Threat Actors Expand Abuse of Microsoft Visual Studio Code
https://www.jamf.com/blog/threat-actors-expand-abuse-of-visual-studio-code/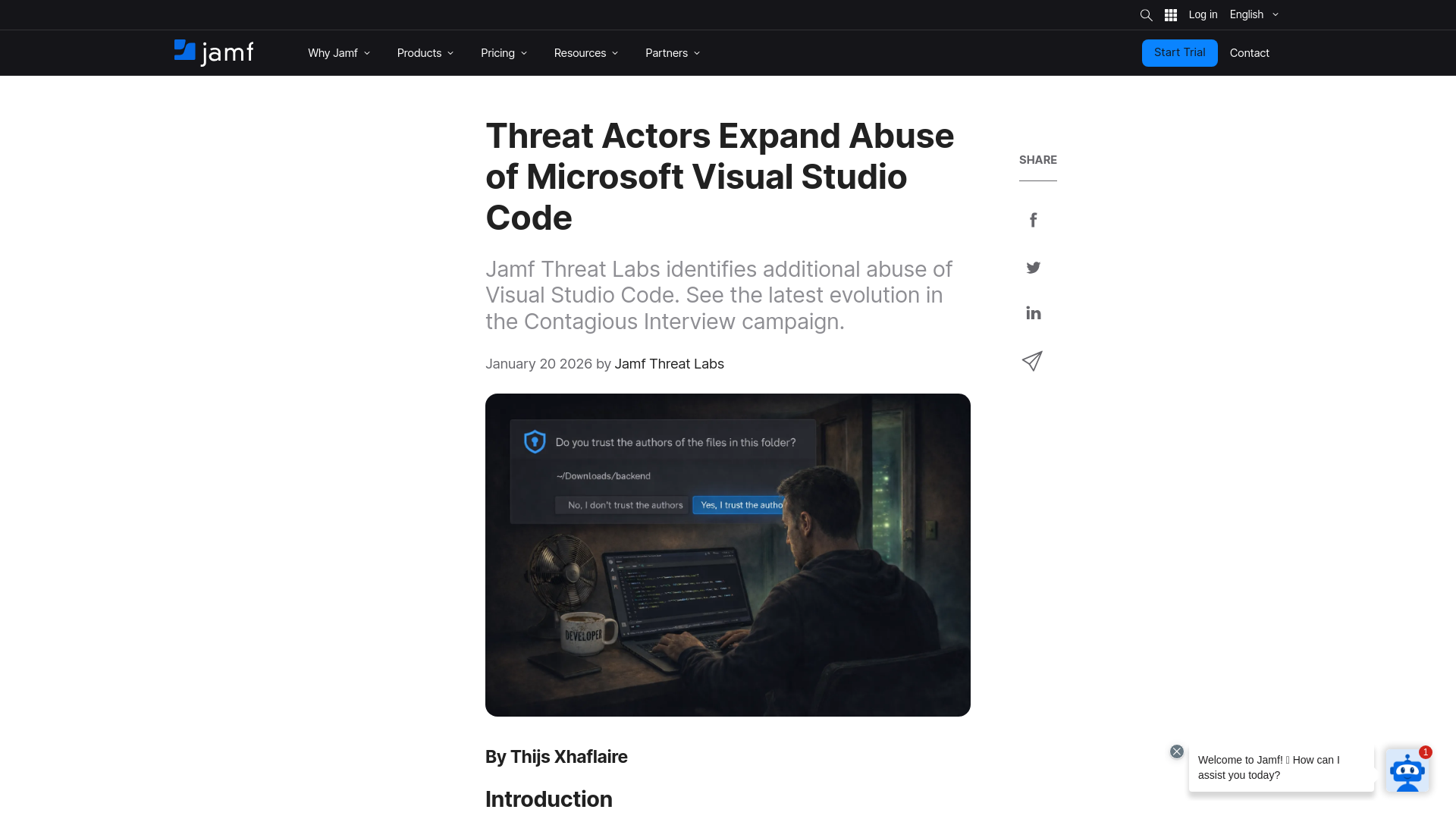
Misconfiguration-Manager/attack-techniques/TAKEOVER/TAKEOVER-5/takeover-5_description.md at main · subat0mik/Misconfiguration-Manager · GitHub
https://github.com/subat0mik/Misconfiguration-Manager/blob/main/attack-techniques/TAKEOVER/TAKEOVER-5/takeover-5_description.md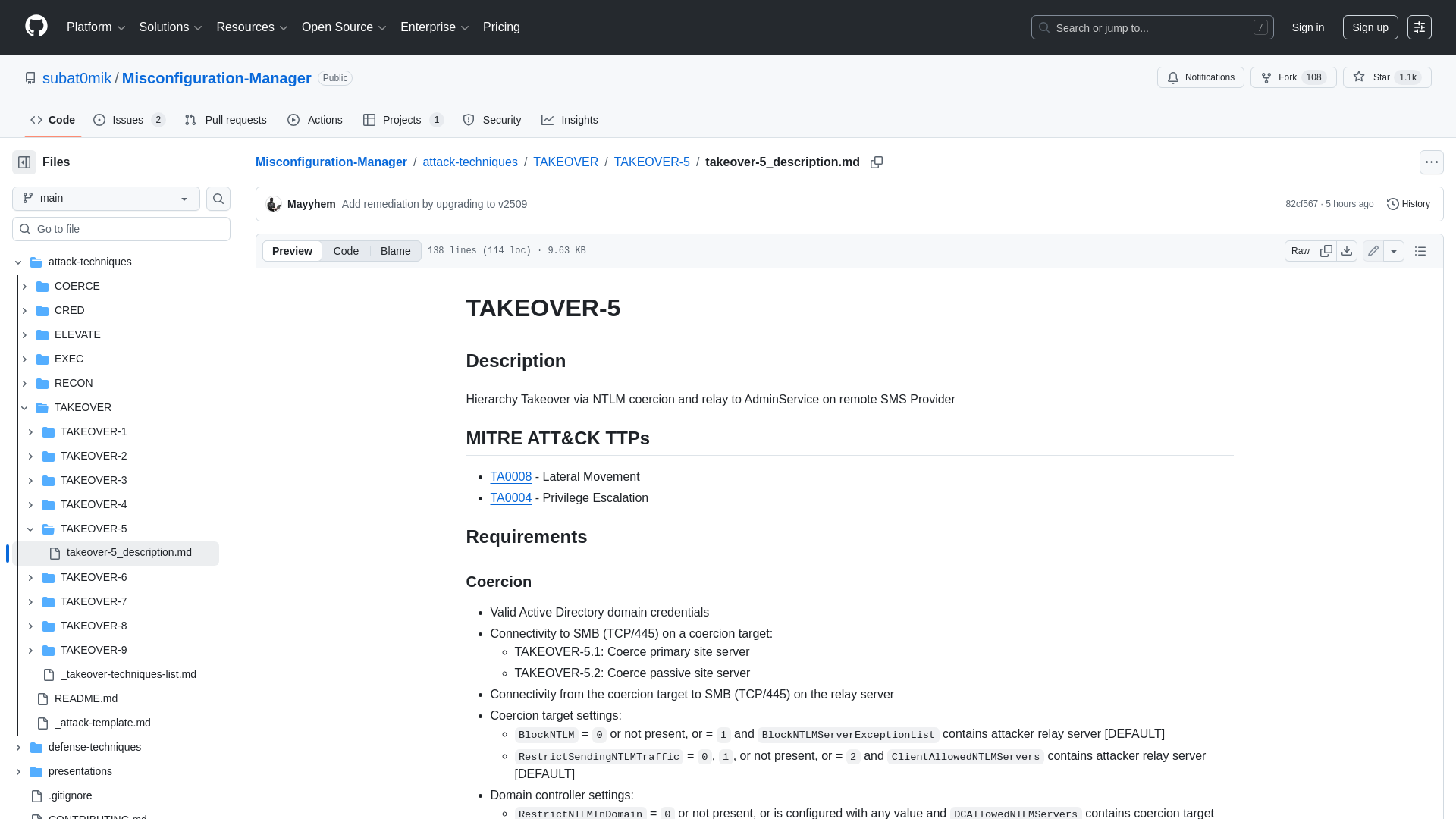
What's new in version 2509 - Configuration Manager | Microsoft Learn
https://learn.microsoft.com/en-us/intune/configmgr/core/plan-design/changes/whats-new-in-version-2509#adminservice-now-rejects-ntlm-authentication
Rishi Sunak: Xi hacks for secrets, Kim for cash, Putin for chaos
https://www.thetimes.com/business/companies-markets/article/rishi-sunak-xi-hacks-for-secrets-kim-for-cash-putin-for-chaos-h2drsnf0k
VoidLink: Evidence That the Era of Advanced AI-Generated Malware Has Begun - Check Point Research
https://research.checkpoint.com/2026/voidlink-early-ai-generated-malware-framework/
oss-sec: GNU InetUtils Security Advisory: remote authentication by-pass in telnetd
https://seclists.org/oss-sec/2026/q1/89
Everest Ransomware Group Allegedly Claims to Have Breached McDonald's India
https://cybersecuritynews.com/mcdonalds-india-everest-ransomware/
On the Coming Industrialisation of Exploit Generation with LLMs – Sean Heelan's Blog
https://sean.heelan.io/2026/01/18/on-the-coming-industrialisation-of-exploit-generation-with-llms/
Defender Timeline Downloader: Extending Data Retention for Incident Response | binaryanalys.is
https://binaryanalys.is/posts/defender_timeline