Company Behind Major Social Security Number Leak Files for Bankruptcy | PCMag
https://www.pcmag.com/news/company-behind-major-social-security-number-leak-files-for-bankruptcy
Process Injection Using Windows Thread Pools | Safebreach
https://www.safebreach.com/blog/process-injection-using-windows-thread-pools/
Lab: Bypassing access controls using email address parsing discrepancies | Web Security Academy
https://portswigger.net/web-security/logic-flaws/examples/lab-logic-flaws-bypassing-access-controls-using-email-address-parsing-discrepancies
Bohemia and Cannabia Dark Web Markets Taken Down After Joint Police Operation
https://thehackernews.com/2024/10/bohemia-and-cannabia-dark-web-markets.html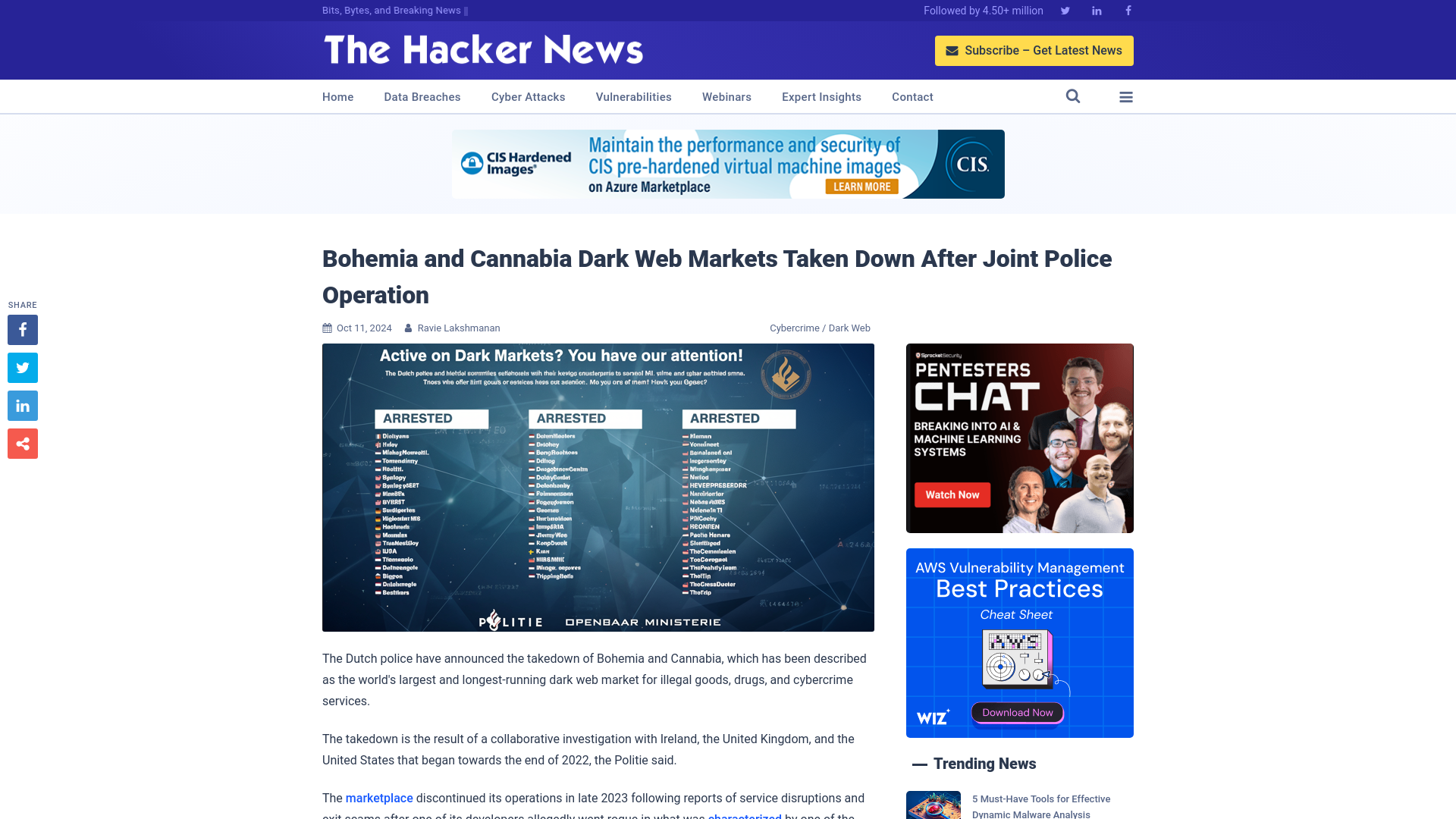
GitHub - doyensec/CSPTPlayground: CSPTPlayground is an open-source playground to find and exploit Client-Side Path Traversal (CSPT).
