GitHub - sinsinology/CVE-2024-29849: Veeam Backup Enterprise Manager Authentication Bypass (CVE-2024-29849)
https://github.com/sinsinology/CVE-2024-29849
Cylance confirms data breach linked to 'third-party' platform
https://www.bleepingcomputer.com/news/security/cylance-confirms-data-breach-linked-to-third-party-platform/
IcedID Brings ScreenConnect and CSharp Streamer to ALPHV Ransomware Deployment – The DFIR Report
https://thedfirreport.com/2024/06/10/icedid-brings-screenconnect-and-csharp-streamer-to-alphv-ransomware-deployment/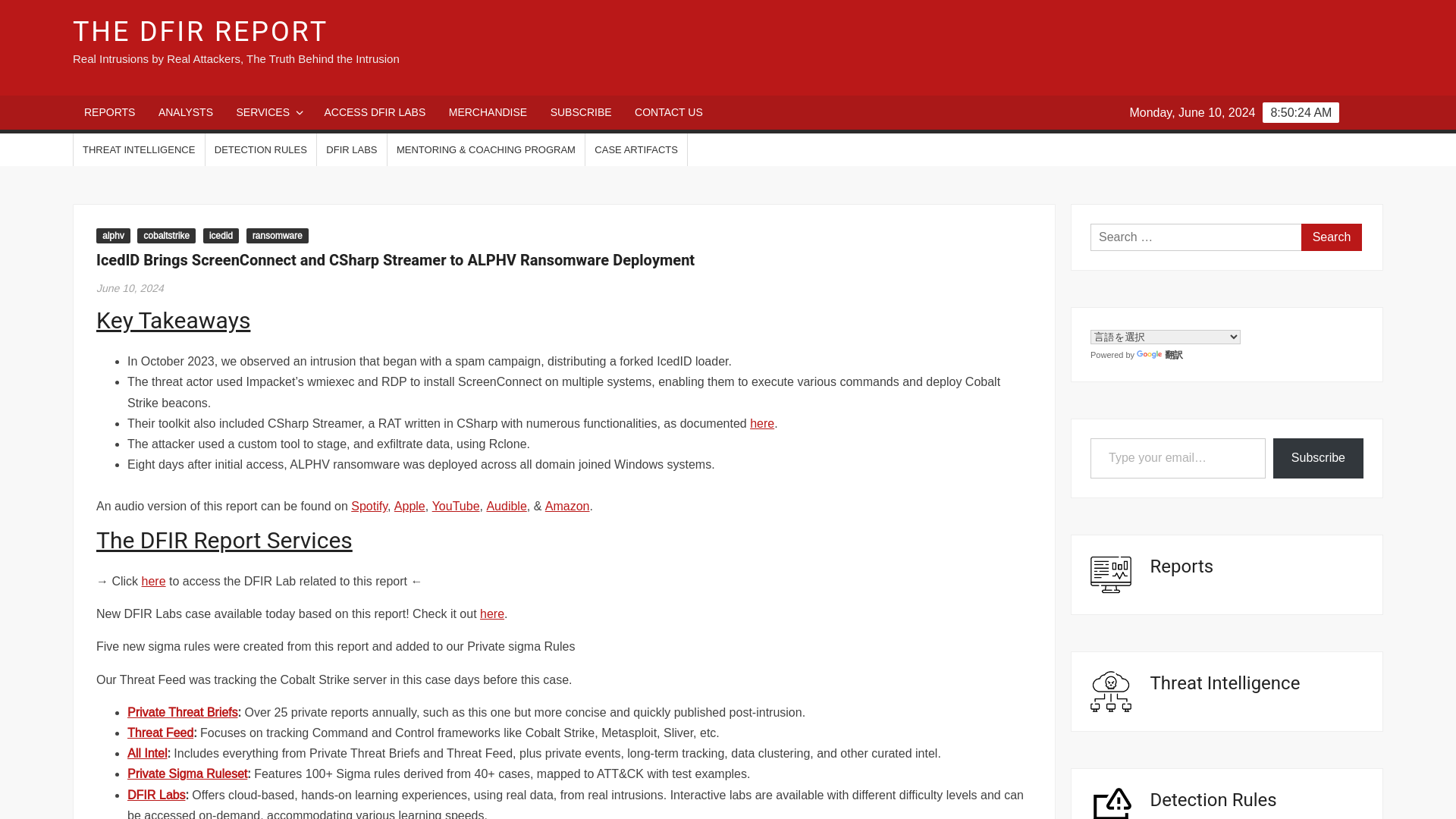
Black Hat USA 2024 | Scholarships
https://www.blackhat.com/us-24/scholarships.html
London hospitals face blood shortage after Synnovis ransomware attack
https://www.bleepingcomputer.com/news/security/london-hospitals-face-blood-shortage-after-synnovis-ransomware-attack/
Malicious VSCode extensions with millions of installs discovered
https://www.bleepingcomputer.com/news/security/malicious-vscode-extensions-with-millions-of-installs-discovered/
