Germán Fernández on Twitter: "🔺 New sample of #ExMatter (.NET/Confuser/64-bit) exfiltration tool commonly associated with #BlackCat, the binary connects to IP 64.227.80.81 AS14061 DIGITALOCEAN-ASN (as usual :D) port 22. PDB: "Z:\vm1\sync\sync\sync\bin\Debug\Confused\sync_enc.pdb" + They added the… https://t.co/A1YEE3vo8o" / Twitter
https://twitter.com/i/web/status/1655014346307559428
Meet Akira — A new ransomware operation targeting the enterprise
https://www.bleepingcomputer.com/news/security/meet-akira-a-new-ransomware-operation-targeting-the-enterprise/
Send My: Arbitrary data transmission via Apple's Find My network | Positive Security
https://positive.security/blog/send-my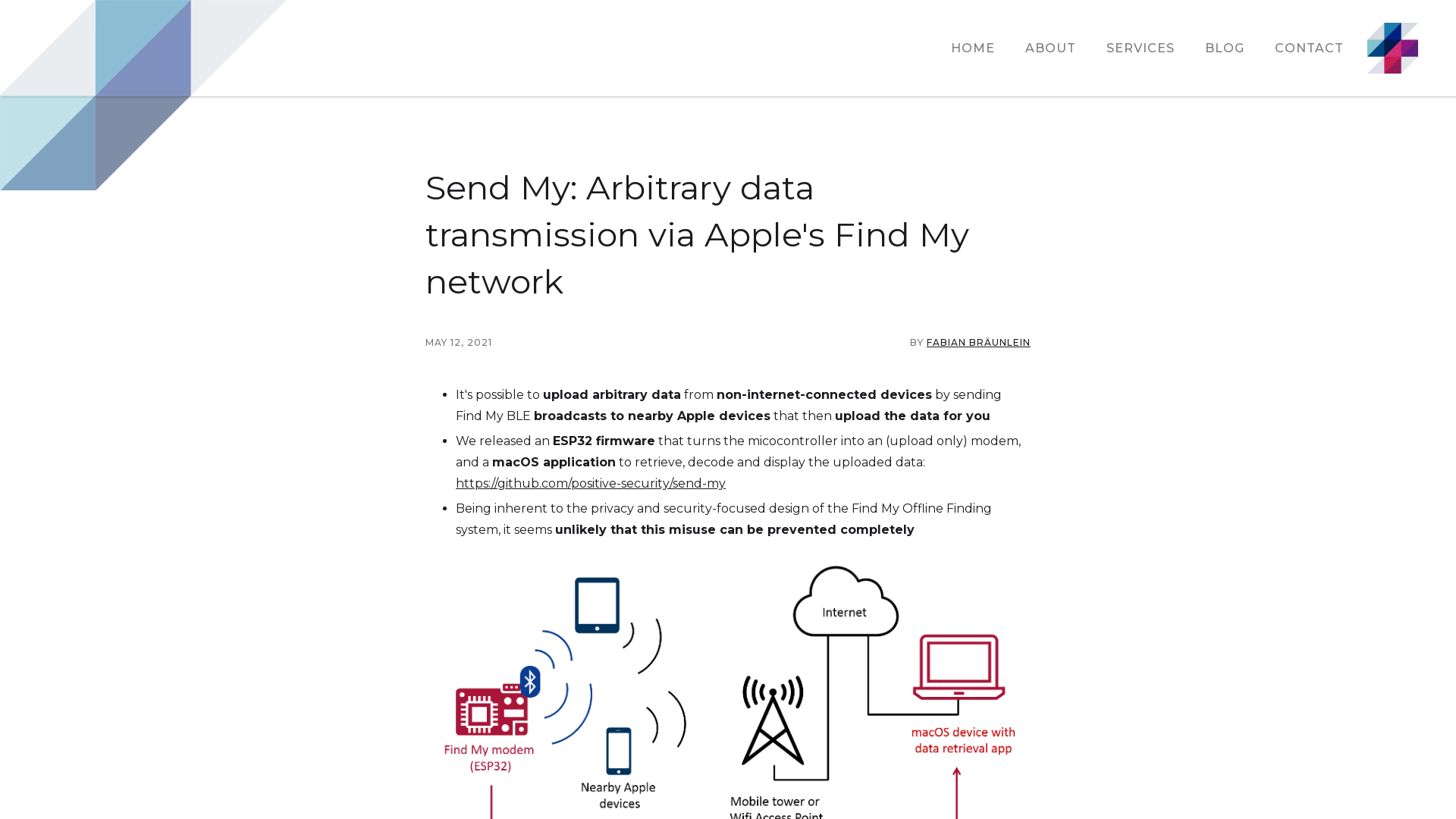
Western Digital says hackers stole customer data in March cyberattack
