2023SORUS546.pdf
https://www.theses.fr/2023SORUS546.pdf
Robots Dream of Root Shells
https://blog.isosceles.com/robots-dream-of-root-shells/
Proof-of-Concept Exploit Released for Progress Software OpenEdge Vulnerability
https://thehackernews.com/2024/03/proof-of-concept-exploit-released-for.html
CVE-2024–23897 - Arbitrary file read in Jenkins
https://blog.securelayer7.net/arbitrary-file-read-in-jenkins/
BianLian Threat Actors Exploiting JetBrains TeamCity Flaws in Ransomware Attacks
https://thehackernews.com/2024/03/bianlian-threat-actors-exploiting.html
Magnet Goblin Hacker Group Leveraging 1-Day Exploits to Deploy Nerbian RAT
https://thehackernews.com/2024/03/magnet-goblin-hacker-group-leveraging-1.html
Exploiting CVE-2024-21378 – Remote Code Execution in Microsoft Outlook
https://www.netspi.com/blog/technical/red-team-operations/microsoft-outlook-remote-code-execution-cve-2024-21378/
Fake Leather wallet app on Apple App Store is a crypto drainer
https://www.bleepingcomputer.com/news/security/fake-leather-wallet-app-on-apple-app-store-is-a-crypto-drainer/
SANS New York City Spring 2024 | Cyber Security Training
https://www.sans.org/u/1uQM
SANS New York City Summer 2024 | Cyber Security Training
https://www.sans.org/u/1uQW
Malware Reverse Engineering for Beginners - Part 1: From 0x0 - Intezer
https://intezer.com/blog/malware-analysis/malware-reverse-engineering-beginners/
nvn1729 · GitHub
https://github.com/nvn1729
Over 15,000 hacked Roku accounts sold for 50¢ each to buy hardware
https://www.bleepingcomputer.com/news/security/over-15-000-hacked-roku-accounts-sold-for-50-each-to-buy-hardware/
