Threat Hunting with VirusTotal ~ VirusTotal Blog
https://blog.virustotal.com/2022/11/threat-hunting-with-virustotal.html
Guide to Reversing and Exploiting iOS binaries Part 2: ARM64 ROP Chains
https://bit.ly/3BgvLxt
Heap Overflows on iOS ARM64: Heap Spraying, Use-After-Free (Part 3)
https://bit.ly/3gGI7rx
The Old Guard on Twitter: ""Every single Google Maps in the entire world is infected with Pegasus spyware to this day." 🤡 #nsogroup #spyware #fraud #infosec #charlatans #dumbass https://t.co/txuc44i3hZ" / Twitter
https://twitter.com/jonathandata0/status/1597395888766611456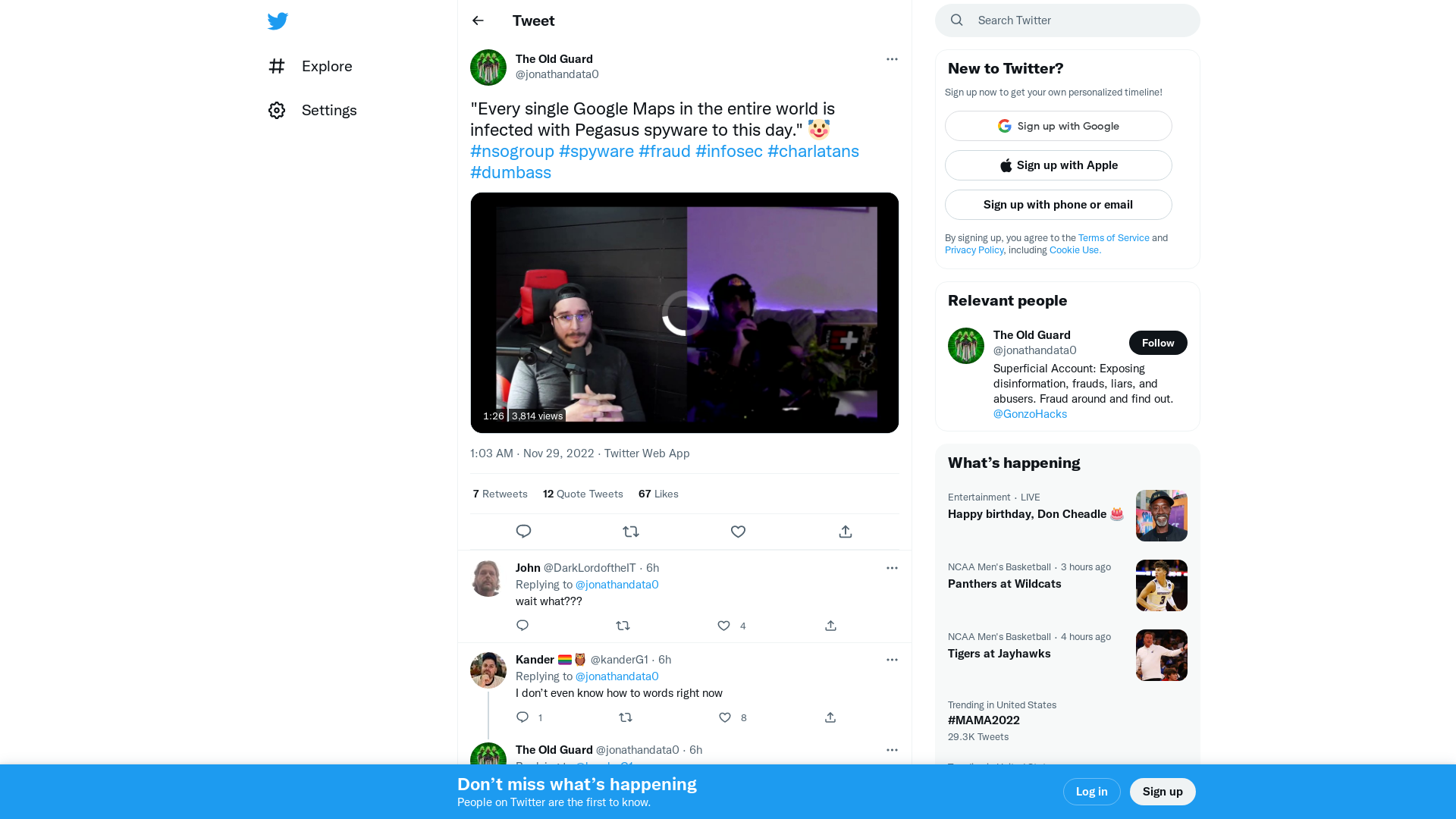
How to Reverse Engineer and Patch an iOS Application for Beginners: Part I
https://bit.ly/3inJgop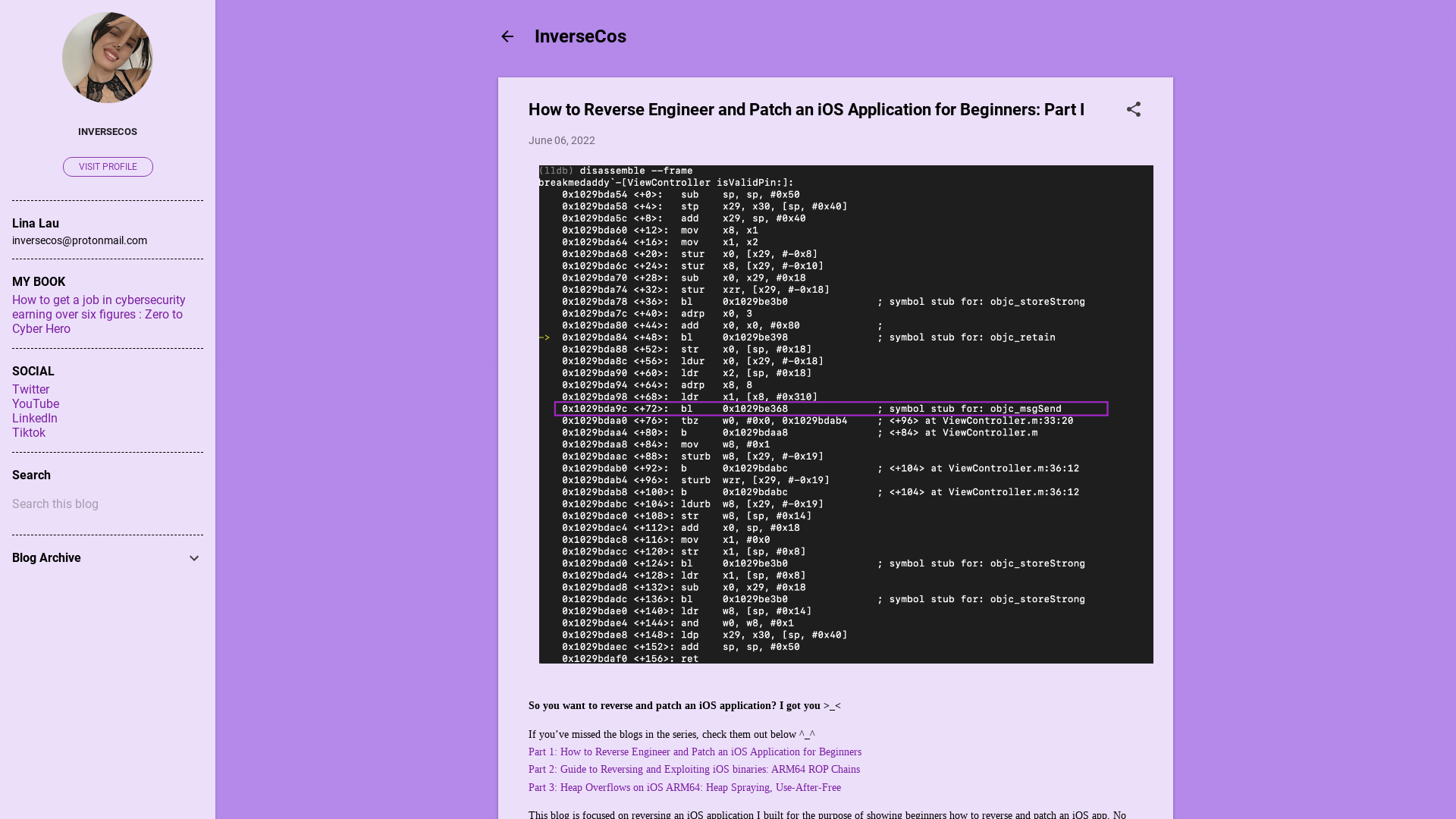
Emotet Strikes Again - Lnk File Leads to Domain Wide Ransomware - The DFIR Report
https://thedfirreport.com/2022/11/28/emotet-strikes-again-lnk-file-leads-to-domain-wide-ransomware/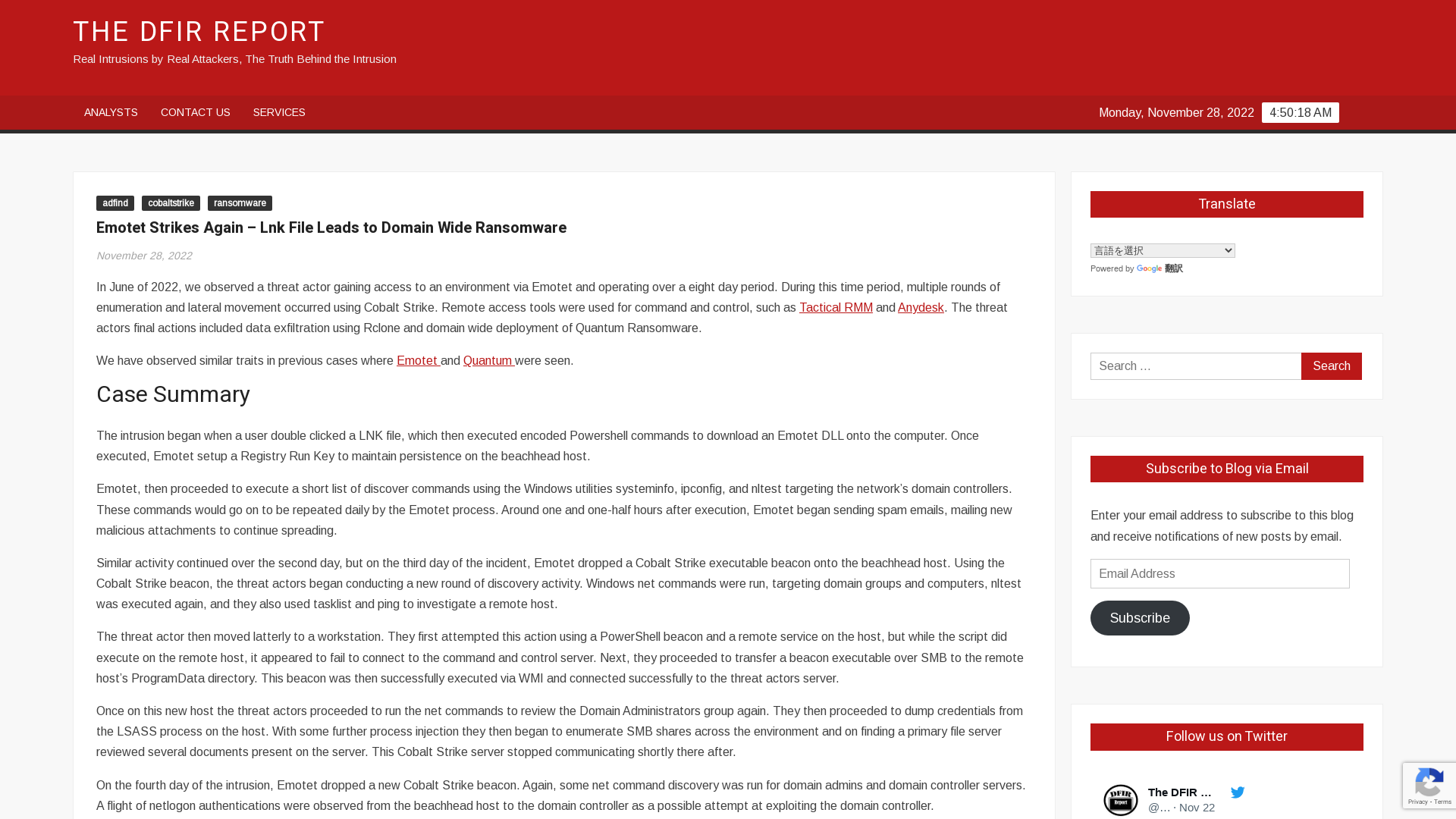
Sign in to GitHub · GitHub
http://cs.github.com
Hijacking service workers via DOM Clobbering | PortSwigger Research
