GitHub - rasta-mouse/SpawnWith
https://github.com/rasta-mouse/SpawnWith
ScreenConnect servers hacked in LockBit ransomware attacks
https://www.bleepingcomputer.com/news/security/screenconnect-servers-hacked-in-lockbit-ransomware-attacks/
LockBit takedown: Police shut more than 14,000 accounts on Mega, Tutanota and Protonmail
https://therecord.media/lockbit-ransomware-takedown-mega-tutanota-protonmail
Microsoft expands free logging capabilities after May breach
https://www.bleepingcomputer.com/news/security/microsoft-expands-free-logging-capabilities-after-may-breach/
Leak reveals Chinese infosec vendor I-Soon hacks for Beijing • The Register
https://go.theregister.com/feed/www.theregister.com/2024/02/22/i_soon_china_infosec_leak/
How the FBI and CISA look to mature the government’s top ransomware task force
https://therecord.media/fbi-cisa-joint-ransomware-task-force-future
Reversing a Simple CrackMe with Ghidra Decompiler | by Craig Young | Medium
https://medium.com/@cy1337/reversing-a-simple-crackme-with-ghidra-decompiler-5dd1b1c3c0ba
A Guide to Reversing Shared Objects with Ghidra | by Craig Young | Medium
https://medium.com/@cy1337/a-guide-to-reversing-shared-objects-with-ghidra-cec83d5031e6
U.S. Offers $15 Million Bounty to Hunt Down LockBit Ransomware Leaders
https://thehackernews.com/2024/02/us-offers-15-million-bounty-to-hunt.html
LockBit ransomware secretly building next-gen encryptor before takedown
https://www.bleepingcomputer.com/news/security/lockbit-ransomware-secretly-building-next-gen-encryptor-before-takedown/
SANS Stay Sharp: May 2024 | Cyber Security Training
https://www.sans.org/u/1uAE
SANS Leadership & Cloud Security - Crystal City 2024 | Cyber Security Training
https://www.sans.org/u/1uAk
A dive into the PE file format - PE file structure - Part 1: Overview - 0xRick’s Blog
https://0xrick.github.io/win-internals/pe2/
A dive into the PE file format - Introduction - 0xRick’s Blog
https://0xrick.github.io/win-internals/pe1/
Special Offer for Asia Pacific Students | SANS Online Training
https://www.sans.org/u/1uF0
