Check My Operator
https://checkmyoperator.com/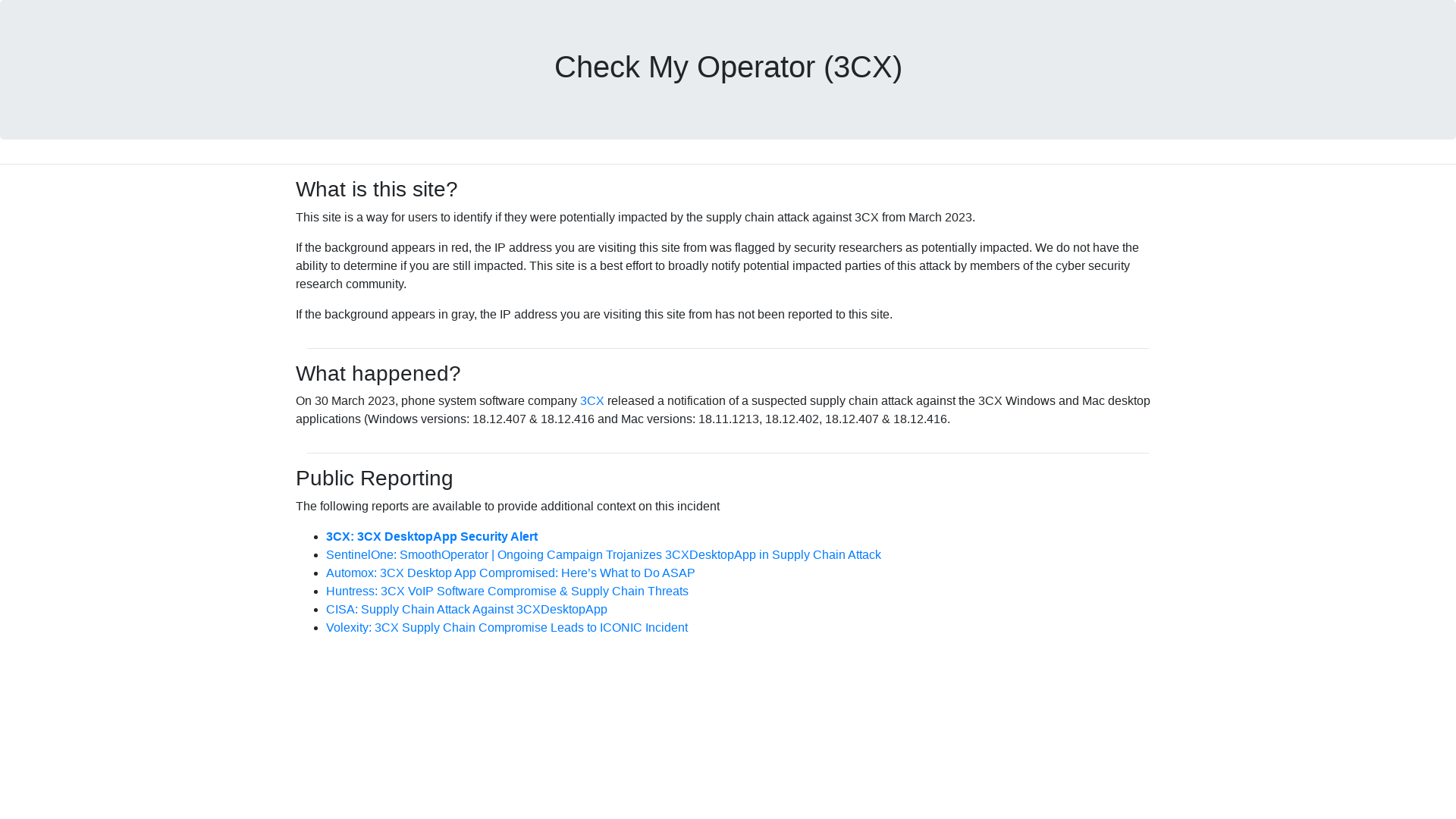
ACE Responder on Twitter: "Do you know what DCOM lateral movement looks like? It can be much more difficult to recognize than WMI/PSExec. The MMC20.Application procedure is more reliable than the others. Look for mmc.exe spawning strange child procs. #ThreatHunting #DFIR https://t.co/HIegxXiNBJ" / Twitter
https://twitter.com/i/web/status/1641957092998168576
GitHub - hisxo/ReconAIzer: An Burp Suite extension to add OpenAI to Burp to help you in your Bug Bounty recon!
