State-backed attackers and commercial surveillance vendors repeatedly use the same exploits
https://blog.google/threat-analysis-group/state-backed-attackers-and-commercial-surveillance-vendors-repeatedly-use-the-same-exploits/
Researcher sued for sharing data stolen by ransomware with media
https://www.bleepingcomputer.com/news/security/researcher-sued-for-sharing-data-stolen-by-ransomware-with-media/
Auditoor : Read better
http://auditoor.xyz
North Korean hackers exploit Chrome zero-day to deploy rootkit
https://www.bleepingcomputer.com/news/security/north-korean-hackers-exploit-chrome-zero-day-to-deploy-rootkit/
Bypassing airport security via SQL injection
https://ian.sh/tsa
io (@iok) / X
https://twitter.com/iok
New Voldemort malware abuses Google Sheets to store stolen data
https://www.bleepingcomputer.com/news/security/new-voldemort-malware-abuses-google-sheets-to-store-stolen-data/
Iranian Hackers Set Up New Network to Target U.S. Political Campaigns
https://thehackernews.com/2024/08/iranian-hackers-set-up-new-network-to.html
SANS Institute Unveils Critical Infrastructure Strategy Guide for 2024: A Call to Action for Securing ICS/OT Environments
https://thehackernews.com/2024/08/sans-institute-unveils-critical.html
[Linux Kernel Exploitation 0x0] Debugging the Kernel with QEMU
https://blog.k3170makan.com/2020/11/linux-kernel-exploitation-0x0-debugging.html![[Linux Kernel Exploitation 0x0] Debugging the Kernel with QEMU](/image/screenshot/de98caf8aeee872ce15b3aaa836d9fa9.png)
Russia-linked APT29 reused iOS and Chrome exploits previously developed by NSO Group and Intellexa
https://securityaffairs.com/167797/apt/apt29-nso-group-and-intellexa-mobile-exploits.html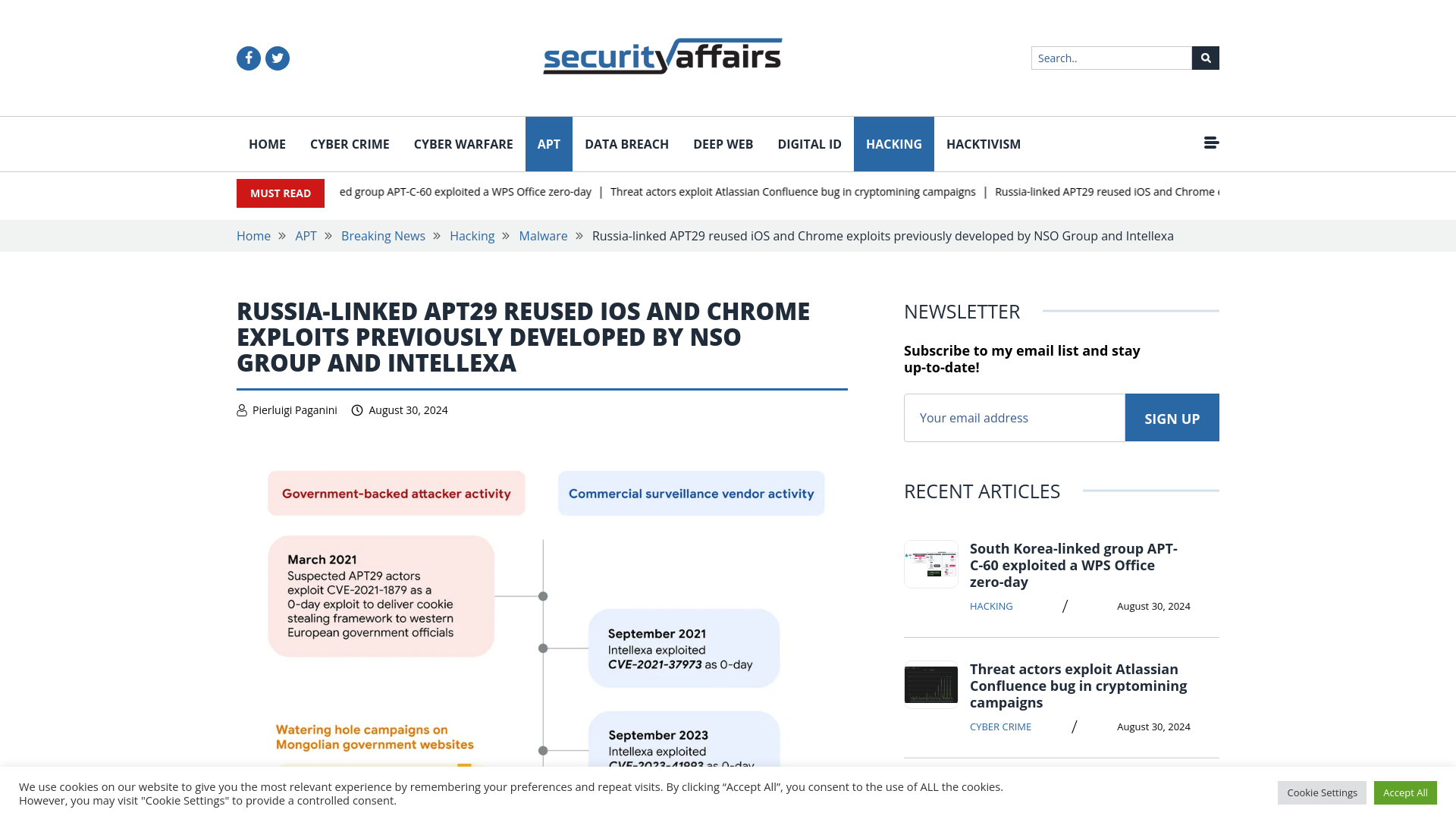
California Advances Landmark Legislation to Regulate Large AI Models - SecurityWeek
https://www.securityweek.com/california-advances-landmark-legislation-to-regulate-large-ai-models/
Critical Flaws in Progress Software WhatsUp Gold Expose Systems to Full Compromise - SecurityWeek
