Welcome to the Jungle: Pentesting AWS
https://www.slideshare.net/MichaelFelch/welcome-to-the-jungle-pentesting-aws
BleepingComputer on Twitter: "Microsoft OneNote will block 120 dangerous file extensions - @serghei https://t.co/6PxsZXXzRb" / Twitter
https://twitter.com/BleepinComputer/status/1641556008639115266
Pinduoduo: One of China's most popular apps has the ability to spy on its users, say experts | CNN Business
https://www.cnn.com/2023/04/02/tech/china-pinduoduo-malware-cybersecurity-analysis-intl-hnk/index.html
Fake ransomware gang targets U.S. orgs with empty data leak threats
https://www.bleepingcomputer.com/news/security/fake-ransomware-gang-targets-us-orgs-with-empty-data-leak-threats/
Hackers Use Password-Protected OneNote Files to Spread Malware | Perception Point
https://perception-point.io/blog/hackers-use-password-protected-onenote-files-to-spread-malware/
CISOtopia - The Cybersecurity Toy Store
https://www.cisotopia.com/
SANS 2023 | Cyber Security Training
https://www.sans.org/u/1o2c
GitHub - jsa2/caOptics: CA Optics - Azure AD Conditional Access Gap Analyzer
https://github.com/jsa2/caOptics
Lohitaksh Nandan on Twitter: "MFASweep - It's a PowerShell script that attempts to log in to various Microsoft services using a provided set of credentials and will attempt to identify if MFA is enabled. https://t.co/LKbzFUMCQf #cybersecurity #infosec #hacking #bugbounty https://t.co/JbbRYxwMTQ" / Twitter