https://github.com/hisxo/ReconAIzer
Never gonna give you up entire video (No ads) - YouTube
https://bit.ly/RetroHound
Authentication Methods Available in Azure Active Directory | DSInternals
https://www.dsinternals.com/en/aad-azure-ad-mfa-authentication-methods/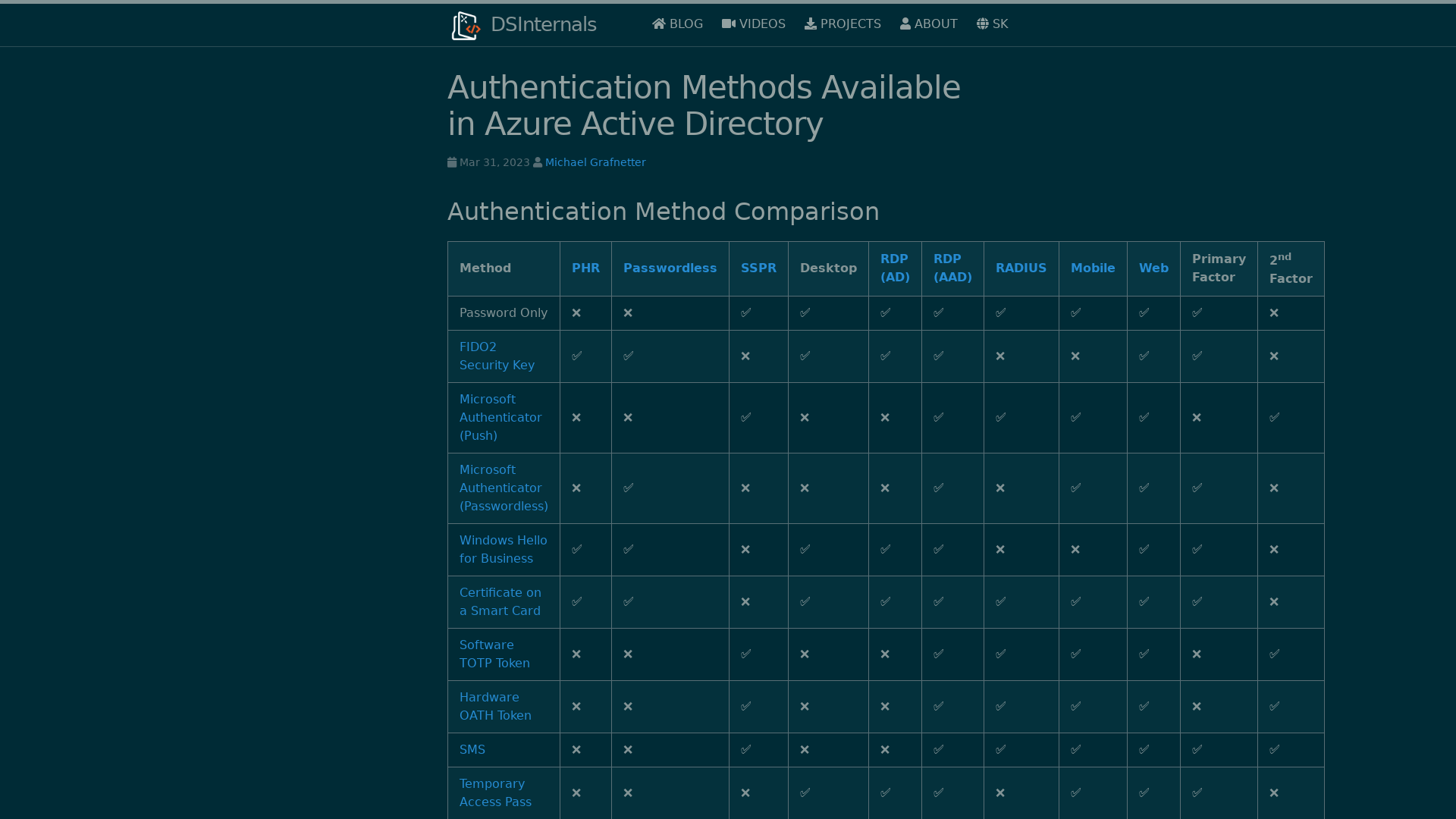
