Implementing Kernel Object Type (Part 2) – Pavel Yosifovich
https://scorpiosoftware.net/2024/08/31/implementing-kernel-object-type-part-2/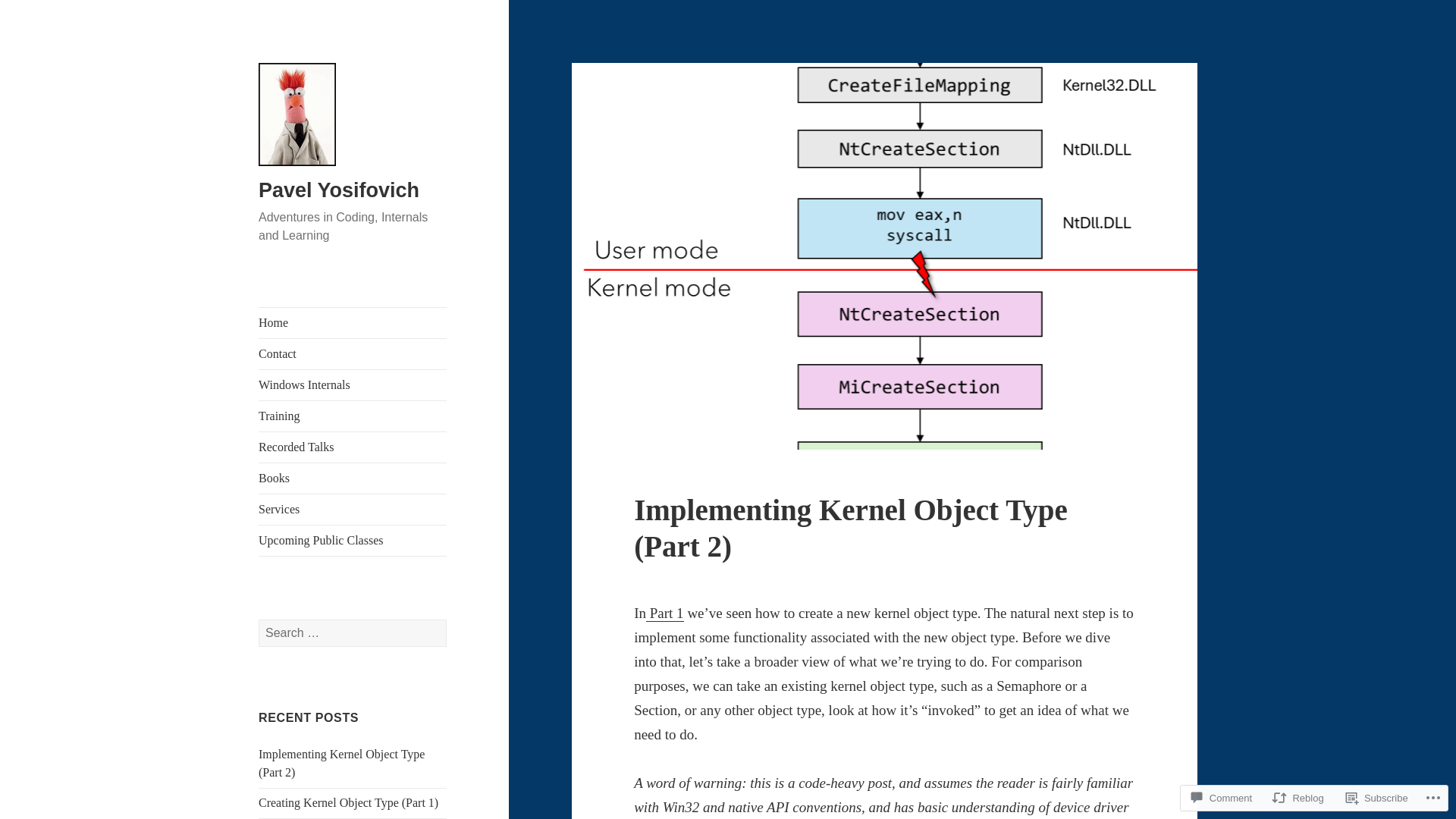
North Korean threat actor Citrine Sleet exploiting Chromium zero-day | Microsoft Security Blog
https://www.microsoft.com/en-us/security/blog/2024/08/30/north-korean-threat-actor-citrine-sleet-exploiting-chromium-zero-day/
ICS CTF 2024
https://ctf.cisaicsctf.com/
Docker-OSX image used for security research hit by Apple DMCA takedown
https://www.bleepingcomputer.com/news/security/docker-osx-image-used-for-security-research-hit-by-apple-dmca-takedown/
GitHub - deh00ni/NtDumpBOF
https://github.com/deh00ni/NtDumpBOF
GitHub - nevesnunes/z80-sans: OpenType font that disassembles Z80 instructions
https://github.com/nevesnunes/z80-sans
VU#455367 - Insecure Platform Key (PK) used in UEFI system firmware signature
https://kb.cert.org/vuls/id/455367
Microsoft Says North Korean Cryptocurrency Thieves Behind Chrome Zero-Day - SecurityWeek
https://www.securityweek.com/microsoft-says-north-korean-cryptocurrency-thieves-behind-chrome-zero-day/
North Korean Hackers Deploy FudModule Rootkit via Chrome Zero-Day Exploit
https://thehackernews.com/2024/08/north-korean-hackers-deploy-fudmodule.html
Researcher sued for sharing data stolen by ransomware with media
https://www.bleepingcomputer.com/news/security/researcher-sued-for-sharing-data-stolen-by-ransomware-with-media/
io (@iok) / X
https://twitter.com/iok
GitHub comments abused to spread Lumma Stealer malware as fake fixes
https://www.bleepingcomputer.com/news/security/github-comments-abused-to-spread-lumma-stealer-malware-as-fake-fixes/
Obfuscated PowerShell leads to Lumma C2 Stealer | Ontinue
https://www.ontinue.com/resource/obfuscated-powershell-leads-to-lumma-c2-stealer/