GitHub - mubix/nfsclient: NFS client written in Go
https://github.com/mubix/nfsclient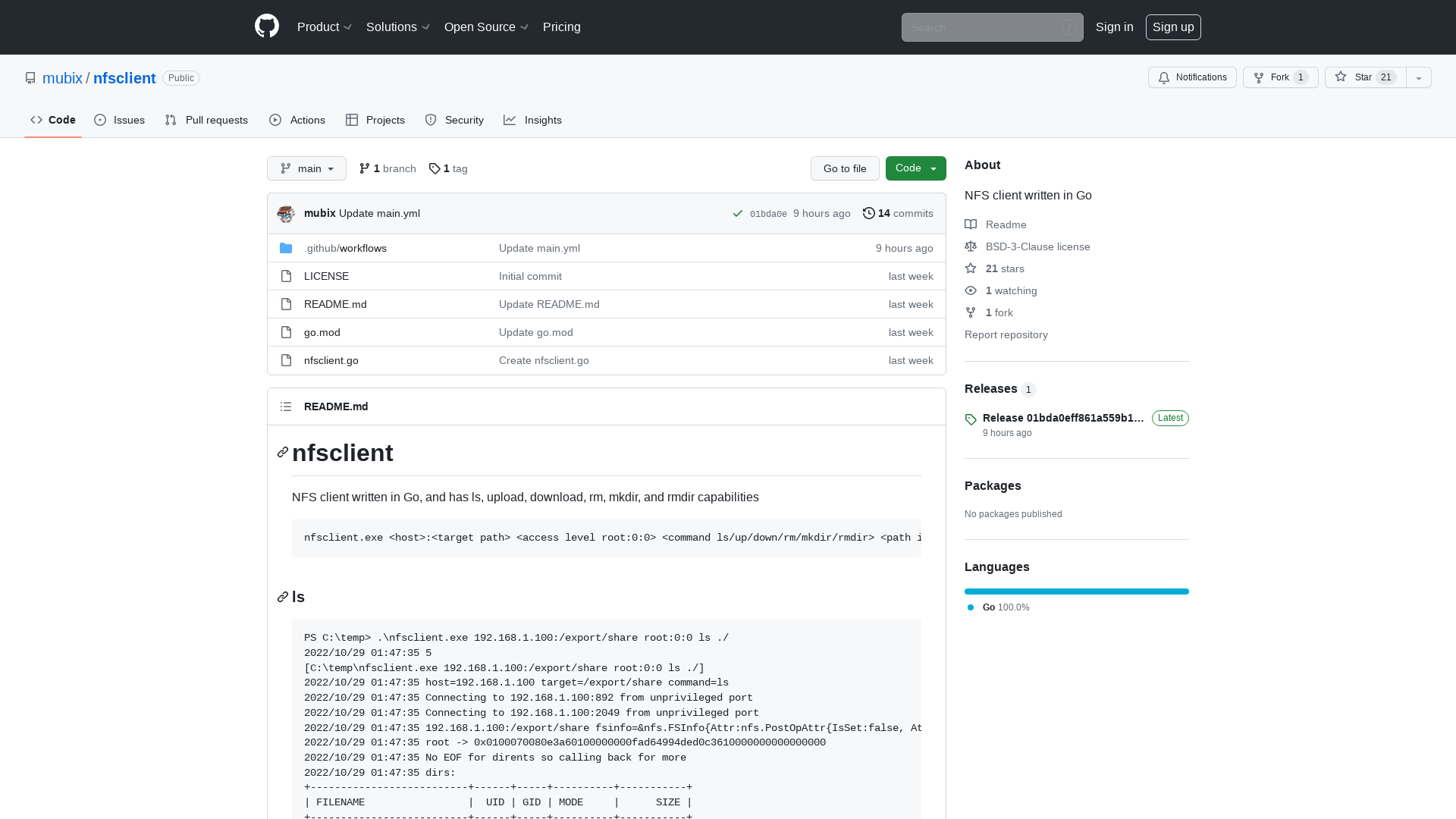
LummaC2 BreakDown - 0xToxin Labs
https://0xtoxin-labs.gitbook.io/malware-analysis/malware-analysis/lummac2-breakdown
From Discord to 4chan: The Improbable Journey of a US Intelligence Leak - bellingcat
https://www.bellingcat.com/news/2023/04/09/from-discord-to-4chan-the-improbable-journey-of-a-us-defence-leak/
GitHub - screamz2k/PhoenixC2: Command & Control-Framework created for collaboration in python3
https://github.com/screamz2k/PhoenixC2
