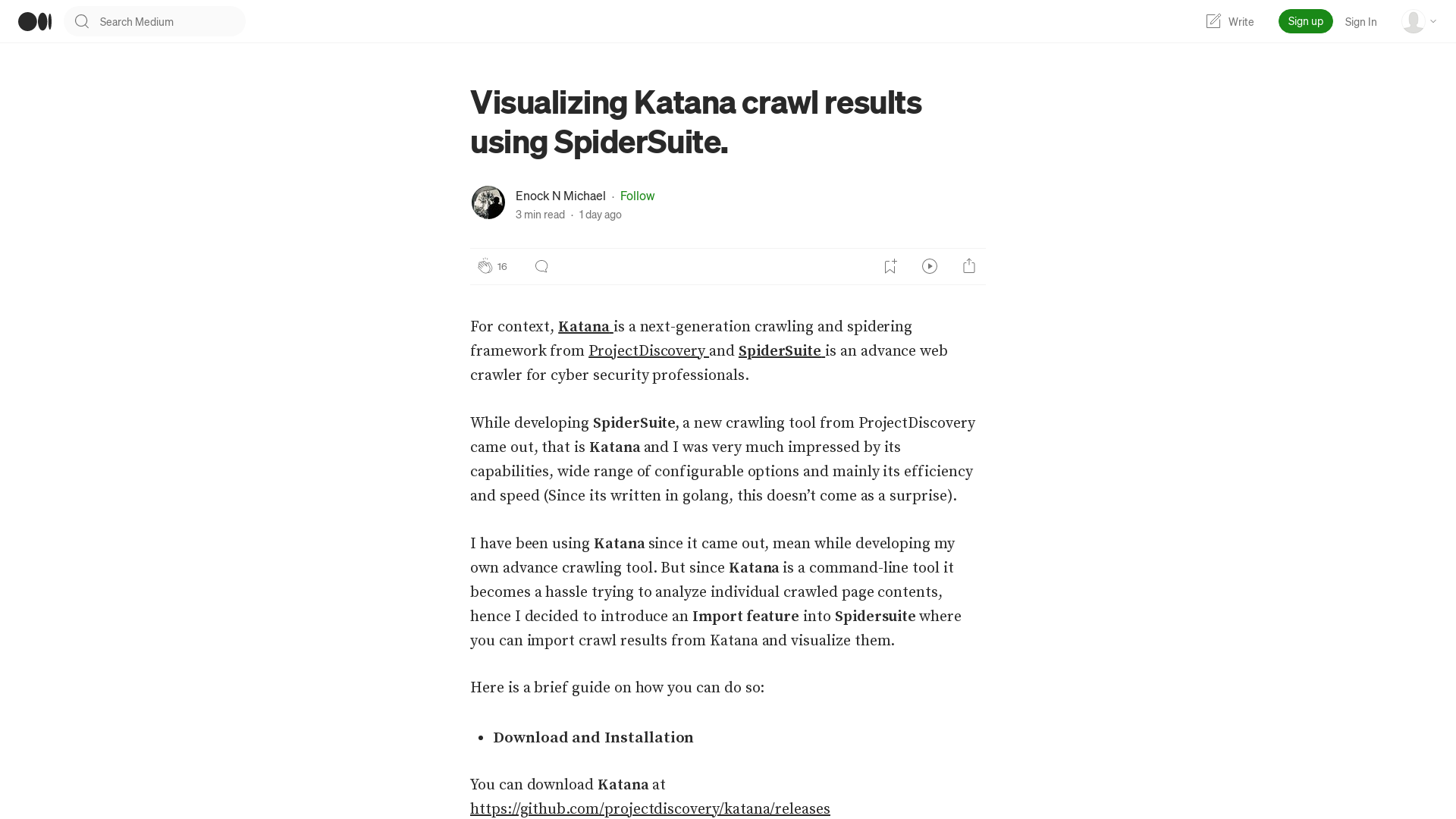
BINARLY🔬 on Twitter: "⛓️Digging deeper into the aftermath of the @msiUSA data breach and its impact on the industry. 🔥Leaked Intel BootGuard keys from MSI are affecting many different device vendors, including @Intel , @Lenovo, @Supermicro_SMCI, and many others industry-wide. 🔬#FwHunt is on! https://t.co/ZB8XKj33Hv" / Twitter
https://twitter.com/binarly_io/status/1654287041339998208
Cookie Bugs - Smuggling & Injection
https://blog.ankursundara.com/cookie-bugs/
ET Labs on Twitter: "Huge thanks to @BushidoToken this week for the elephant in the room of sig contributions - over 250 SIDs spanning 2045317-2045592 for Raspberry Robin Domain alerts. See them here: https://t.co/mwjzya38i0 from: https://t.co/u8zFa6ypYZ" / Twitter
https://twitter.com/et_labs/status/1654626028076105731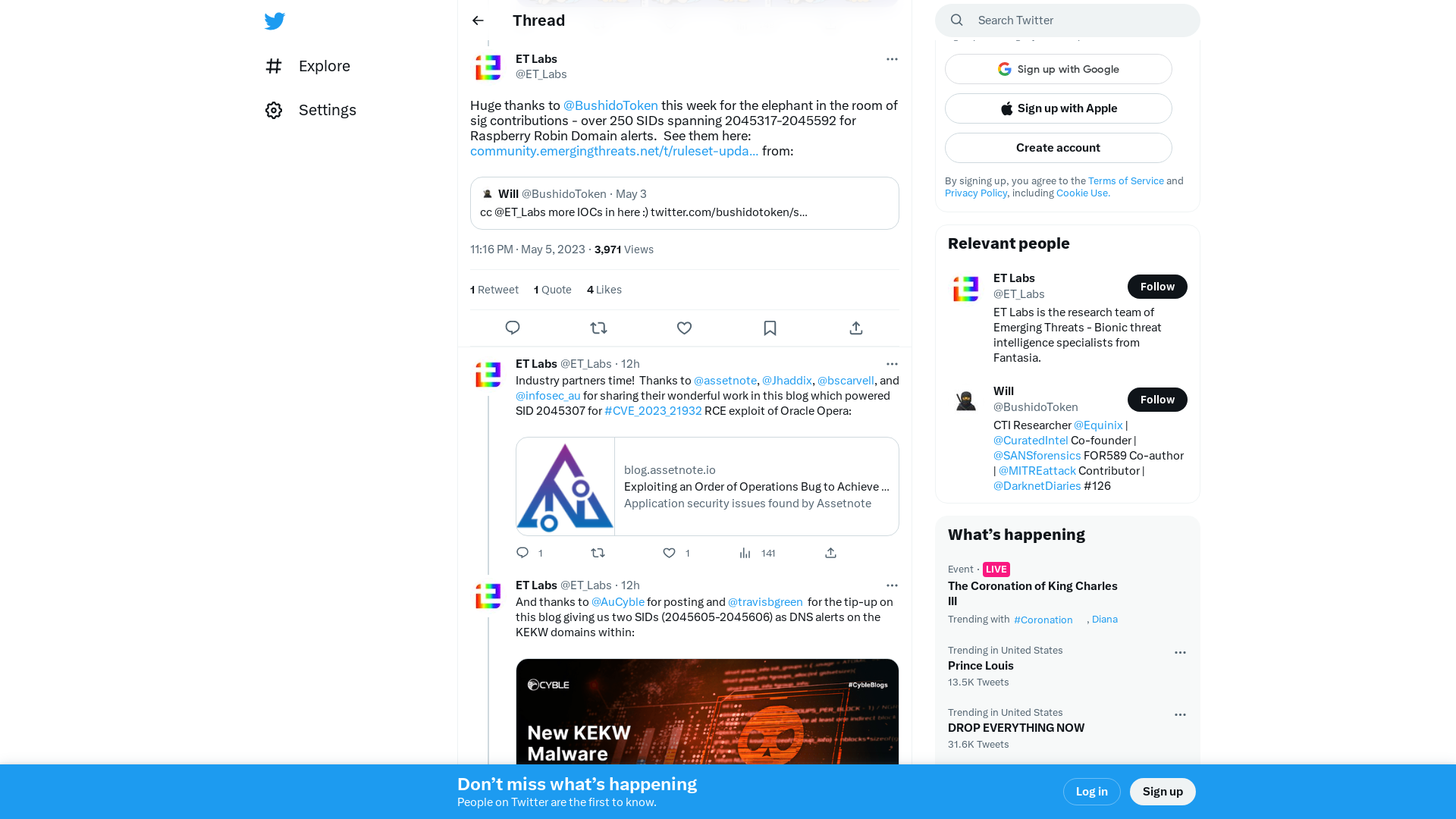
