Reversing UK mobile rail tickets
https://eta.st/2023/01/31/rail-tickets.html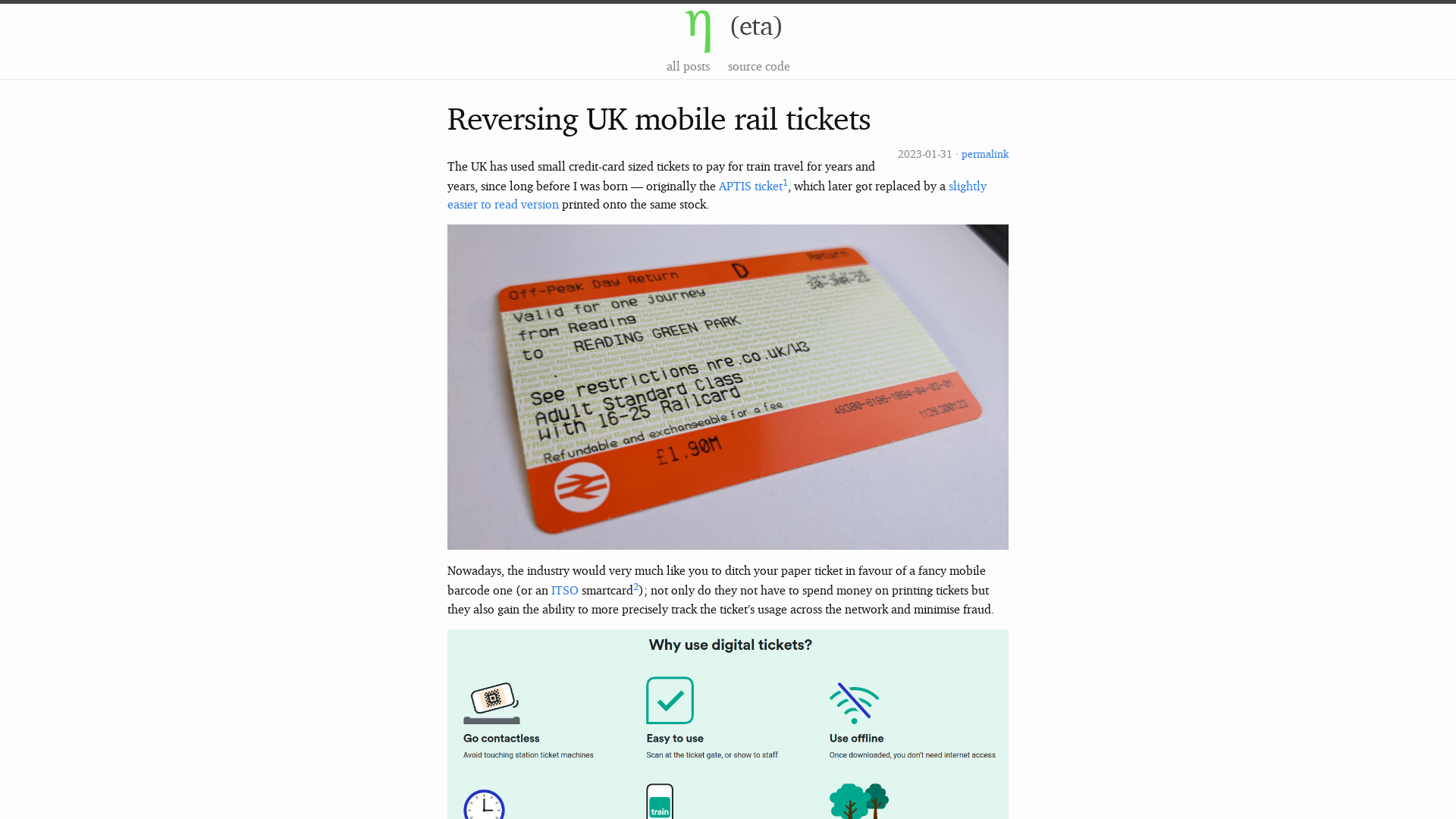
My RCE PoC walkthrough for (CVE-2021–21974) VMware ESXi OpenSLP heap-overflow vulnerability | by Johnny Yu (@straight_blast) | Medium
https://straightblast.medium.com/my-poc-walkthrough-for-cve-2021-21974-a266bcad14b9
GitHub - CMEPW/BypassAV: This map lists the essential techniques to bypass anti-virus and EDR
https://github.com/CMEPW/BypassAV
Massive ESXiArgs ransomware attack targets VMware ESXi servers worldwide
https://www.bleepingcomputer.com/news/security/massive-esxiargs-ransomware-attack-targets-vmware-esxi-servers-worldwide/
Linux version of Royal Ransomware targets VMware ESXi servers
https://www.bleepingcomputer.com/news/security/linux-version-of-royal-ransomware-targets-vmware-esxi-servers/
OALabsLive - Twitch
https://www.twitch.tv/oalabslive
Solving a VM-based CTF challenge without solving it properly - gynvael.coldwind//vx.log
https://gynvael.coldwind.pl/?lang=en&id=763
Mindmap/Crackmapexec at main · Ignitetechnologies/Mindmap · GitHub
