Notepad++ supply chain attack breakdown | Securelist
https://securelist.com/notepad-supply-chain-attack/118708/
Operation Neusploit: APT28 Uses CVE-2026-21509 | ThreatLabz
https://www.zscaler.com/blogs/security-research/apt28-leverages-cve-2026-21509-operation-neusploit
Georgy Kucherin on X: "It turned out there are many more payloads used in the Notepad++ attack! To stay undetected, its masterminds were COMPLETELY changing execution chains about every month. Here are more IPs used in the attack: 45.76.155[.]202 45.32.144[.]255 Read below for many other IoCs! [1/8] https://t.co/BGrMchxGjs" / X
https://x.com/kucher1n/status/2018626488434843674?s=46&t=C0_T_re0wRP_NfKa27Xw9w![Georgy Kucherin on X: "It turned out there are many more payloads used in the Notepad++ attack! To stay undetected, its masterminds were COMPLETELY changing execution chains about every month. Here are more IPs used in the attack: 45.76.155[.]202 45.32.144[.]255 Read below for many other IoCs! [1/8] https://t.co/BGrMchxGjs" / X](/image/screenshot/6179b80b55dd205ffd9cf40b956cd3ff.png)
Notepad++ Hijacked by State-Sponsored Hackers | Notepad++
https://notepad-plus-plus.org/news/hijacked-incident-info-update/
The Chrysalis Backdoor: A Deep Dive into Lotus Blossom’s toolkit
https://www.rapid7.com/blog/post/tr-chrysalis-backdoor-dive-into-lotus-blossoms-toolkit/
Wave of Citrix NetScaler scans use thousands of residential proxies
https://www.bleepingcomputer.com/news/security/wave-of-citrix-netscaler-scans-use-thousands-of-residential-proxies/
CISA flags critical SolarWinds RCE flaw as exploited in attacks
https://www.bleepingcomputer.com/news/security/cisa-flags-critical-solarwinds-rce-flaw-as-actively-exploited/
Open-source attacks move through normal development workflows - Help Net Security
https://www.helpnetsecurity.com/2026/02/03/open-source-attacks-supply-chain-development-workflows/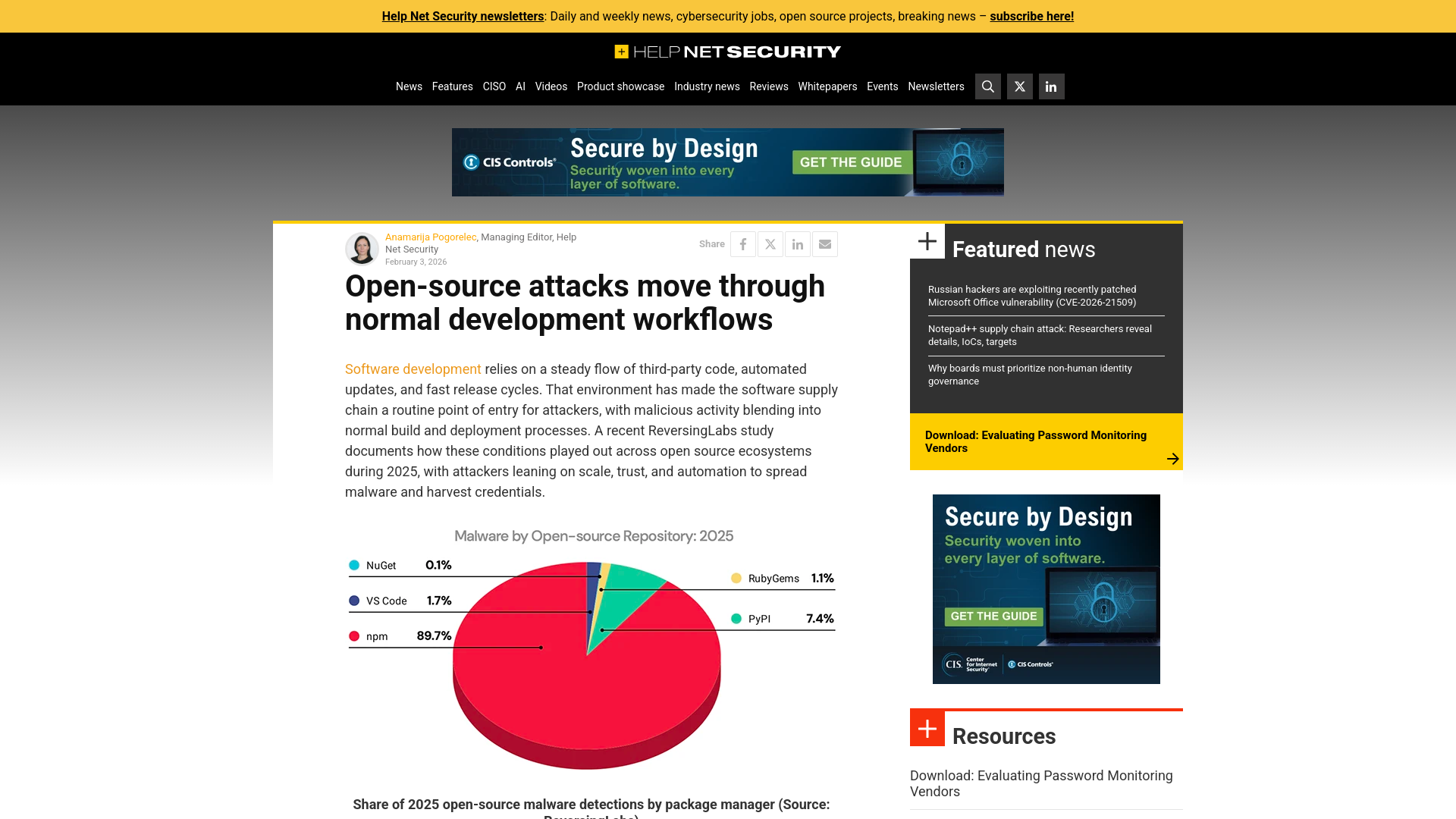
MalwareBazaar | SHA256 fd3f13db41cd5b442fa26ba8bc0e9703ed243b3516374e3ef89be71cbf07436b
https://bazaar.abuse.ch/sample/fd3f13db41cd5b442fa26ba8bc0e9703ed243b3516374e3ef89be71cbf07436b/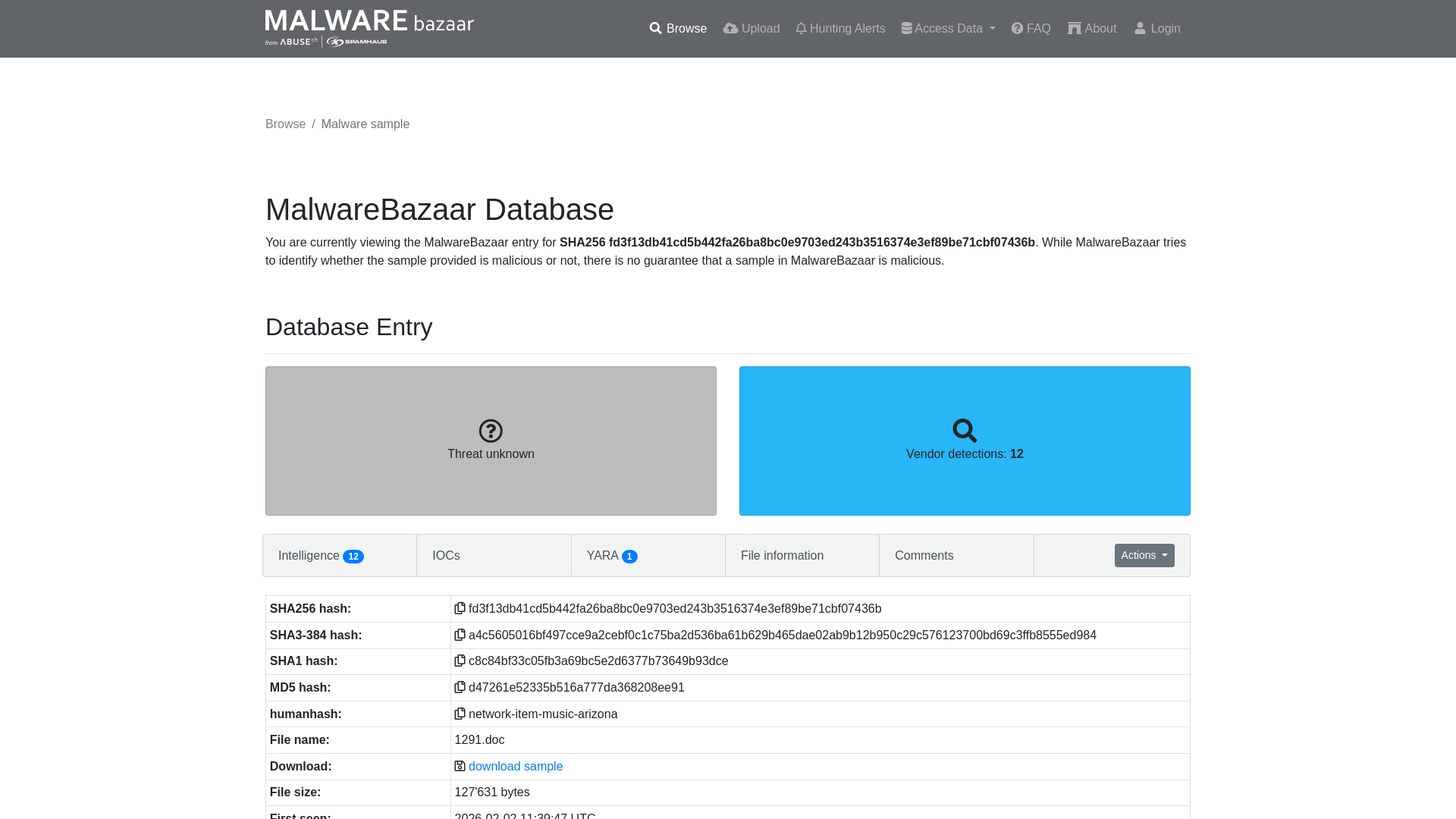
Notepad++ Hosting Breach Attributed to China-Linked Lotus Blossom Hacking Group
https://thehackernews.com/2026/02/notepad-hosting-breach-attributed-to.html