Microsoft Threat Intelligence on Twitter: "More actors are exploiting unpatched CVE-2023-27350 in print management software Papercut since we last reported on Lace Tempest. Microsoft has now observed Iranian state-sponsored threat actors Mint Sandstorm (PHOSPHORUS) & Mango Sandstorm (MERCURY) exploiting CVE-2023-27350." / Twitter
https://twitter.com/MsftSecIntel/status/1654610012457648129
Alex Matrosov on Twitter: "⛓️Confirmed, Intel OEM private key leaked, causing an impact on the entire ecosystem. It appears that Intel BootGuard may not be effective on certain devices based on the 11th Tiger Lake, 12th Adler Lake, and 13th Raptor Lake. Our investigation is ongoing, stay tuned for updates. https://t.co/fLopw1qeSD" / Twitter
https://twitter.com/matrosov/status/1654560343295934464
oss-sec: Re: double-free vulnerability in OpenSSH server 9.1 (CVE-2023-25136)
https://seclists.org/oss-sec/2023/q1/92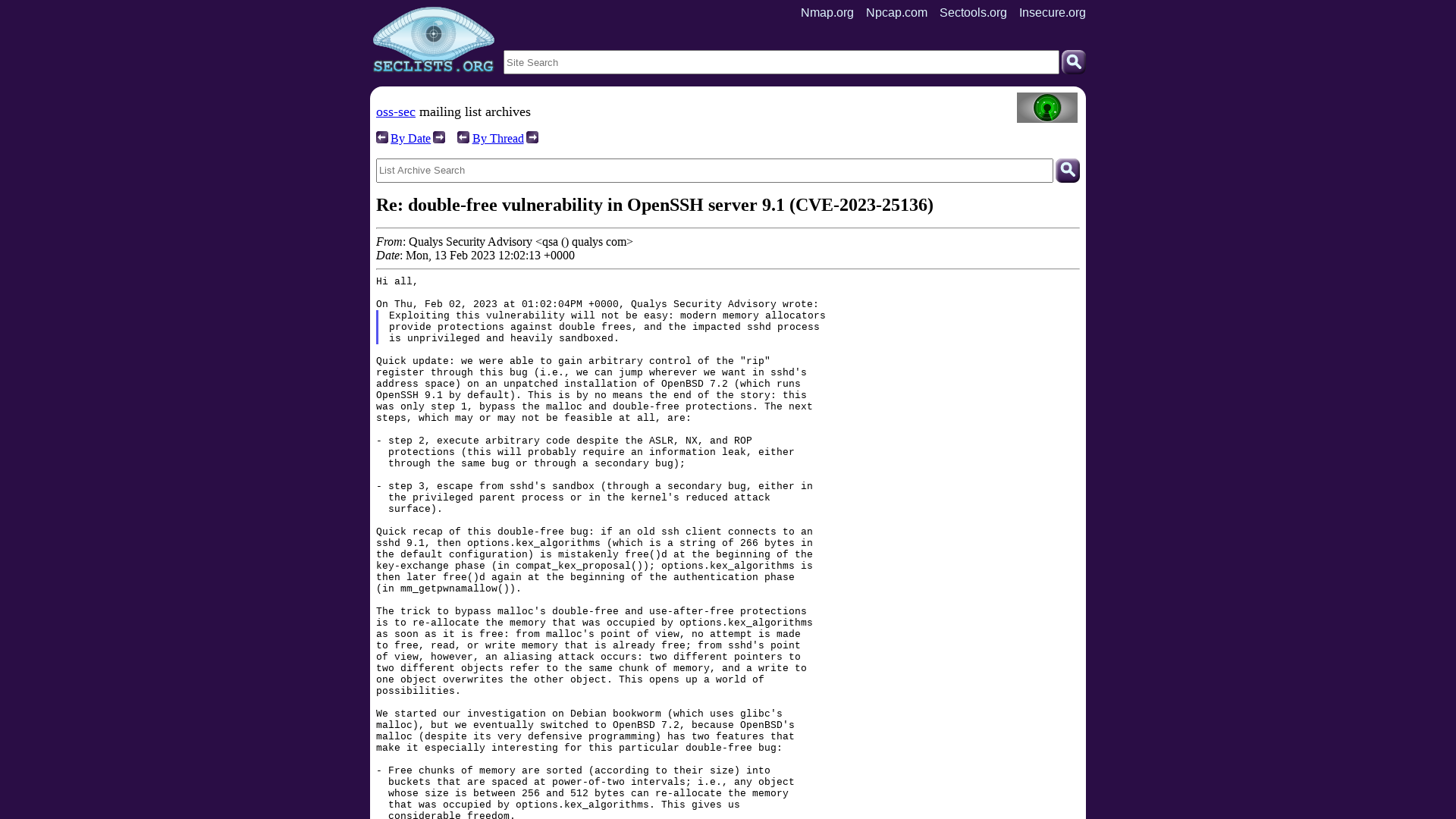
GitHub - glavstroy/CVE-2023-28231: DHCP Server Remote Code Execution impact: 2008 R2 SP1 до Server 2019
https://github.com/glavstroy/CVE-2023-28231