https://github.com/Ignitetechnologies/Mindmap/tree/main/Crackmapexec
Software Security Austerity - Software security debt in modern software development eBook : Whitehouse, Ollie, Vaughan, James: Amazon.co.uk: Kindle Store
https://www.amazon.co.uk/Software-Security-Austerity-security-development-ebook/dp/B007H76ABC?ref=d6k_applink_bb_dls&dplnkId=79a6ea31-128c-410c-b271-1b0c051016d5
GitHub - cyberark/PipeViewer: A tool that shows detailed information about named pipes in Windows
https://github.com/cyberark/PipeViewer
NY attorney general forces spyware vendor to alert victims
https://www.bleepingcomputer.com/news/security/ny-attorney-general-forces-spyware-vendor-to-alert-victims/
Analysing A Sample Of Arechclient2 | dr4k0nia
https://dr4k0nia.github.io/posts/Analysing-a-sample-of-ArechClient2/
Building a Custom Mach-O Memory Loader for macOS - Part 1 - XPN InfoSec Blog
https://blog.xpnsec.com/building-a-mach-o-memory-loader-part-1/
cts on Twitter: "CTF Challenges by Category * crypto: guess the paper * web: guess the blog post * pwn: 猜blog post但是中文版 * rev: seek therapy." / Twitter
