New details on commercial spyware vendor Variston
https://blog.google/threat-analysis-group/new-details-on-commercial-spyware-vendor-variston/
GitHub - reecdeep/HiveV5_file_decryptor: Hive v5 file decryption algorithm
https://github.com/reecdeep/HiveV5_file_decryptor
I Am Whoever I Say I Am: Infiltrating Identity Providers Using a 0Click Exploit - YouTube
http://youtu.be/2y3jgJSgnEo
Outsider Security - Trainings
https://outsidersecurity.nl/trainings/
Sam Curry on Twitter: "More car hacking! Earlier this year, we were able to remotely unlock, start, locate, flash, and honk any remotely connected Honda, Nissan, Infiniti, and Acura vehicles, completely unauthorized, knowing only the VIN number of the car. Here's how we found it, and how it works: https://t.co/ul3A4sT47k" / Twitter
https://twitter.com/samwcyo/status/1597792097175674880
Crafty threat actor uses 'aged' domains to evade security platforms
https://www.bleepingcomputer.com/news/security/crafty-threat-actor-uses-aged-domains-to-evade-security-platforms/
Qakbot/Qakbot_obama224_30.11.2022.txt at main · pr0xylife/Qakbot · GitHub
https://github.com/pr0xylife/Qakbot/blob/main/Qakbot_obama224_30.11.2022.txt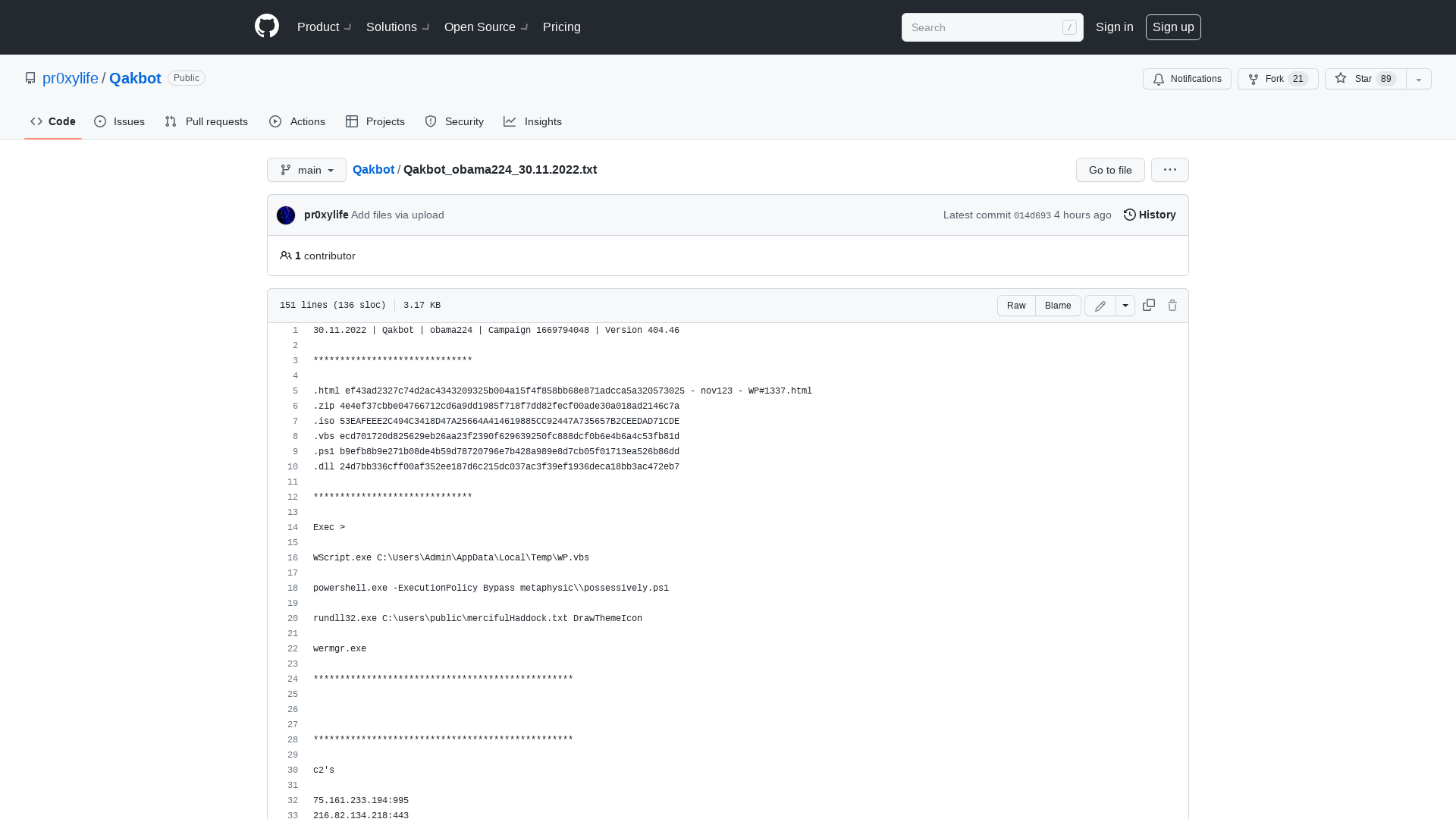
MalwareBazaar | SHA256 ef43ad2327c74d2ac4343209325b004a15f4f858bb68e871adcca5a320573025 (Quakbot)
https://bazaar.abuse.ch/sample/ef43ad2327c74d2ac4343209325b004a15f4f858bb68e871adcca5a320573025/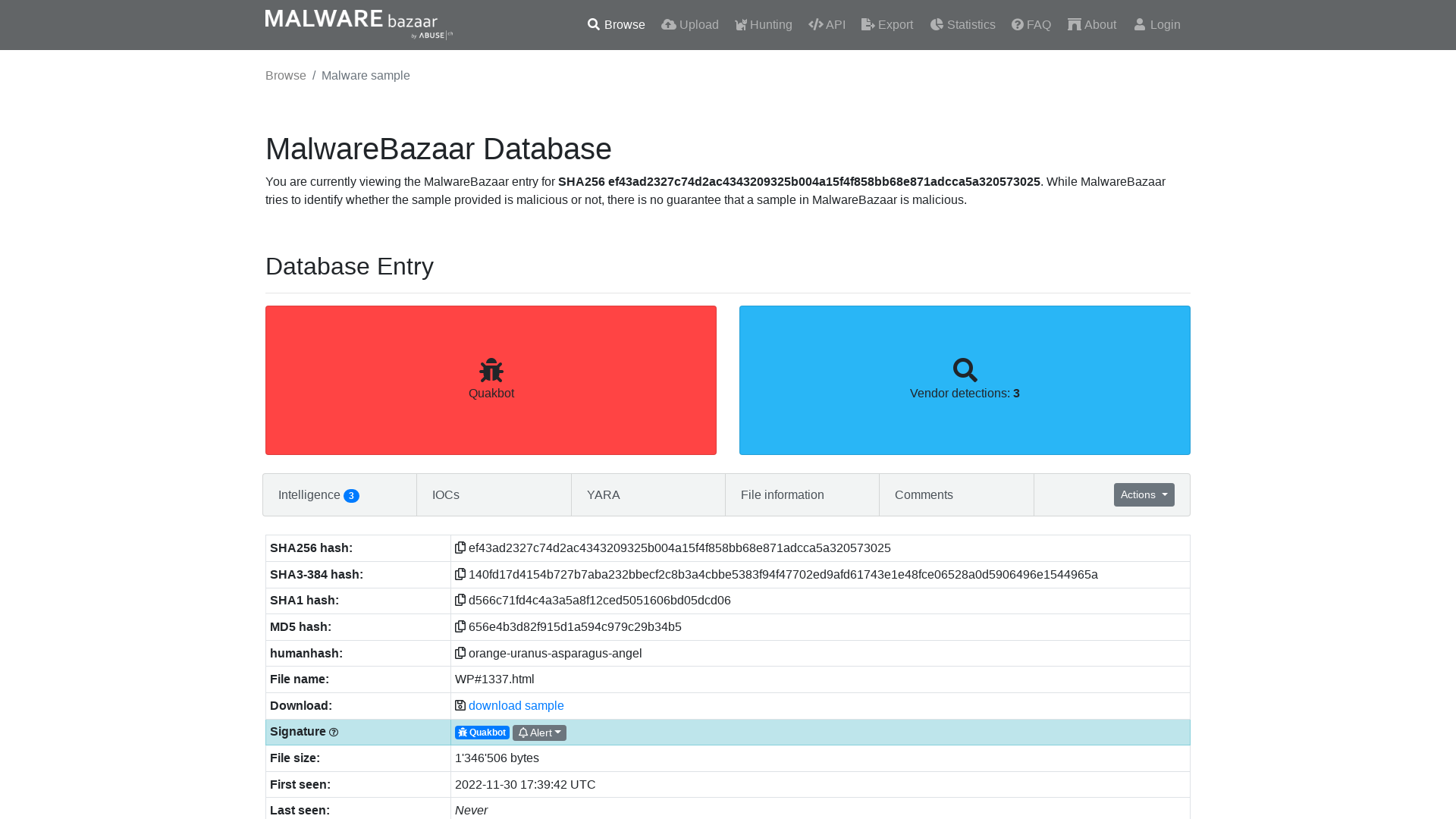
reecDeep on Twitter: "Hi folks, I've just released my #Hive #ransomware v5 keystream decryption tool publicly available. 👇 https://t.co/2L87S46v63 #infosec #malware #reverseengineering #CyberSecurity" / Twitter