CVE-2023-25136 OpenSSH Pre-Auth Double Free Writeup & PoC
https://jfrog.com/blog/openssh-pre-auth-double-free-cve-2023-25136-writeup-and-proof-of-concept/
Metasploit Weekly Wrap-Up: May 5, 2023 | Rapid7 Blog
https://www.rapid7.com/blog/post/2023/05/05/metasploit-weekly-wrap-up-9/
Intel OEM Private Key Leak: A Blow to UEFI Secure Boot Security
https://securityonline.info/intel-oem-private-key-leak-a-blow-to-uefi-secure-boot-security/
Jon Gorenflo 🇺🇦🌻 on Twitter: "#OSINT Tip: Did you know you can recover scrubbed metadata from a PDF that wasn't scrubbed properly? The changes are incremental, and the history is stored in the PDF. This command removes the "updates" to the PDF metadata: exiftool -PDF-update:all= file.pdf https://t.co/jMB9sfOA0k" / Twitter
https://twitter.com/i/web/status/1654617325520433152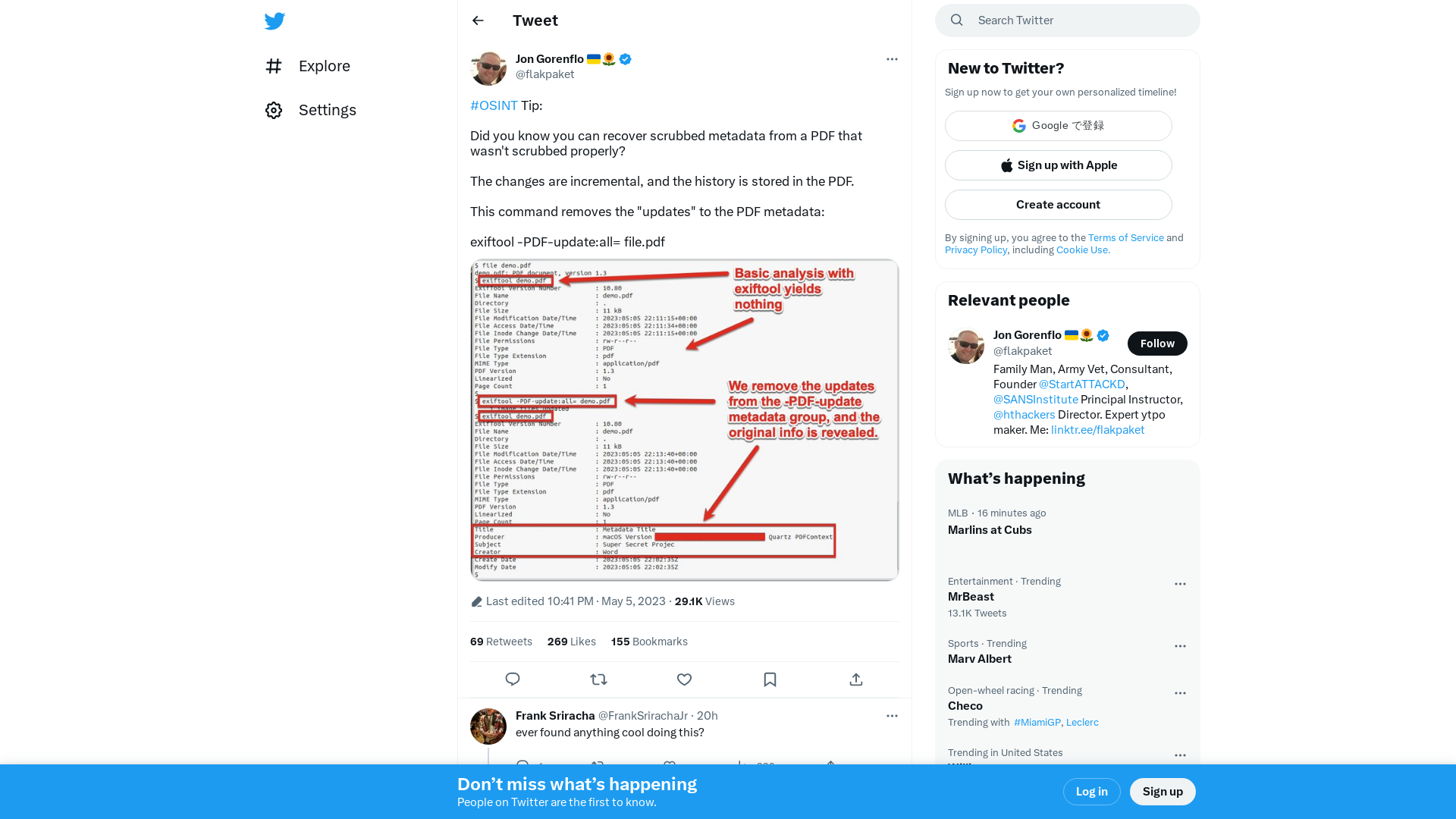
Twitter says 'security incident' exposed private Circle tweets