https://www.bleepingcomputer.com/news/security/western-digital-says-hackers-stole-customer-data-in-march-cyberattack/
GreenMwizi - Kenyan scamming campaign using Twitter bots
https://blog.bushidotoken.net/2023/05/greenmwizi-kenyan-scamming-campaign.html
OnlyMalware - Getting Started with Windows Malware Development - by rad98 - YouTube
https://www.youtube.com/watch?v=L9SI-PZ8-j8
Evilginx Mastery
https://academy.breakdev.org/evilginx-mastery
Theo - t3.gg on Twitter: "Gonna start judging startups by if they pick us-east-1 or us-west-2" / Twitter
https://twitter.com/t3dotgg/status/1655063735743156225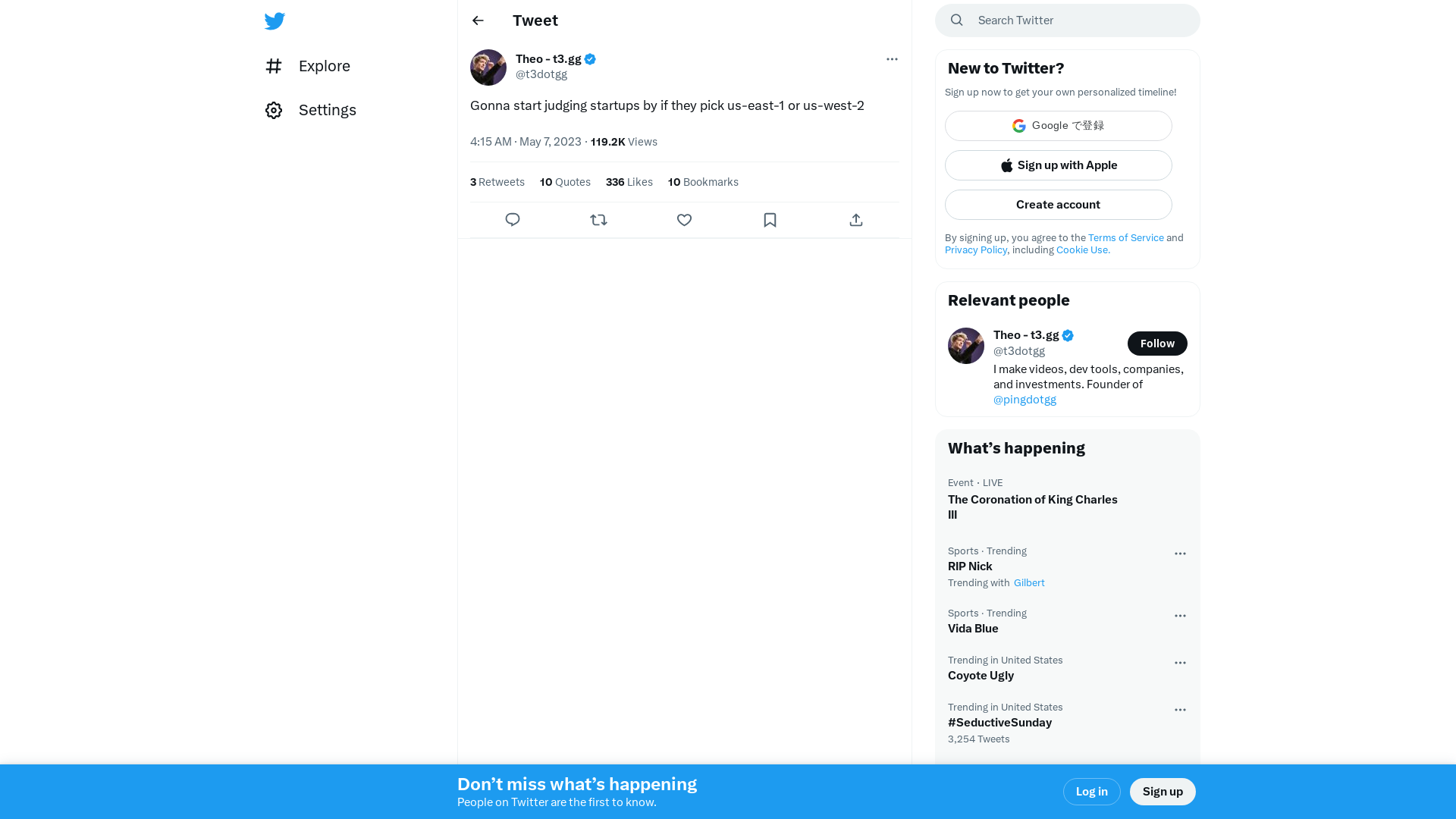
AgentTesla - Full Loader Analysis - Resolving API Hashes Using Conditional Breakpoints
