GitHub - watchtowrlabs/connectwise-screenconnect_auth-bypass-add-user-poc
https://github.com/watchtowrlabs/connectwise-screenconnect_auth-bypass-add-user-poc
Cyber-related Designations | Office of Foreign Assets Control
https://ofac.treasury.gov/recent-actions/20240220
snovvcrash/ollvm13 - Docker Image | Docker Hub
https://hub.docker.com/r/snovvcrash/ollvm13
US offers $15 million bounty for info on LockBit ransomware gang
https://www.bleepingcomputer.com/news/security/us-offers-15-million-bounty-for-info-on-lockbit-ransomware-gang/
Russian Hackers Target Ukraine with Disinformation and Credential-Harvesting Attacks
https://thehackernews.com/2024/02/russian-hackers-target-ukraine-with.html
ConnectWise ScreenConnect: Authentication Bypass Deep Dive – Horizon3.ai
https://www.horizon3.ai/attack-research/red-team/connectwise-screenconnect-auth-bypass-deep-dive/
llvm-project-deluge/Manifesto.md at deluge · pizlonator/llvm-project-deluge · GitHub
https://github.com/pizlonator/llvm-project-deluge/blob/deluge/Manifesto.md
A first analysis of the i-Soon data leak | Malwarebytes
https://www.malwarebytes.com/blog/news/2024/02/a-first-analysis-of-the-i-soon-data-leak