https://github.com/doyensec/CSPTPlayground
CISA: Hackers abuse F5 BIG-IP cookies to map internal servers
https://www.bleepingcomputer.com/news/security/cisa-hackers-abuse-f5-big-ip-cookies-to-map-network-devices/
Iran and China-linked actors used ChatGPT for preparing attacks
https://securityaffairs.com/169659/apt/openai-reports-iran-and-china-linked-apt-used-chatgpt.html
I’m Running Out of Ways to Explain How Bad This Is - The Atlantic
https://www.theatlantic.com/technology/archive/2024/10/hurricane-milton-conspiracies-misinformation/680221/?gift=bQgJMMVzeo8RHHcE1_KM0QW0K3DKS019CAwkgCJs0j8
CVE-2024-32987 - Security Update Guide - Microsoft - Microsoft SharePoint Server Information Disclosure Vulnerability
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-32987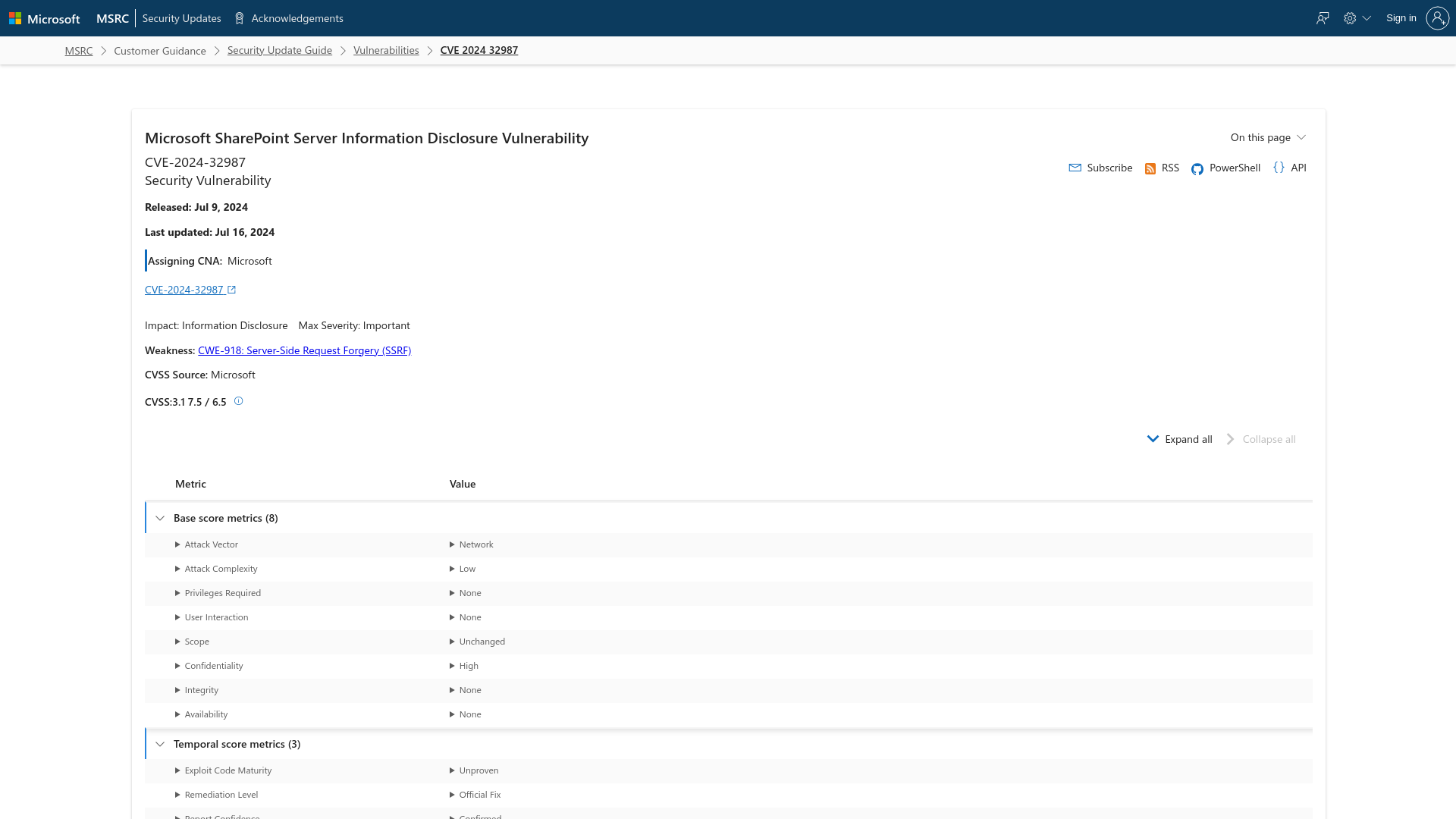
Release Volatility 3 2.8.0 · volatilityfoundation/volatility3 · GitHub
https://github.com/volatilityfoundation/volatility3/releases/tag/v2.8.0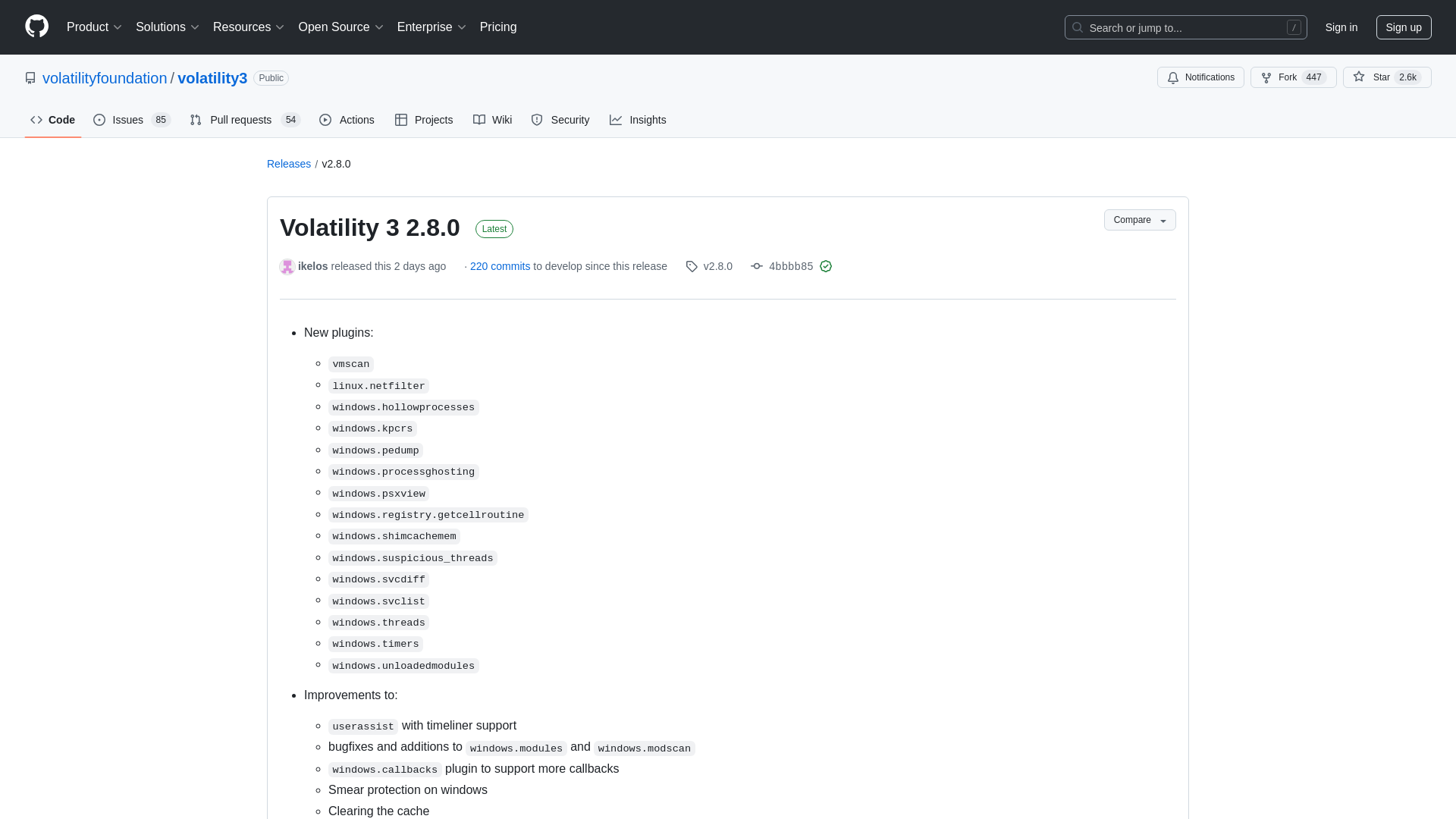
EU adopts Cyber Resilience Act to secure connected products - Help Net Security
https://www.helpnetsecurity.com/2024/10/11/eu-adopts-cyber-resilience-act-to-secure-connected-products/
GitHub, Telegram Bots, and QR Codes Abused in New Wave of Phishing Attacks
https://thehackernews.com/2024/10/github-telegram-bots-and-qr-codes.html
Beyond the good ol' LaunchAgents - 34 - launchd embedded plist · theevilbit blog
https://theevilbit.github.io/beyond/beyond_0034/
