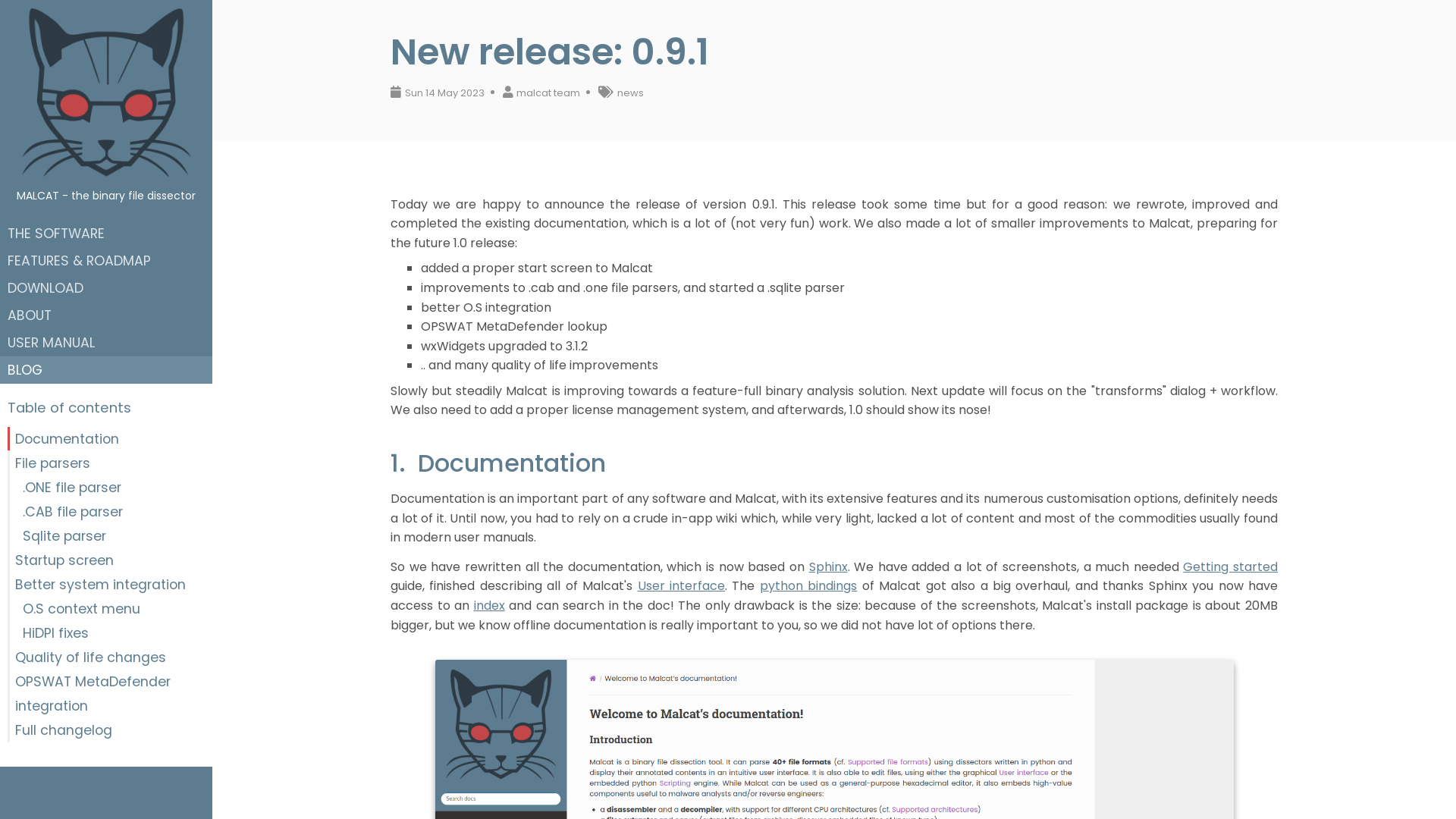
Qakbot/Qakbot_BB28_15.05.2023.txt at main · pr0xylife/Qakbot · GitHub
https://github.com/pr0xylife/Qakbot/blob/main/Qakbot_BB28_15.05.2023.txt
CS:GO: From Zero to 0-day — Neodyme
https://neodyme.io/blog/csgo_from_zero_to_0day/
🇺🇦Mike Saunders on Twitter: "@Octoberfest73 I'm a fan of a @strandjs quote - to paraphrase "at some point, it's just wizards talking to wizards." You give a super technical talk, very few people in the room will actually understand