Introduction to the Windows Filtering Platform – Pavel Yosifovich
http://scorpiosoftware.net/2022/12/25/introduction-to-the-windows-filtering-platform/
GitHub - kkent030315/CVE-2022-42046: CVE-2022-42046 Proof of Concept of wfshbr64.sys local privilege escalation via DKOM
https://github.com/kkent030315/CVE-2022-42046
Pwn the ESP32 Forever: Flash Encryption and Sec. Boot Keys Extraction - LimitedResults
https://limitedresults.com/2019/11/pwn-the-esp32-forever-flash-encryption-and-sec-boot-keys-extraction/
Linux kernel exploit development - Breaking Bits
https://breaking-bits.gitbook.io/breaking-bits/exploit-development/linux-kernel-exploit-development
GitHub - securityjoes/ThreatResearch
https://github.com/securityjoes/ThreatResearch/
New info-stealer malware infects software pirates via fake cracks sites
https://www.bleepingcomputer.com/news/security/new-info-stealer-malware-infects-software-pirates-via-fake-cracks-sites/
GitHub - BeetleChunks/SpoolSploit: A collection of Windows print spooler exploits containerized with other utilities for practical exploitation.
https://github.com/BeetleChunks/SpoolSploit
W4SP Stealer Discovered in Multiple PyPI Packages Under Various Names
https://thehackernews.com/2022/12/w4sp-stealer-discovered-in-multiple.html
Expert found Backdoor credentials in ZyXEL LTE3301 M209Security Affairs
https://securityaffairs.co/wordpress/139974/hacking/backdoor-credentials-zyxel-lte3301-m209.html
GitHub - lab52io/StopDefender: Stop Windows Defender programmatically
https://github.com/lab52io/StopDefender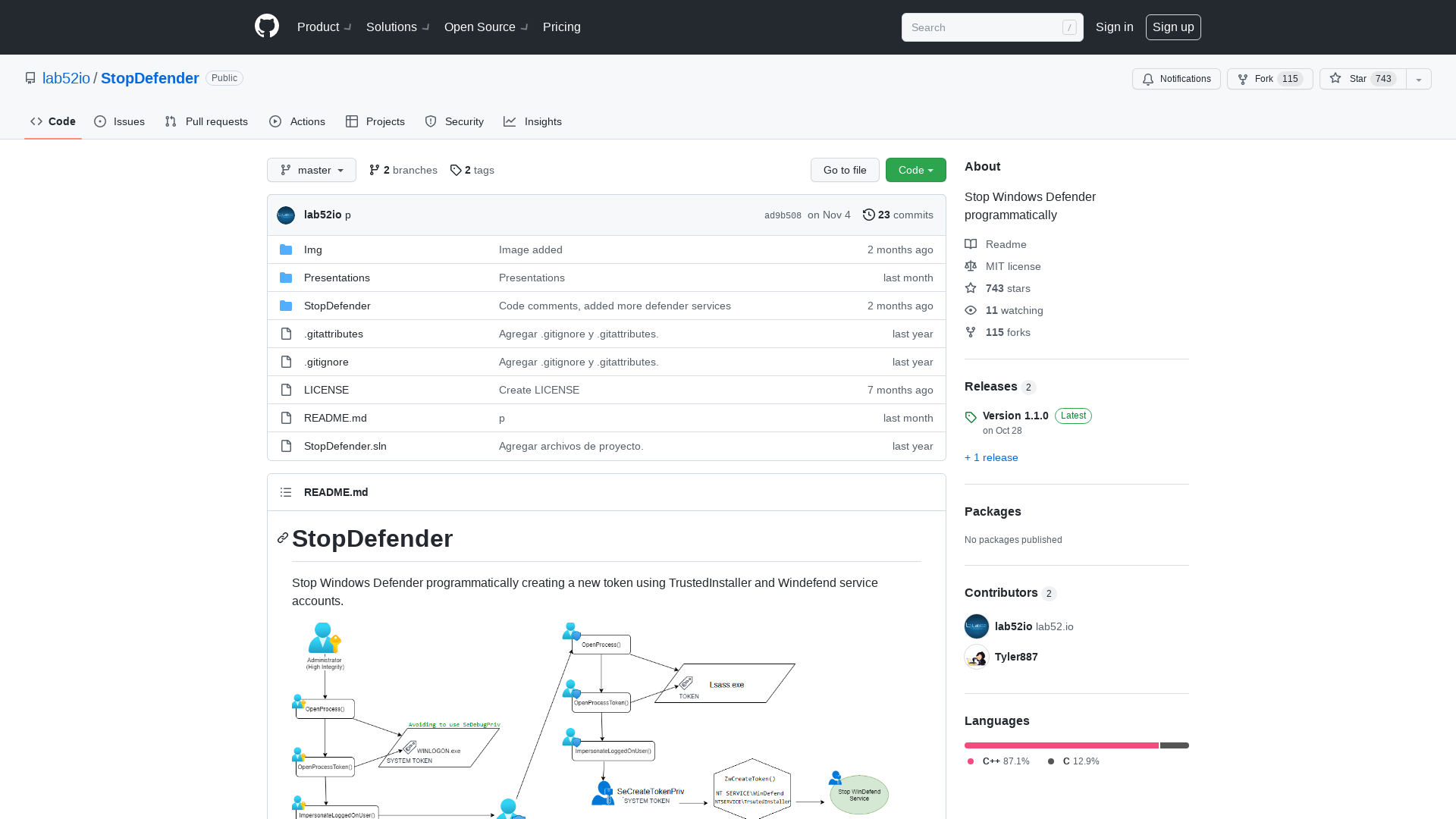
Twitter Files Thread: The Spies Who Loved Twitter
https://open.substack.com/pub/taibbi/p/twitter-files-thread-the-spies-who?r=5mz1&utm_campaign=post&utm_medium=web
ipa-medit: Memory search and patch tool for IPA without Jailbreaking/ipa-medit-bh2022-europe - Speaker Deck