https://embee-research.ghost.io/agenttesla-full-analysis-api-hashing/
Alex Matrosov on Twitter: "⛓️Confirmed, Intel OEM private key leaked, causing an impact on the entire ecosystem. It appears that Intel BootGuard may not be effective on certain devices based on the 11th Tiger Lake, 12th Adler Lake, and 13th Raptor Lake. Our investigation is ongoing, stay tuned for updates. https://t.co/fLopw1qeSD" / Twitter
https://twitter.com/matrosov/status/1654560343295934464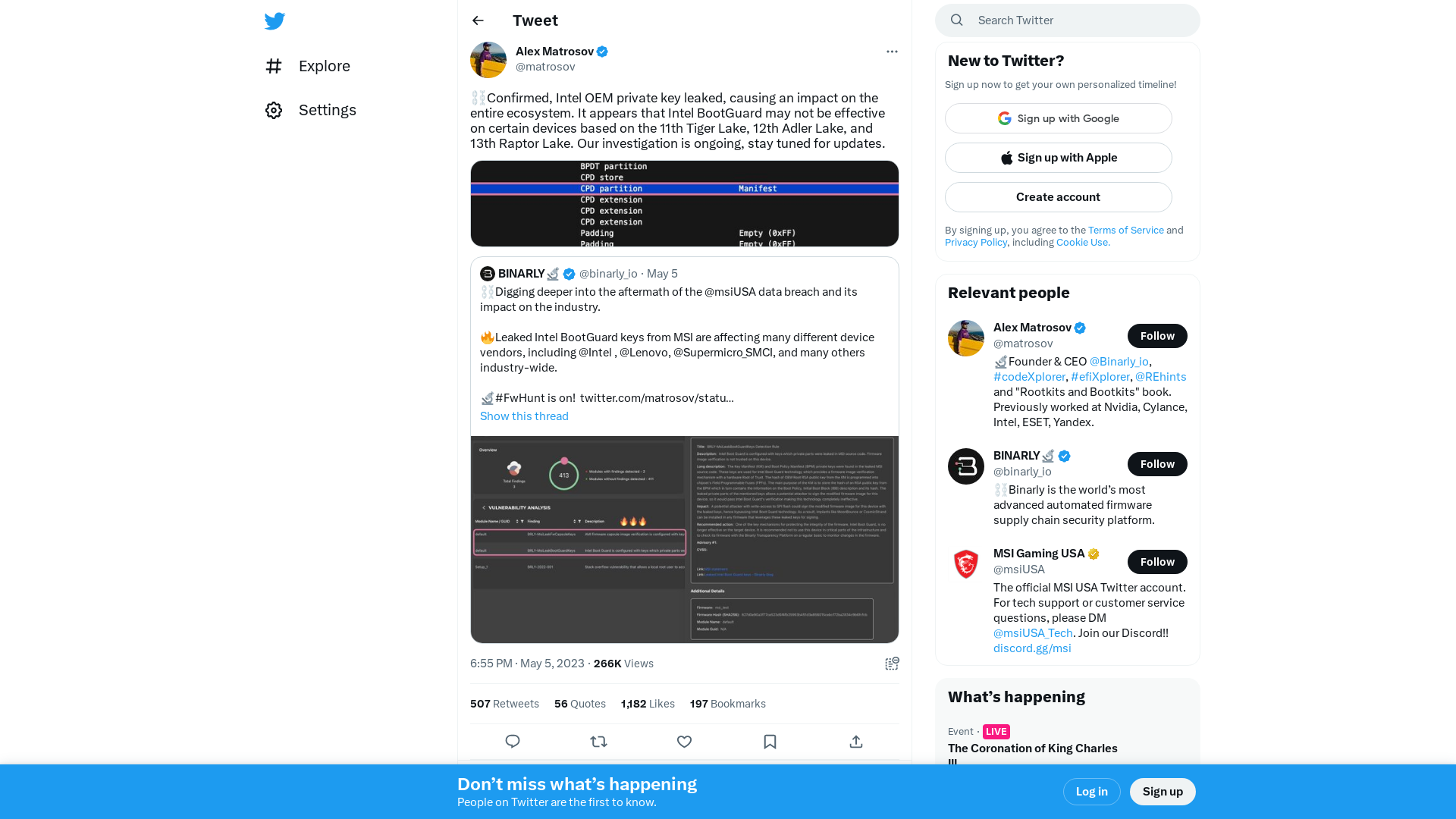
OnlyMalware Presents: Getting Started with Windows Malware Development - YouTube
https://youtu.be/Rs0xPnVr0dQ
Jon Gorenflo 🇺🇦🌻 on Twitter: "#OSINT Tip: Did you know you can recover scrubbed metadata from a PDF that wasn't scrubbed properly? The changes are