the content, only a few of those will be able to capitalize on it" / Twitter
https://twitter.com/hardwaterhacker/status/1657821364194013186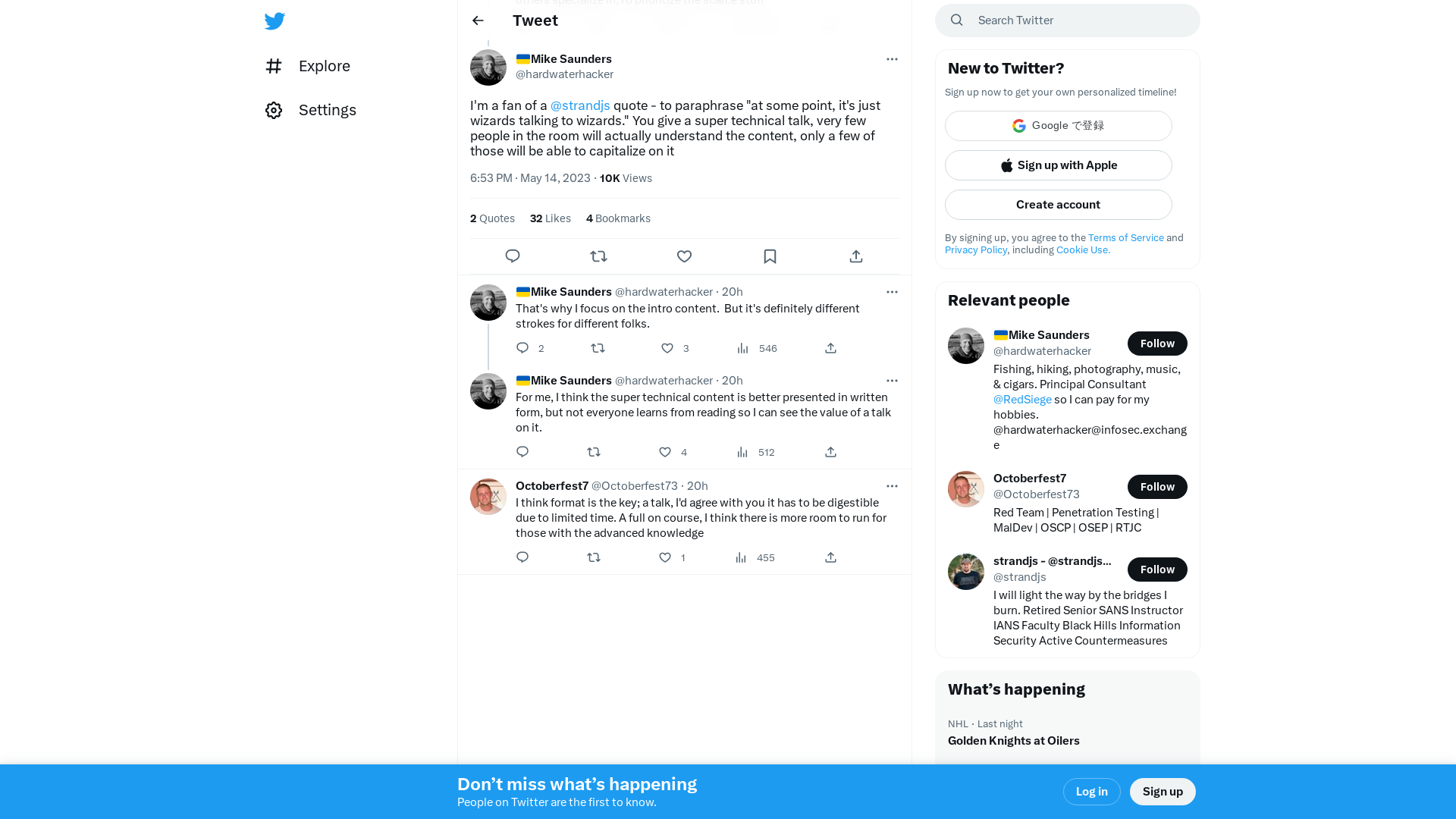
CVE-2023-26818 - Bypass TCC with Telegram in macOS | Dan Revah’s Blog
https://danrevah.github.io/2023/05/15/CVE-2023-26818-Bypass-TCC-with-Telegram/
Micro-channel public platform
https://mp-weixin-qq-com.translate.goog/s/hi1YgUUHnFDGf26cUXJkQQ?_x_tr_sl=auto&_x_tr_tl=en&_x_tr_hl=en-US&_x_tr_pto=wapp