Michael Koczwara on Twitter: "Hunting Sliver C2 infra 🎯 Threat Actors when deploying Sliver C2 sometimes change default ports from 31337 to other ones for example 3000, 3306, 8089, and so on so scanning only 31337 is not always enough. Censys filter below is checking Sliver default certificates also in… https://t.co/kDVfGGpTv4" / Twitter
https://twitter.com/i/web/status/1645002394734845956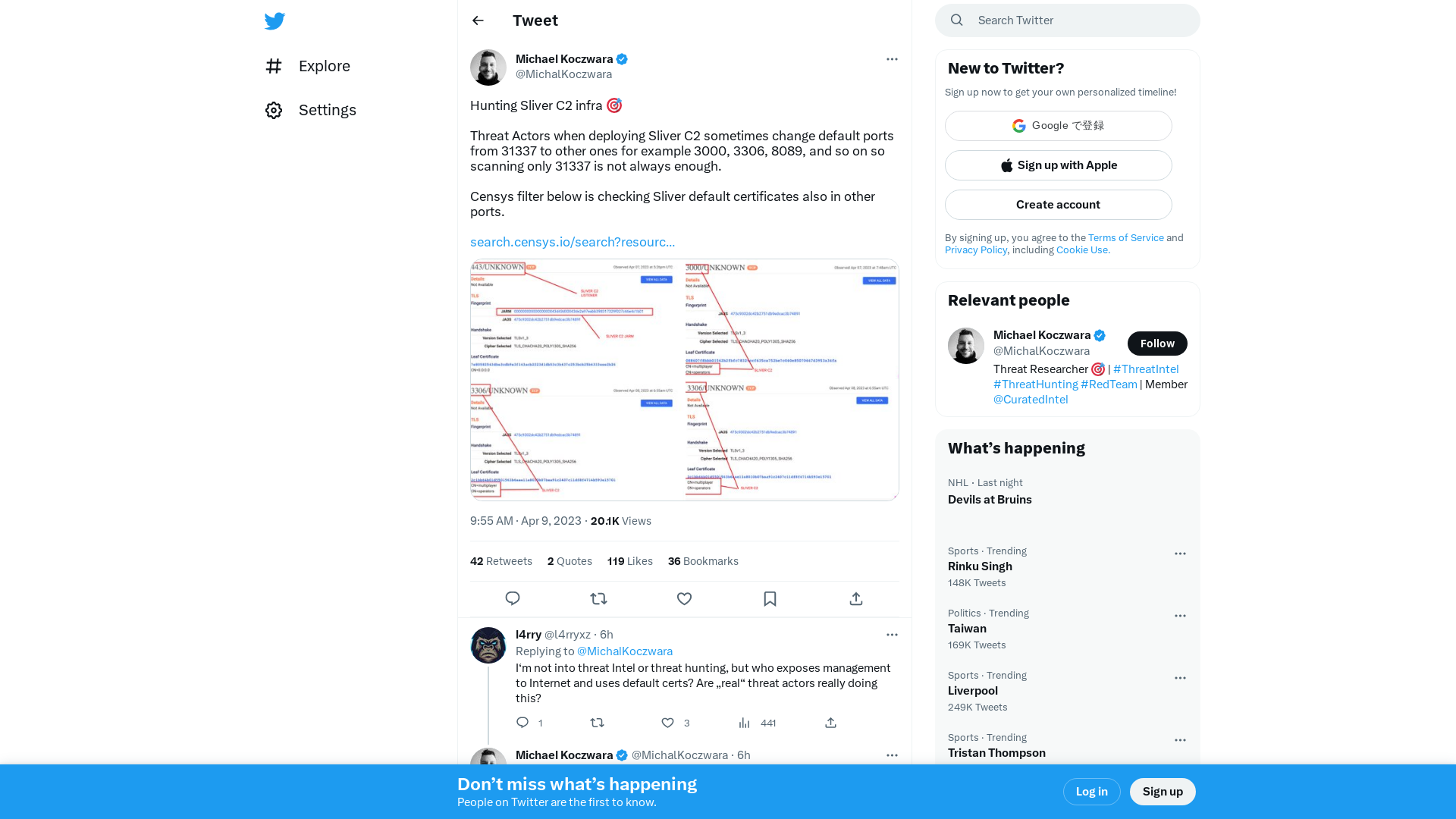
GitHub - ald3ns/copy-as-yara: This is a little plugin to copy disassembly in a way that is usable in YARA rules!