Hackers exploit WordPress plugin flaw to infect 3,300 sites with malware
https://www.bleepingcomputer.com/news/security/hackers-exploit-wordpress-plugin-flaw-to-infect-3-300-sites-with-malware/
OPC UA Deep Dive Series (Part 8): Gaining Client-Side Remote Code Execution | Claroty
https://claroty.com/team82/research/opc-ua-deep-dive-series-part-8-gaining-client-side-remote-code-execution
AIS247: AI Security Essentials for Business Leaders | SANS Institute
https://www.sans.org/u/1ukG
Researchers expose Microsoft SCCM misconfigs usable in cyberattacks
https://www.bleepingcomputer.com/news/security/researchers-expose-microsoft-sccm-misconfigs-usable-in-cyberattacks/
Broadcom Merges Symantec and Carbon Black Into New Business Unit - SecurityWeek
https://www.securityweek.com/broadcom-merges-symantec-and-carbon-black-into-new-business-unit/
Possibly Exploited Fortinet Flaw Impacts Many Systems, but No Signs of Mass Attacks - SecurityWeek
https://www.securityweek.com/possibly-exploited-fortinet-flaw-impacts-many-systems-but-still-no-sign-of-mass-attacks/
Red box (phreaking) - Wikipedia
https://en.wikipedia.org/wiki/Red_box_(phreaking)
KNOXSS – State of the art in XSS Testing
http://knoxss.me
GitHub - leftp/BackupCreds: A C# implementation of dumping credentials from Windows Credential Manager
https://github.com/leftp/BackupCreds
Magnet Goblin Delivers Linux Malware Using One-Day Vulnerabilities - SecurityWeek
https://www.securityweek.com/magnet-goblin-delivers-linux-malware-using-one-day-vulnerabilities/
Attacking Android
https://blog.devsecopsguides.com/attacking-android
10 free cybersecurity guides you might have missed - Help Net Security