GitHub - Chocapikk/CVE-2024-25600: Unauthenticated Remote Code Execution – Bricks <= 1.9.6
https://github.com/Chocapikk/CVE-2024-25600
SANS Security West San Diego 2024 | Cyber Security Training
https://www.sans.org/u/1uAa
Sign in to stealthmole
https://platform.stealthmole.com/cases/62875030-d152-11ee-983f-f02f74830b7c
SANS Attack & Respond 2024 | Cyber Security Training
https://www.sans.org/u/1uAu
Russian Government Software Backdoored to Deploy Konni RAT Malware
https://thehackernews.com/2024/02/russian-government-software-backdoored.html
Hunting for Windows “Features” with Frida: DLL Sideloading
https://securityintelligence.com/posts/windows-features-dll-sideloading/
Threat Actors Quick to Abuse 'SSH-Snake' Worm-Like Tool - SecurityWeek
https://www.securityweek.com/threat-actors-quick-to-abuse-ssh-snake-worm-like-tool/
“To live is to fight, to fight is to live! - IBM ODM Remote Code Execution
https://labs.watchtowr.com/double-k-o-rce-in-ibm-operation-decision-manager/
New Wi-Fi Vulnerabilities Expose Android and Linux Devices to Hackers
https://thehackernews.com/2024/02/new-wi-fi-vulnerabilities-expose.html
Apple Unveils PQ3 Protocol - Post-Quantum Encryption for iMessage
https://thehackernews.com/2024/02/apple-unveils-pq3-protocol-post-quantum.html
AIS247: AI Security Essentials for Business Leaders | SANS Institute
https://www.sans.org/u/1ukG
CVE-2024-1709 & 1708: ScreenConnect Vulnerabilities Under Active Attack
https://securityonline.info/cve-2024-1709-1708-screenconnect-vulnerabilities-under-active-attack/
US Government Issues Guidance on Securing Water Systems - SecurityWeek
https://www.securityweek.com/us-government-issues-guidance-on-securing-water-systems/
New Mustang Panda campaign targets Asia with a backdoor dubbed DOPLUGS
https://securityaffairs.com/159464/apt/mustang-panda-doplugs-backdoor.html
Bitwarden’s new auto-fill option adds phishing resistance
https://www.bleepingcomputer.com/news/security/bitwardens-new-auto-fill-option-adds-phishing-resistance/