https://github.com/ald3ns/copy-as-yara
Intelligence leak exposes U.S. spying on adversaries and allies - The Washington Post
https://www.washingtonpost.com/national-security/2023/04/08/intelligence-leak-documents-ukraine-pentagon/
Spain's most dangerous and elusive hacker now in police custody
https://www.bleepingcomputer.com/news/security/spains-most-dangerous-and-elusive-hacker-now-in-police-custody/
A Tale of .Net Deobfuscation - VirtualGuard Devirtualization
https://mrt4ntr4.github.io/VirtualGuard-P2/
A Tale of .Net Deobfuscation - VirtualGuard Basics
https://mrt4ntr4.github.io/VirtualGuard-P1/
Inside the international sting operation to catch North Korean crypto hackers | CNN Politics
https://www.cnn.com/2023/04/09/politics/north-korean-crypto-hackers-crackdown/index.html
Taiwanese PC Company MSI Falls Victim to Ransomware Attack
https://thehackernews.com/2023/04/taiwanese-pc-company-msi-falls-victim.html
Self-Extracting Archives, Decoy Files and Their Hidden Payloads
https://www.crowdstrike.com/blog/self-extracting-archives-decoy-files-and-their-hidden-payloads/?utm_medium=soc&utm_source=twtr&utm_term=spklr&utm_content=9388227764&utm_campaign=%5Bglobal%5D&utm_activation=corporate+blog
Week 15 – 2023 – This Week In 4n6
http://thisweekin4n6.com/2023/04/09/week-15-2023/
BSidesCharm on Twitter: "BSidesCharm is officially sold out! We are counting down the final weeks for our exciting talks and villages, as well as the greatly anticipated keynotes from Matthew Green (@Matthew_d_green) and Elissa Shevinsky (@ElissaBeth)!" / Twitter
https://twitter.com/BSidesCharm/status/1643425182978121730
INSOMNIHACK 2023 - We hacked a box! - YouTube
https://www.youtube.com/watch?v=_IrZcSVIBVE
Bellingcat on Twitter: "We still don't know exactly who leaked the many US intel documents that have recently appeared online. But in a new @bellingcat investigation, @arictoler spoke to several people on the Discord server where they may have first originated. https://t.co/tdRuhBfztS" / Twitter
https://twitter.com/bellingcat/status/1644876019768217603
Michael Koczwara on Twitter: "Hunting Mythic C2 🎯 when 7443 default port is turned off Example 🤘 /44.213.147.172 /dental-delta.com default Mythic port 7443 is turned off but threat actors still need to learn (or maybe not?) a bit about opsec xD My hunting filter in Shodan HTTP/1.1 404 Not Found Server:… https://t.co/h4NqcjhSHd" / Twitter