Microsoft Fixes New Azure AD Vulnerability Impacting Bing Search and Major Apps
https://thehackernews.com/2023/04/microsoft-fixes-new-azure-ad.html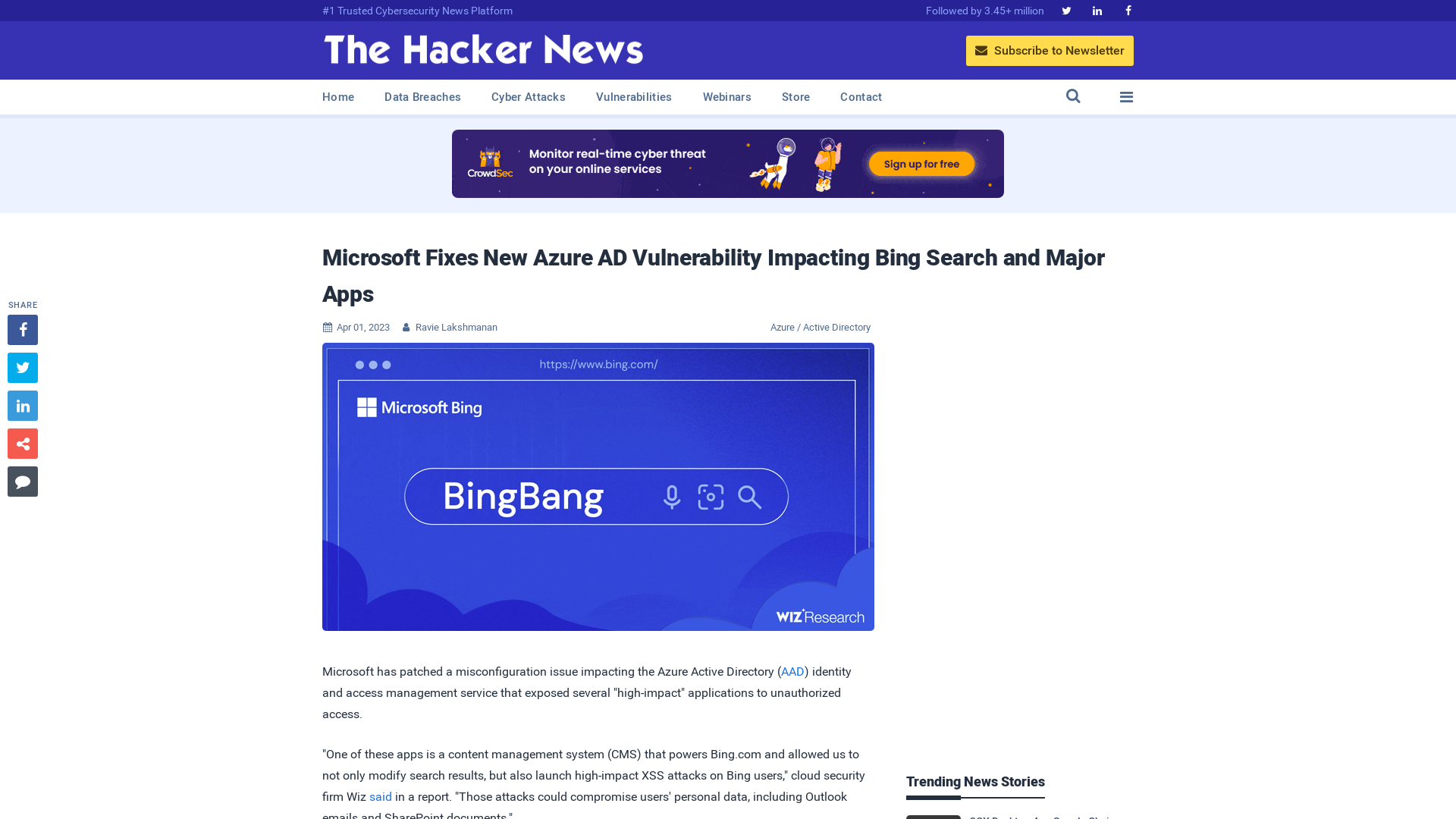
Adrien on Twitter: "🤯 OpenAI + Burp Suite = welcome to "ReconAIzer" A powerful extension for Burp Suite that leverages OpenAI to help bug bounty hunters optimize their recon process. 