New SSH-Snake malware steals SSH keys to spread across the network
https://www.bleepingcomputer.com/news/security/new-ssh-snake-malware-steals-ssh-keys-to-spread-across-the-network/
Apple Adds Post-Quantum Encryption to iMessage - SecurityWeek
https://www.securityweek.com/apple-adds-post-quantum-encryption-to-imessage/
Signal Introduces Usernames, Allowing Users to Keep Their Phone Numbers Private
https://thehackernews.com/2024/02/signal-introduces-usernames-allowing.html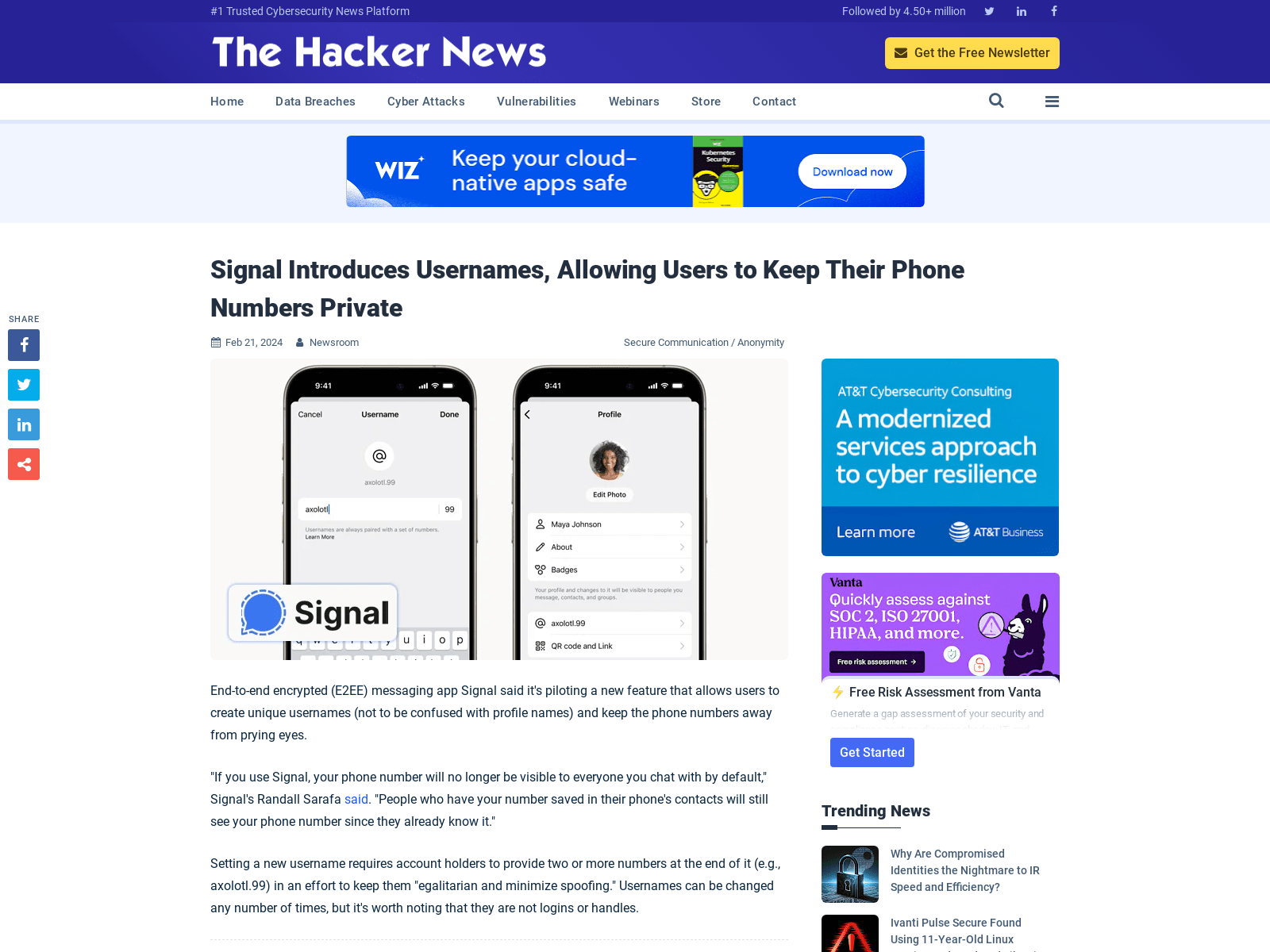
Mustang Panda Targets Asia with Advanced PlugX Variant DOPLUGS
https://thehackernews.com/2024/02/mustang-panda-targets-asia-with.html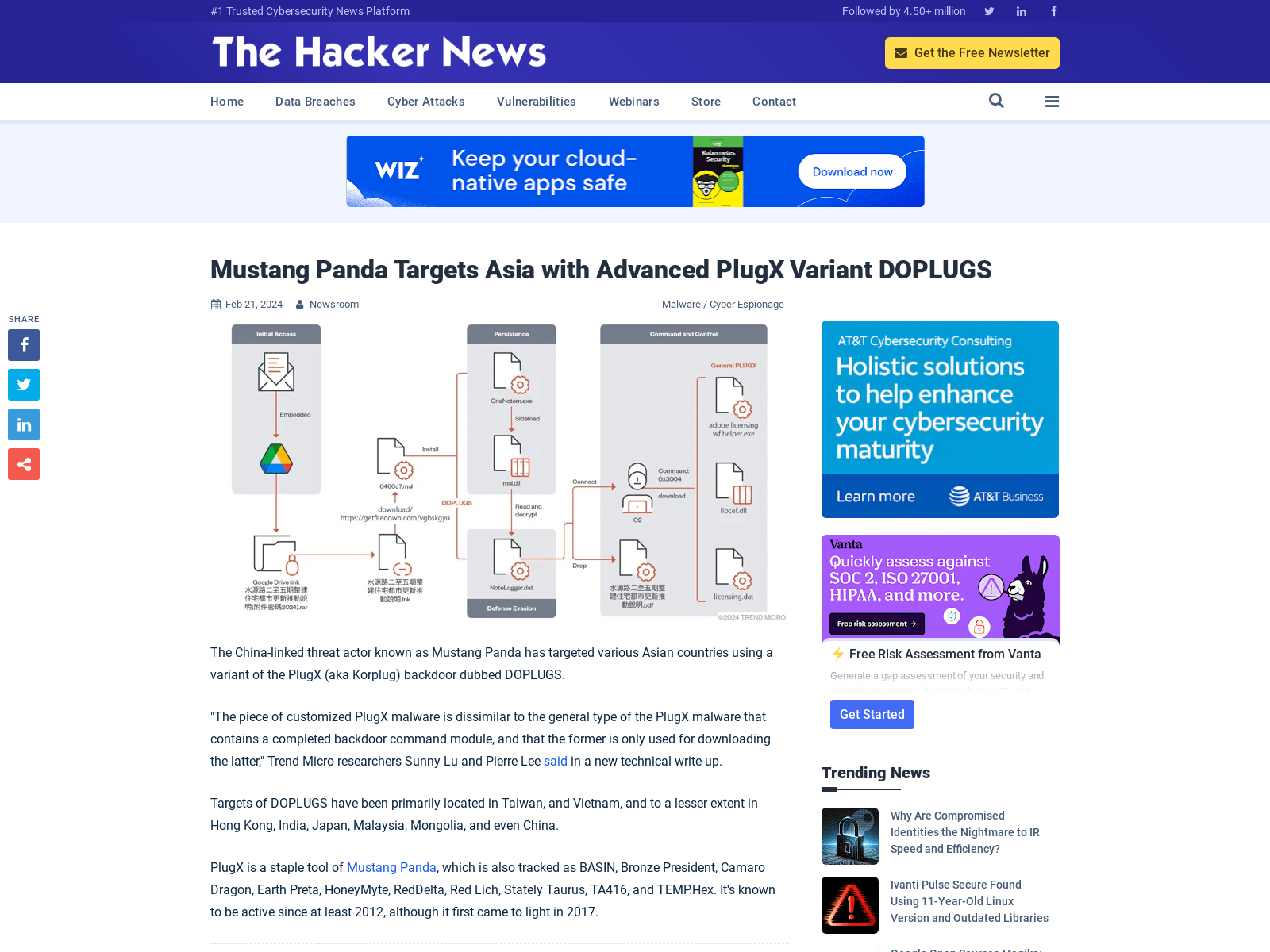
Microsoft rolls out expanded logging six months after Chinese breach | CyberScoop
https://cyberscoop.com/microsoft-logging-cisa-omb/
Top 10 web hacking techniques of 2023 | PortSwigger Research
https://portswigger.net/research/top-10-web-hacking-techniques-of-2023
VMware Alert: Uninstall EAP Now - Critical Flaw Puts Active Directory at Risk
https://thehackernews.com/2024/02/vmware-alert-uninstall-eap-now-critical.html
Detection Rules Development Framework – Purple Team
https://ipurple.team/2024/02/21/detection-rules-development-framework/