https://twitter.com/NandanLohitaksh/status/1641757508913225728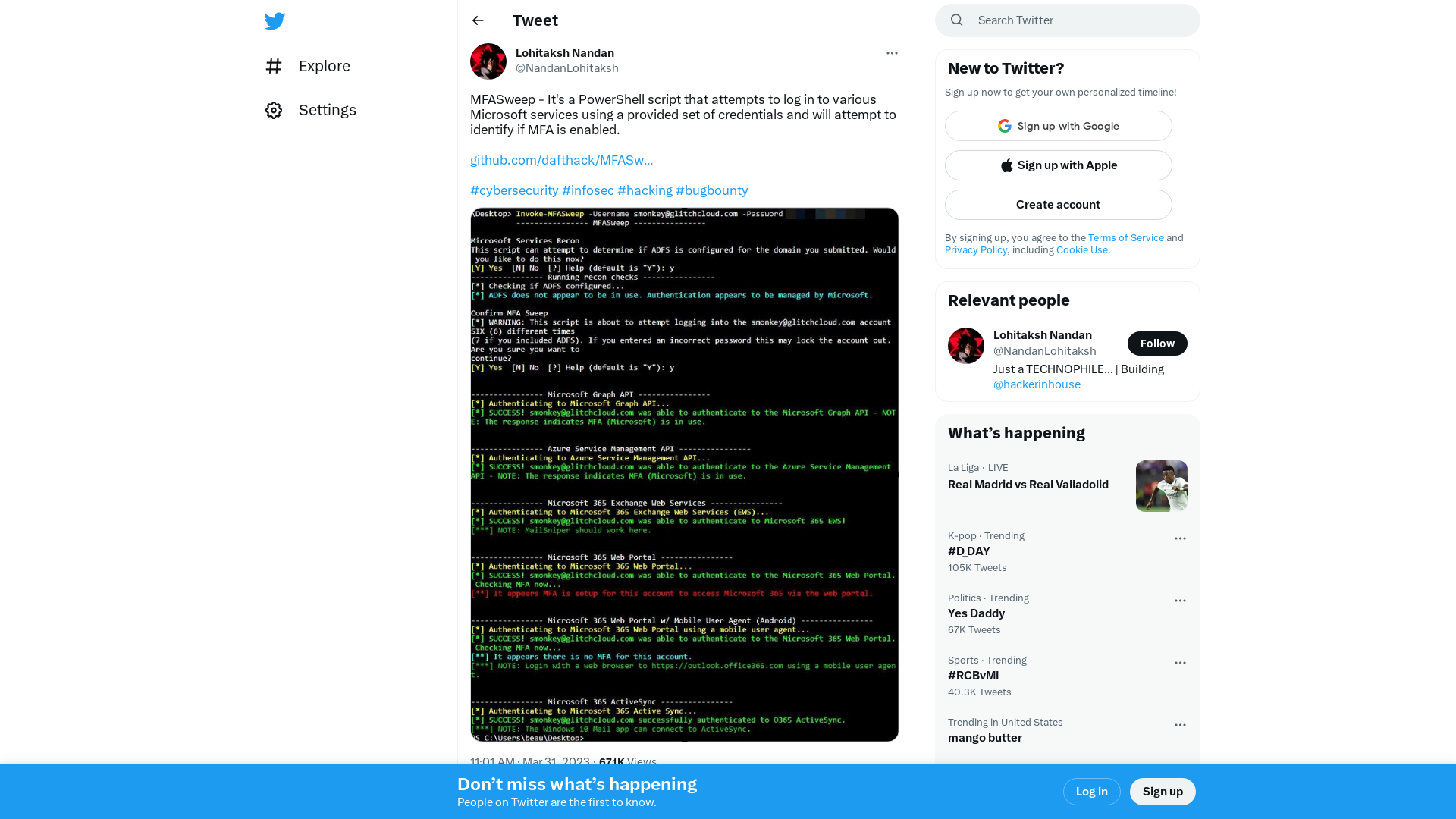
Mick Douglas 🇺🇦🌻 on Twitter: "JD1 attempting to threaten me. For the record, I stand behind what I've said this entire saga. I do wish I had used a different tone though. As a professional, I should do better. I should have been more cutting, and spent more time to better expose this charlatan. https://t.co/g5bB7NeLd3" / Twitter
https://twitter.com/bettersafetynet/status/1642415187767484416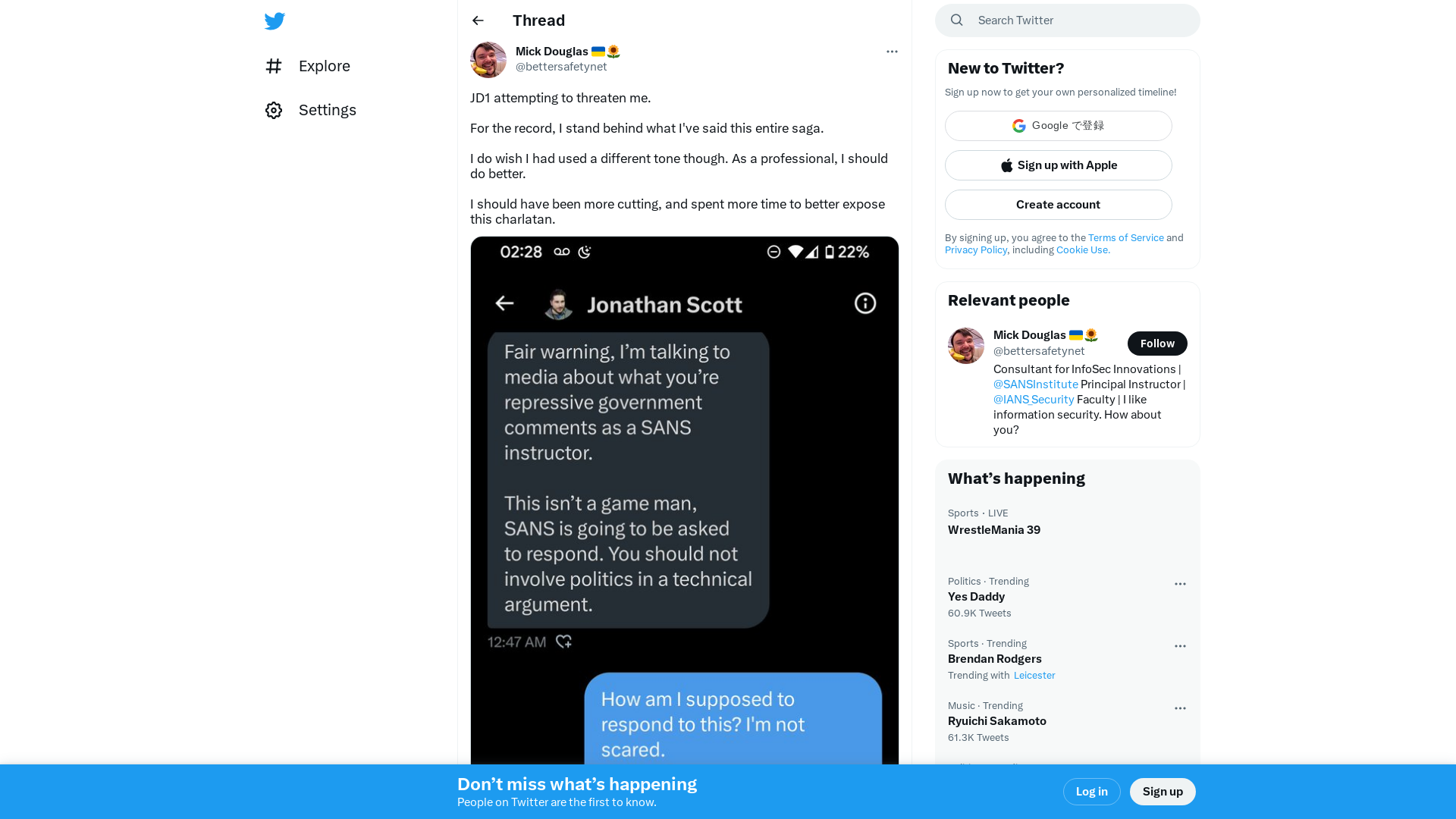
Cyber security news at your fingertips | Filter by topic or interest
http://cyberiqs.com/latestnews
Jerome Taylor on Twitter: "“We haven’t seen a mainstream app like this trying to escalate their privileges to gain access to things that they’re not supposed