incremental, and the history is stored in the PDF. This command removes the "updates" to the PDF metadata: exiftool -PDF-update:all= file.pdf https://t.co/jMB9sfOA0k" / Twitter
https://twitter.com/i/web/status/1654617325520433152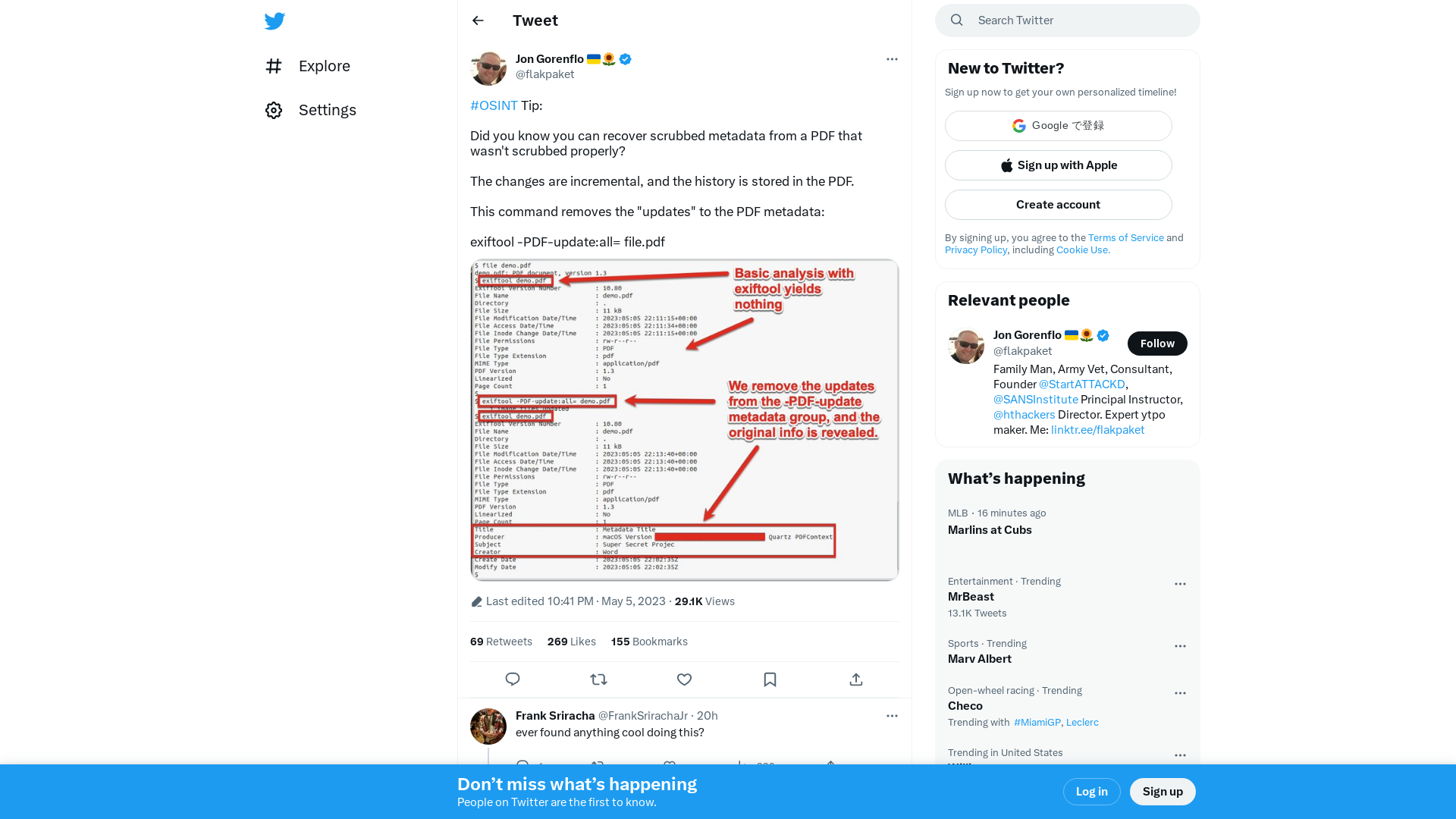
Cybercrime, the mysterious malware from Türkiye is SnakeKeylogger/StormKitty
https://www.difesaesicurezza.com/en/defence-and-security/cybercrime-the-mysterious-malware-from-turkiye-is-snakekeylogger-stormkitty/
New Cactus ransomware encrypts itself to evade antivirus
https://www.bleepingcomputer.com/news/security/new-cactus-ransomware-encrypts-itself-to-evade-antivirus/
GitHub - chenaotian/CVE-2023-0386: CVE-2023-0386 analysis and Exp
https://github.com/chenaotian/CVE-2023-0386