🔗Link: https://t.co/s76e4DpwId (It's not a serious project, it's just for fun 😂) https://t.co/jN4BcRxBMD" / Twitter
https://twitter.com/i/web/status/1641921422745321473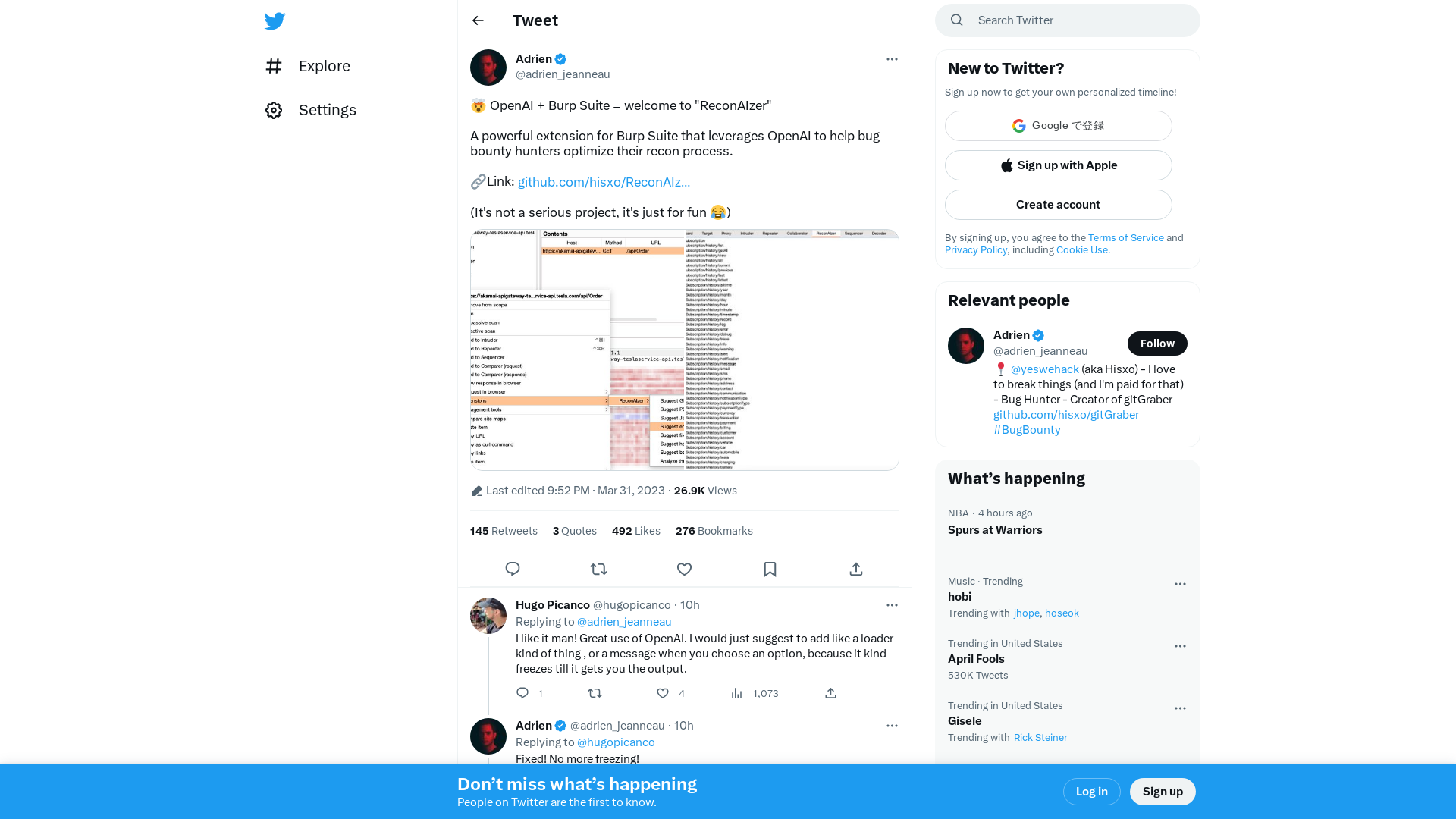
Andy Robbins on Twitter: "To understand our future, we must study our past. I am proud to announce