https://www.bleepingcomputer.com/news/security/twitter-says-security-incident-exposed-private-circle-tweets/
https://webmail.une.net.co/home/[email protected]/Briefcase/
https://webmail.une.net.co/home/[email protected]/Briefcase/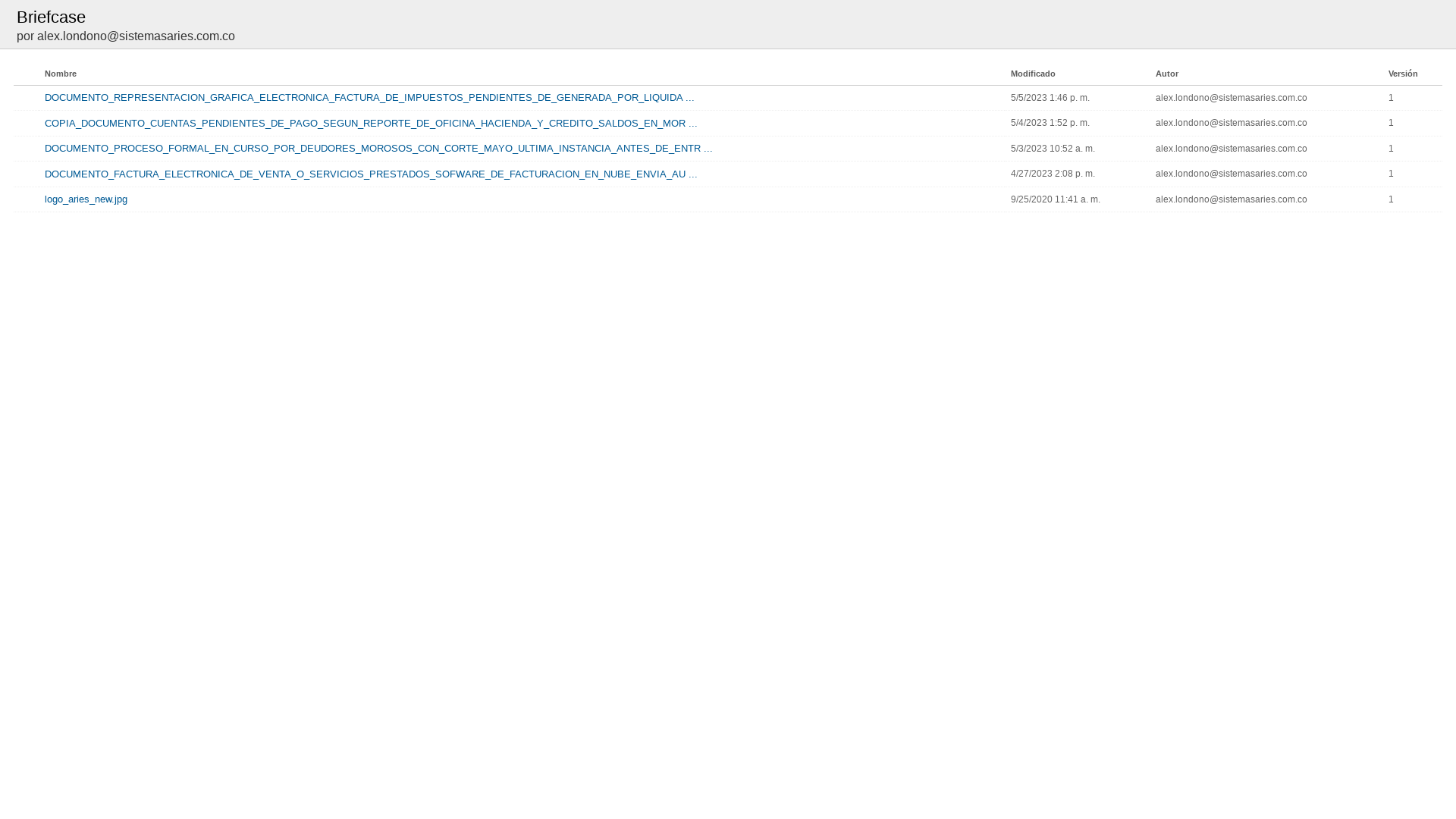
Microsoft Threat Intelligence on Twitter: "More actors are exploiting unpatched CVE-2023-27350 in print management software Papercut since we last reported on Lace Tempest. Microsoft has now observed Iranian state-sponsored threat actors Mint Sandstorm (PHOSPHORUS) & Mango Sandstorm (MERCURY) exploiting CVE-2023-27350." / Twitter
https://twitter.com/msftsecintel/status/1654610012457648129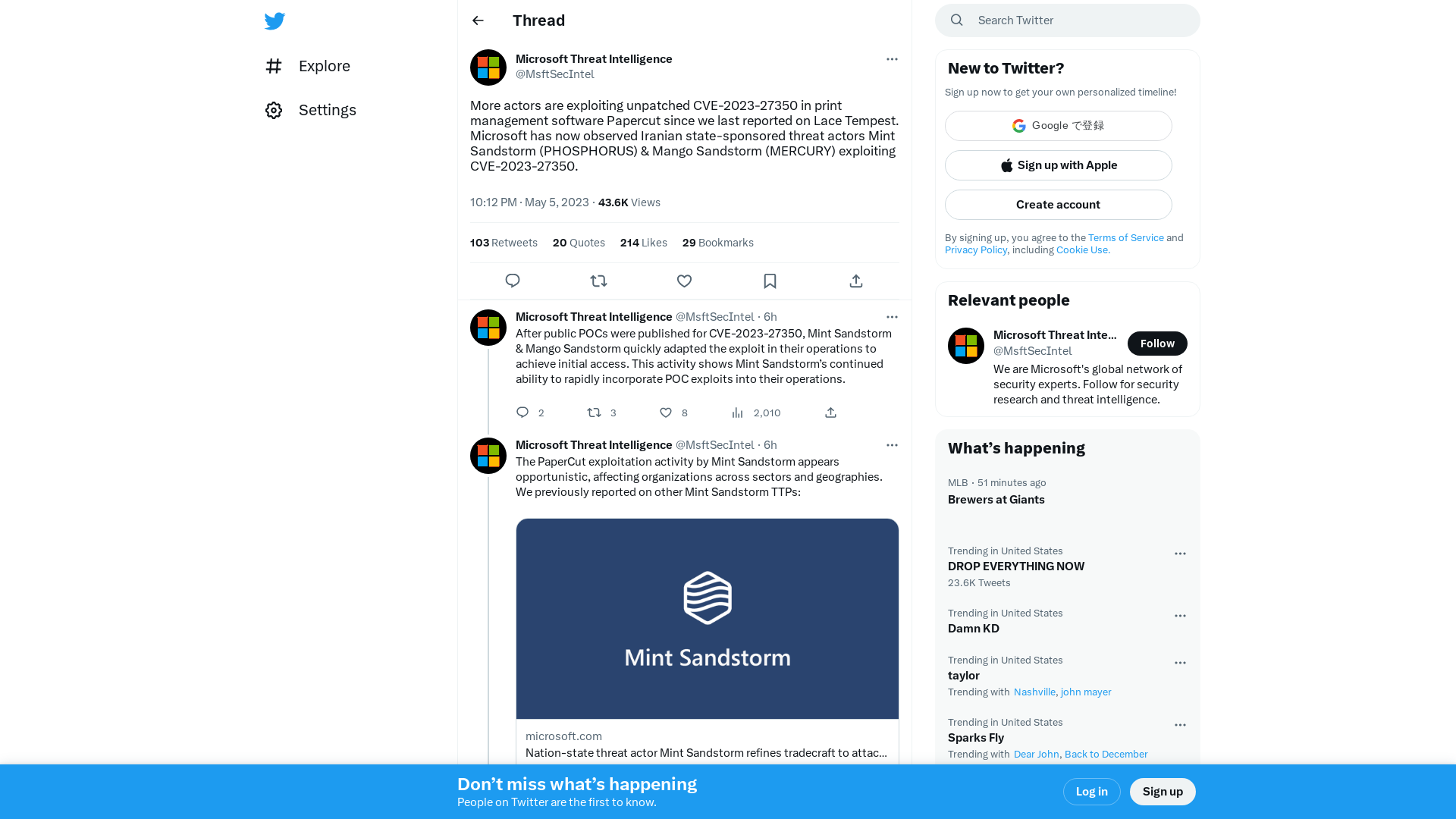
0xToxin🕷️ on Twitter: "#BlindEagle operation review: opendir - https://t.co/6ST8oCyPFF (this account hosted on Colombia Movil, explained later in the post...) camapigns towards Colombia 🇨🇴 📊 4 payloads: 🐀 3 AsyncRAT (2 used during April, 1 during May) 🏹 1 Remcos ⚠️ C2: 177.255.89[.112… https://t.co/YFWyCbw3Gb" / Twitter