Release Version 0.4 Release · Idov31/Nidhogg · GitHub
https://github.com/Idov31/Nidhogg/releases/tag/v0.4
Rich Felgate on Twitter: "Yesterday I got arrested whilst filming a @JustStop_Oil supporter holding a banner on the pavement near the coronation route. I'm a filmmaker and had my @BECTU press accreditation visible around my neck. Police deemed this to be "conspiracy to commit a public nuisance". https://t.co/obgLH8Qj42" / Twitter
https://twitter.com/richfelgate/status/1655199737471959041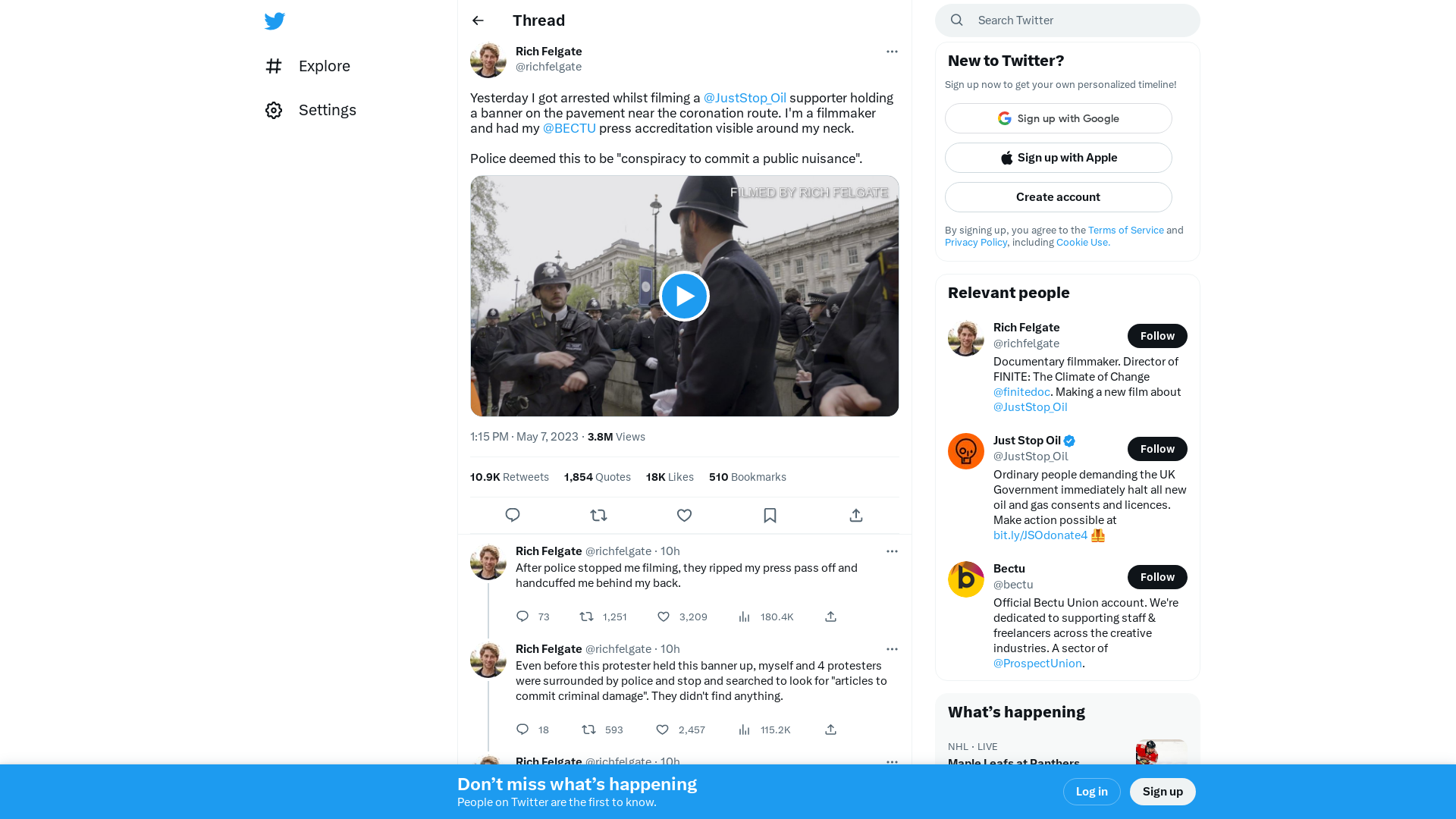
GitHub - Sq00ky/RunAsPasswd: A RunAs clone with the ability to specify the password as an argument.
https://github.com/Sq00ky/RunAsPasswd
