Building a Custom Mach-O Memory Loader for macOS - Part 1 - XPN InfoSec Blog
https://blog.xpnsec.com/building-a-mach-o-memory-loader-part-1/
Shodan Search Engine
https://beta.shodan.io/search?query=html%3A%22We+hacked+your+company+successfully%22+title%3A%22How+to+Restore+Your+Files%22
Malware-Traffic-Analysis.net - 2023-02-03 - DEV-0569 activity: Google ad --> FakeBat Loader --> Redline Stealer & Gozi/ISFB/Ursnif
https://www.malware-traffic-analysis.net/2023/02/03/index.html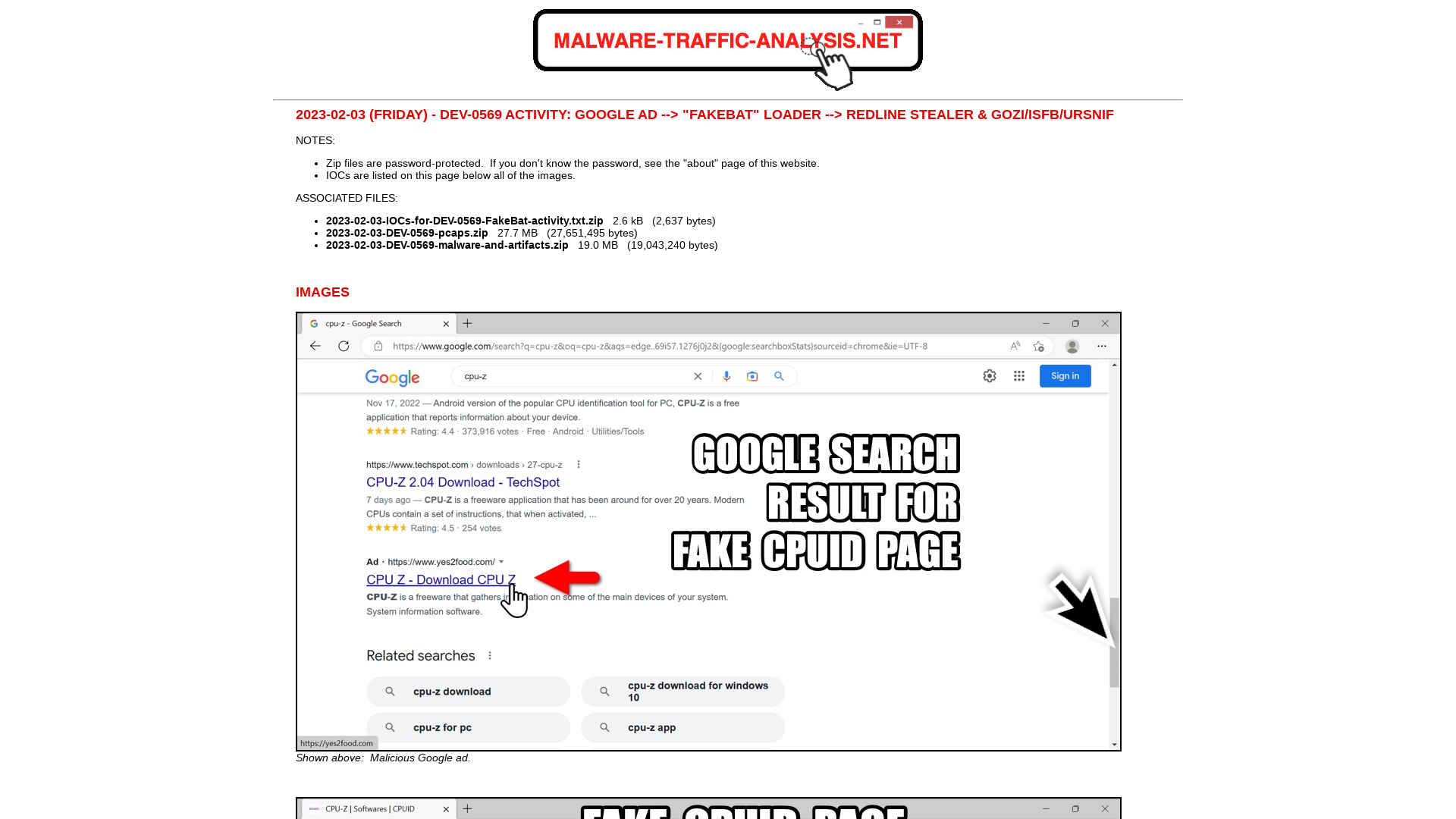
Arnaud de Bermingham on Twitter: "🚨A tous : Si vous utilisez ESXi 6.x, mettez à jour IMMÉDIATEMENT, un cryptolock est en train de se propager à toute vitesse ! If you're using ESXi 6.x, update IMMEDIATELY, a cryptolock is rolling out fast!" / Twitter
https://twitter.com/a_bermingham/status/1621503163584118790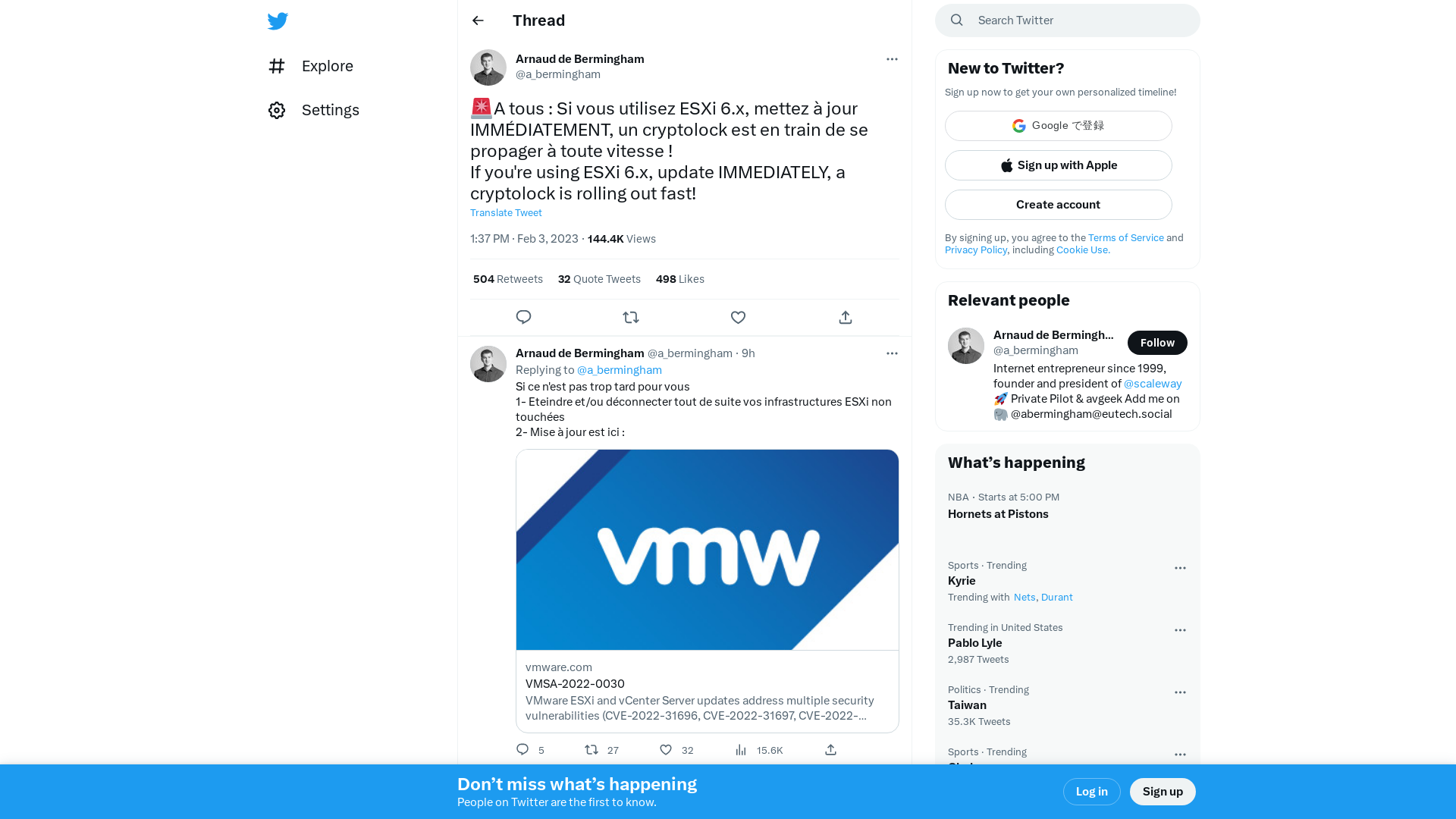
Joo N/A: "ffuf v2.0 is out! There's a lo…" - Infosec Exchange
https://infosec.exchange/@joohoi/109806822104162973
New Wave of Ransomware Attacks Exploiting VMware Bug to Target ESXi Servers
https://thehackernews.com/2023/02/new-wave-of-ransomware-attacks.html
Massive ESXiArgs ransomware attack targets VMware ESXi servers worldwide
https://www.bleepingcomputer.com/news/security/massive-esxiargs-ransomware-attack-targets-vmware-esxi-servers-worldwide/
Warning: Hackers Actively Exploiting Zero-Day in Fortra's GoAnywhere MFT
https://thehackernews.com/2023/02/warning-hackers-actively-exploiting.html
Exploitation of GoAnywhere MFT zero-day vulnerability | Rapid7 Blog
https://www.rapid7.com/blog/post/2023/02/03/exploitation-of-goanywhere-mft-zero-day-vulnerability/
Onenote Malware: Classification and Personal Notes
https://marcoramilli.com/2023/02/04/onenote-malware-classification-and-personal-notes/
DocumentsFolder_209852_Feb_03.one (MD5: B5C046E6227C76F5AB828B5057F6D4D2) - Interactive analysis - ANY.RUN
https://app.any.run/tasks/1ffa650a-1719-4d03-898b-951e7b1b8103