the release of #RetroHound! ✅ Runs on Windows 3.1 ✅ Backed by an MS Access database ✅ Full NetBEUI & LANMAN support See it in action here: https://t.co/gwMaOqwnIF https://t.co/4yrtlPc7sb" / Twitter
https://twitter.com/_wald0/status/1642172467497308163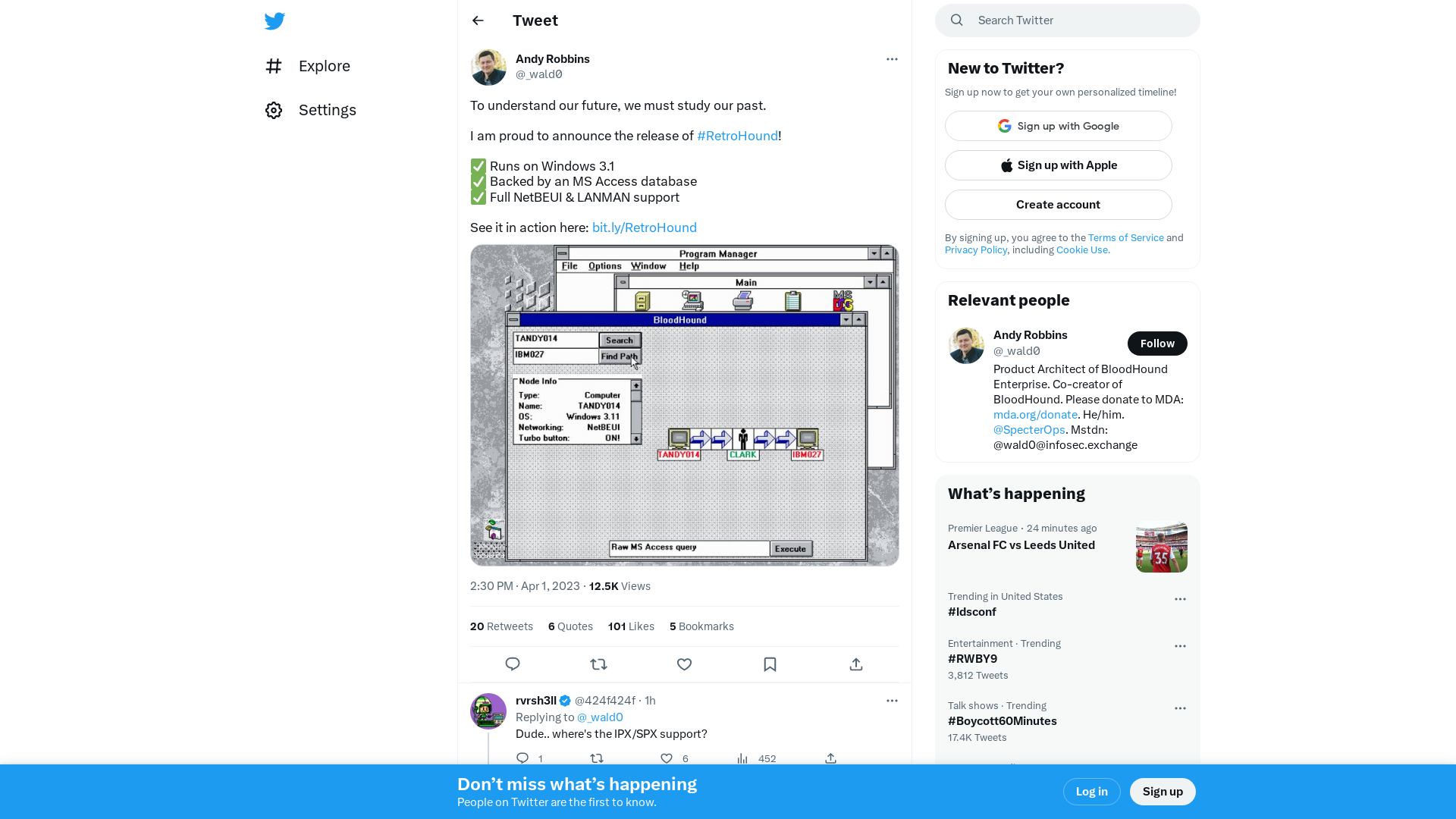