BINARLY🔬 on Twitter: "⛓️Digging deeper into the aftermath of the @msiUSA data breach and its impact on the industry. 🔥Leaked Intel BootGuard keys from MSI are affecting many different device vendors, including @Intel , @Lenovo, @Supermicro_SMCI, and many others industry-wide. 🔬#FwHunt is on! https://t.co/ZB8XKj33Hv" / Twitter
https://twitter.com/binarly_io/status/1654287041339998208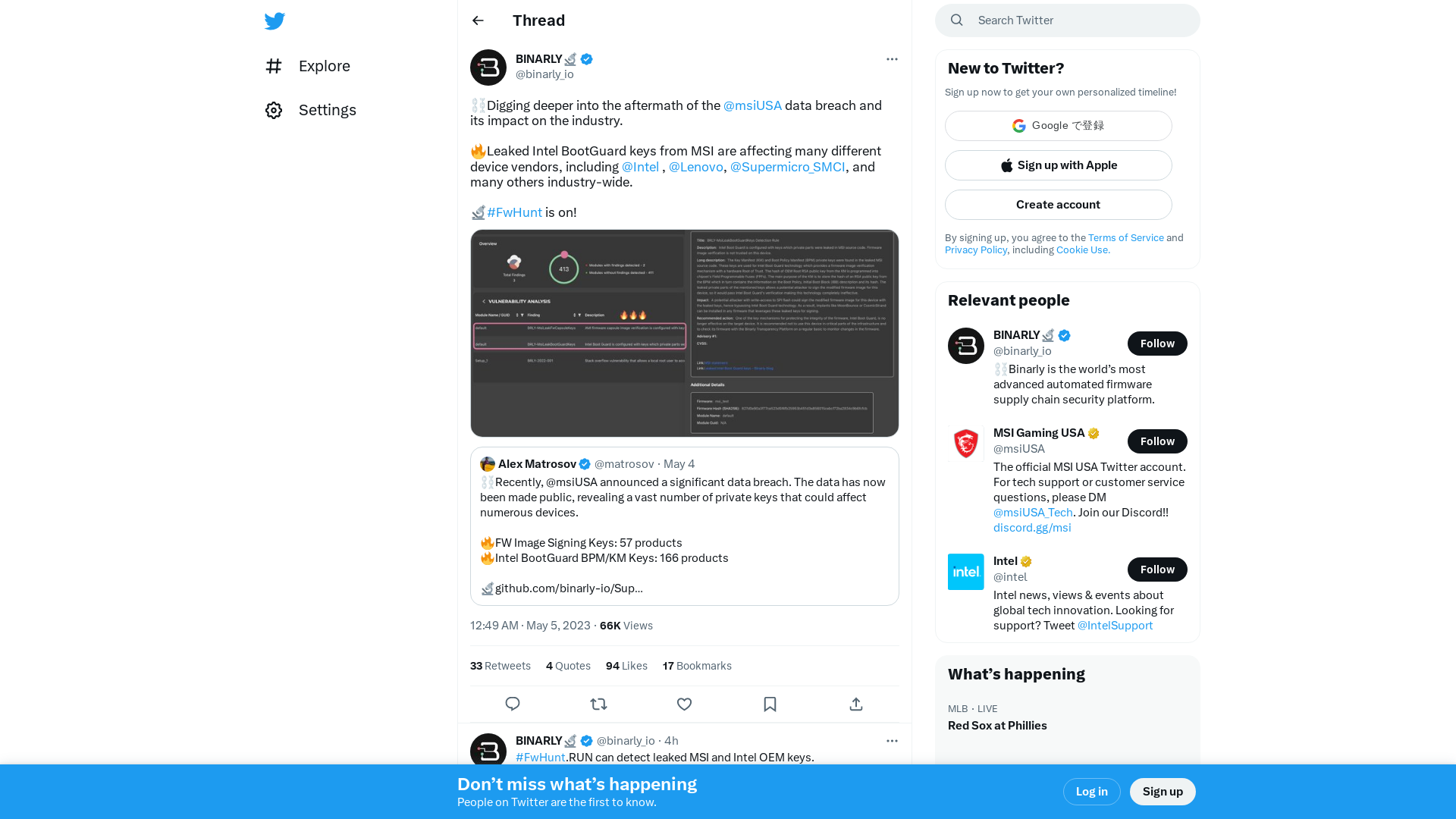
A smorgasbord of a bug chain: postMessage, JSONP, WAF bypass, DOM-based XSS, CORS, CSRF... :: jub0bs.com
https://jub0bs.com/posts/2023-05-05-smorgasbord-of-a-bug-chain/
strandjs - @[email protected] on Twitter: "The most effective way to improve organizational security is to get hacked." / Twitter
https://twitter.com/strandjs/status/1655208987506114560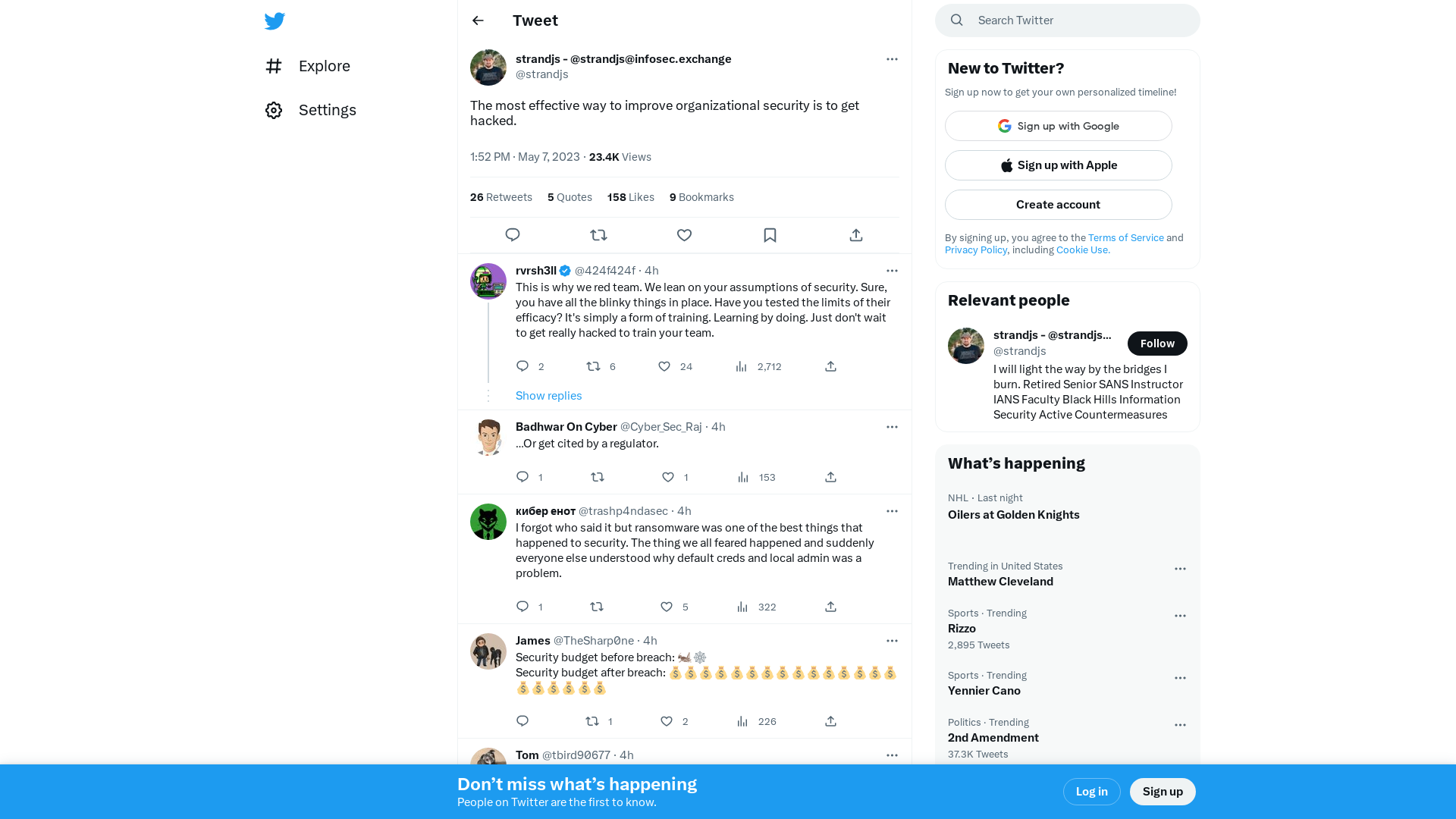
https://webmail.une.net.co/home/[email protected]/Briefcase/