to gain access to,” said @Mikko Hyppönen, chief research officer at WithSecure, a Finnish cybersecurity firm." / Twitter
https://twitter.com/jerometaylor/status/1642569152635215873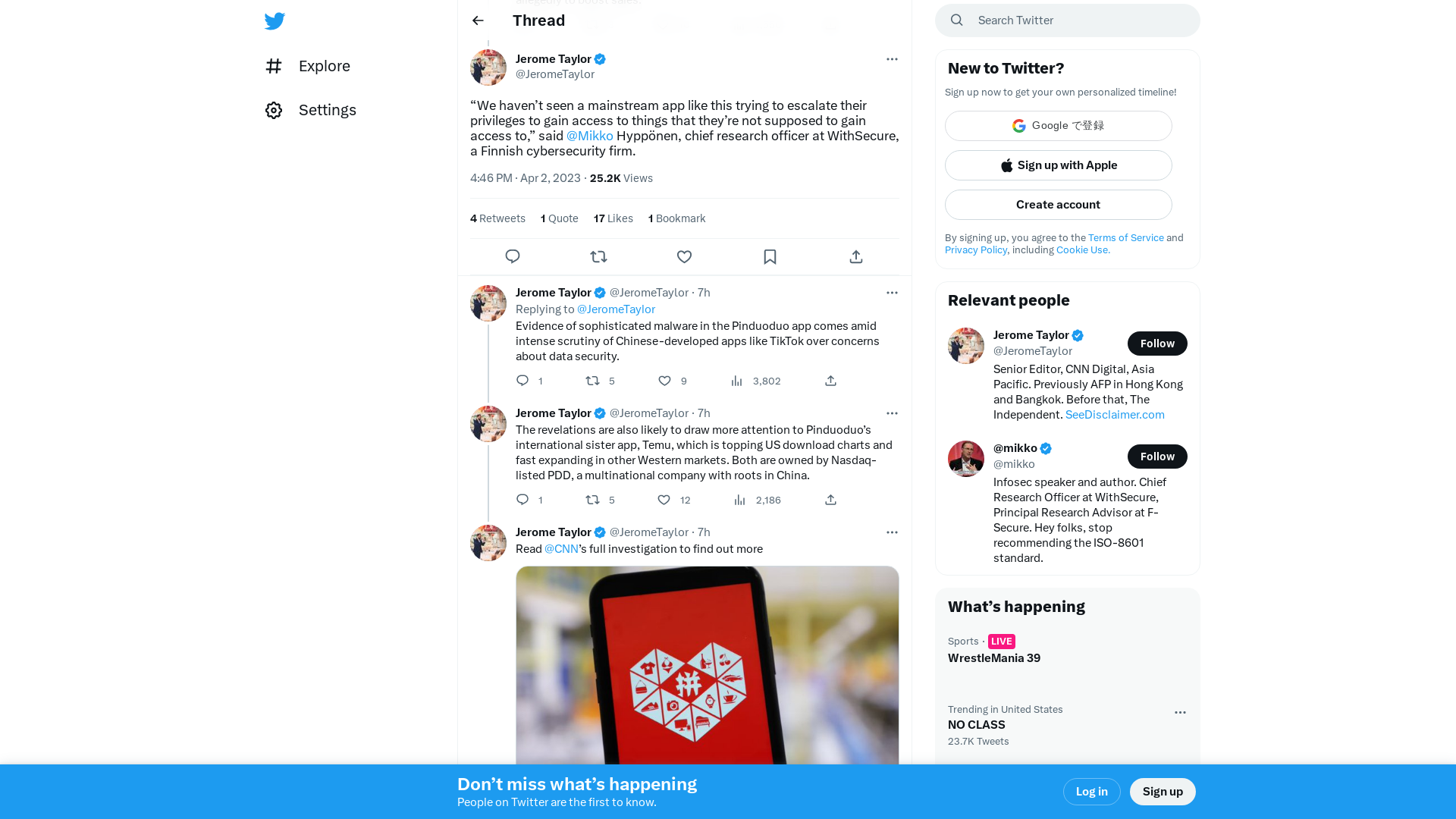
Flangvik - Twitch
https://www.twitch.tv/flangvik
Fake ransomware gang targets U.S. orgs with empty data leak threats
https://www-bleepingcomputer-com.cdn.ampproject.org/c/s/www.bleepingcomputer.com/news/security/fake-ransomware-gang-targets-us-orgs-with-empty-data-leak-threats/amp/
Report: Chinese state-sponsored hacking group highly active | AP News
https://apnews.com/article/china-hacking-report-redgolf-insikt-88a76977ce50d6d28d7a1be5130a1aa7
Analysis of Twitter algorithm code reveals social medium down-ranks tweets about Ukraine