ランサムウェアによる暗号化被害データに関する復号ツールの開発について|警察庁Webサイト
https://www.npa.go.jp/news/release/2024/20240214002.html
Marco Ivaldi: "Sensecon 23: from #Windows dri…" - Infosec Exchange
https://infosec.exchange/@raptor/111967866681269848
New Wi-Fi Vulnerabilities Expose Android and Linux Devices to Hackers
https://thehackernews.com/2024/02/new-wi-fi-vulnerabilities-expose.html
BREAKDEV - Offensive Security Tools & Research
https://breakdev.org/
APT_REPORT/summary/2024/2024-unit42-incident-response-report_compressed.pdf at master · blackorbird/APT_REPORT · GitHub
https://github.com/blackorbird/APT_REPORT/blob/master/summary/2024/2024-unit42-incident-response-report_compressed.pdf
Cross-Site Scripting (XSS) Explained! // How to Bug Bounty - YouTube
https://youtu.be/ej2O4lOUzRc
Operation Texonto: Information operation targeting Ukrainian speakers in the context of the war
https://www.welivesecurity.com/en/eset-research/operation-texonto-information-operation-targeting-ukrainian-speakers-context-war/
SensePost | Sensecon 23: from windows drivers to an almost fully working edr
https://sensepost.com/blog/2024/sensecon-23-from-windows-drivers-to-an-almost-fully-working-edr/