To Russia With Love: Assessing a KONNI-Backdoored Suspected Russian Consular Software Installer | by DCSO CyTec Blog | Feb, 2024 | Medium
https://medium.com/@DCSO_CyTec/to-russia-with-love-assessing-a-konni-backdoored-suspected-russian-consular-software-installer-ce618ea4b8f3
A Technical Deep Dive: Comparing Anti-Cheat Bypass and EDR Bypass - White Knight Labs
https://whiteknightlabs.com/2024/02/09/a-technical-deep-dive-comparing-anti-cheat-bypass-and-edr-bypass/
Chinese hacking documents offer glimpse into state surveillance | AP News
https://apnews.com/article/china-cybersecurity-leak-document-dump-spying-aac38c75f268b72910a94881ccbb77cb
Diving Into Glupteba's UEFI Bootkit
https://unit42.paloaltonetworks.com/glupteba-malware-uefi-bootkit/
Change Healthcare Cyberattack Causes Significant Disruption - SecurityWeek
https://www.securityweek.com/change-healthcare-cyberattack-causes-significant-disruption/
LABSCon23 Replay | Chasing Shadows | The rise of a prolific espionage actor - YouTube
https://www.youtube.com/watch?v=-7Swd1ZetiQ
Hacking Some More Secure USB Flash Drives (Part I) | SySS Tech Blog
https://blog.syss.com/posts/hacking-usb-flash-drives-part-1/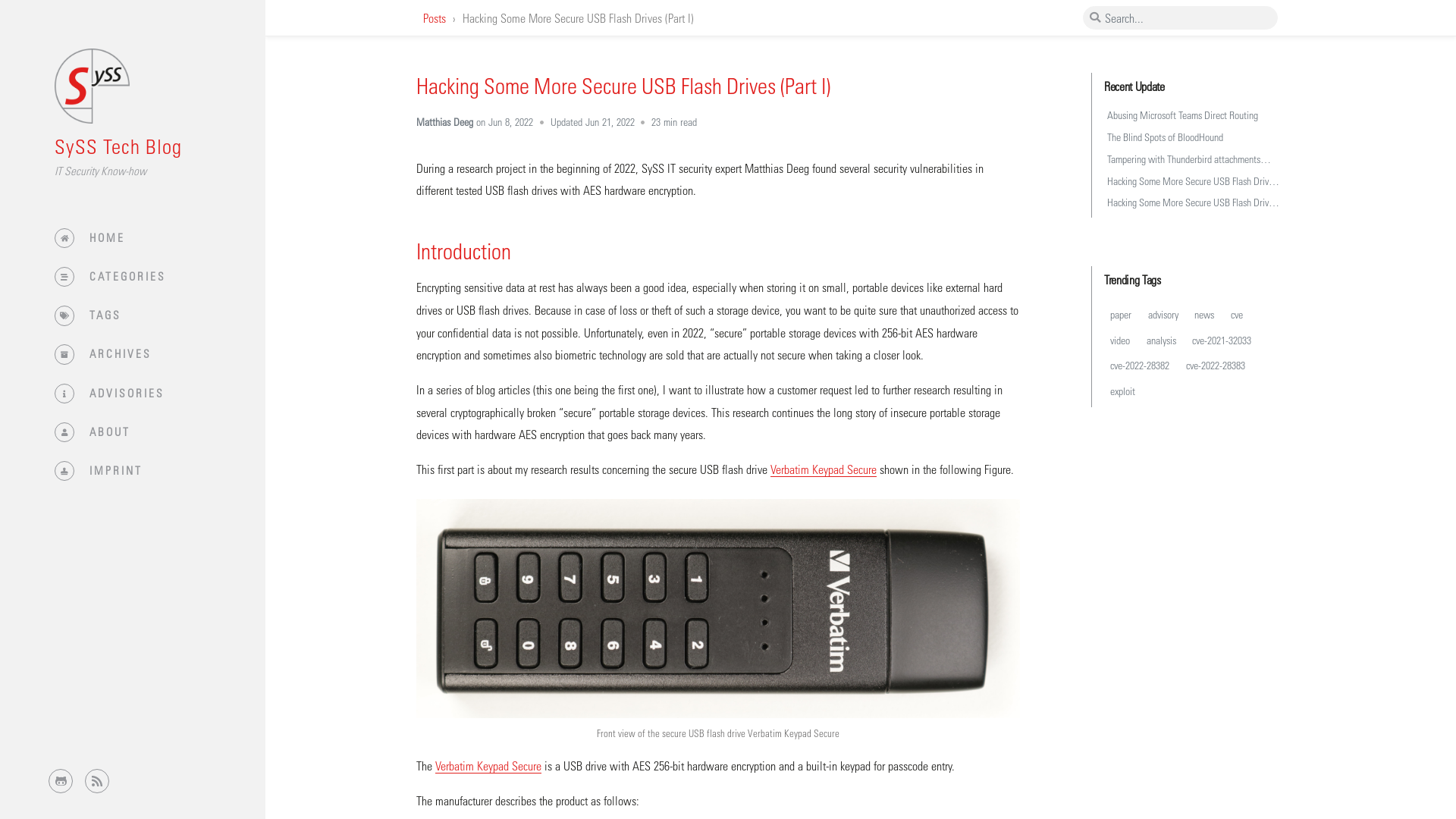
US Offering $10M for LockBit Leaders as Law Enforcement Taunts Cybercriminals - SecurityWeek
https://www.securityweek.com/us-offering-10m-for-lockbit-leaders-as-law-enforcement-taunts-cybercriminals/
Cybersecurity fears drive a return to on-premise infrastructure from cloud computing - Help Net Security
https://www.helpnetsecurity.com/2024/02/22/cloud-repatriation-projects-reasons/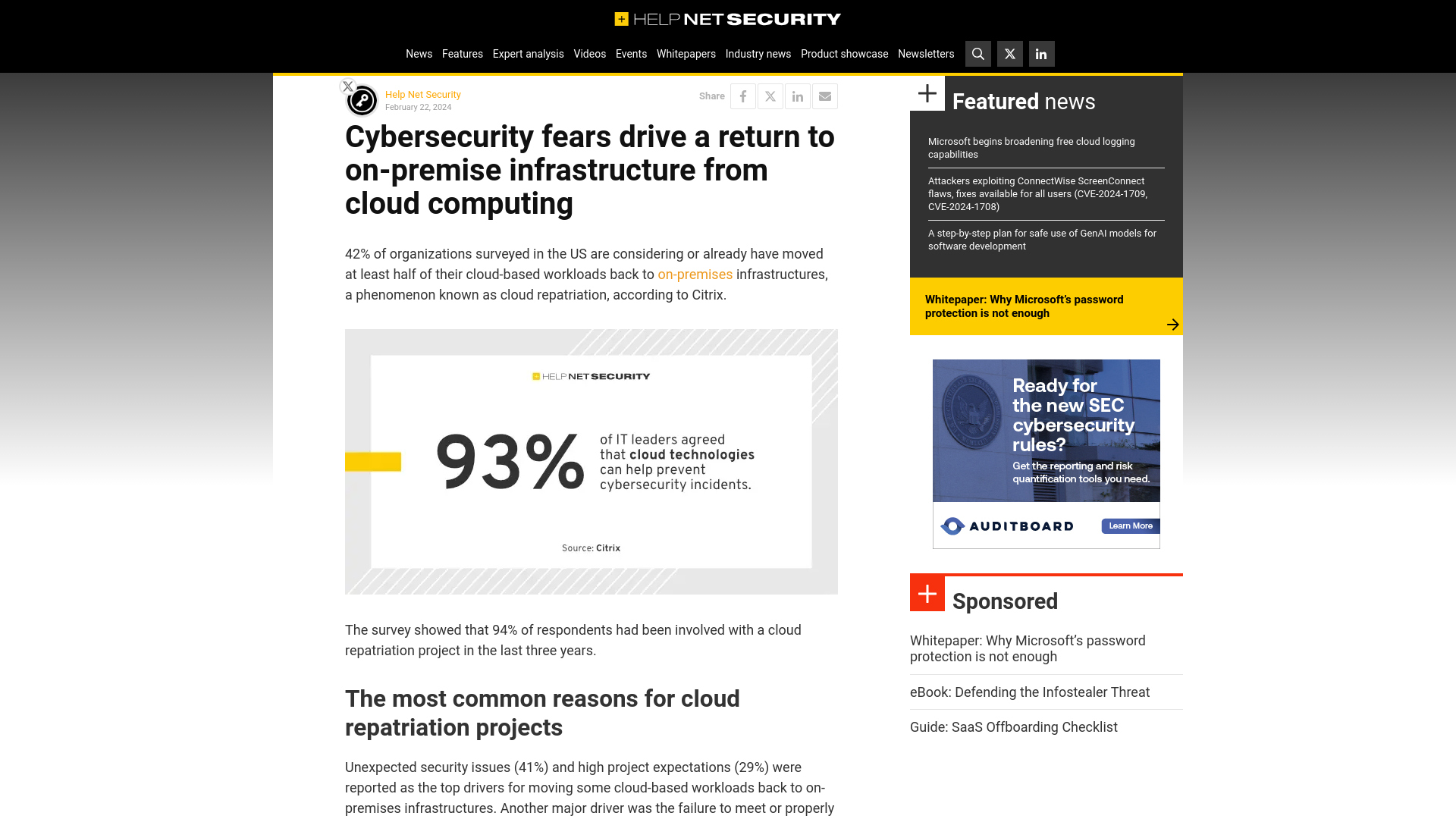
Hackers abuse Google Cloud Run in massive banking trojan campaign
https://www.bleepingcomputer.com/news/security/hackers-abuse-google-cloud-run-in-massive-banking-trojan-campaign/

Microsoft rolls out expanded logging six months after Chinese breach | CyberScoop
https://cyberscoop.com/microsoft-logging-cisa-omb/
New Leak Shows Business Side of China’s APT Menace – Krebs on Security
https://krebsonsecurity.com/2024/02/new-leak-shows-business-side-of-chinas-apt-menace/