23andMe data breach under investigation in UK and Canada
https://www.bleepingcomputer.com/news/security/23andme-data-breach-under-investigation-in-uk-and-canada/
Impacket AES Key Calculator · GitHub
https://gist.github.com/dadevel/1fdb0dc2afc470140c211236e9277fc9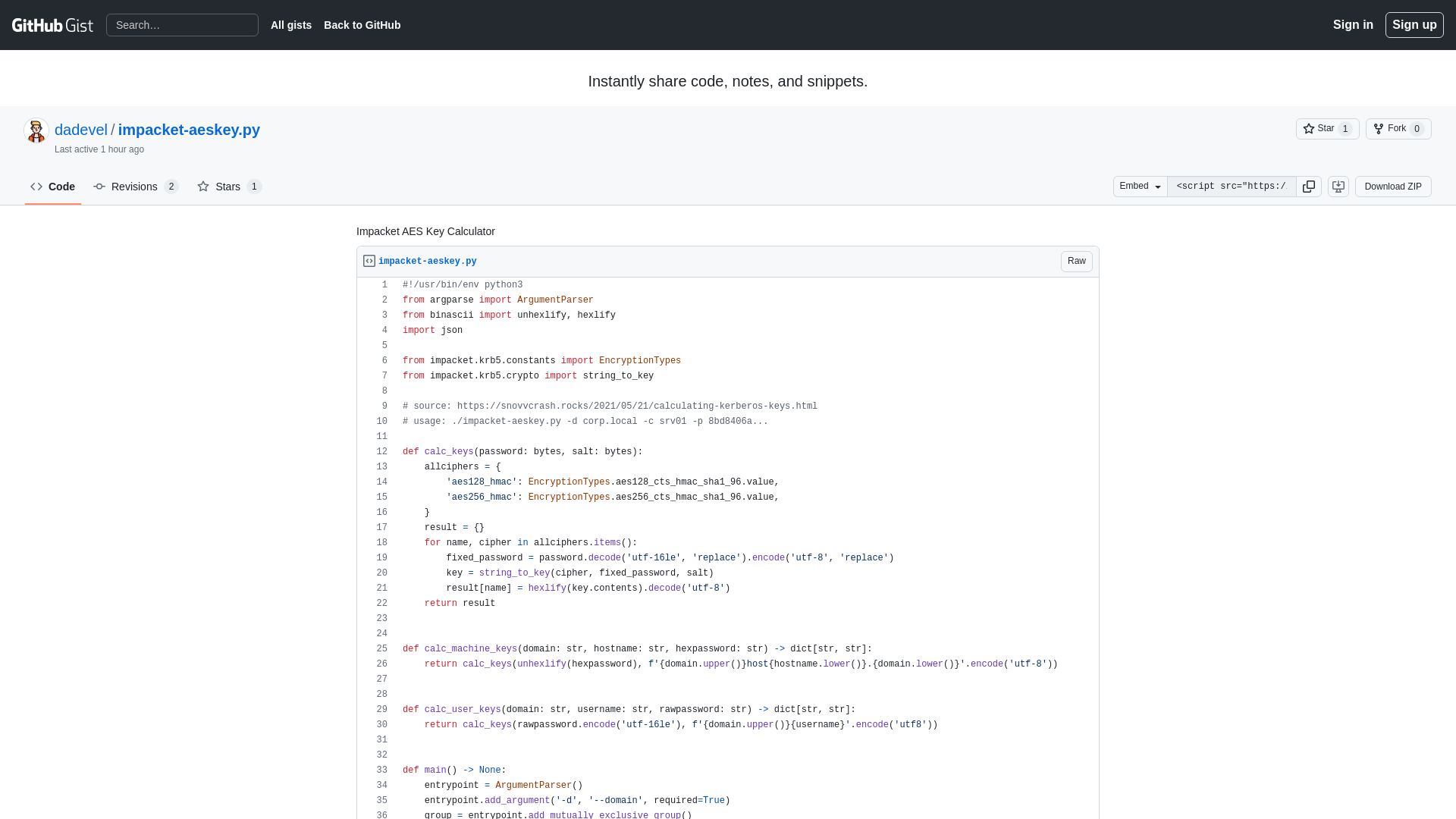
Bypassing Veeam Authentication CVE-2024-29849
https://summoning.team/blog/veeam-enterprise-manager-cve-2024-29849-auth-bypass/
Critical PyTorch Vulnerability Can Lead to Sensitive AI Data Theft - SecurityWeek
https://www.securityweek.com/critical-pytorch-vulnerability-can-lead-to-sensitive-ai-data-theft/
GitHub - elkokc/reflector: Burp plugin able to find reflected XSS on page in real-time while browsing on site
https://github.com/elkokc/reflector
GitHub - AlteredSecurity/Disable-TamperProtection: A POC to disable TamperProtection and other Defender / MDE components
https://github.com/AlteredSecurity/Disable-TamperProtection