Bypassing a noexec by elf roping - The Cave
https://blog.xilokar.info/bypassing-a-noexec-by-elf-roping.html
Control Systems Firm PSI Struggles to Recover From Ransomware Attack - SecurityWeek
https://www.securityweek.com/control-systems-firm-psi-struggles-to-recover-from-ransomware-attack/
Teeth/planck-mini.bin at main · lozaning/Teeth · GitHub
https://github.com/lozaning/Teeth/blob/main/planck-mini.bin
Executive Order on Port Cybersecurity Points to IT/OT Threat Posed by Chinese Cranes - SecurityWeek
https://www.securityweek.com/executive-order-on-port-cybersecurity-points-to-it-ot-threat-posed-by-chinese-cranes/
AWS Ransomware | dfir.ch
https://dfir.ch/posts/aws_ransomware/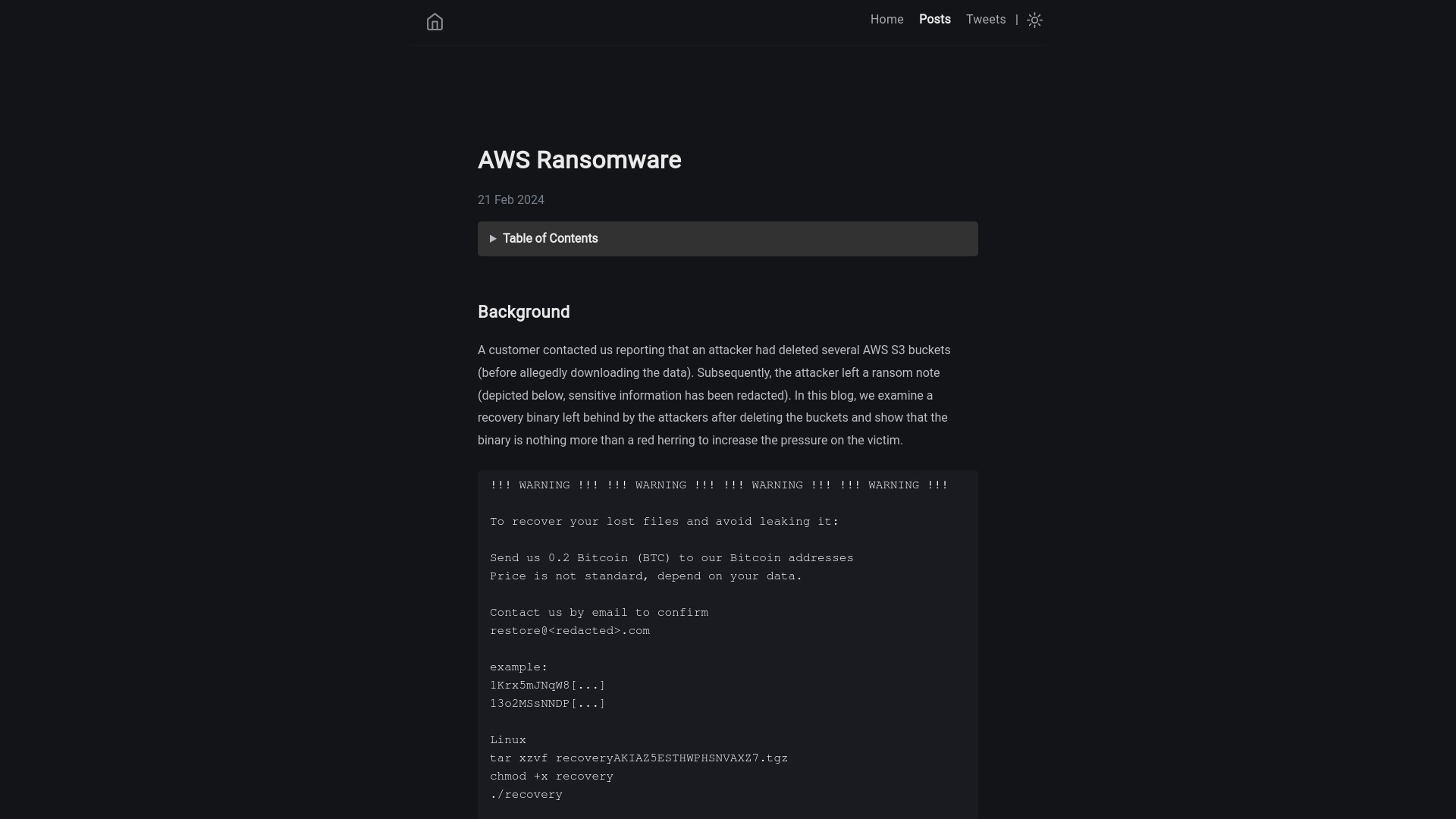
All About Hackbots: AI Agents That Hack · Joseph Thacker
https://josephthacker.com/ai/2024/02/21/hackbots.html
SANS Digital Forensics and Incident Response - YouTube
https://www.youtube.com/@SANSForensics/videos?view=0&sort=dd&shelf_id=0
Chrome 122, Firefox 123 Patch High-Severity Vulnerabilities - SecurityWeek
https://www.securityweek.com/chrome-122-firefox-123-patch-high-severity-vulnerabilities/
Playing with Libmalloc in 2024
https://blackwinghq.com/blog/posts/playing-with-libmalloc/