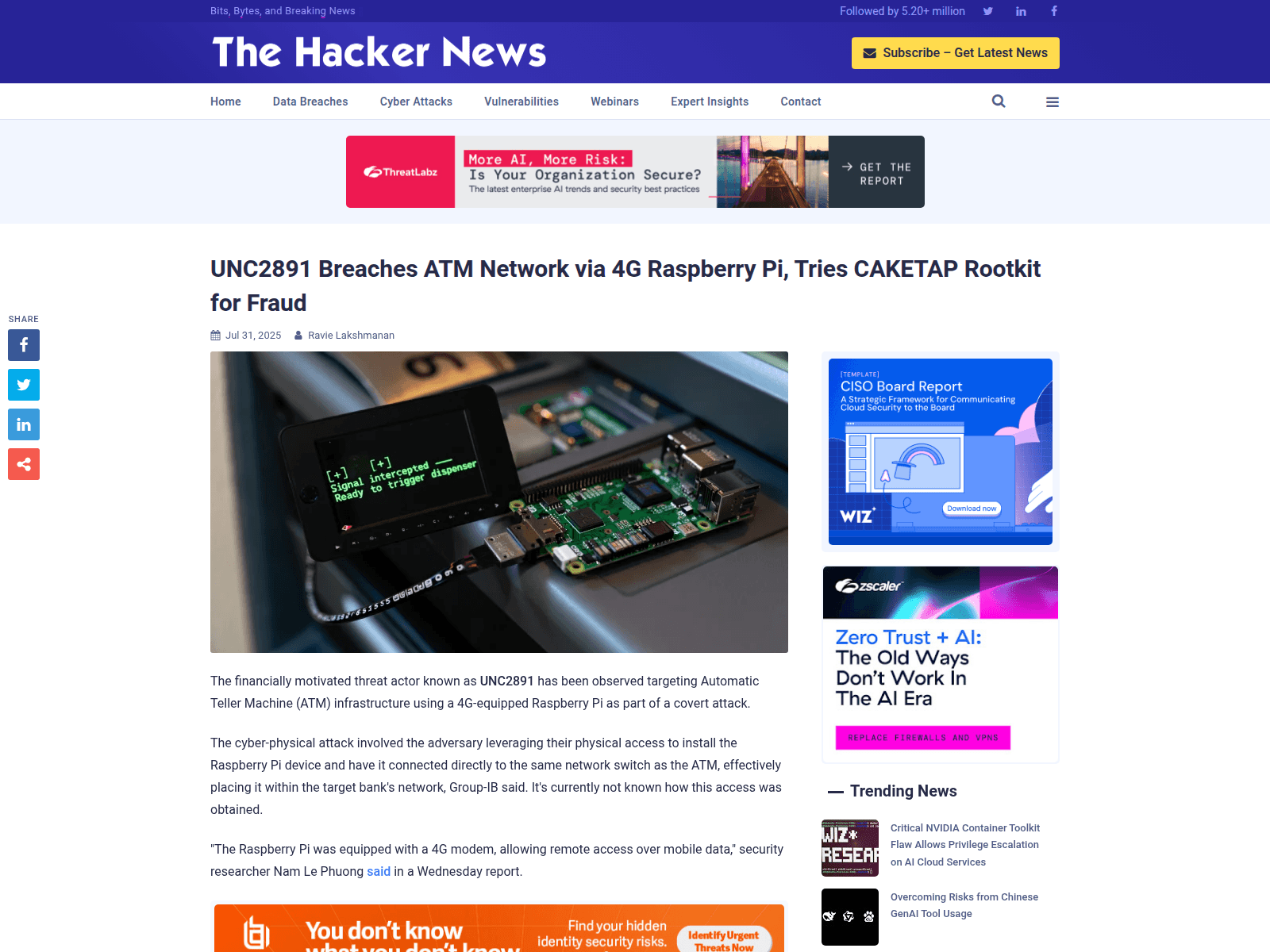
Full Chain Baseband Exploits, Part 1 - taszk.io labs
https://labs.taszk.io/articles/post/full_chain_bb_part1/
[CVE-2025-37752] Two Bytes Of Madness: Pwning The Linux Kernel With A 0x0000 Written 262636 Bytes Out-Of-Bounds
https://syst3mfailure.io/two-bytes-of-madness/![[CVE-2025-37752] Two Bytes Of Madness: Pwning The Linux Kernel With A 0x0000 Written 262636 Bytes Out-Of-Bounds](/image/screenshot/48714df2a75b4f890a24e523e3709c54.png)
Microsoft to disable Excel workbook links to blocked file types
https://www.bleepingcomputer.com/news/microsoft/microsoft-to-disable-external-workbook-links-to-blocked-file-types/
Frozen in transit: Secret Blizzard’s AiTM campaign against diplomats | Microsoft Security Blog
https://www.microsoft.com/en-us/security/blog/2025/07/31/frozen-in-transit-secret-blizzards-aitm-campaign-against-diplomats/
CISA open-sources Thorium platform for malware, forensic analysis
https://www.bleepingcomputer.com/news/security/cisa-open-sources-thorium-platform-for-malware-forensic-analysis/
Hackers target Python devs in phishing attacks using fake PyPI site
https://www.bleepingcomputer.com/news/security/hackers-target-python-devs-in-phishing-attacks-using-fake-pypi-site/
Hackers Exploit Critical WordPress Theme Flaw to Hijack Sites via Remote Plugin Install
https://thehackernews.com/2025/07/hackers-exploit-critical-wordpress.html
Microsoft now pays up to $40,000 for some .NET vulnerabilities