https://twitter.com/i/web/status/1654802474534830080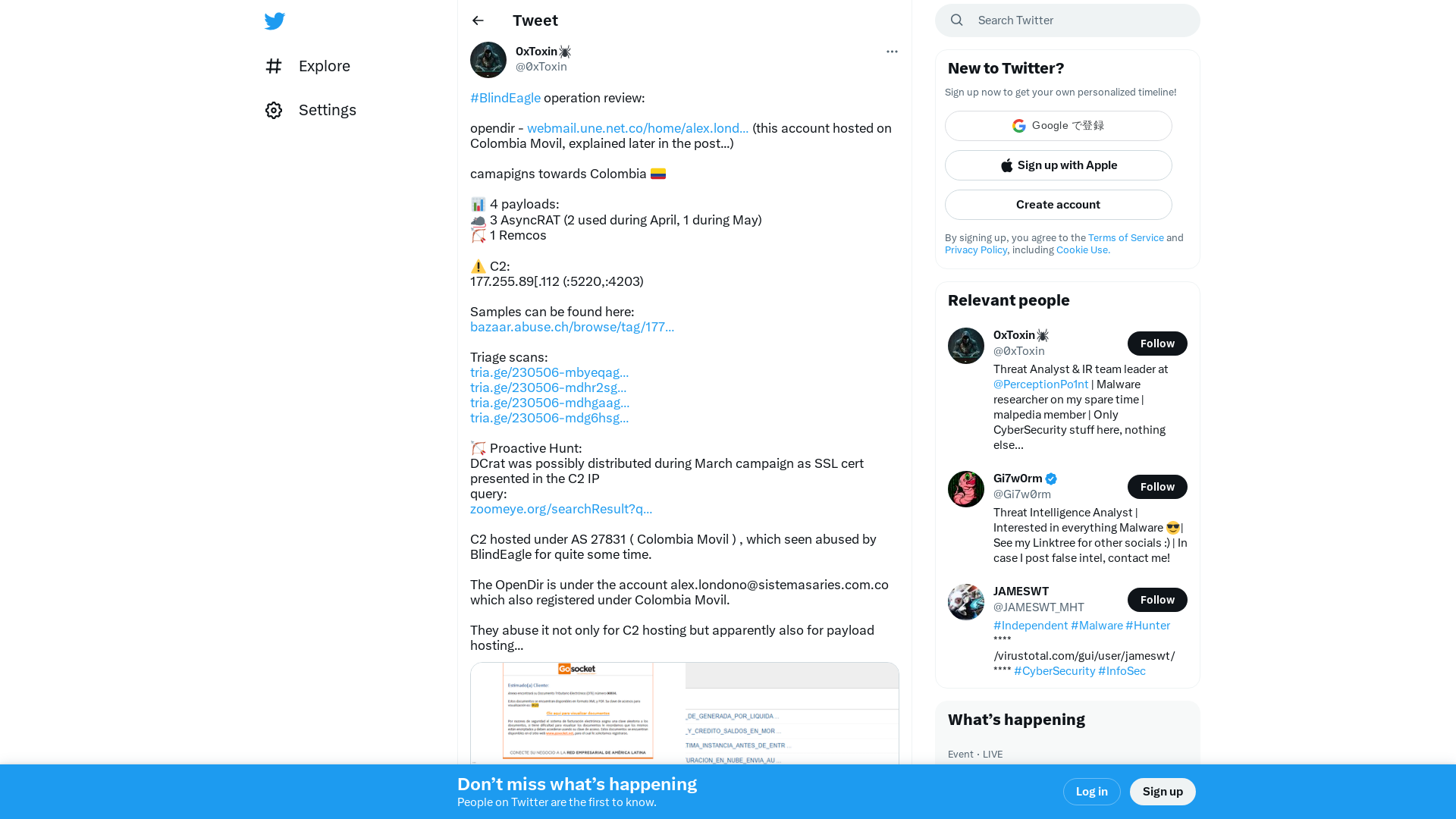
Dragon Breath APT Group Using Double-Clean-App Technique to Target Gambling Industry
https://thehackernews.com/2023/05/dragon-breath-apt-group-using-double.html
Ptrace Security GmbH on Twitter: "Lab - Certificate Authority Setup https://t.co/7z9BmEo1su #Pentesting #CyberSecurity #Infosec https://t.co/7bVQHK7dry" / Twitter
https://twitter.com/i/web/status/1654773153493667842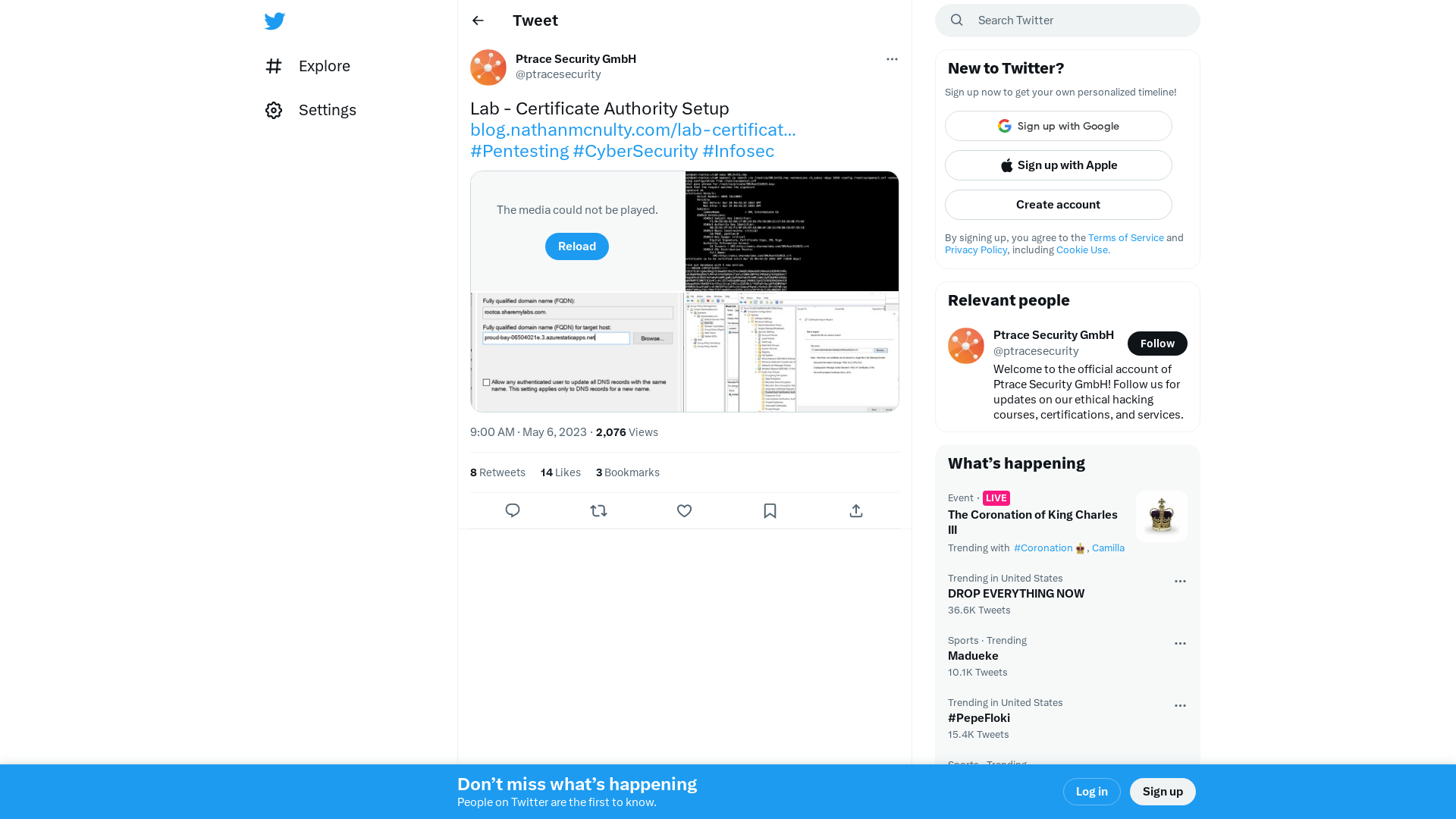
Lack of Visibility: The Challenge of Protecting Websites from Third-Party Scripts
https://thehackernews.com/2023/05/lack-of-visibility-challenge-of.html
CVE-2021-38001: A Brief Introduction to V8 Inline Cache and Exploitating Type Confusion – !
http://y4y.space/2023/05/06/cve-2021-38001-a-brief-introduction-to-v8-inline-cache-and-exploitating-type-confusion/
A smorgasbord of a bug chain: postMessage, JSONP, WAF bypass, DOM-based XSS, CORS, CSRF... :: jub0bs.com