Two arrested in UK over fake cell tower smishing campaign • The Register
http://dlvr.it/T84SmV
Exploit for critical Veeam auth bypass available, patch now
https://www.bleepingcomputer.com/news/security/exploit-for-critical-veeam-auth-bypass-available-patch-now/
SECCON Beginners CTF 2024
https://score.beginners.seccon.jp/
Frontier Communications data breach impacted over 750K people
https://securityaffairs.com/164315/data-breach/frontier-communications-data-breach.html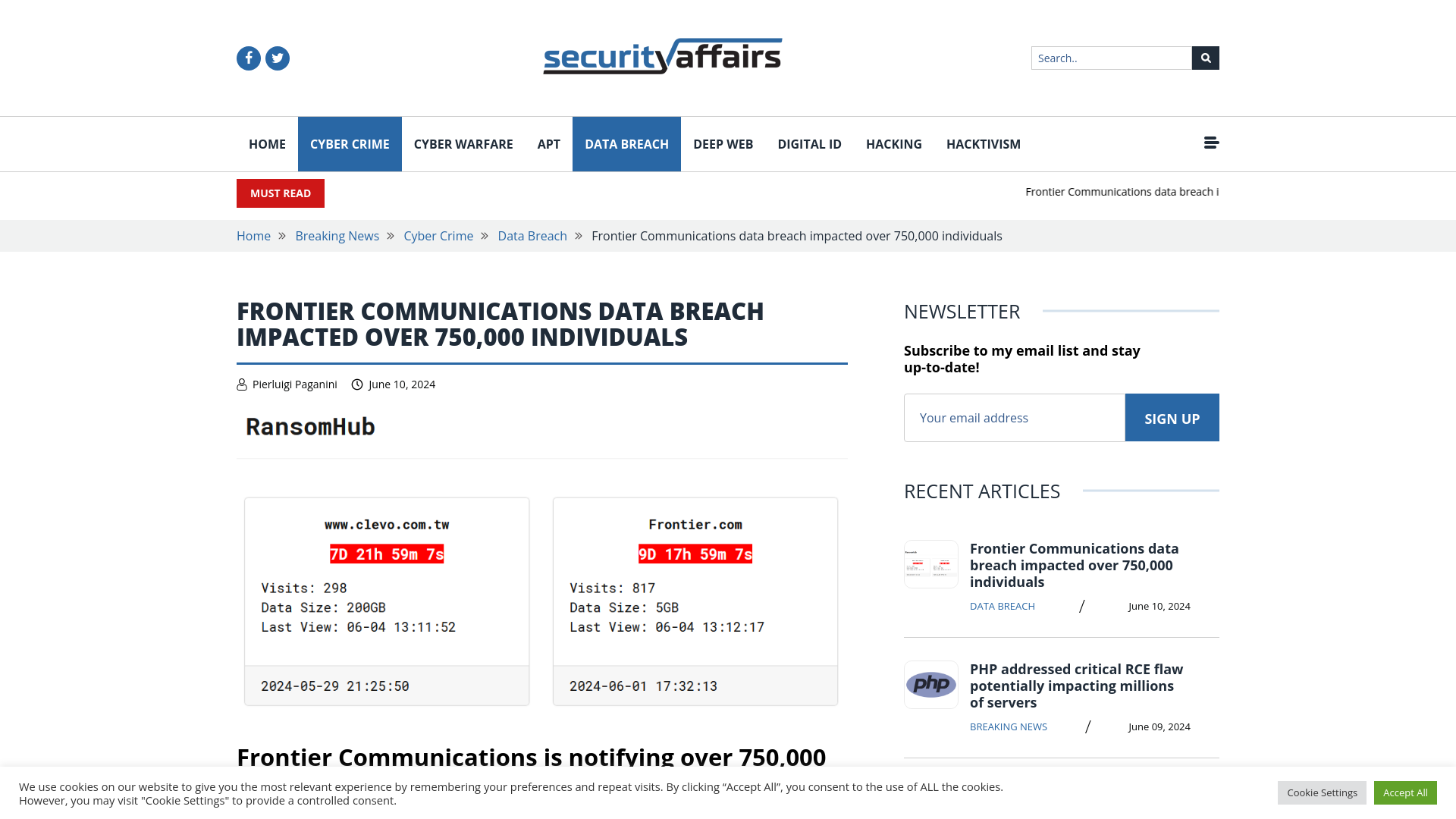
Azure Service Tags Vulnerability: Microsoft Warns of Potential Abuse by Hackers
https://thehackernews.com/2024/06/azure-service-tags-vulnerability.html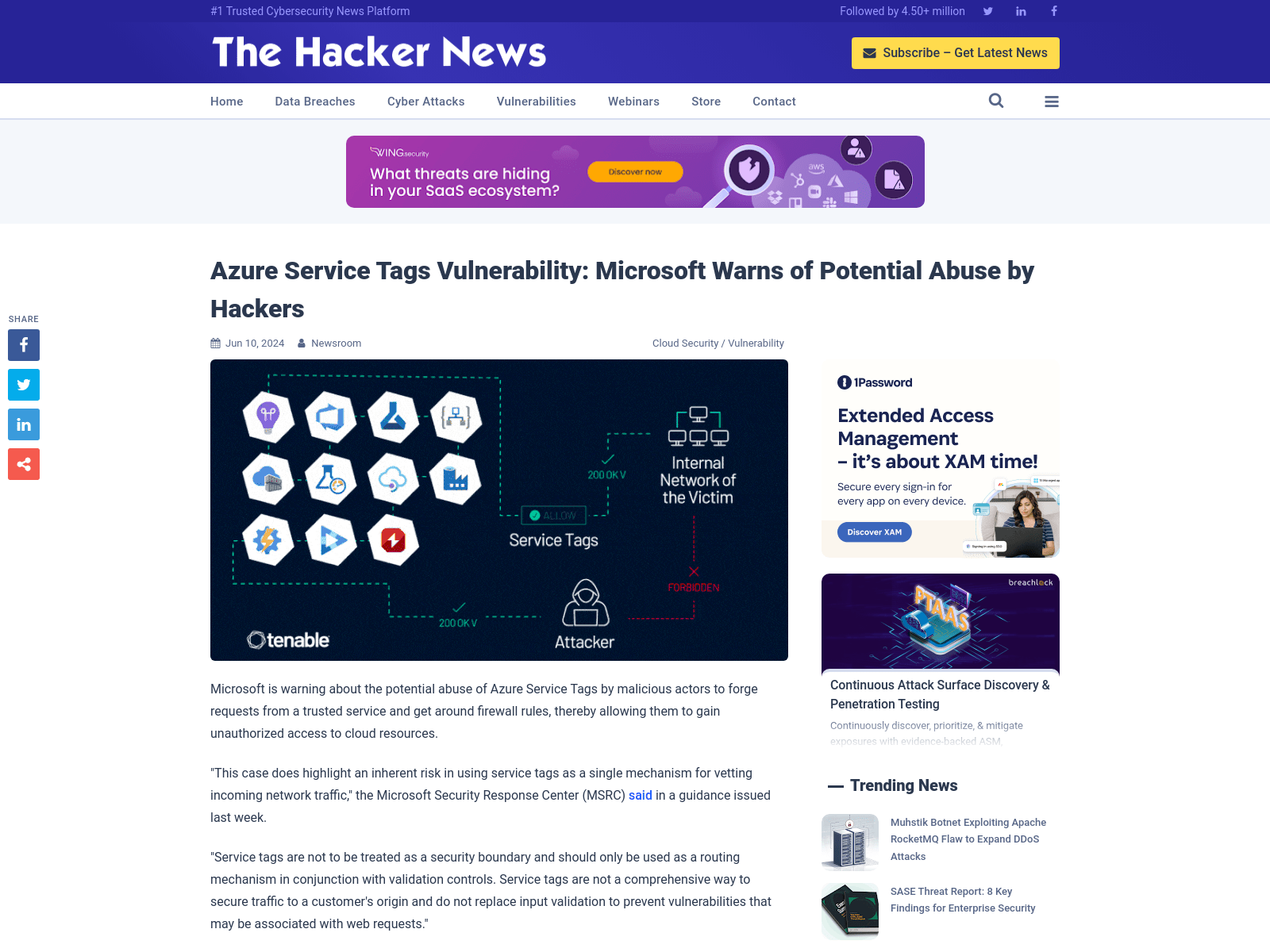
Fortinet Expands Cloud Security Portfolio with Lacework Acquisition - SecurityWeek
https://www.securityweek.com/fortinet-expands-cloud-security-portfolio-with-lacework-acquisition/
PHP Patches Critical Remote Code Execution Vulnerability - SecurityWeek