Rufus T. Firefly (sworn enemy of Rakell) on Twitter: "Holy fuck 😂😂😂😂 https://t.co/SI5tBCn2kl" / Twitter
https://twitter.com/hoggomcswineass/status/1641941228001304578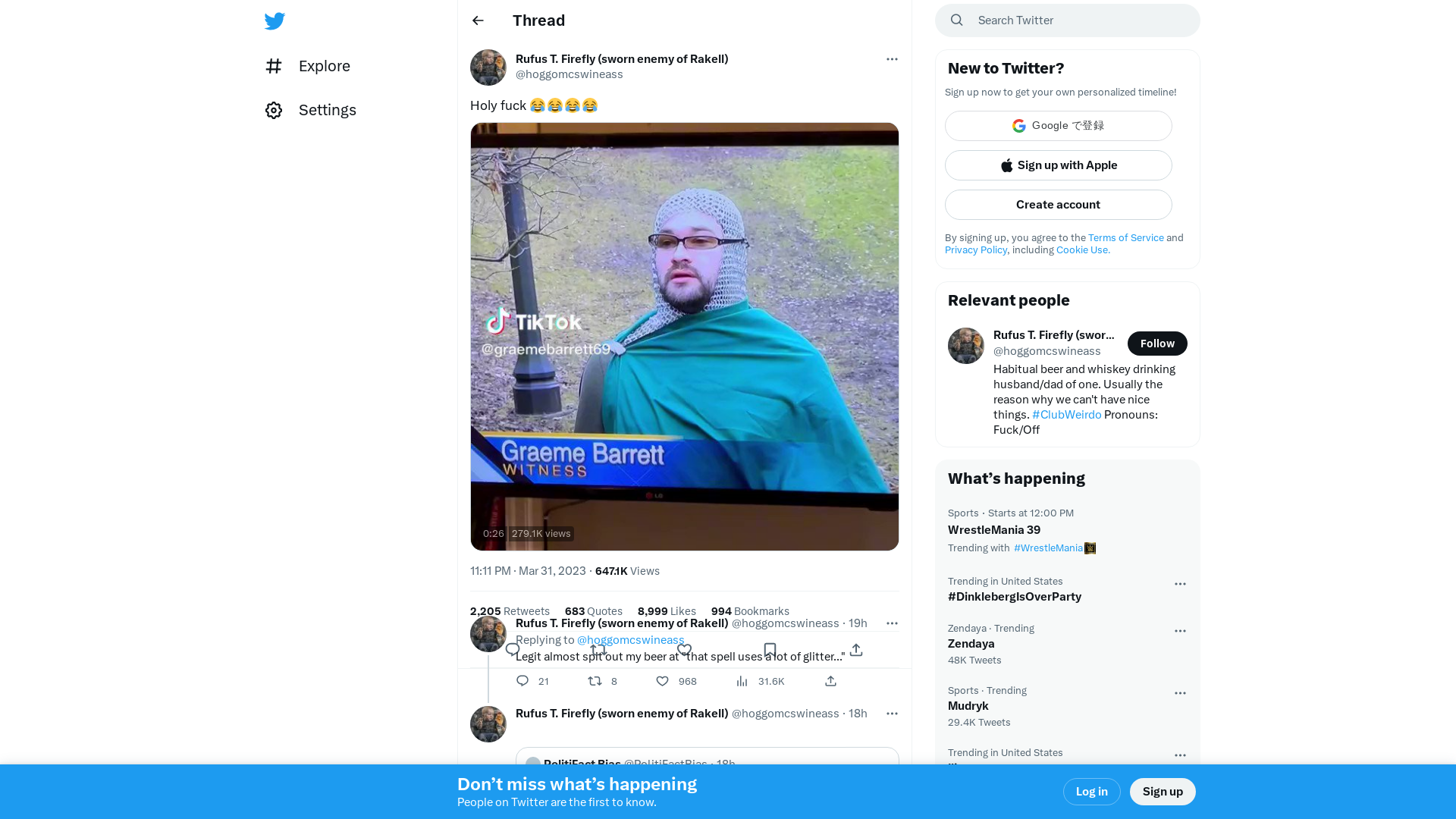
Cacti, Realtek, and IBM Aspera Faspex Vulnerabilities Under Active Exploitation
https://thehackernews.com/2023/04/cacti-realtek-and-ibm-aspera-faspex.html