Lawmakers press agencies, telecoms for more details on Salt Typhoon hacks | CyberScoop
https://cyberscoop.com/congress-salt-typhoon-hack-telecoms-att-lumen-verizon/
CVE-2024-9465 (CVSS 9.2) SQLi Flaw in Palo Alto Expedition Revealed: Full Exploit & PoC Published
https://securityonline.info/cve-2024-9465-cvss-9-2-sqli-flaw-in-palo-alto-expedition-revealed-full-exploit-poc-published/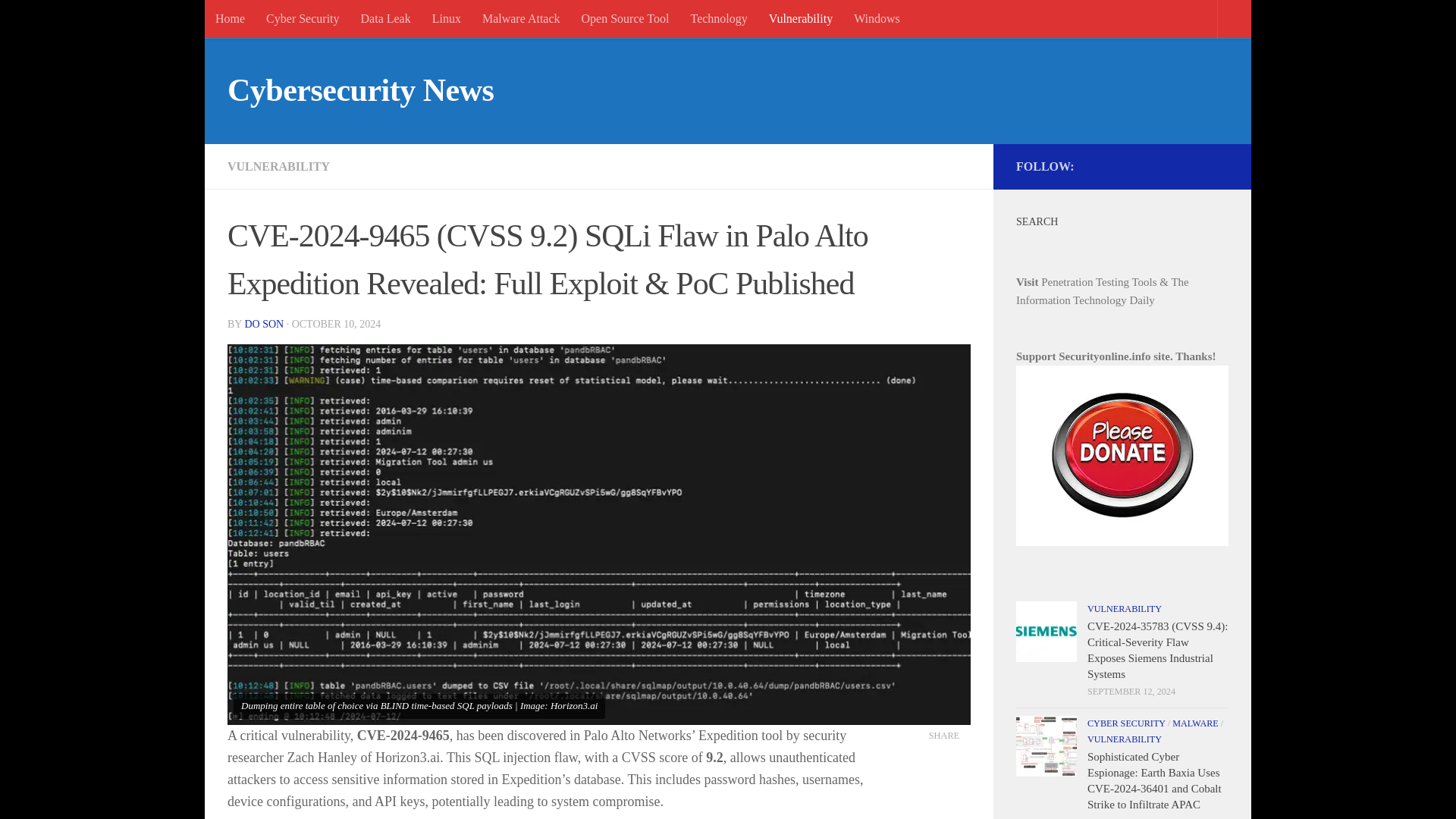
Three-Headed Potato Dog – Compass Security Blog
https://blog.compass-security.com/2024/09/three-headed-potato-dog/
Casio confirms customer data stolen in a ransomware attack
https://www.bleepingcomputer.com/news/security/casio-confirms-customer-data-stolen-in-a-ransomware-attack/