https://webmail.une.net.co/home/[email protected]/Briefcase/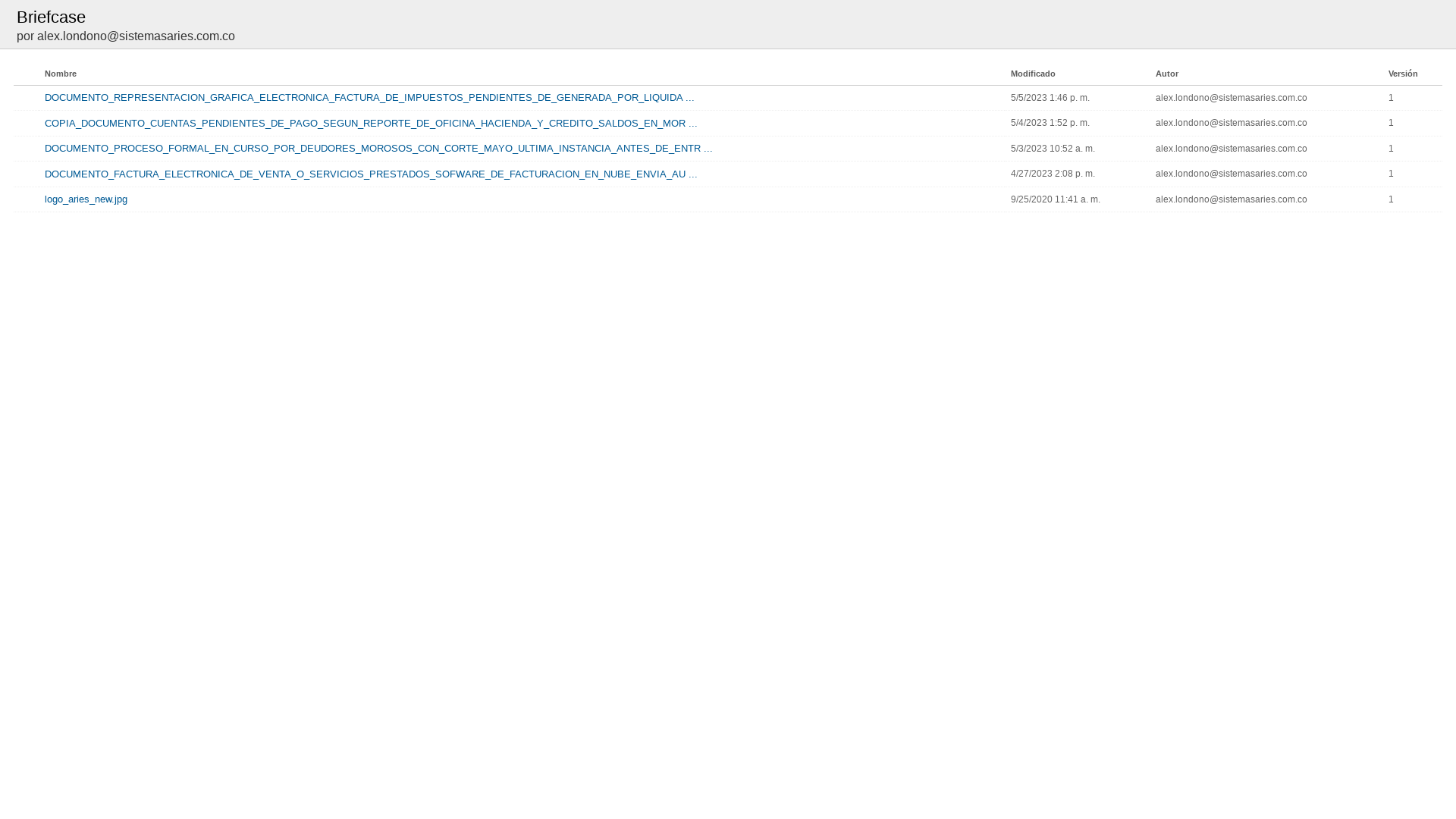
Release 2.5.0 · sensepost/gowitness · GitHub
https://github.com/sensepost/gowitness/releases/tag/2.5.0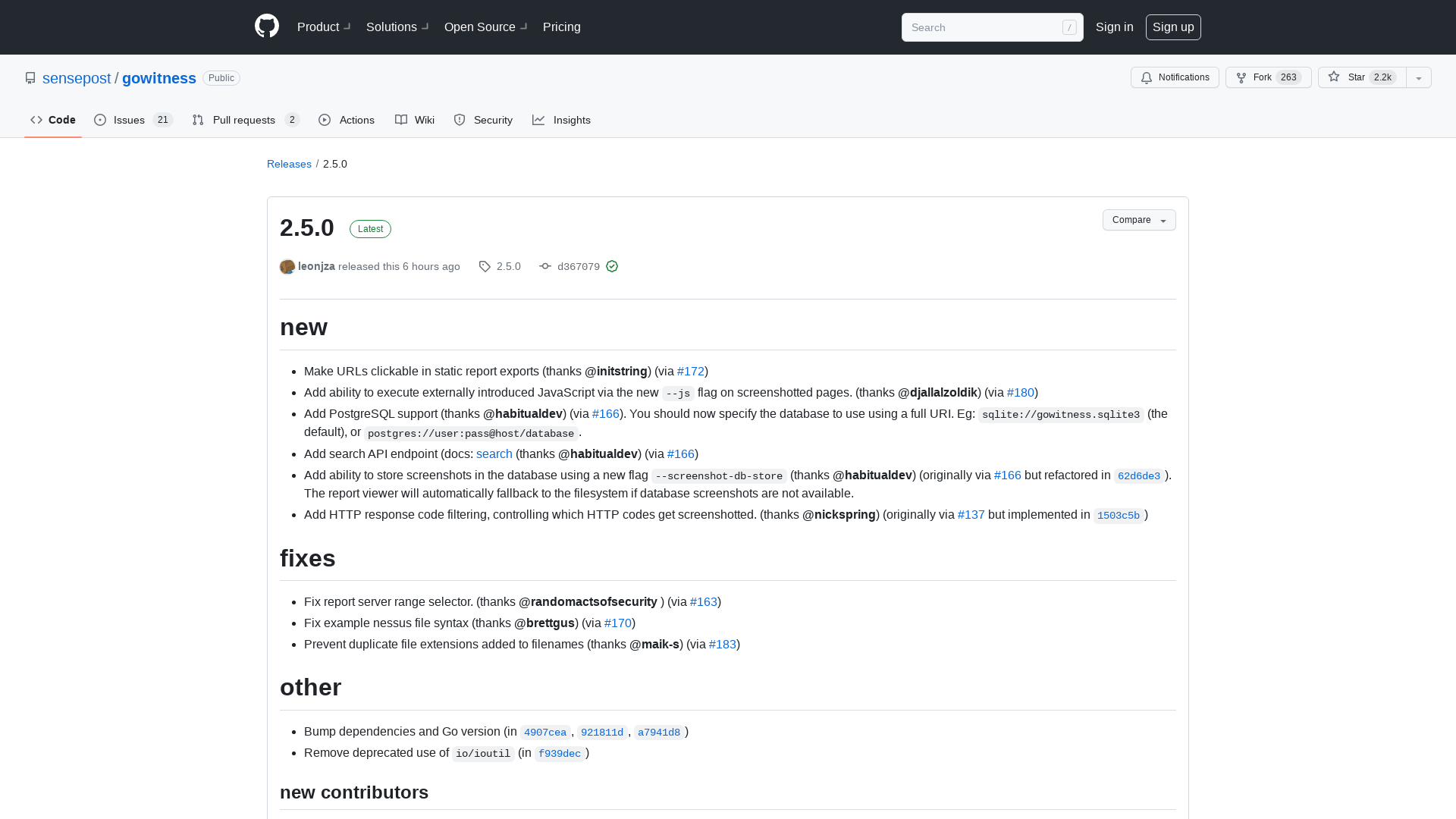
GitHub - epi052/osed-scripts: bespoke tooling for offensive security's Windows Usermode Exploit Dev course (OSED)
https://github.com/epi052/osed-scripts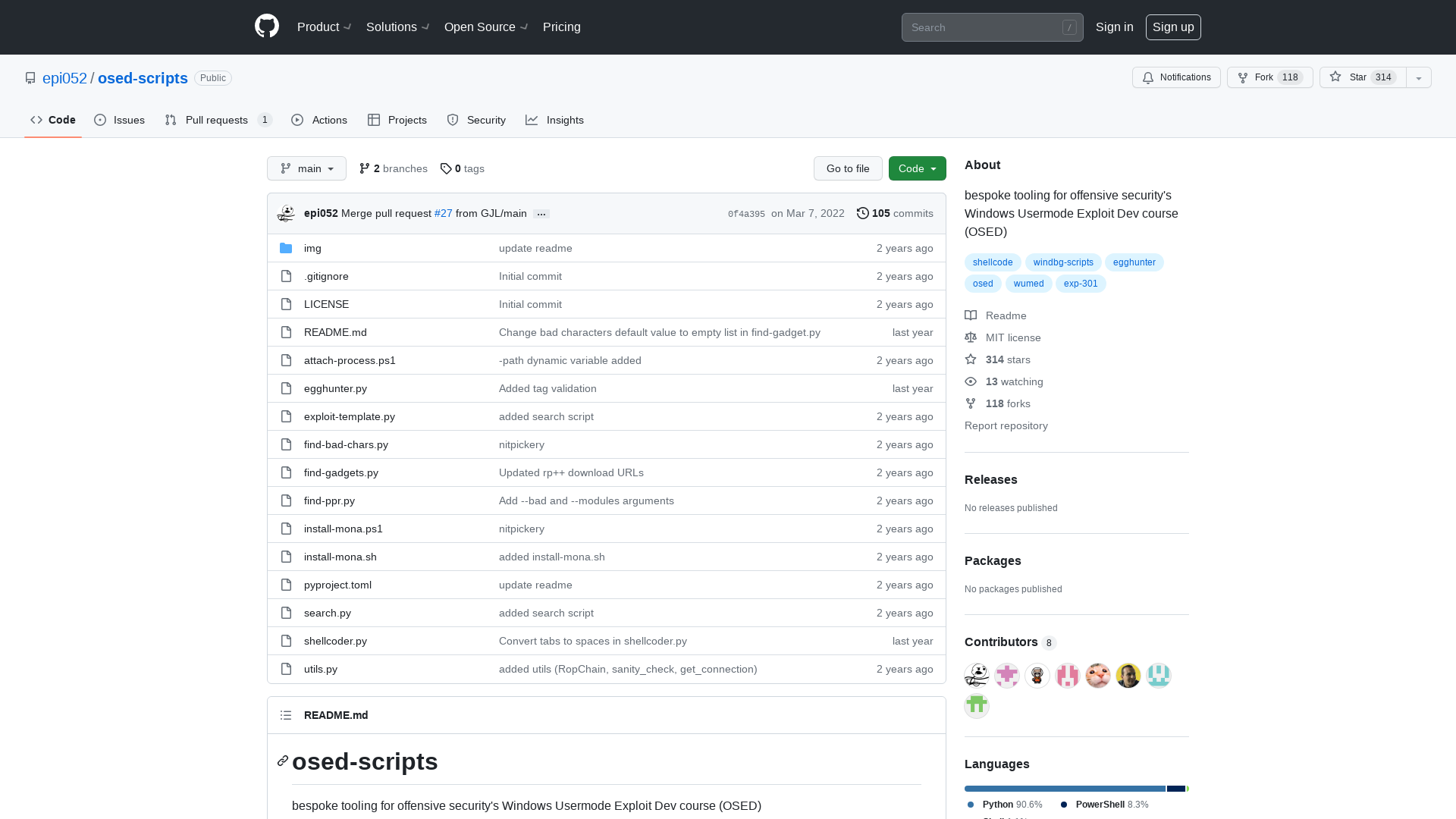
InfoSec Handlers Diary Blog - SANS Internet Storm Center
https://i5c.us/d29818
PC Classics, Right In Your Browser With EmuOS | Hackaday
https://hackaday.com/2023/05/06/pc-classics-right-in-your-browser-with-emuos/