https://twitter.com/reecdeep/status/1546766063223857152?s=20&t=hs_X8ps-LHC9sbgFc2iD2w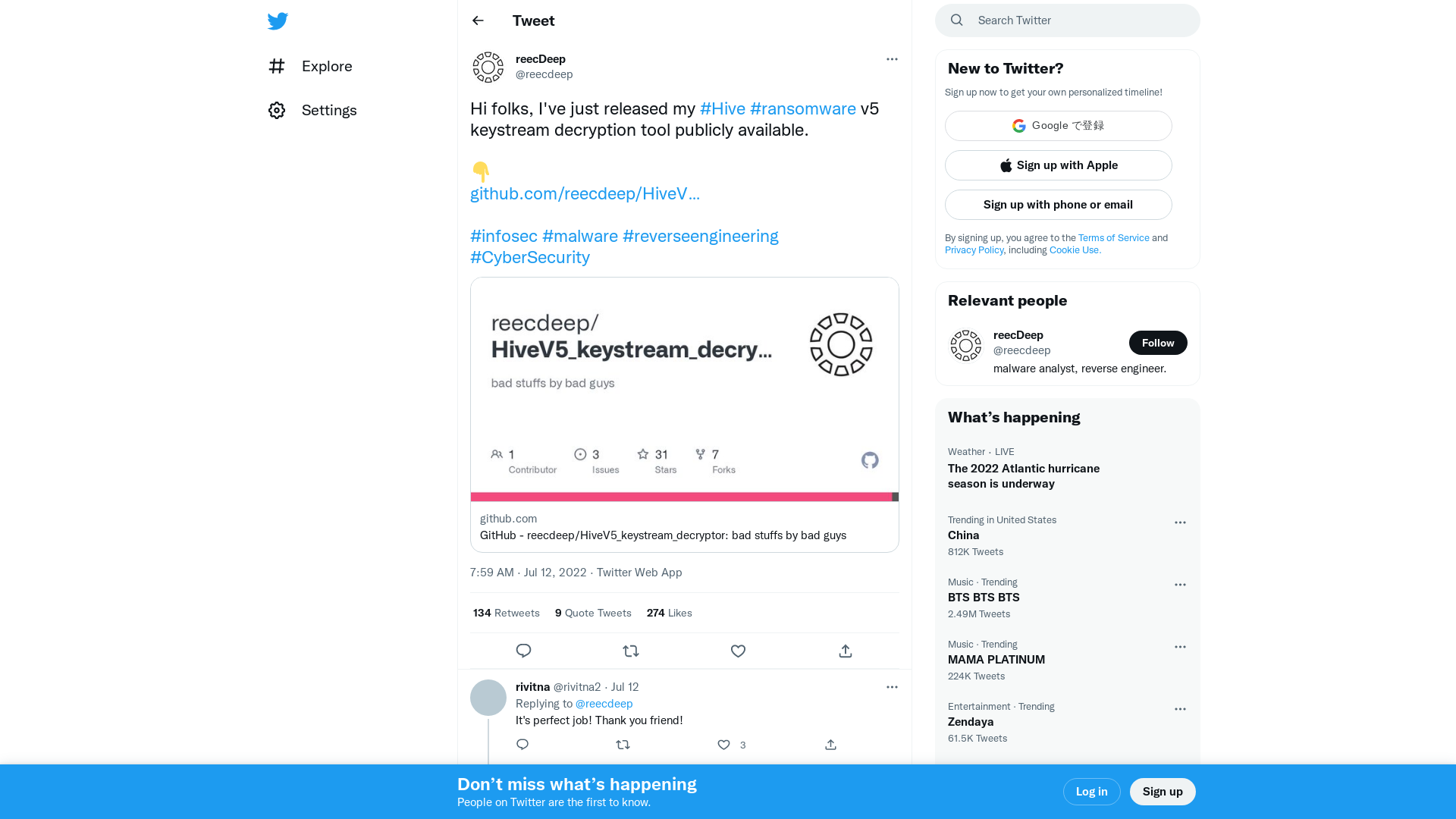
KRON4 News on Twitter: "San Francisco police clarified that it would not arm robots with guns. Instead, they would be equipped with explosives. https://t.co/u9h2SDPwOO" / Twitter
https://twitter.com/kron4news/status/1597689392746872834
Parliament approves Government’s privacy penalty bill | Our ministers – Attorney-General’s portfolio
https://ministers.ag.gov.au/media-centre/parliament-approves-governments-privacy-penalty-bill-28-11-2022