https://twitter.com/i/web/status/1622275916121645056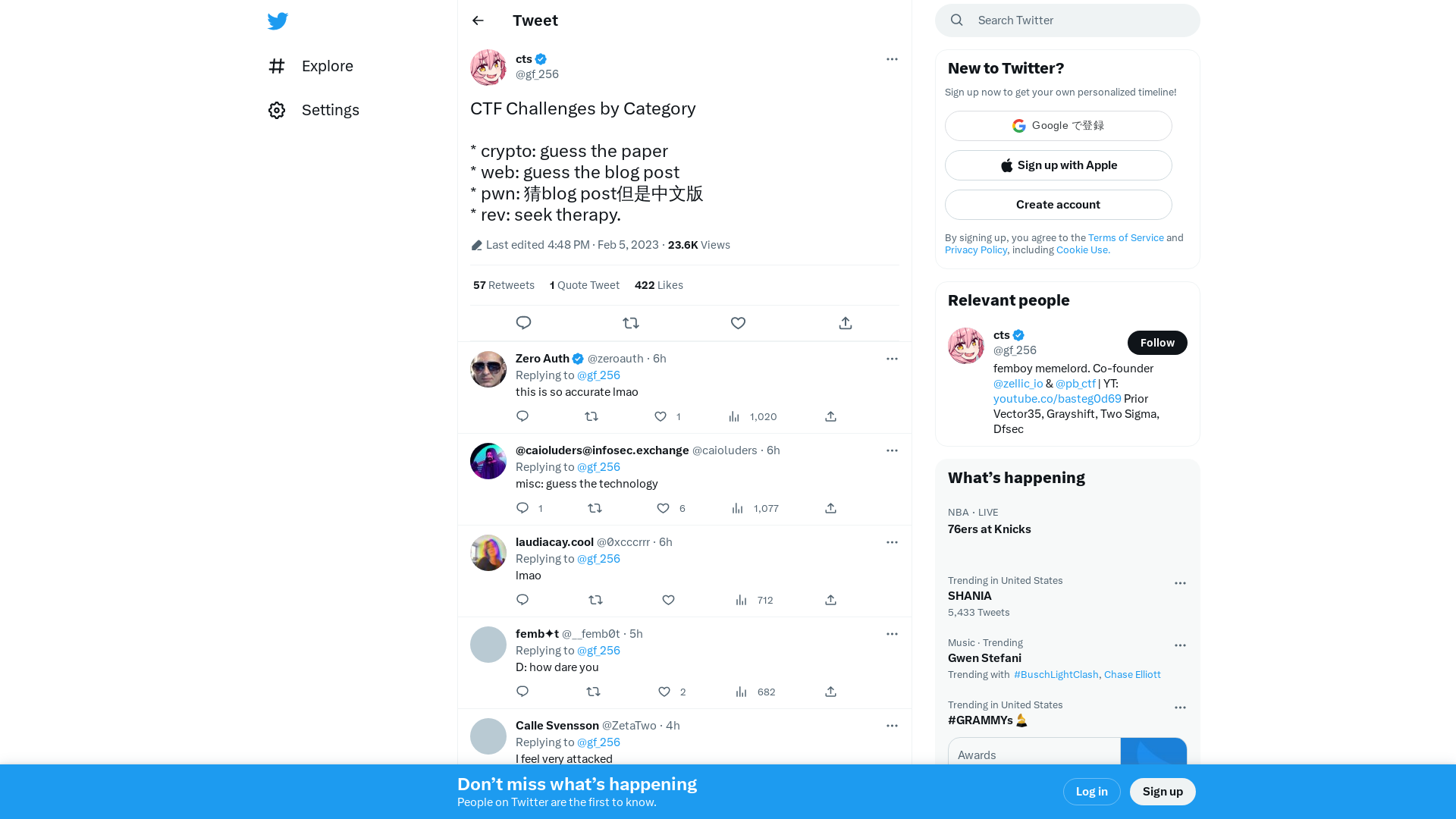
Antisyphon Summit 2023 - Antisyphon
https://www.antisyphontraining.com/2023-most-offensive-summit/
Joo N/A: "ffuf v2.0 is out! There's a lo…" - Infosec Exchange
https://infosec.exchange/@joohoi/109806822104162973
New Wave of Ransomware Attacks Exploiting VMware Bug to Target ESXi Servers
https://thehackernews.com/2023/02/new-wave-of-ransomware-attacks.html
KQL-queries/onenote-spwning-mshta at main · cyb3rmik3/KQL-queries · GitHub
https://github.com/cyb3rmik3/KQL-queries/blob/main/onenote-spwning-mshta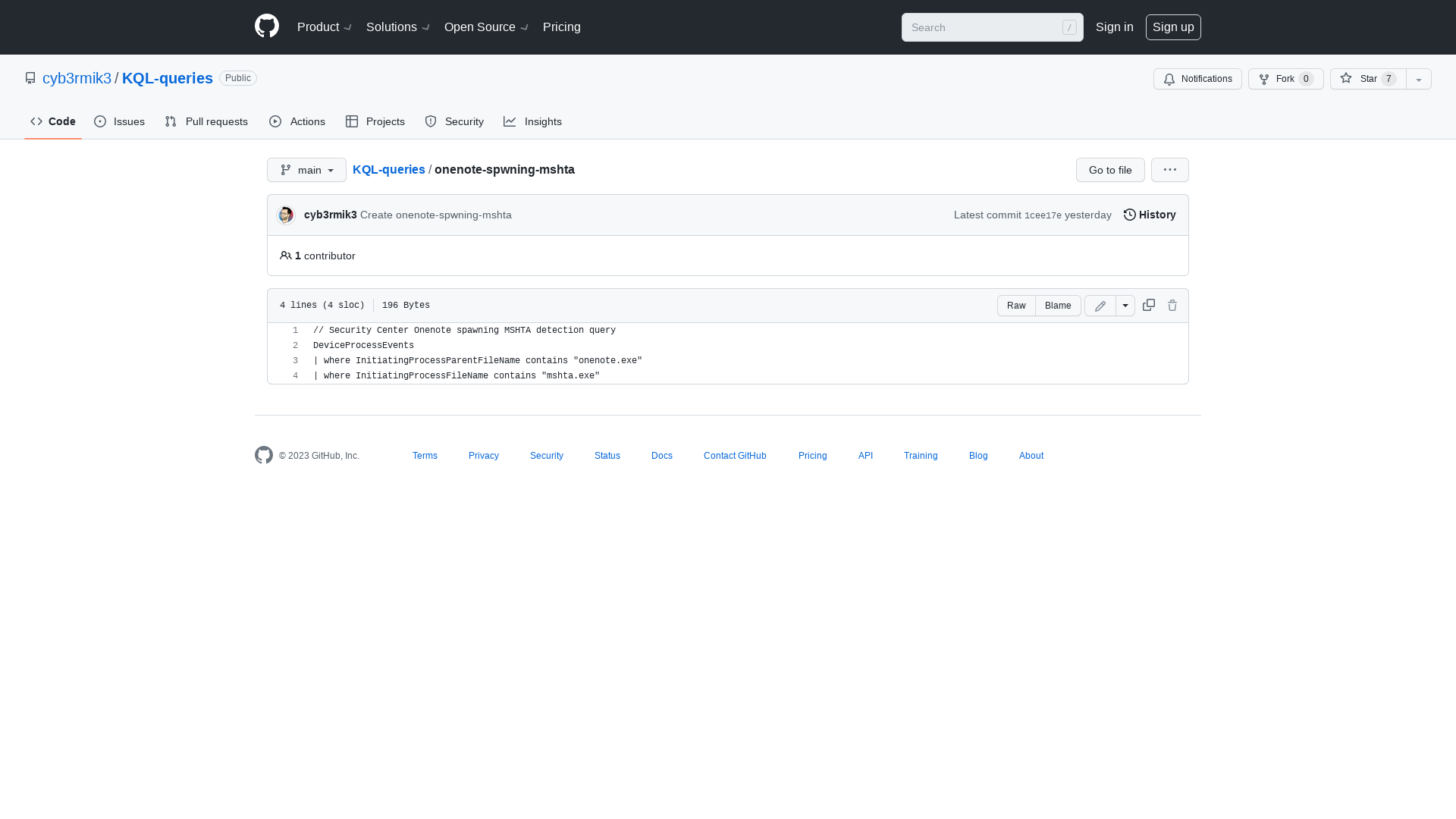
GitHub - Acebond/ReverseSocks5: Single executable reverse socks5 proxy written in Golang.
https://github.com/Acebond/ReverseSocks5
Florida hospital takes IT systems offline after cyberattack
https://www.bleepingcomputer.com/news/security/florida-hospital-takes-it-systems-offline-after-cyberattack/
Kremlin-Linked Group Arranged Payments to European Politicians to Support Russia’s Annexation of Crimea - OCCRP