https://www.bleepingcomputer.com/news/microsoft/microsoft-now-pays-up-to-40-000-for-some-net-vulnerabilities/
Spikes in malicious activity precede new security flaws in 80% of cases
https://www.bleepingcomputer.com/news/security/spikes-in-malicious-activity-precede-new-cves-in-80-percent-of-cases/
Beijing asks Nvidia about backdoors in China-bound AI chips • The Register
https://go.theregister.com/feed/www.theregister.com/2025/07/31/beijing_nvidia_backdoors/
CrushFTP RCE Explained
https://pwn.guide/free/web/crushftp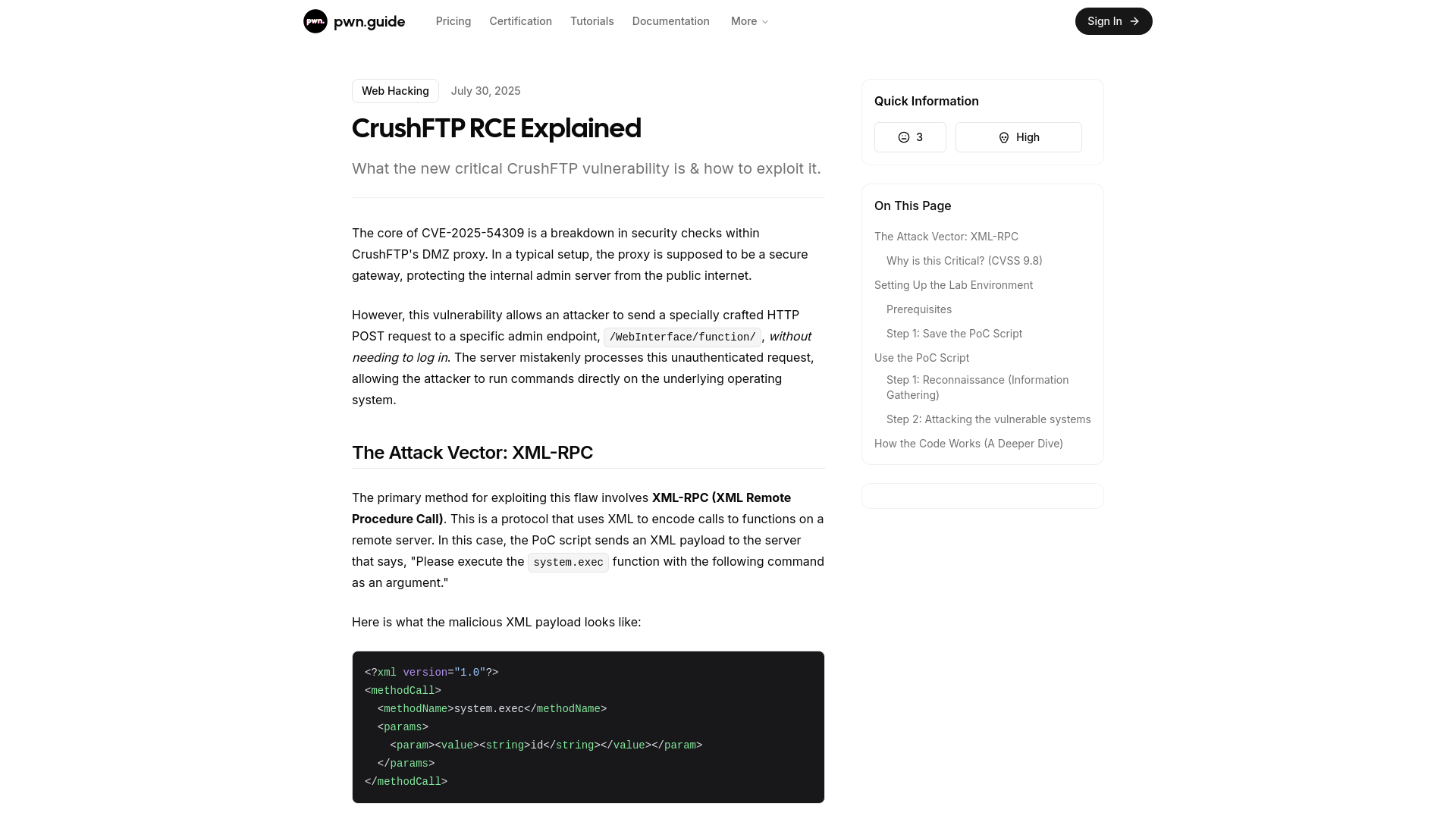
Kali Linux can now run in Apple containers on macOS systems
https://www.bleepingcomputer.com/news/security/kali-linux-can-now-run-in-apple-containers-on-macos-systems/
Proton launches free standalone cross-platform Authenticator app
https://www.bleepingcomputer.com/news/security/proton-launches-free-standalone-cross-platform-authenticator-app/
Microsoft: Russian hackers use ISP access to hack embassies in AiTM attacks
https://www.bleepingcomputer.com/news/security/microsoft-russian-hackers-use-isp-access-to-hack-embassies-in-aitm-attacks/
Experts Detect Multi-Layer Redirect Tactic Used to Steal Microsoft 365 Login Credentials
https://thehackernews.com/2025/07/experts-detect-multi-layer-redirect.html
UNC2891 Bank Heist: Physical ATM Backdoor & Linux Forensic Evasion Evasion | Group-IB Blog
https://www.group-ib.com/blog/unc2891-bank-heist/