https://www.securityweek.com/critical-flaws-in-progress-software-whatsup-gold-expose-systems-to-full-compromise/
US Government Issues Advisory on Ransomware Group Blamed for Halliburton Cyberattack - SecurityWeek
https://www.securityweek.com/us-government-issues-advisory-on-ransomware-group-blamed-for-halliburton-cyberattack/
North Korean Hackers Target Developers with Malicious npm Packages
https://thehackernews.com/2024/08/north-korean-hackers-target-developers.html
North Korean threat actor Citrine Sleet exploiting Chromium zero-day | Microsoft Security Blog
https://www.microsoft.com/en-us/security/blog/2024/08/30/north-korean-threat-actor-citrine-sleet-exploiting-chromium-zero-day/
Threat actors exploit Atlassian Confluence bug in cryptomining campaigns
https://securityaffairs.com/167813/cyber-crime/atlassian-confluence-data-center-confluence-server-cryptocurrency-mining-campaigns.html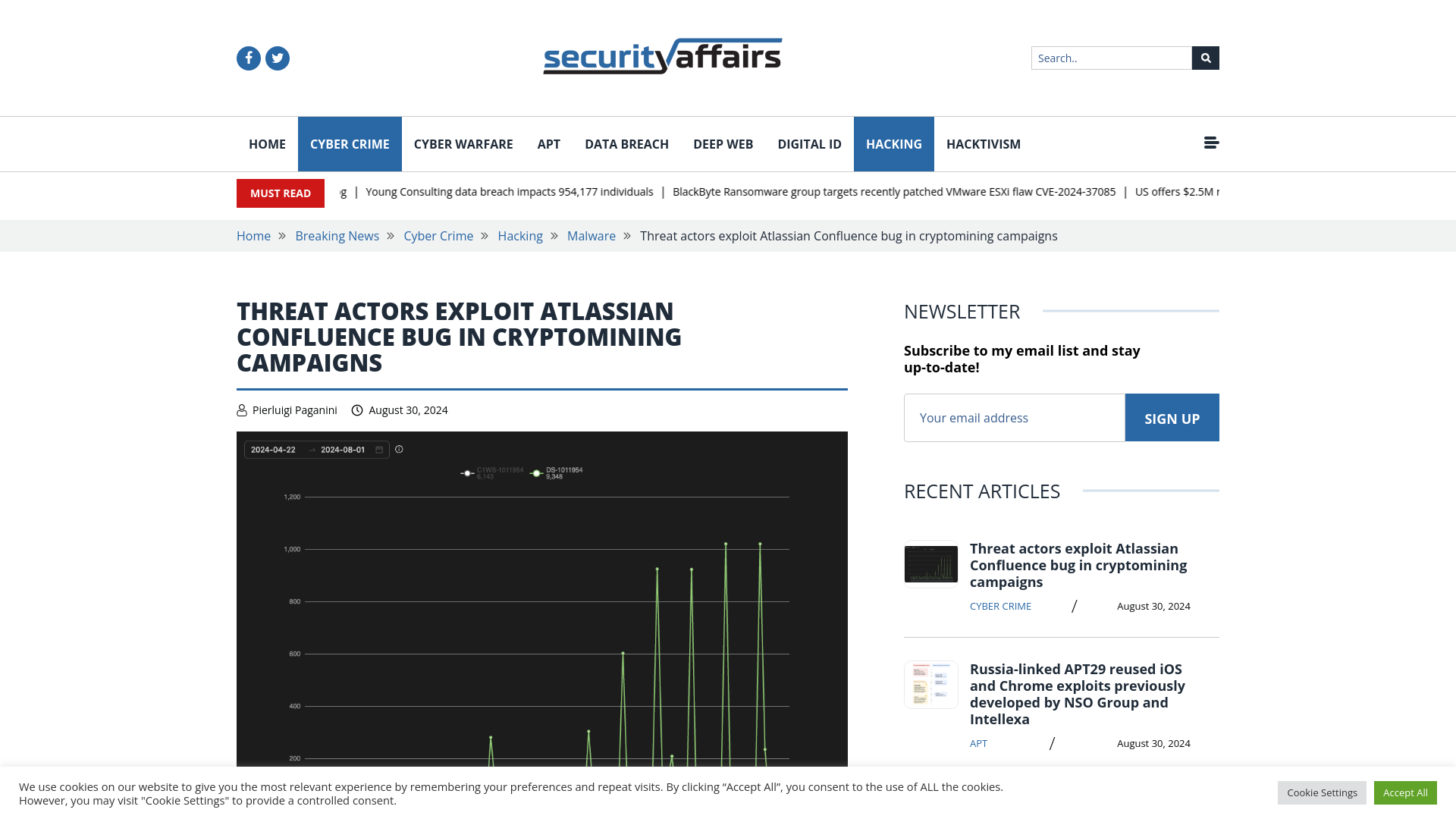
New Cyberattack Targets Chinese-Speaking Businesses with Cobalt Strike Payloads