https://www.securityweek.com/php-patches-critical-remote-code-execution-vulnerability/
Let's reproduce GPT-2 (124M) - YouTube
https://youtu.be/l8pRSuU81PU
UNC5537 Targets Snowflake Customer Instances for Data Theft and Extortion | Google Cloud Blog
https://cloud.google.com/blog/topics/threat-intelligence/unc5537-snowflake-data-theft-extortion
More_eggs Malware Disguised as Resumes Targets Recruiters in Phishing Attack
https://thehackernews.com/2024/06/moreeggs-malware-disguised-as-resumes.html
EDR Internals for macOS and Linux | Outflank Security Blog
https://www.outflank.nl/blog/2024/06/03/edr-internals-macos-linux/
Detection as Code - by Panagiotis Gkatziroulis
https://purpleteamsec.substack.com/p/detection-as-code
Christie's Says Ransomware Attack Impacts 45,000 People - SecurityWeek
https://www.securityweek.com/christies-says-ransomware-attack-impacts-45000-people/
New York Times Responds to Source Code Leak - SecurityWeek
https://www.securityweek.com/new-york-times-responds-to-source-code-leak/
Today I Learned - Instrument ClamAV to extract AutoIT scripts | dfir.ch
https://dfir.ch/posts/today_i_learned_clamav_autoit/
[EN] Unsecure time-based secret and Sandwich Attack - Analysis of my research and release of the “Reset Tolkien” tool
https://www.aeth.cc/public/Article-Reset-Tolkien/secret-time-based-article-en.html![[EN] Unsecure time-based secret and Sandwich Attack - Analysis of my research and release of the “Reset Tolkien” tool](/image/screenshot/114dd8950f4a17629d320b0abc89e945.png)
Google Takes Down Influence Campaigns Tied to China, Indonesia, and Russia
https://thehackernews.com/2024/06/google-takes-down-influence-campaigns.html
Urgent call for O-type blood donations following London hospitals ransomware attack
https://therecord.media/london-hospitals-ransomware-urgent-call-blood-donations-otype
Sticky Werewolf Expands Cyber Attack Targets in Russia and Belarus
https://thehackernews.com/2024/06/sticky-werewolf-expands-cyber-attack.html