BlackHoodie at TROOPERS 2023 - Blackhoodie
https://blackhoodie.re/Troopers-2023/
Sh0ck on Twitter: "3 RCE vulnerabilities found on Counter-Strike Global Offensive by Neodyme AG https://t.co/v3ZCdDt2gb" / Twitter
https://twitter.com/i/web/status/1658027211297792000
GitHub - Mr-xn/BLACKHAT_Asia2023: Black Hat Asia 2023 PDF Public
https://github.com/Mr-xn/BLACKHAT_Asia2023
Quasar Rat Analysis - Identification of 64 Quasar Servers Using Shodan and Censys
https://embee-research.ghost.io/hunting-quasar-rat-shodan
Avast Anti-Virus privileged arbitrary file create on virus restore (CVE-2023-1586) | the-deniss.github.io
https://the-deniss.github.io/posts/avast-privileged-arbitrary-file-create-on-restore/
CLR SqlShell Malware Targets MS SQL Servers for Crypto Mining and Ransomware
https://thehackernews.com/2023/05/clr-sqlshell-malware-targets-ms-sql.html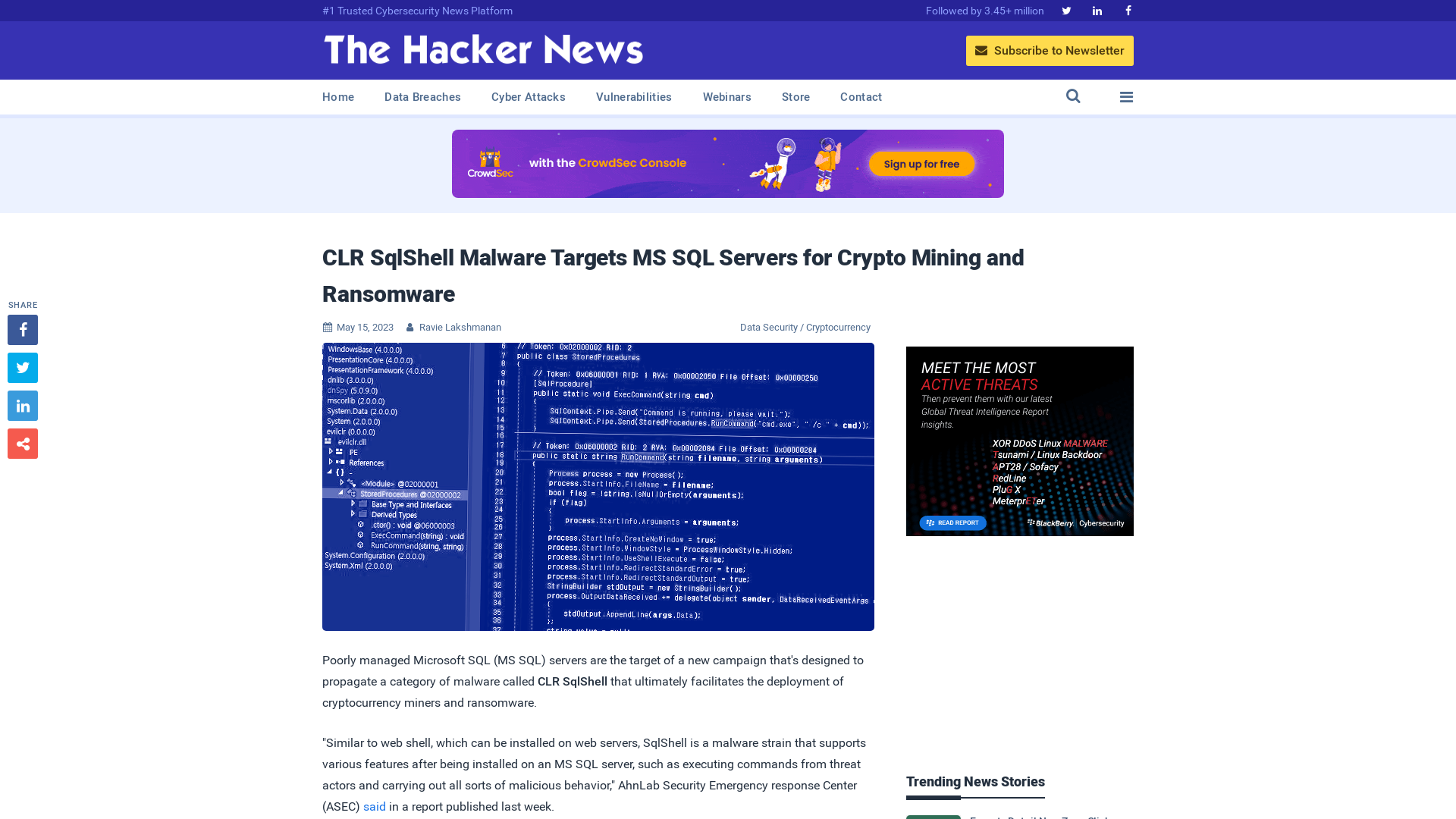
Gi7w0rm on Twitter: "#Smokeloader leads to #Amadey #Botnet leads to #Glupteba and an unknown #malware