Looting Microsoft Configuration Manager | WithSecure™ Labs
https://labs.withsecure.com/publications/looting-microsoft-configuration-manager
Flight of the Bumblebee: Email Lures and File Sharing Services Lead to Malware
https://bit.ly/3oTxRN2
Trigona ransomware spotted in increasing attacks worldwide
https://www.bleepingcomputer.com/news/security/trigona-ransomware-spotted-in-increasing-attacks-worldwide/
Who’s swimming in South Korean waters? Meet ScarCruft’s Dolphin | WeLiveSecurity
https://www.welivesecurity.com/2022/11/30/whos-swimming-south-korean-waters-meet-scarcrufts-dolphin/
MalwareBazaar | Browse Checking your browser
https://bit.ly/3AXXJOl
French Electricity Provider Fined for Storing Users' Passwords with Weak MD5 Algorithm
https://thehackernews.com/2022/11/french-electricity-provider-fined-for.html
Flight of the Predator - Lighthouse Reports
https://www.lighthousereports.nl/investigation/flight-of-the-predator/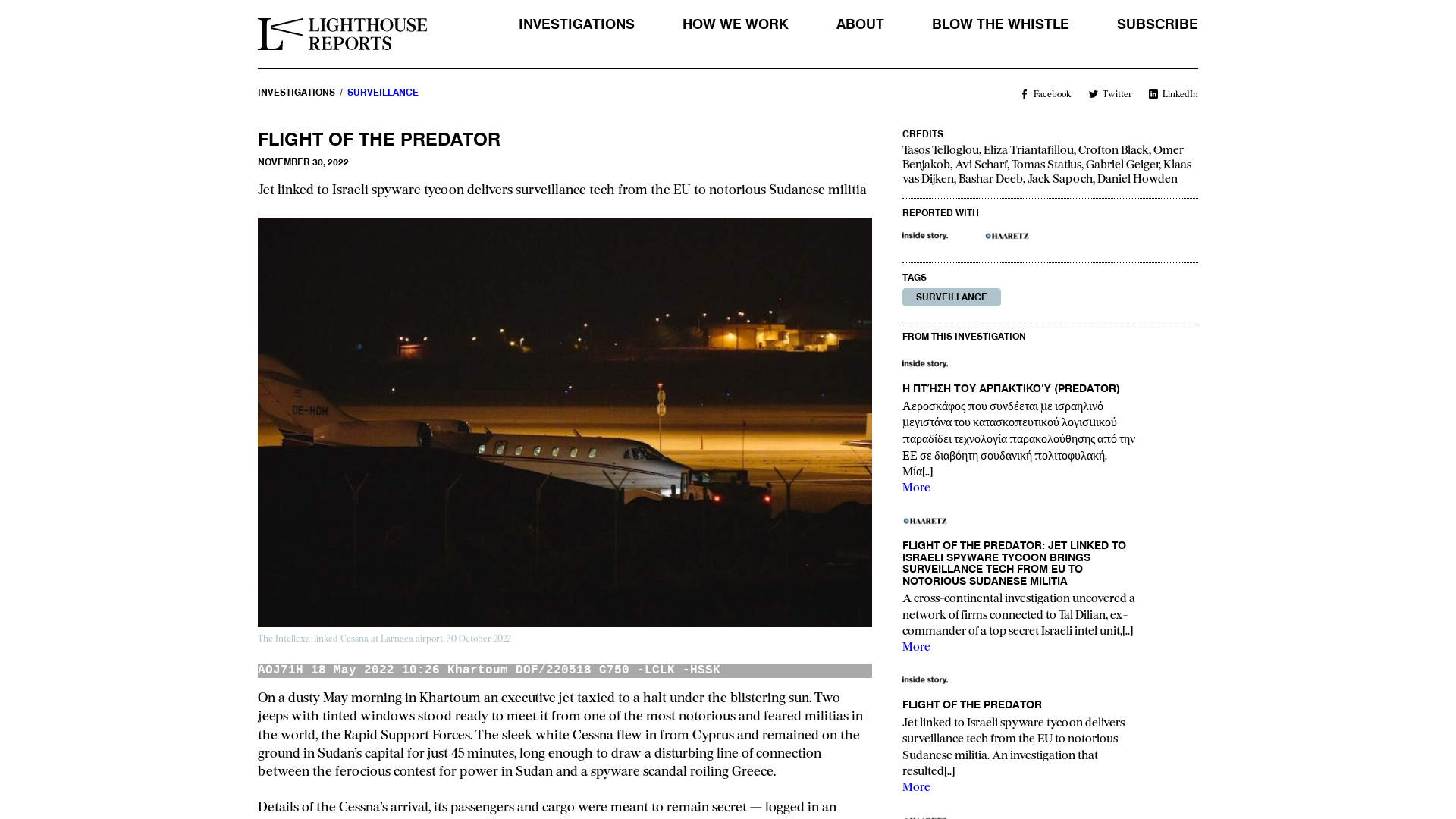
Notice of Recent Security Incident - The LastPass Blog
https://blog.lastpass.com/2022/11/notice-of-recent-security-incident/
Linux Kernel: UAF in Bluetooth L2CAP Handshake · Advisory · google/security-research · GitHub