https://jub0bs.com/posts/2023-05-05-smorgasbord-of-a-bug-chain/
「勝手に学ぶ人」と「期待されて学ぶ人」の差が埋められない|柴田史郎|note
https://note.com/4bata/n/nf8fbcb832e91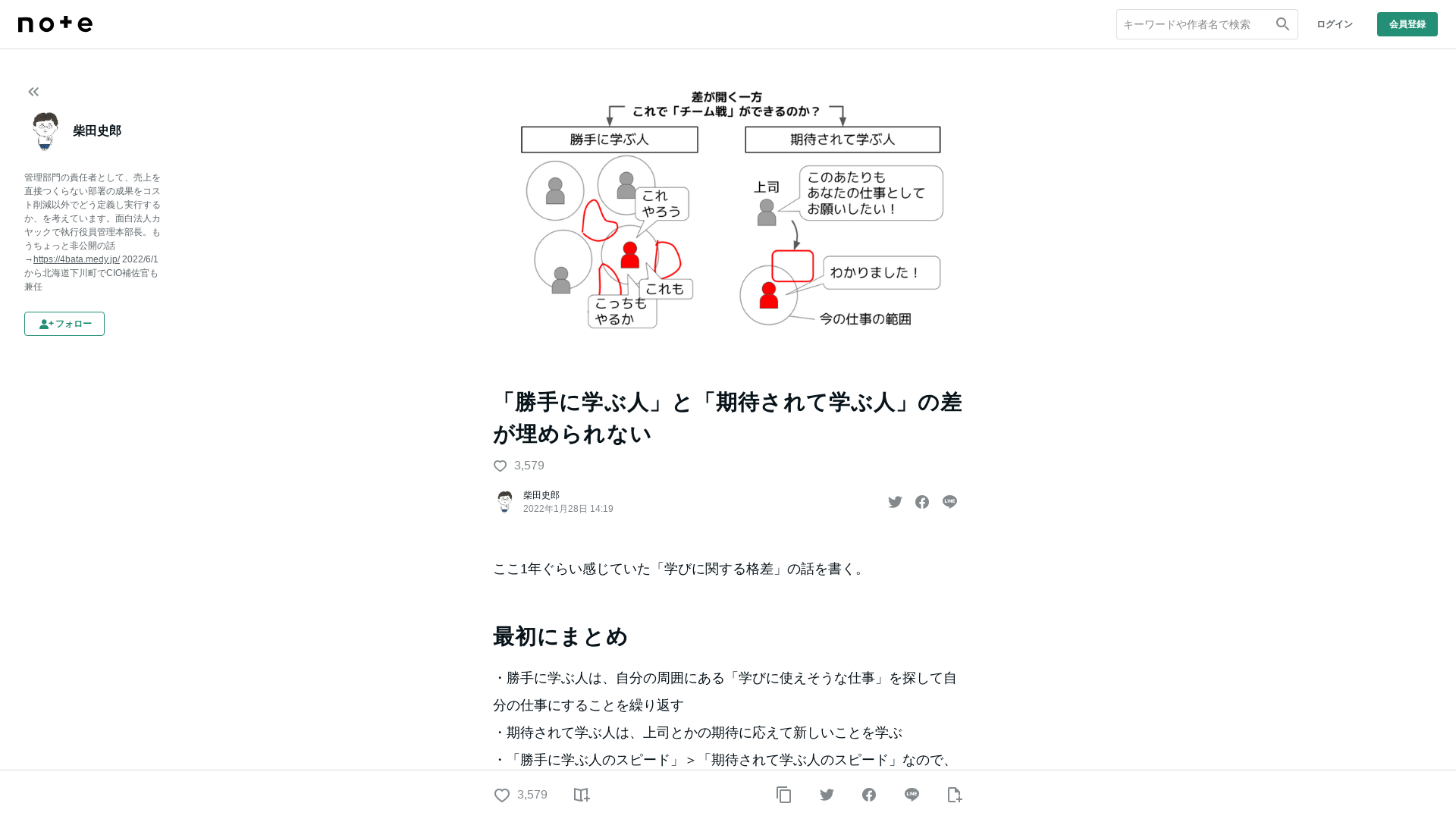
New Android FluHorse malware steals your passwords, 2FA codes
https://www.bleepingcomputer.com/news/security/new-android-fluhorse-malware-steals-your-passwords-2fa-codes/
Coming to DEF CON 31: Hacking AI models | CyberScoop
https://cyberscoop.com/def-con-red-teaming-ai/
New Vulnerability in Popular WordPress Plugin Exposes Over 2 Million Sites to Cyberattacks
https://thehackernews.com/2023/05/new-vulnerability-in-popular-wordpress.html
Lab - Certificate Authority Setup
https://blog.nathanmcnulty.com/lab-certificate-authority-setup/
WordPress Advanced Custom Fields plugin XSS exposes +2M sites to attacksSecurity Affairs
https://securityaffairs.com/145847/hacking/wordpress-advanced-custom-fields-xss.html
misc/CVE-2023-28231_poc.py at master · omair2084/misc · GitHub
