Magnet Goblin hackers use 1-day flaws to drop custom Linux malware
https://www.bleepingcomputer.com/news/security/magnet-goblin-hackers-use-1-day-flaws-to-drop-custom-linux-malware/
SOC Analyst Training: How to Analyze Malicious PDFs - YouTube
https://www.youtube.com/watch?v=AzXf7GV0jew
the Apple curl security incident 12604 | daniel.haxx.se
https://daniel.haxx.se/blog/2024/03/08/the-apple-curl-security-incident-12604/
Hackers exploit WordPress plugin flaw to infect 3,300 sites with malware
https://www.bleepingcomputer.com/news/security/hackers-exploit-wordpress-plugin-flaw-to-infect-3-300-sites-with-malware/
Game of Active Directory (GOAD) | Ludus
https://docs.ludus.cloud/docs/Environment%20Guides/goad/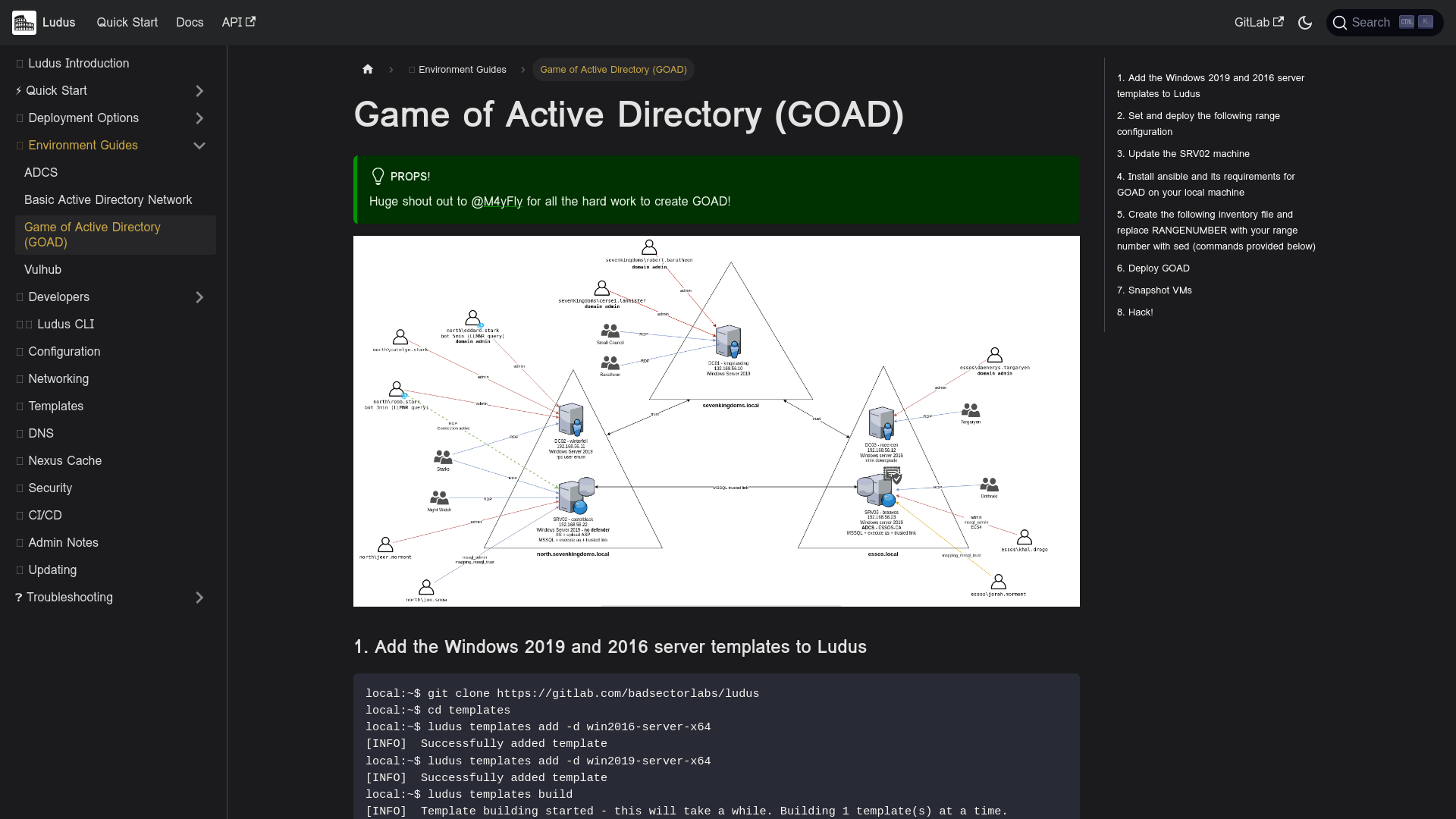
TrustedSec | Careers
https://www.trustedsec.com/about-us/careers
GitHub - SeanHeelan/claude_opus_cve_2023_0266: Demo showing Claude Opus does not find CVE-2023-0266
https://github.com/SeanHeelan/claude_opus_cve_2023_0266
KNOXSS – State of the art in XSS Testing
http://knoxss.me
Malware Reverse Engineering for Beginners - Part 1: From 0x0 - Intezer
https://intezer.com/blog/malware-analysis/malware-reverse-engineering-beginners/
Say Friend and Enter: Digitally lockpicking an advanced smart lock (Part 2: discovered vulnerabilities)
https://alephsecurity.com/2024/03/07/kontrol-lux-lock-2
sicat: an advanced exploit search tool
https://securityonline.info/sicat-an-advanced-exploit-search-tool/