that could be a #neoreklami #Adware variant. #IoC: Smokeloader Botnet: pub1 C2: hxxp://potunulit.org/ #Amadey C2: 77.73.134.27/n9kdjc3xSf/index.php ( 37941 victims ) #Glupteba:… https://t.co/Jl39nwpLMa" / Twitter
https://twitter.com/i/web/status/1658060675770351616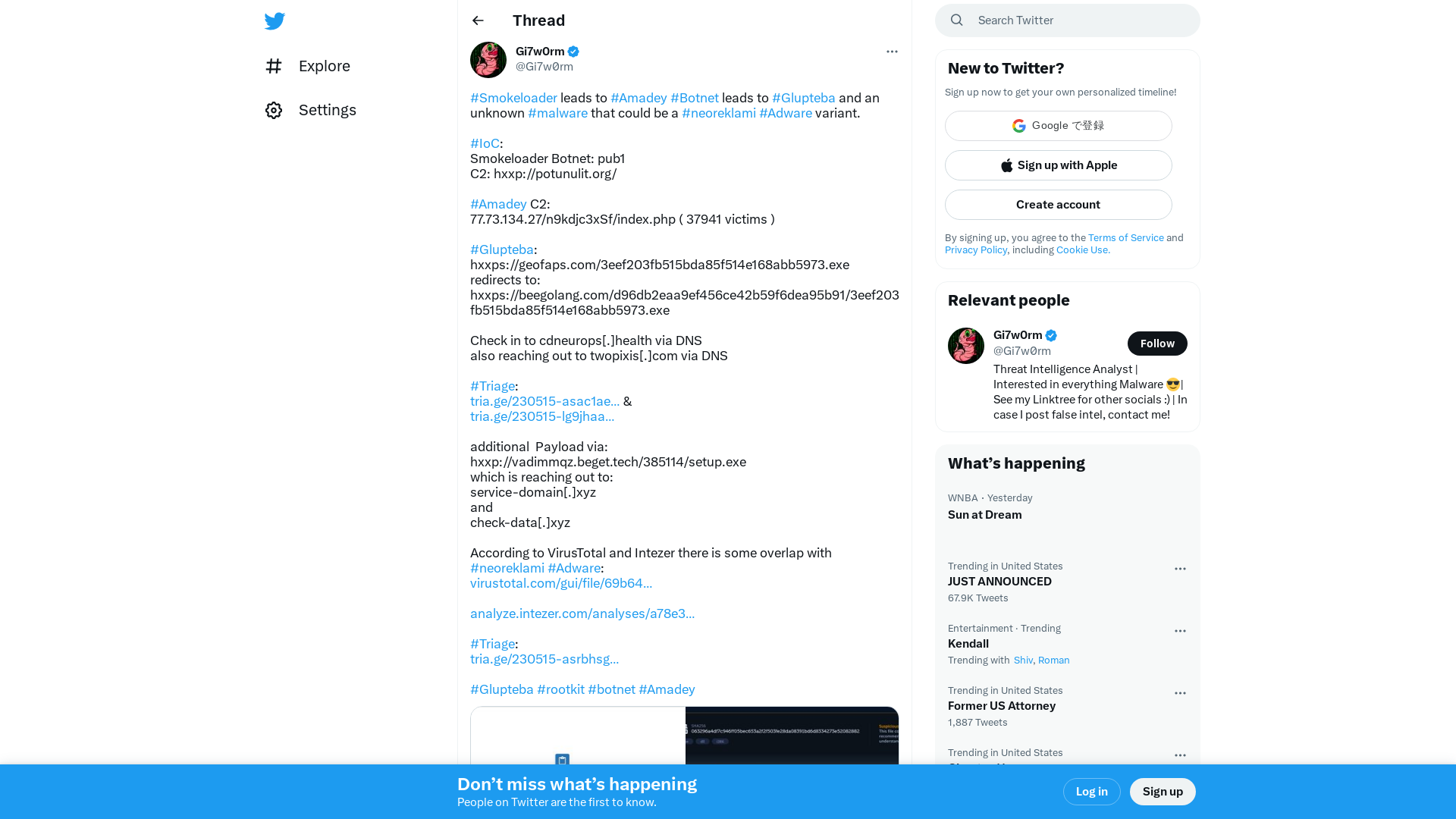
DC31 RTV "Pip-Boy" | Red Team Village
https://redteamvillage.square.site/product/dc31badge/2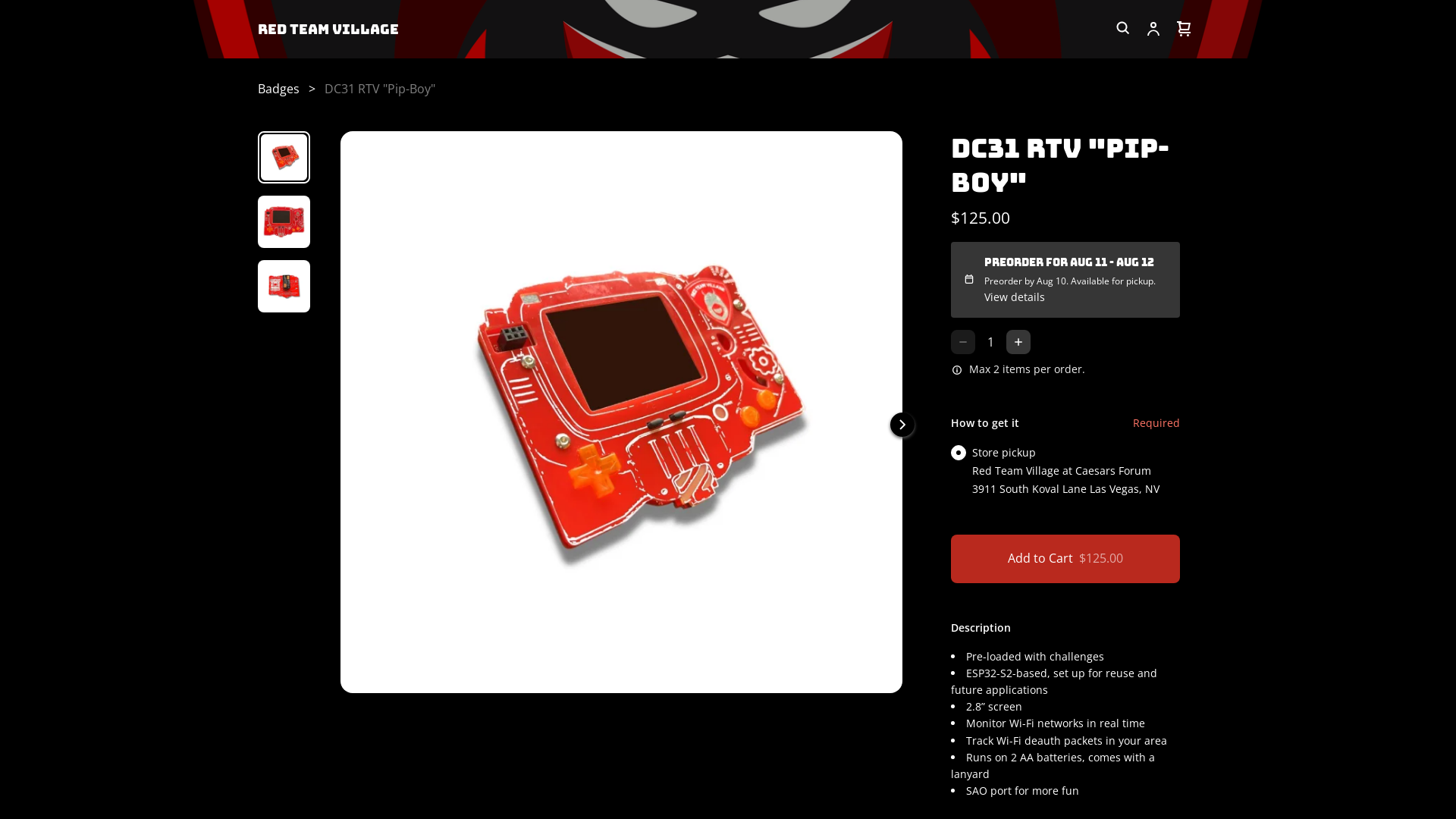
New release: 0.9.1
https://malcat.fr/blog/new-release-091/