https://github.com/google/security-research/security/advisories/GHSA-pf87-6c9q-jvm4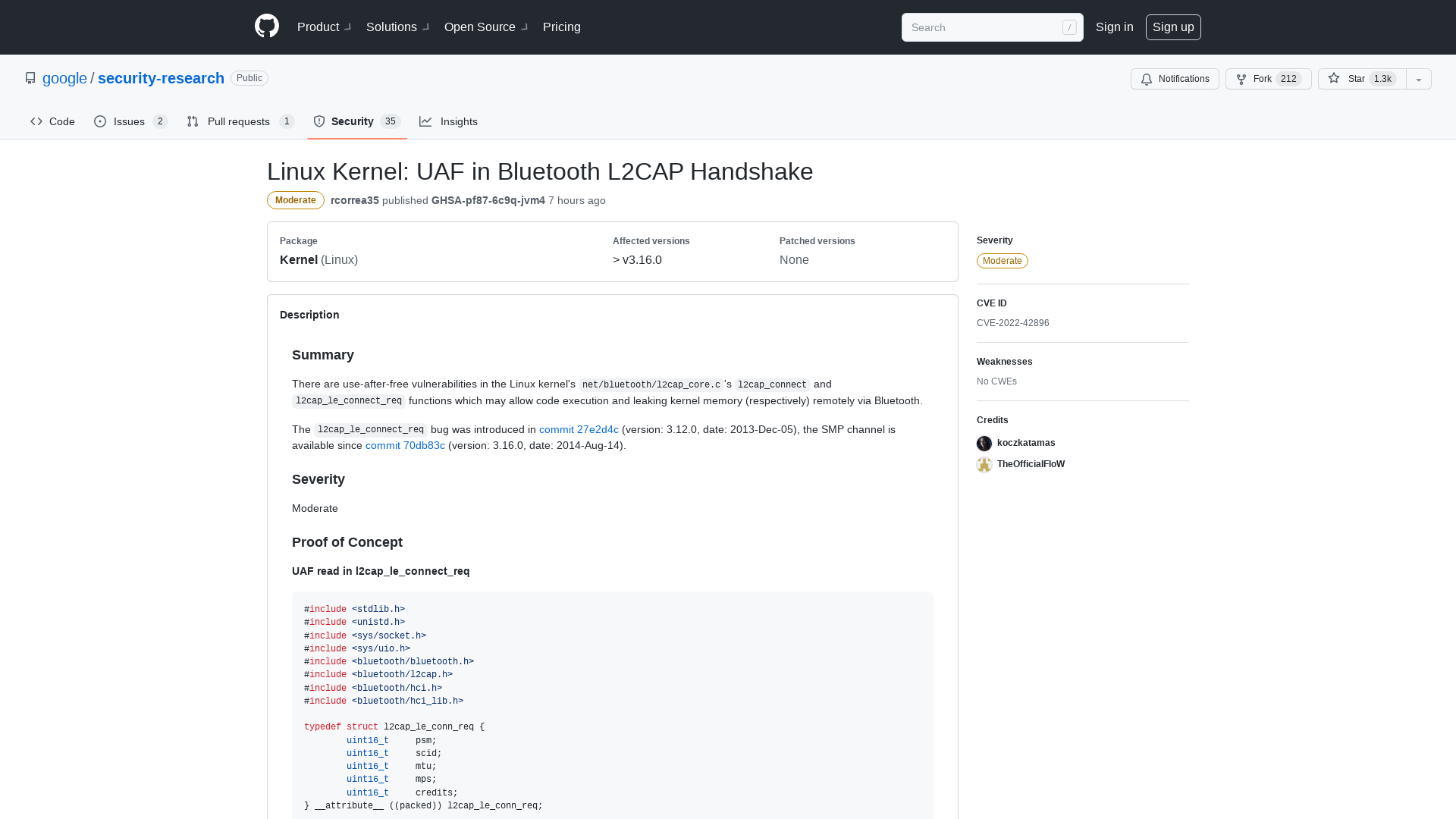
How to Find MFA Bypasses in Conditional Access Policies - YouTube
https://youtu.be/SK1zgqaAZ2E
Threat actors are offering access to corporate networks via unauthorized Fortinet VPN accessSecurity Affairs
https://securityaffairs.co/wordpress/139085/cyber-crime/iabs-offers-access-via-fortinet-products.html
Linux Kernel: Infoleak in Bluetooth L2CAP Handling · Advisory · google/security-research · GitHub