https://github.com/omair2084/misc/blob/master/CVE-2023-28231_poc.py
Capita’s “standard industry practice” 633gb open cloud storage | by Kevin Beaumont | May, 2023 | DoublePulsar
https://doublepulsar.com/capitas-standard-industry-practice-633gb-open-cloud-storage-5d87e7e96a70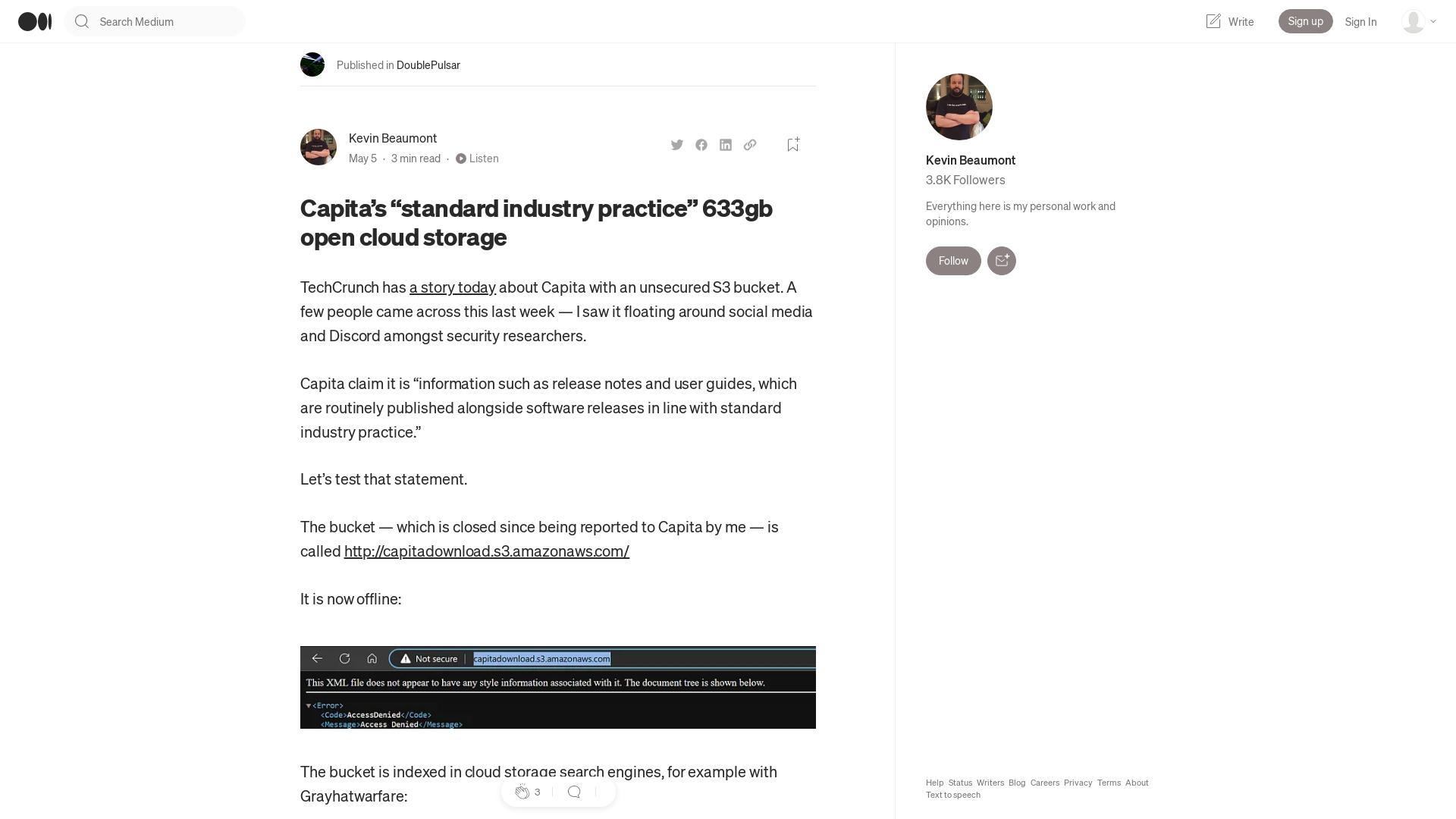
@mikko on Twitter: "40 years ago, on May 5th 1983, Atari released Star Wars. The game was *amazing*, with color vector graphics. https://t.co/SdjQzC3mjF" / Twitter
https://twitter.com/mikko/status/1654545573792342016
Evilginx Mastery
https://academy.breakdev.org/evilginx-mastery
ABC7 Eyewitness News on Twitter: "#BREAKING San Bernardino County pays $1.1 million ransom after hackers access Sheriff's Dept. systems. https://t.co/tjdNvjTXAf" / Twitter
https://twitter.com/abc7/status/1654592654506876929
APT_REPORT/Anonymous-Sudan-Report.pdf at master · blackorbird/APT_REPORT · GitHub
https://github.com/blackorbird/APT_REPORT/blob/master/Anonymous/Anonymous-Sudan-Report.pdf