https://portswigger.net/research/hijacking-service-workers-via-dom-clobbering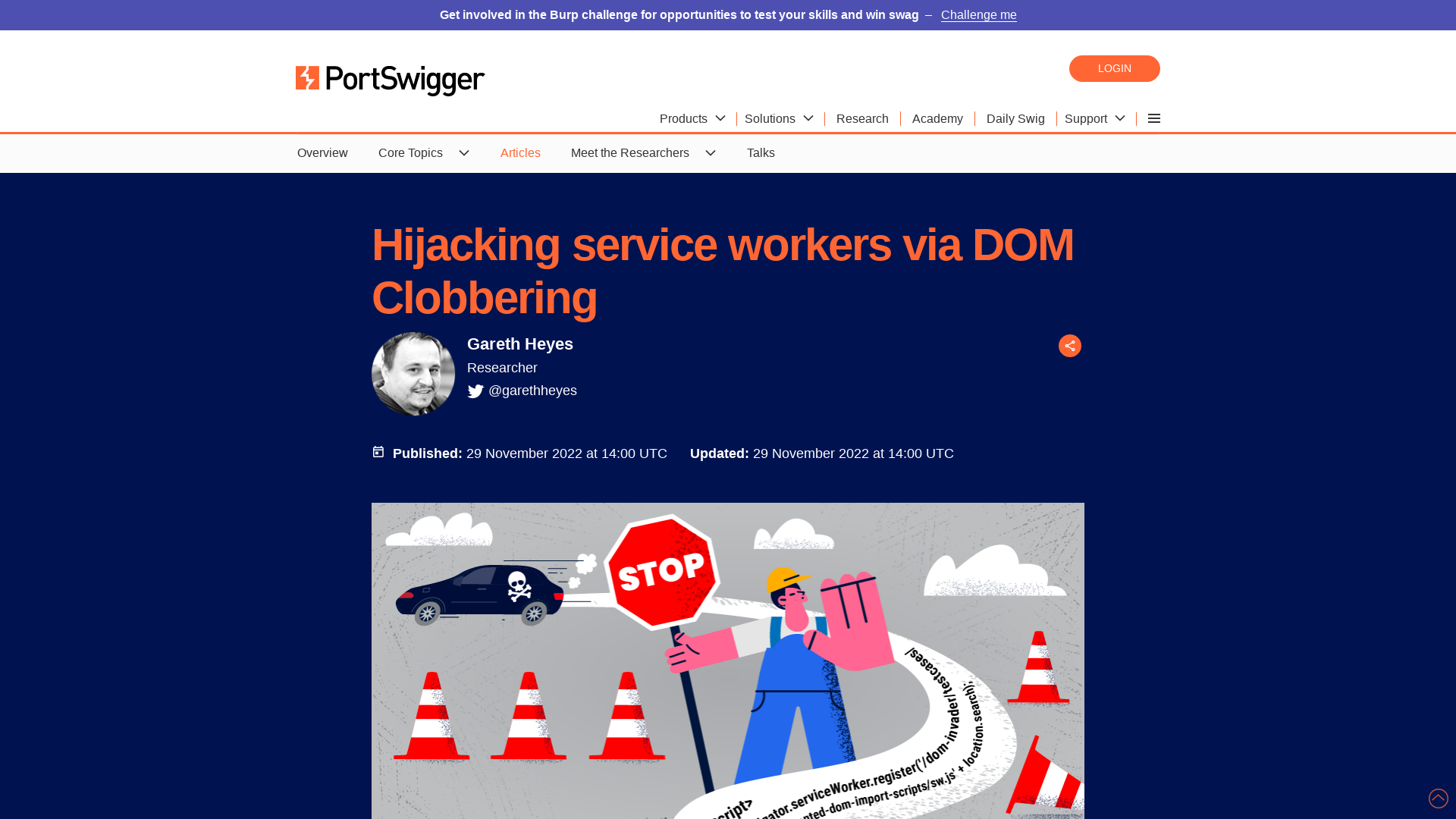
Sergio Caltagirone @[email protected] on Twitter: "We at @GblEmancipation are raising money for our next set of tools and expansions into more countries. Each $100k raised enables us to positively identify one more human trafficking victim daily. Please consider a donation. https://t.co/DPZAHpPTOn #GivingTuesday #cybersecurity" / Twitter
https://twitter.com/cnoanalysis/status/1597604882416017408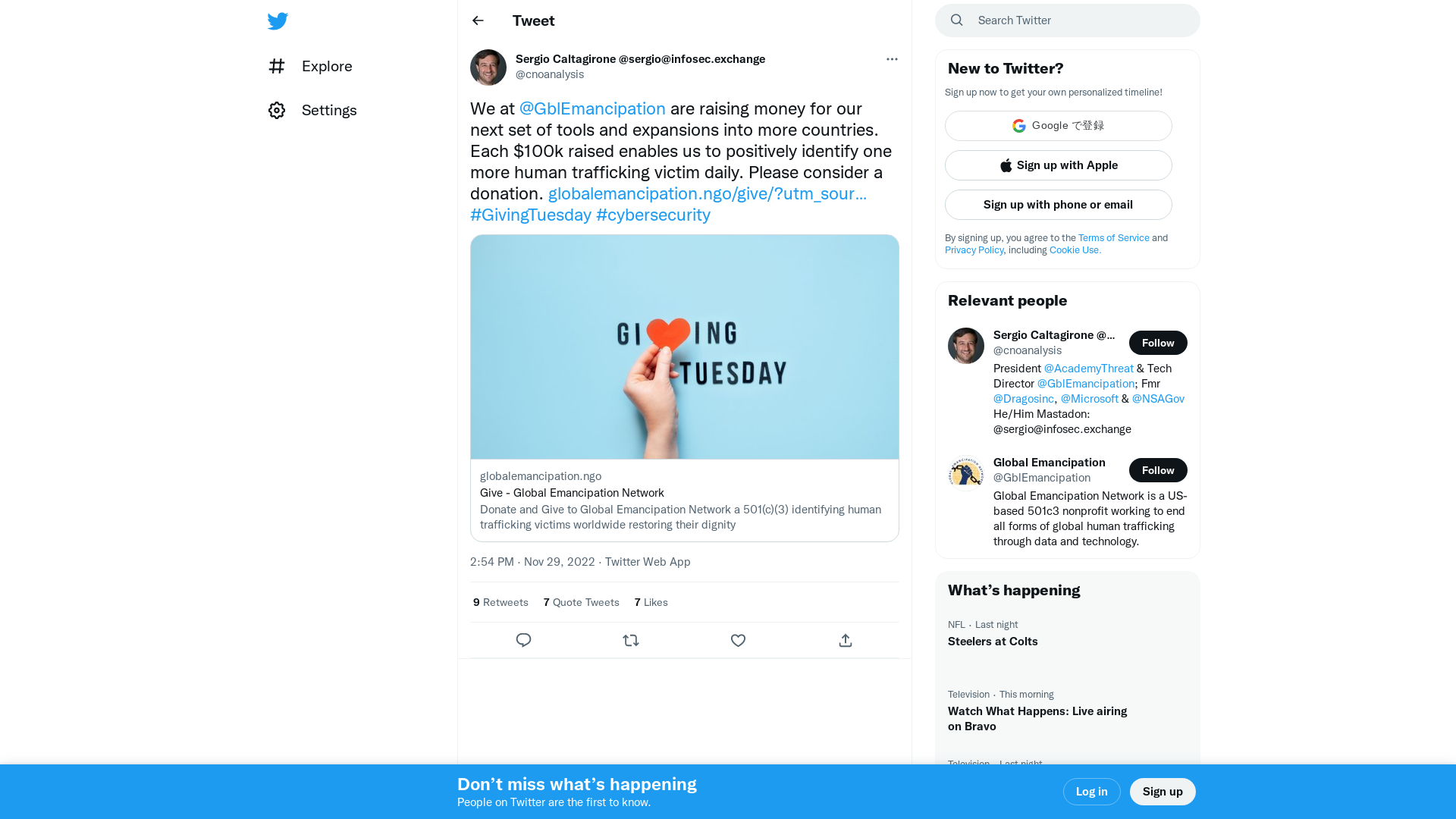