https://www.occrp.org/en/investigations/kremlin-linked-group-arranged-payments-to-european-politicians-to-support-russias-annexation-of-crimea
New Mimic Ransomware Abuses Everything APIs for its Encryption Process
https://research.trendmicro.com/3kE6LdL
Mykhailo on Twitter: "I received bizarre microchips from the downed Russian SU-24M near Bakhmut. Research revealed that at least one microchip is part of the SVP-24 automatic targeting system. As you can guess, it is full of Western parts 🧵 https://t.co/mZ8cSuWk3C" / Twitter
https://twitter.com/mxpoliakov/status/1606650142379196416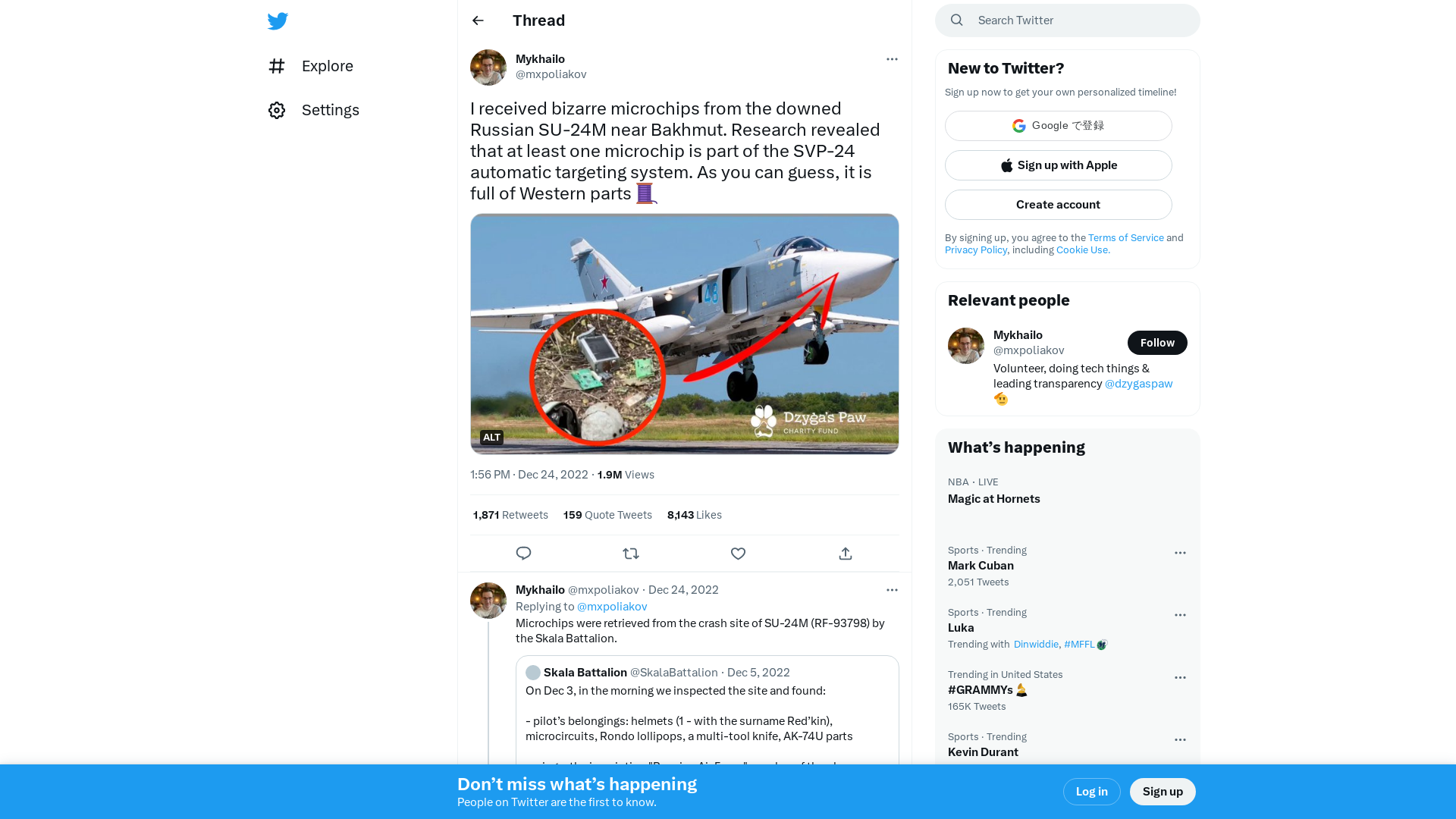
Week 6 – 2023 – This Week In 4n6
http://thisweekin4n6.com/2023/02/05/week-6-2023/
Triage | Behavioral Report
https://tria.ge/230205-ex6n8abe2v/behavioral2
GitHub - reveng007/AMSI-patches-learned-till-now: I have documented all of the AMSI patches that I learned till now
https://github.com/reveng007/AMSI-patches-learned-till-now
Incident Response in Google Cloud: Forensic Artifacts