Red Team Village - Cybersecurity Training and Briefings
https://redteamvillage.io/
SwiftOnSecurity on Twitter: "WARNING: I asked ChatGPT for references of malware analysts accidentally running malware, and it hallucinated a story about @msuiche. He confirms that DID NOT HAPPEN. He was involved in analyzing NotPetya and talking to the press, but this story never occurred! Be careful verify https://t.co/Q5F15yrOy1" / Twitter
https://twitter.com/swiftonsecurity/status/1654676071663509505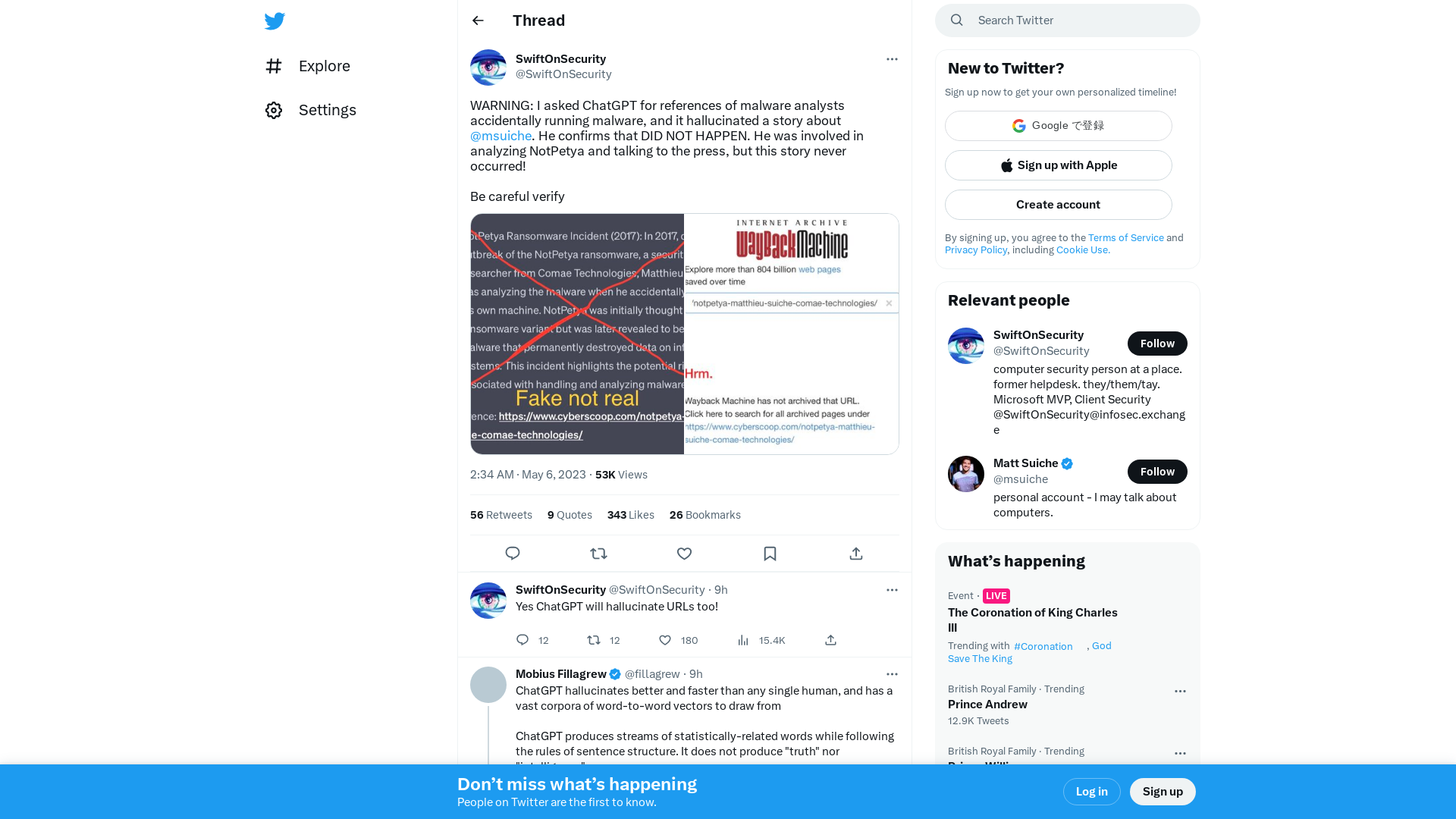
GitHub - Malwareman007/CVE-2023-27326: VM Escape for Parallels Desktop <18.1.1
https://github.com/Malwareman007/CVE-2023-27326
c3rb3ru5d3d53c - Twitch
https://twitch.tv/c3rb3ru5d3d53c
InfoSec Handlers Diary Blog - SANS Internet Storm Center
https://i5c.us/d29816
Visualizing Katana crawl results using SpiderSuite. | by Enock N Michael | May, 2023 | Medium
https://medium.com/@enock.n.michael/visualizing-katana-crawl-results-using-spidersuite-a49c853f24ee