https://www.helpnetsecurity.com/2024/03/11/free-cybersecurity-guides/
Thousands of VMware ESXi Instances Exposed to Critical CVE-2024-22252 Vulnerability
https://securityonline.info/thousands-of-vmware-esxi-instances-exposed-to-critical-cve-2024-22252-vulnerability/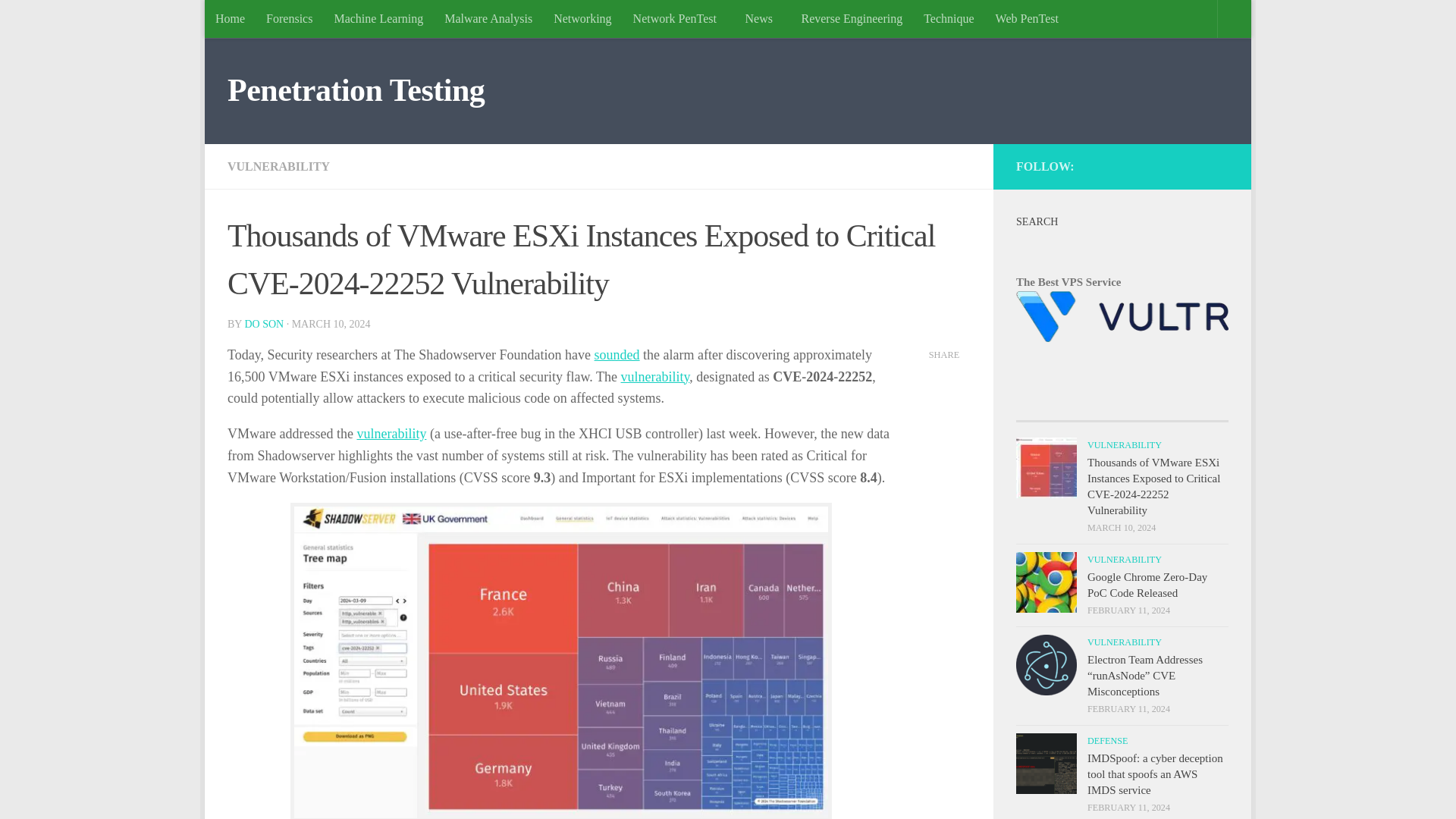
Experts released PoC exploit for critical Progress Software OpenEdge bug
https://securityaffairs.com/160347/hacking/progress-software-openedge-critical-flaw.html
Critical Vulnerability Allows Access to QNAP NAS Devices - SecurityWeek
https://www.securityweek.com/critical-vulnerability-allows-access-to-qnap-nas-devices/
Shellphish's AIxCC Story | Shellphish Support Syndicate
https://support.shellphish.net/blog/2024/03/11/shellphish-x-aixcc/
Hackers exploited WordPress Popup Builder plugin flaw to compromise 3,300 sites
https://securityaffairs.com/160329/hacking/wordpress-popup-builder-plugin-bug.html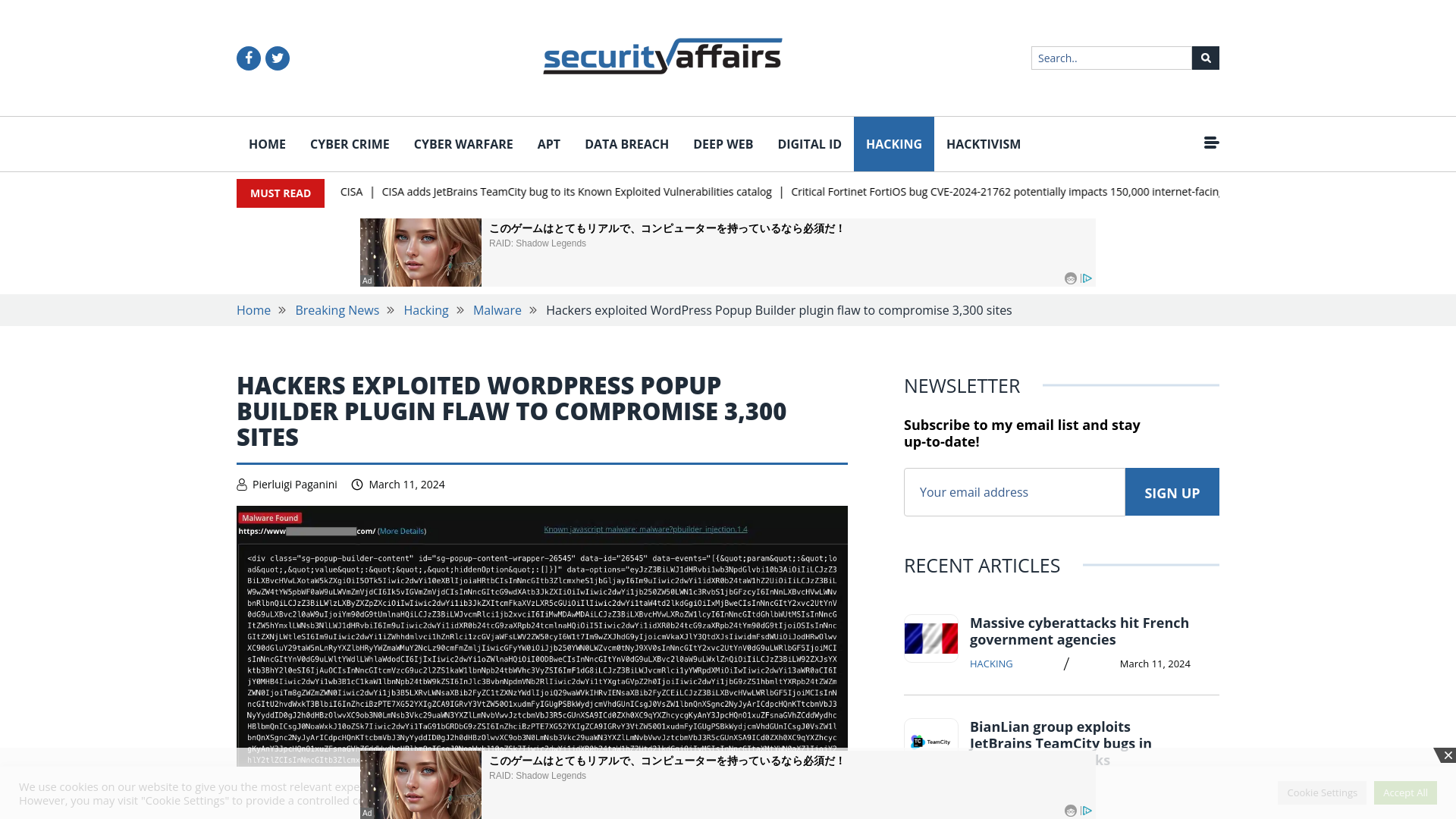
New Banking Trojan CHAVECLOAK Targets Brazilian Users via Phishing Tactics
https://thehackernews.com/2024/03/new-banking-trojan-chavecloak-targets.html
Magnet Goblin Targets Publicly Facing Servers Using 1-Day Vulnerabilities - Check Point Research
https://research.checkpoint.com/2024/magnet-goblin-targets-publicly-facing-servers-using-1-day-vulnerabilities/
Okta says data leaked on hacking forum not from its systems
https://www.bleepingcomputer.com/news/security/okta-says-data-leaked-on-hacking-forum-not-from-its-systems/
GitHub - thiagopeixoto/winsos-poc: A PoC demonstrating code execution via DLL Side-Loading in WinSxS binaries.
https://github.com/thiagopeixoto/winsos-poc