https://twitter.com/i/web/status/1645071233468231685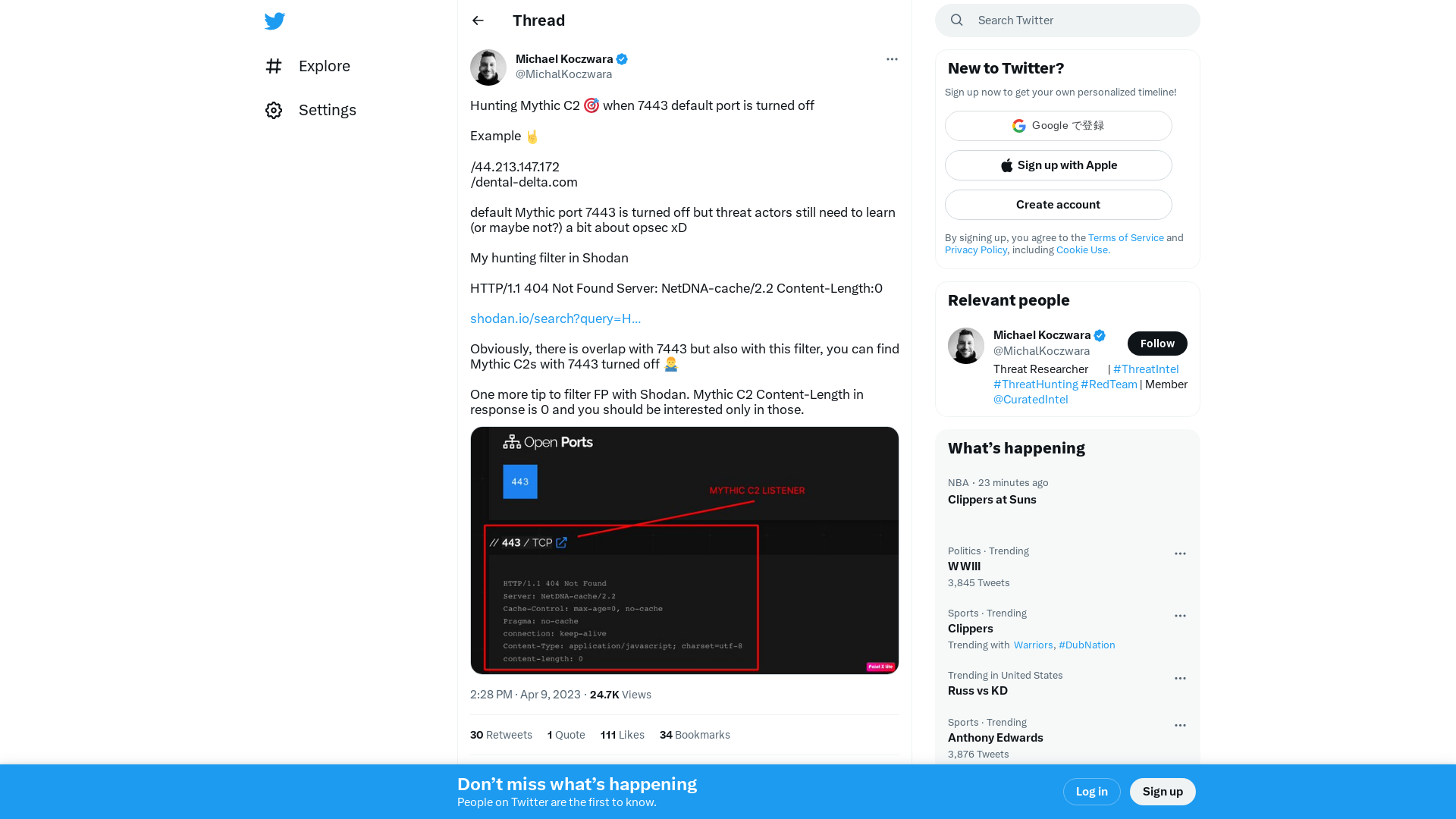
Breached shutdown sparks migration to ARES data leak forums
https://www.bleepingcomputer.com/news/security/breached-shutdown-sparks-migration-to-ares-data-leak-forums/
Uber data targeted in breach of third-party law firm | SC Media
https://bit.ly/3Mg2itL
#1888803 Use of Cryptographically Weak Pseudo-Random Number Generator in WebCrypto keygen
https://hackerone.com/reports/1888803
This Makes Hacking TOO Easy - Flipper Zero - YouTube
https://youtu.be/nLIp4wd0oXs
InfoSec Handlers Diary Blog - SANS Internet Storm Center
https://i5c.us/d29730
GitHub - lsecqt/OffensiveCpp: This repo contains C/C++ snippets that can be handy in specific offensive scenarios.
https://github.com/lsecqt/OffensiveCpp
Greg Linares (Mantis) on Twitter: "Attention anyone having an MSI motherboard or computer. MSI just said they were hacked and attackers might have tried modifying BIOS and software updates. Disable all updates from MSI for the time being https://t.co/7bm7yYT0Nv" / Twitter
https://twitter.com/Laughing_Mantis/status/1644571977225748481
All Dutch govt networks to use RPKI to prevent BGP hijacking
https://www.bleepingcomputer.com/news/security/all-dutch-govt-networks-to-use-rpki-to-prevent-bgp-hijacking/
Dcrat - Manual De-obfuscation of .NET malware
https://embee-research.ghost.io/dcrat-manual-de-obfuscation/
Cyber security news at your fingertips | Filter by topic or interest
http://cyberiqs.com/latestnews
GitHub - vu-ls/Crassus
https://github.com/vu-ls/Crassus
[QuickNote] Uncovering Suspected Malware Distributed By Individuals from Vietnam | 0day in {REA_TEAM}
https://kienmanowar.wordpress.com/2023/04/08/quicknote-uncovering-suspected-malware-distributed-by-individuals-from-vietnam/![[QuickNote] Uncovering Suspected Malware Distributed By Individuals from Vietnam | 0day in {REA_TEAM}](/image/screenshot/2c13a92c3163415f8890cf4916f6e71c.png)
Purpleteam/ThreatHunting.md at main · mthcht/Purpleteam · GitHub
https://github.com/mthcht/Purpleteam/blob/main/Logging/ThreatHunting.md
Rule Writing for CodeQL and Semgrep | Spaceraccoon's Blog
https://spaceraccoon.dev/comparing-rule-syntax-codeql-semgrep/
Hacking Brightway scooters: A case study – RoboCoffee
https://robocoffee.de/?p=436