0xToxin🕷️ on Twitter: "#BlindEagle operation review: opendir - https://t.co/6ST8oCyPFF (this account hosted on Colombia Movil, explained later in the post...) camapigns towards Colombia 🇨🇴 📊 4 payloads: 🐀 3 AsyncRAT (2 used during April, 1 during May) 🏹 1 Remcos ⚠️ C2: 177.255.89[.112… https://t.co/YFWyCbw3Gb" / Twitter
https://twitter.com/i/web/status/1654802474534830080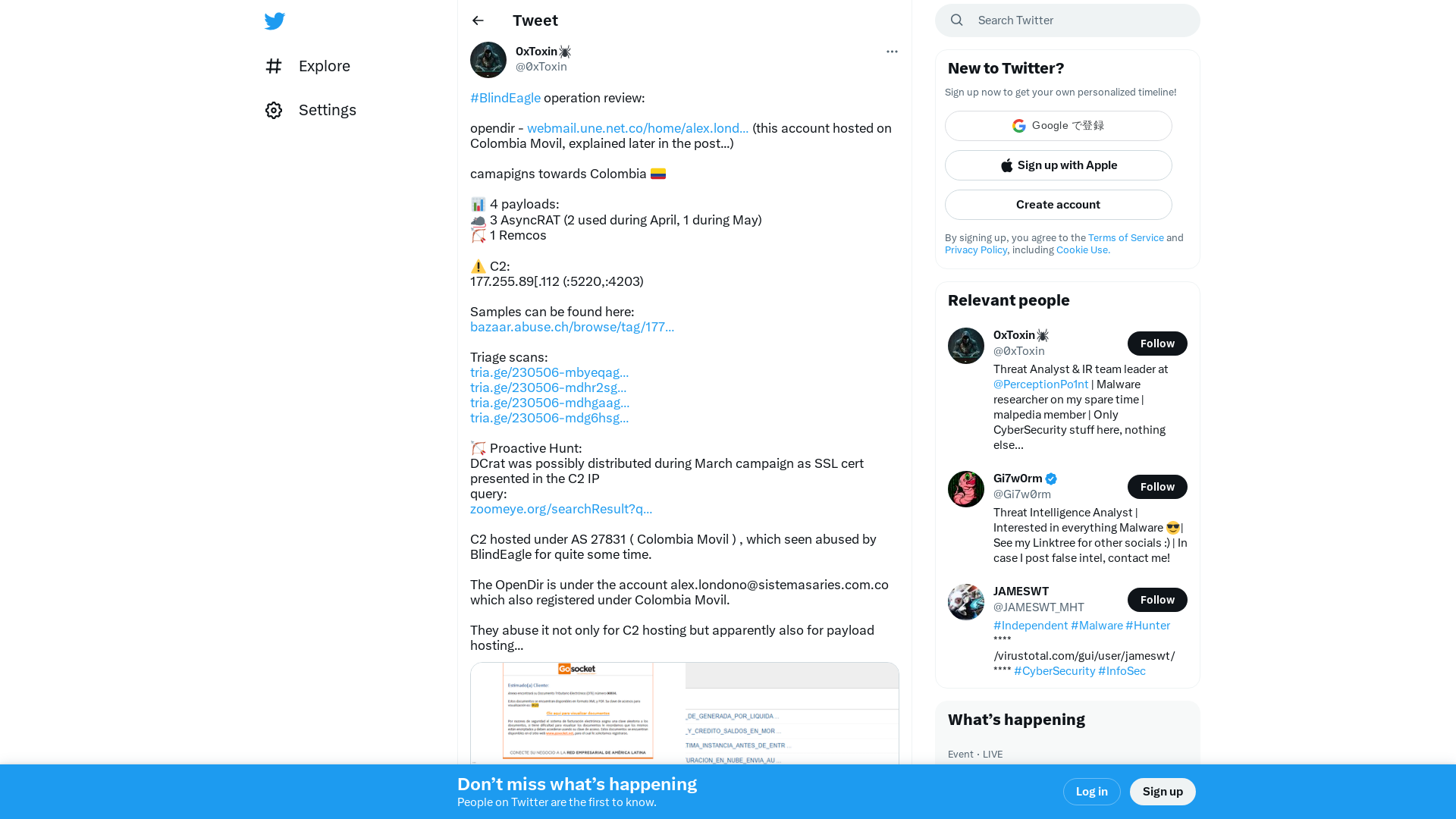
Telegram: Contact @hackgit
https://t.me/hackgit/8600
chompie on Twitter: "I have hard time describing my job and what I do on a day to day basis but I think “weird machine mechanic” puts it succinctly" / Twitter
https://twitter.com/chompie1337/status/1654932554405892096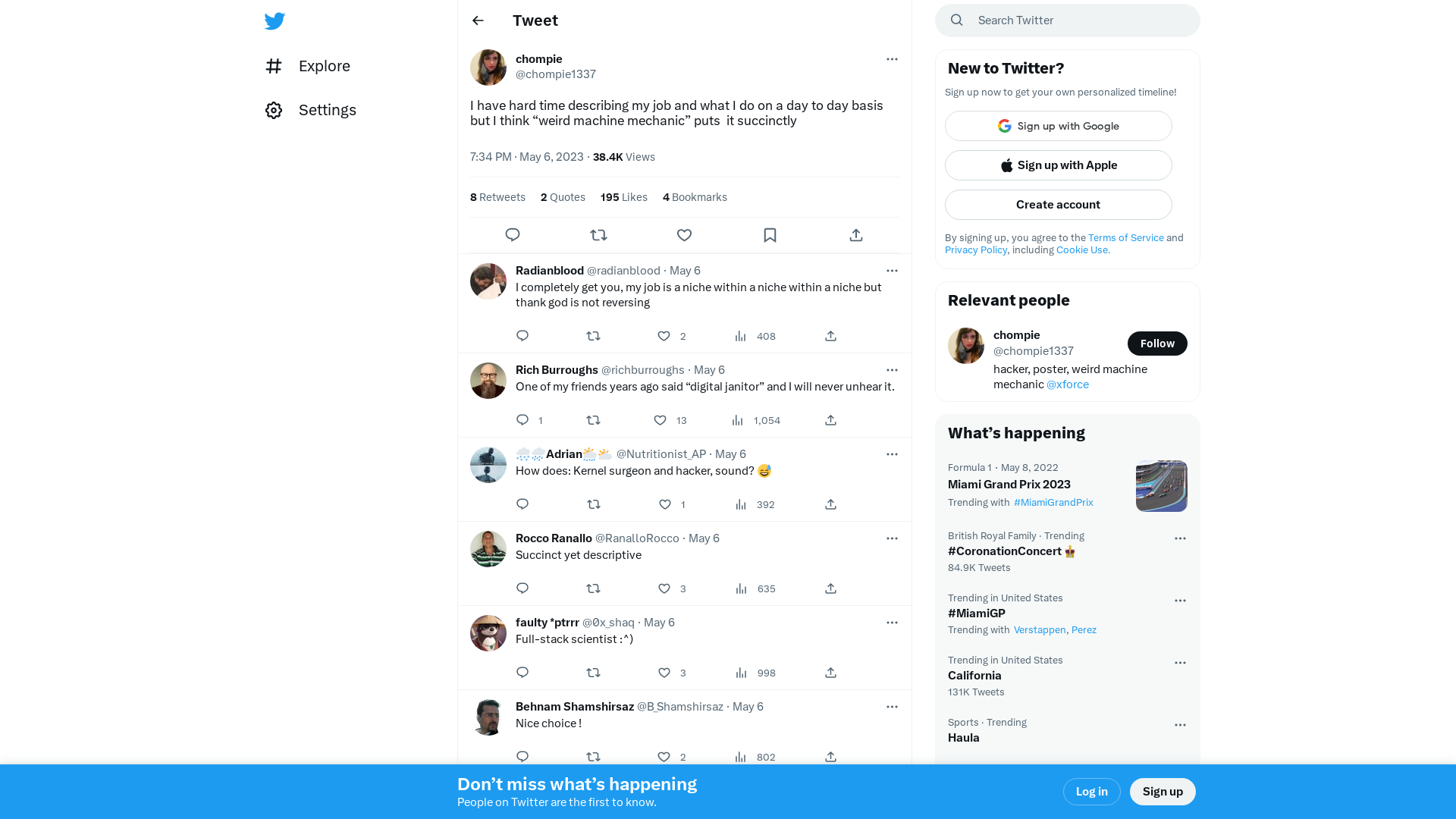
Exploiting an Order of Operations Bug to Achieve RCE in Oracle Opera – Assetnote
https://blog.assetnote.io/2023/04/30/rce-oracle-opera/