https://blog.sygnia.co/incident-response-in-google-cloud-forensic-artifacts
SensePost | Linux heap exploitation intro series: riding free on the heap – double free attacks!
https://sensepost.com/blog/2017/linux-heap-exploitation-intro-series-riding-free-on-the-heap-double-free-attacks/
Named Pipe Pass-the-Hash | S3cur3Th1sSh1t
https://s3cur3th1ssh1t.github.io/Named-Pipe-PTH/
Linux Privilege Escalation: DirtyPipe (CVE 2022-0847) - Codelivly
https://www.codelivly.com/linux-privilege-escalation-dirtypipe/
Instant Checkmate, TruthFinder Data Breach: 20M Accounts Leaked
https://www.hackread.com/instant-checkmate-truthfinder-data-breach/
GitHub - voidz0r/CVE-2022-44268: A PoC for the CVE-2022-44268 - ImageMagick arbitrary file read
https://github.com/voidz0r/CVE-2022-44268
InfoSec Handlers Diary Blog - SANS Internet Storm Center
https://i5c.us/d29512
Twitter Dev on Twitter: "Starting February 9, we will no longer support free access to the Twitter API, both v2 and v1.1. A paid basic tier will be available instead 🧵" / Twitter
https://twitter.com/TwitterDev/status/1621026986784337922