https://news.yahoo.com/analysis-twitter-algorithm-code-reveals-072800540.html
3CX users under DLL-sideloading attack: What you need to know – Sophos News
https://news.sophos.com/en-us/2023/03/29/3cx-dll-sideloading-attack/
DJI Mavic 3 Drone Firmware Analysis
https://www.nozominetworks.com/blog/dji-mavic-3-drone-research-part-1-firmware-analysis/
Michael Koczwara on Twitter: "Hunting Havoc C2 infra 🎯 If you are interested to hunt C2s I recommend reading the GitHub source code because all info is usually there. Havoc generates a number of certificates you should look for: ACME, Partners, Tech, Cloud, Synergy, Test, Debug + prefixes… https://t.co/dbe6MQtCq4" / Twitter
https://twitter.com/i/web/status/1642218400691699851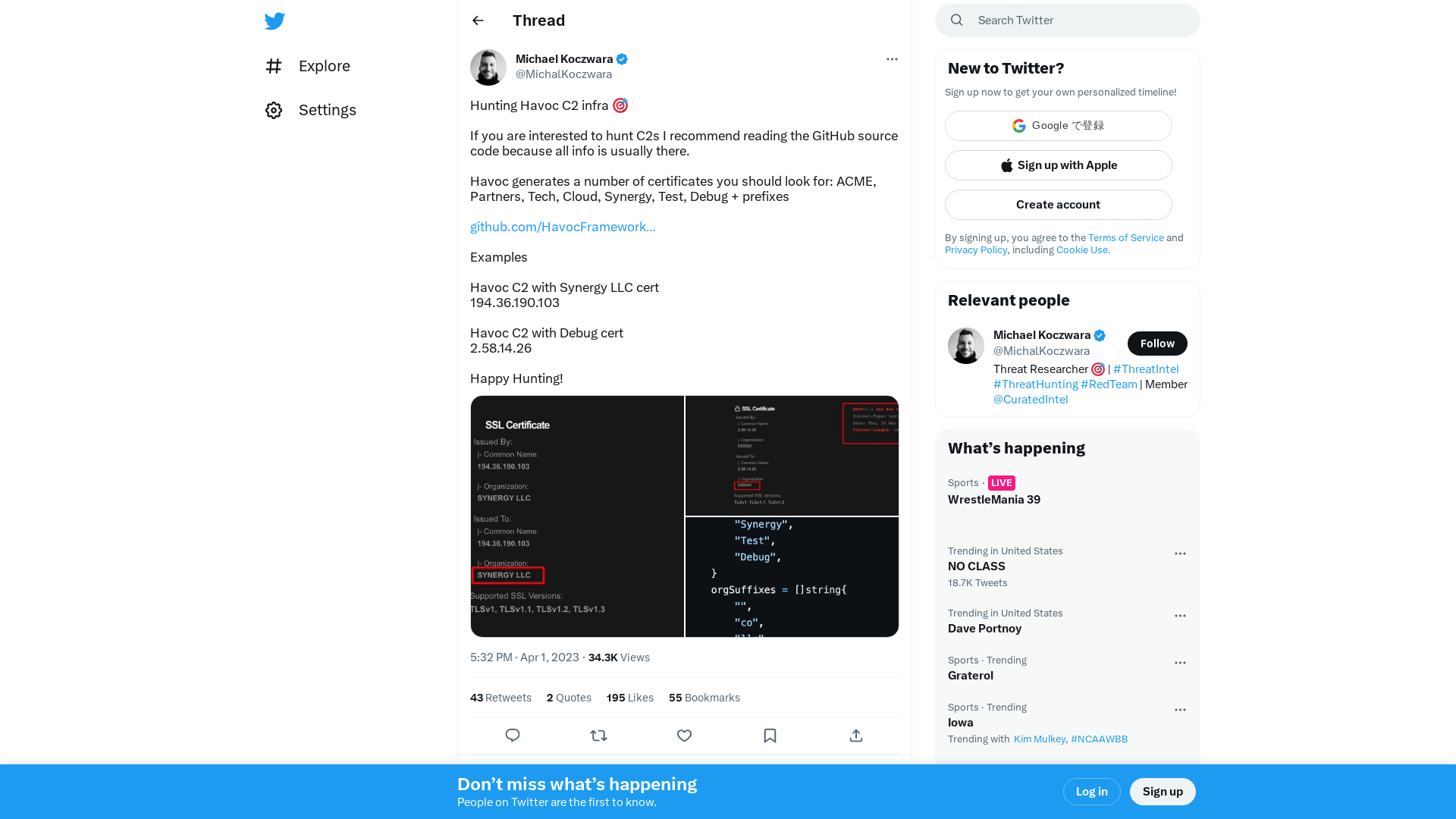
pr0xylife (pr0xylife) · GitHub
https://github.com/pr0xylife
Melvin langvik on Twitter: "Rust + Malware dev + ChatGPT, some solid clickbait content in the making! Going 🔴LIVE🔴 tomorrow 6PM UTC https://t.co/t5bf9IbVW8 Aprils fools day is the best day for announcements 😅😅 https://t.co/jhEnc8uKn3" / Twitter
https://twitter.com/Flangvik/status/1642221846098587648
Cybersecurity in Medical Devices: Refuse to Accept Policy for Cyber Devices and Related Systems Under Section 524B of the FD&C Act | FDA
https://www.fda.gov/regulatory-information/search-fda-guidance-documents/cybersecurity-medical-devices-refuse-accept-policy-cyber-devices-and-related-systems-under-section
MalwareBazaar | @pr0xylife