https://thehackernews.com/2024/08/new-cyberattack-targets-chinese.html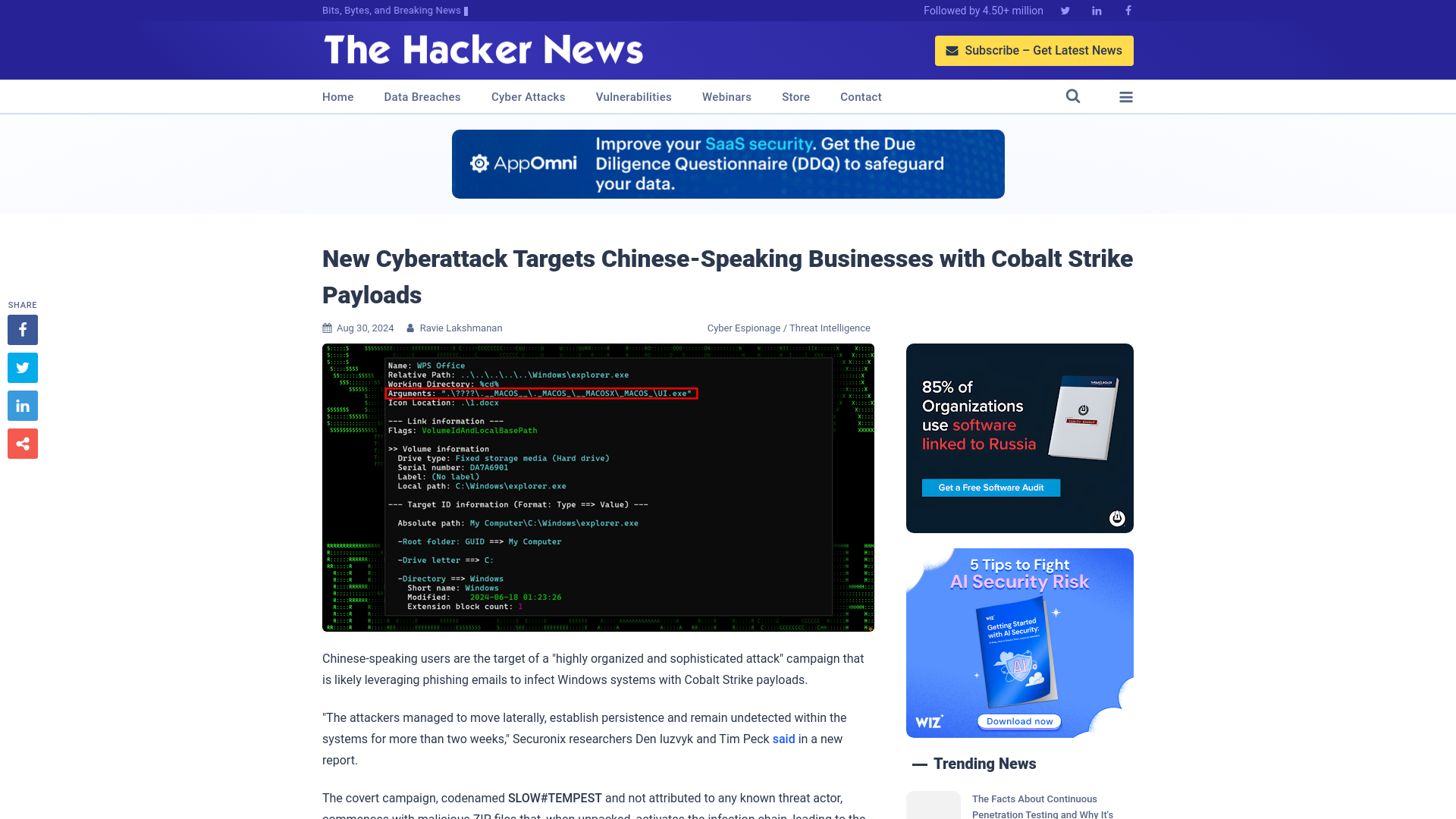
Changes to the OSCP – OffSec Support Portal
https://help.offsec.com/hc/en-us/articles/29840452210580-Changes-to-the-OSCP
Cicada 3301 - Ransomware-as-a-Service - Technical Analysis
https://www.truesec.com/hub/blog/dissecting-the-cicada
Pwning a Brother labelmaker, for fun and interop!
https://sdomi.pl/weblog/20-pwning-a-labelmaker/
Hacking the Hackers: Taking Down a Live Botnet | by Jacob Masse | Aug, 2024 | Medium
https://jacobmasse.medium.com/hacking-the-hackers-taking-down-a-live-botnet-28c1fb703153
Cyberattackers Exploit Google Sheets for Malware Control in Likely Espionage Campaign
https://thehackernews.com/2024/08/cyberattackers-exploit-google-sheets.html
Metasploit Weekly Wrap-Up 08/30/2024 | Rapid7 Blog
https://www.rapid7.com/blog/post/2024/08/30/metasploit-weekly-wrap-up-08-30-2024/
CTO at NCSC Summary: week ending September 1st
https://ctoatncsc.substack.com/p/cto-at-ncsc-summary-week-ending-september