Get started with insider risk management forensic evidence (preview) - Microsoft Purview (compliance) | Microsoft Learn
https://learn.microsoft.com/en-us/microsoft-365/compliance/insider-risk-management-forensic-evidence-configure?WT.mc_id=EM-MVP-5003929&view=o365-worldwide
The Anatomy of a Threat Hunting Hypothesis — Lauren Proehl
https://www.laurenproehl.com/blog/2022/11/28/the-anatomy-of-a-threat-hunting-hypothesis
Linux Kernel: UAF in Bluetooth L2CAP Handshake · Advisory · google/security-research · GitHub
https://github.com/google/security-research/security/advisories/GHSA-pf87-6c9q-jvm4
Linux Kernel: Infoleak in Bluetooth L2CAP Handling · Advisory · google/security-research · GitHub
https://github.com/google/security-research/security/advisories/GHSA-vccx-8h74-2357
CISA Warns of Actively Exploited Critical Oracle Fusion Middleware Vulnerability
https://thehackernews.com/2022/11/cisa-warns-of-actively-exploited.html
APT_REPORT/Threat Hunting with VirusTotal.pdf at master · blackorbird/APT_REPORT · GitHub
https://github.com/blackorbird/APT_REPORT/blob/master/APT-hunting/Threat%20Hunting%20with%20VirusTotal.pdf
Enter "Sandbreak" - Vulnerability In vm2 Sandbox Module Enables Remote Code Execution (CVE-2022-36067)
https://www.oxeye.io/blog/vm2-sandbreak-vulnerability-cve-2022-36067
Always Another Secret: Lifting the Haze on China-nexus Espionage in Southeast Asia | Mandiant
https://www.mandiant.com/resources/blog/china-nexus-espionage-southeast-asia
Acer fixes UEFI bugs that can be used to disable Secure Boot
https://www.bleepingcomputer.com/news/security/acer-fixes-uefi-bugs-that-can-be-used-to-disable-secure-boot/