1 bug, $50,000+ in bounties, how Zendesk intentionally left a backdoor in hundreds of Fortune 500 companies · GitHub
https://gist.github.com/hackermondev/68ec8ed145fcee49d2f5e2b9d2cf2e52
OpenAI confirms threat actors use ChatGPT to write malware
https://www.bleepingcomputer.com/news/security/openai-confirms-threat-actors-use-chatgpt-to-write-malware/
Microsoft's guidance to help mitigate Kerberoasting | Microsoft Security Blog
https://www.microsoft.com/en-us/security/blog/2024/10/11/microsofts-guidance-to-help-mitigate-kerberoasting/
Hacked Robot Vacuums Across the U.S. Started Yelling Slurs
https://gizmodo.com/hacked-robot-vacuums-across-the-us-started-yelling-slurs-2000511013
Microsoft deprecates PPTP and L2TP VPN protocols in Windows Server
https://www.bleepingcomputer.com/news/microsoft/microsoft-deprecates-pptp-and-l2tp-vpn-protocols-in-windows-server/
New Release: Tails 6.8.1 | The Tor Project
https://blog.torproject.org/new-release-tails-6-8-1/
A cyber attack hit Iranian government sites and nuclear facilities
https://securityaffairs.com/169693/cyber-warfare-2/cyber-attack-hit-iranian-nuclear-facilities.html
Hackers Advertise Stolen Verizon Push-to-Talk ‘Call Logs’
https://www.404media.co/hackers-advertise-stolen-verizon-push-to-talk-call-logs/
Black Hat - YouTube
https://m.youtube.com/@BlackHatOfficialYT/videos
Downgrade attack: a story as old as Windows… – AaLl86 Security
https://www.andrea-allievi.com/blog/downgrade-attack-a-story-as-old-as-windows/
FBI Creates Fake Cryptocurrency to Expose Widespread Crypto Market Manipulation
https://thehackernews.com/2024/10/fbi-creates-fake-cryptocurrency-to.html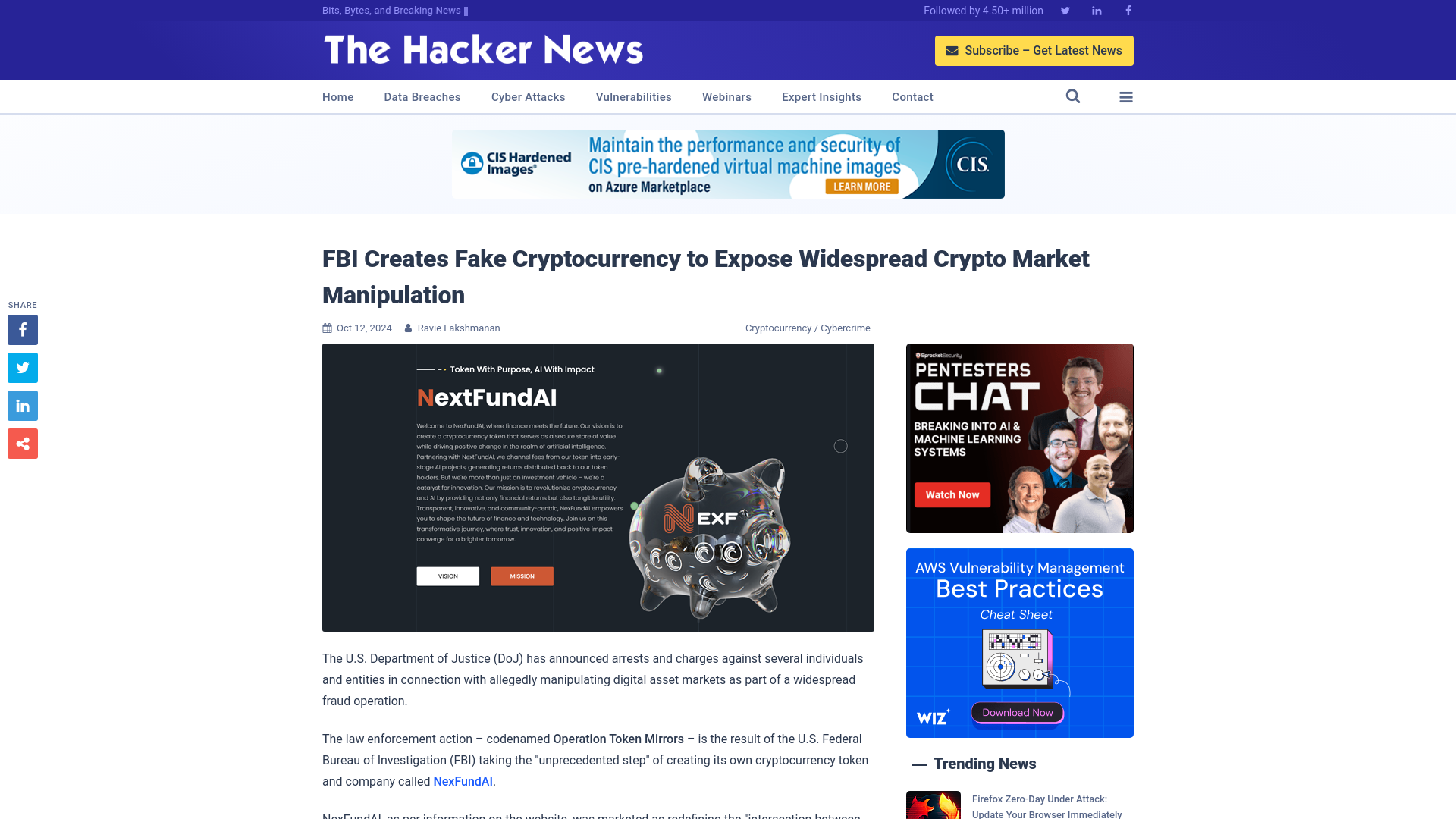
Windows Drivers Reverse Engineering Methodology - VoidSec
https://voidsec.com/windows-drivers-reverse-engineering-methodology/