https://github.com/google/security-research/security/advisories/GHSA-vccx-8h74-2357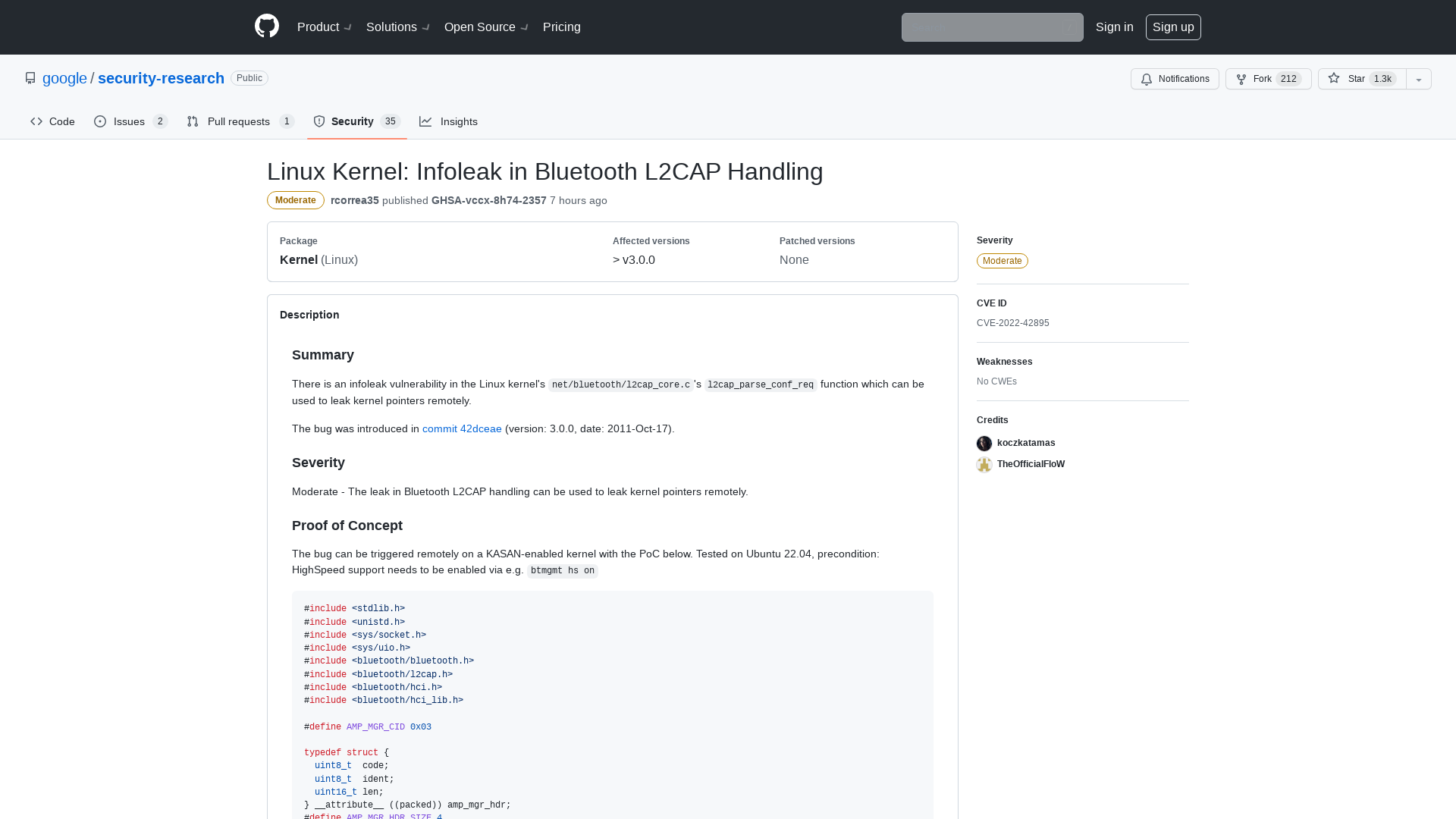
Xiongmai IoT Exploitation - Blog - VulnCheck
https://vulncheck.com/blog/xiongmai-iot-exploitation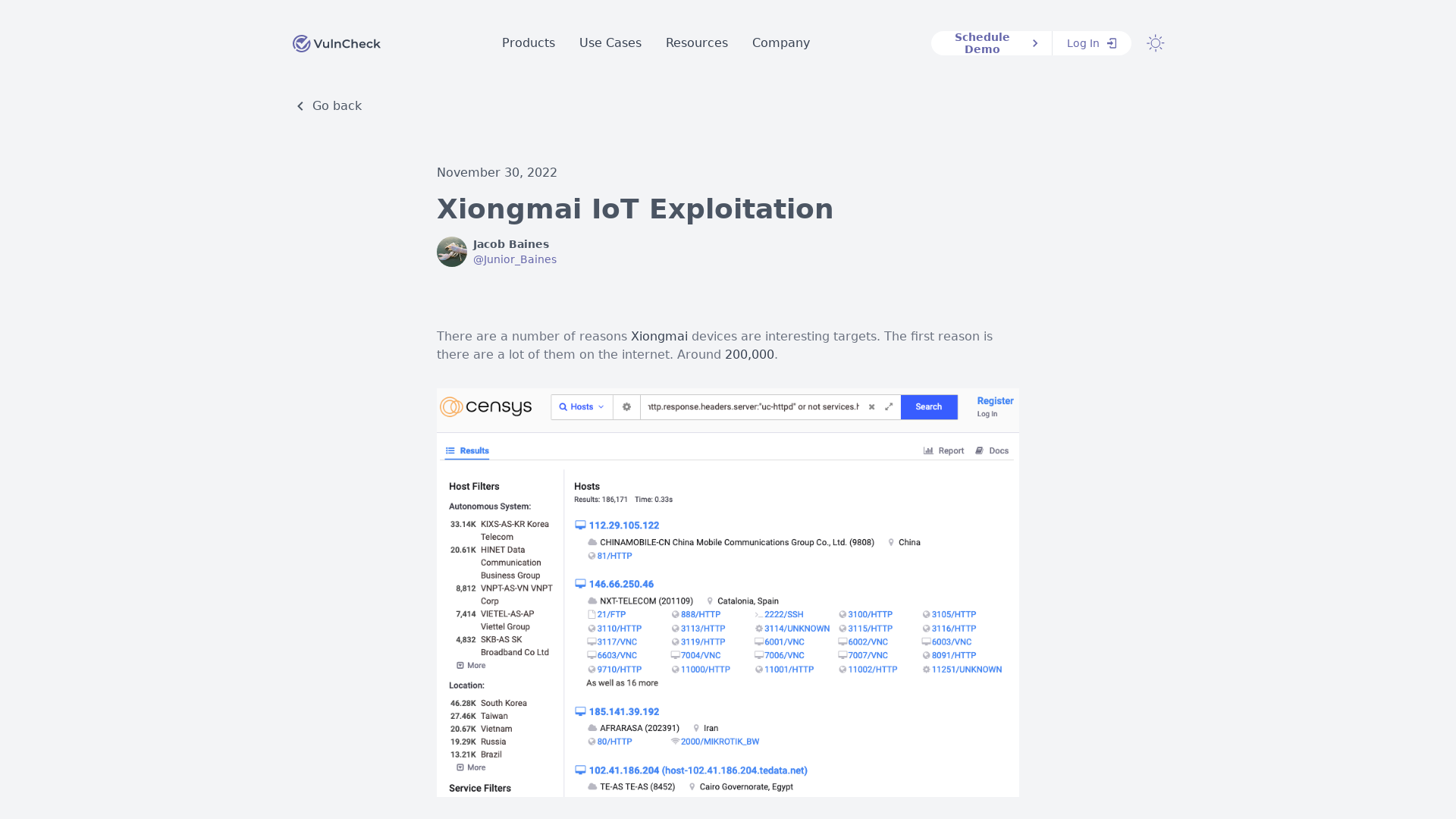
Google discovers Windows exploit framework used to deploy spyware
https://www.bleepingcomputer.com/news/security/google-discovers-windows-exploit-framework-used-to-deploy-spyware/
GitHub - rabobank-cdc/DeTTECT: Detect Tactics, Techniques & Combat Threats
https://github.com/rabobank-cdc/DeTTECT