https://bazaar.abuse.ch/user/1413258196500815881/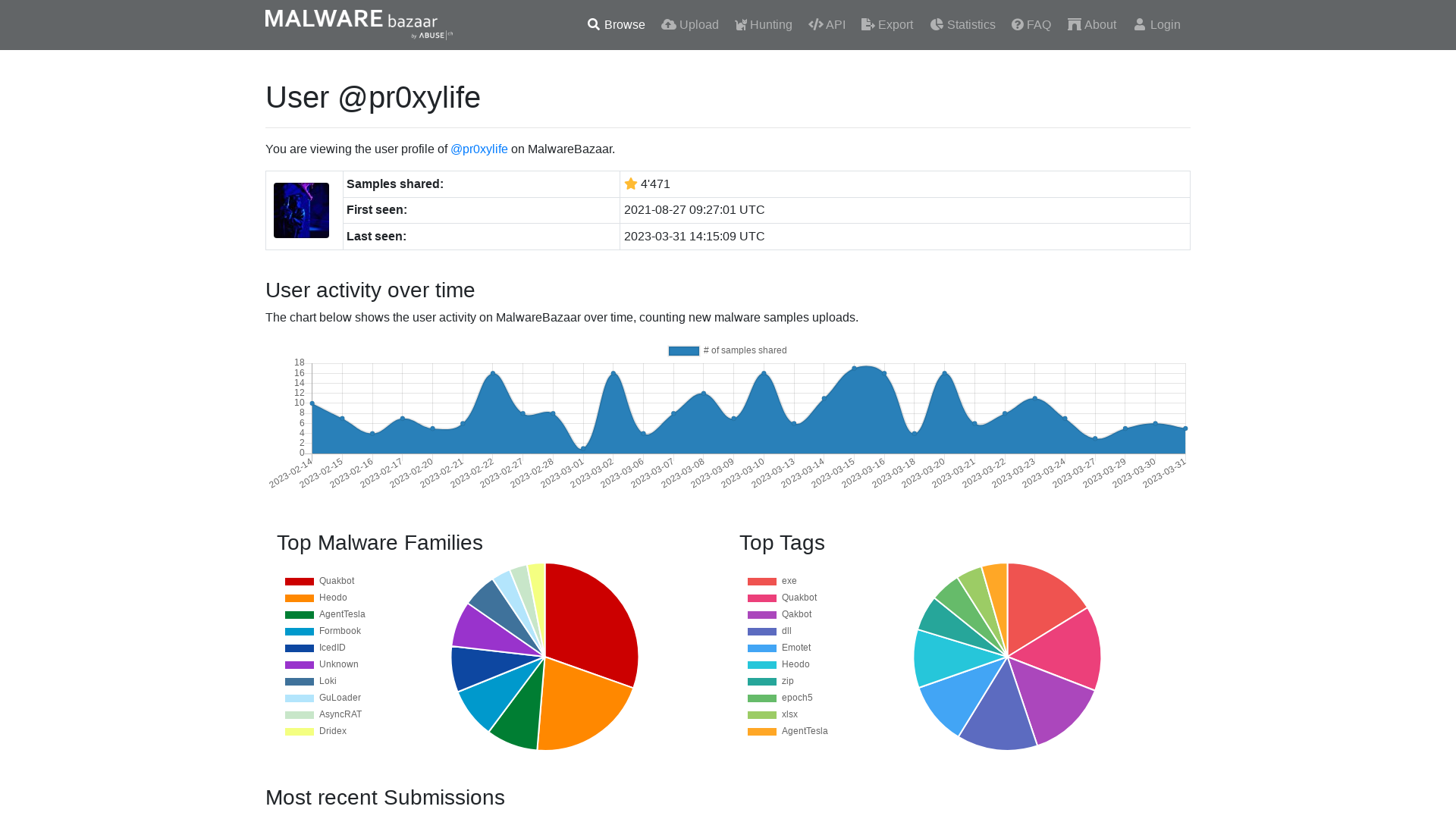
Mark Mazzetti on Twitter: "NEW: Days after the White House in 2021 blacklisted NSO, the notorious Israeli hacking firm, a secret contract was signed for a hacking tool. The contract states that the USG is the user. A thread https://t.co/i2PSUXq3NJ" / Twitter
https://twitter.com/markmazzettinyt/status/1642637136212946947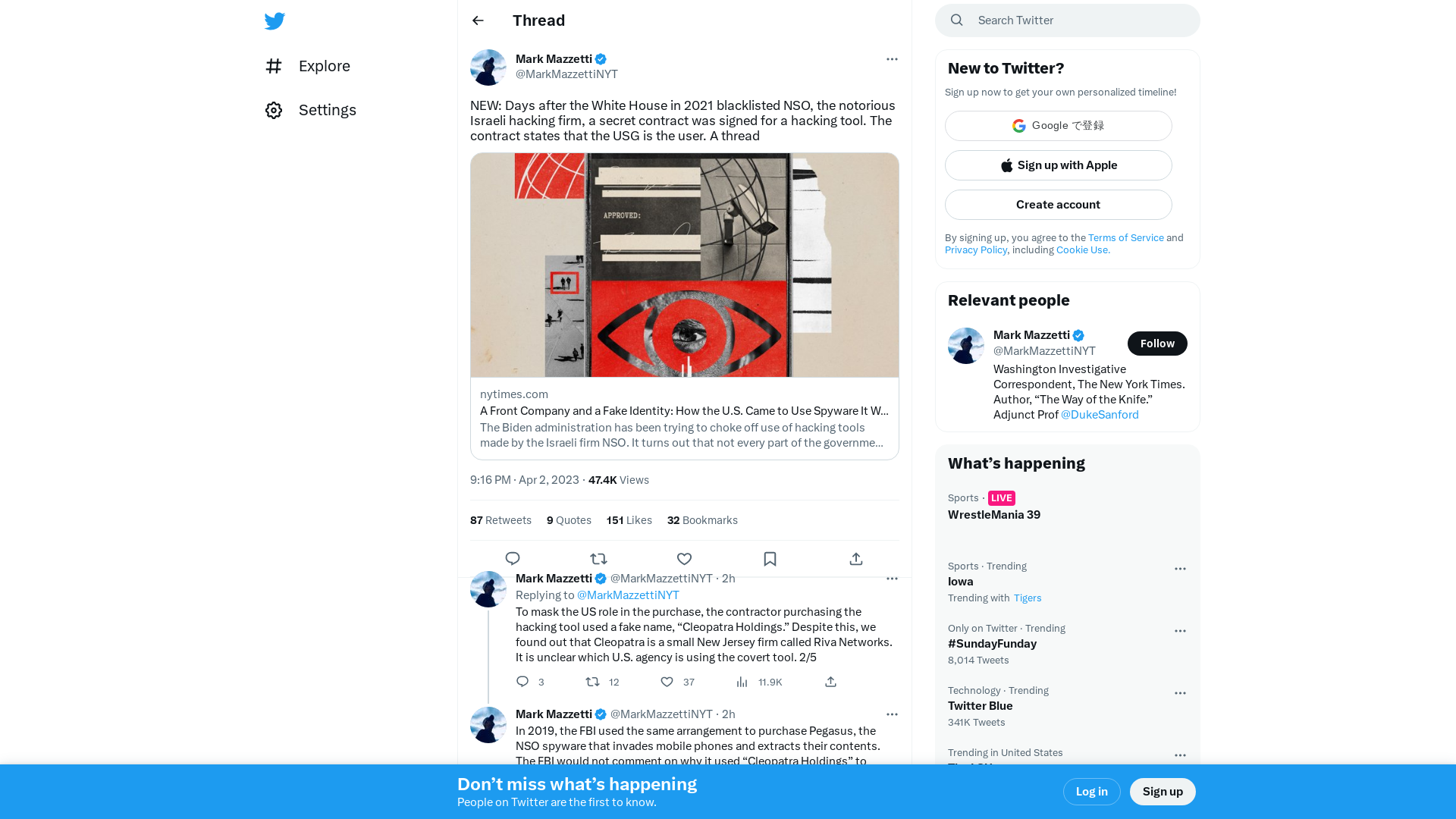
1746245 - (webgpu-in-nightly) Enable WebGPU in Nightly by default
https://bugzilla.mozilla.org/show_bug.cgi?id=1746245
New Money Message ransomware demands million dollar ransoms
https://www.bleepingcomputer.com/news/security/new-money-message-ransomware-demands-million-dollar-ransoms/