https://speakerdeck.com/tkmru/ipa-medit-bh2022-europe
hexacon2022_AppleAVD/hexacon2022_AppleAVD.pdf at main · isciurus/hexacon2022_AppleAVD · GitHub
https://github.com/isciurus/hexacon2022_AppleAVD/blob/main/hexacon2022_AppleAVD.pdf
Powershell Without Powershell - How To Bypass Application Whitelisting, Environment Restrictions & AV - Black Hills Information Security
https://www.blackhillsinfosec.com/powershell-without-powershell-how-to-bypass-application-whitelisting-environment-restrictions-av/
Faithless - Insomnia (Official 4K Video) - YouTube
https://youtu.be/P8JEm4d6Wu4
@0xLupin Challenge 🎄
https://www.hacklupin.com/
Pwn the ESP32 Secure Boot - LimitedResults
https://limitedresults.com/2019/09/pwn-the-esp32-secure-boot/
Pwn the ESP32 crypto-core - LimitedResults
https://limitedresults.com/2019/08/pwn-the-esp32-crypto-core/
Top 11 exploited vulnerabilities for initial access and compromise in ‘22 | by Winter_Soldiers | Dec, 2022 | Medium
https://link.medium.com/ABT2zY8L2vb
Texas Cyber Summit 2022: Windows built-in Sandbox Disables Microsoft Defender and other EDR/AV - YouTube
https://youtu.be/NGrSPuC7xr0
The CyberWire: The 12 Days of Malware.
https://bit.ly/cw12days
Week 52 – 2022 – This Week In 4n6
http://thisweekin4n6.com/2022/12/25/week-52-2022/
GitHub - jart/blink: tiniest x86-64-linux emulator
https://github.com/jart/blink
GitHub - mytechnotalent/Reverse-Engineering: A FREE comprehensive reverse engineering tutorial covering x86, x64, 32-bit ARM & 64-bit ARM architectures.
https://github.com/mytechnotalent/Reverse-Engineering
Forensic artifacts in Office 365 and where to find them - Microsoft Tech Community
https://techcommunity.microsoft.com/t5/security-compliance-and-identity/forensic-artifacts-in-office-365-and-where-to-find-them/ba-p/3634865
