Radar #16: Week of 01/05/2026
https://loworbitsecurity.com/radar/radar16/
ClickFix attack uses fake Windows BSOD screens to push malware
https://www.bleepingcomputer.com/news/security/clickfix-attack-uses-fake-windows-bsod-screens-to-push-malware/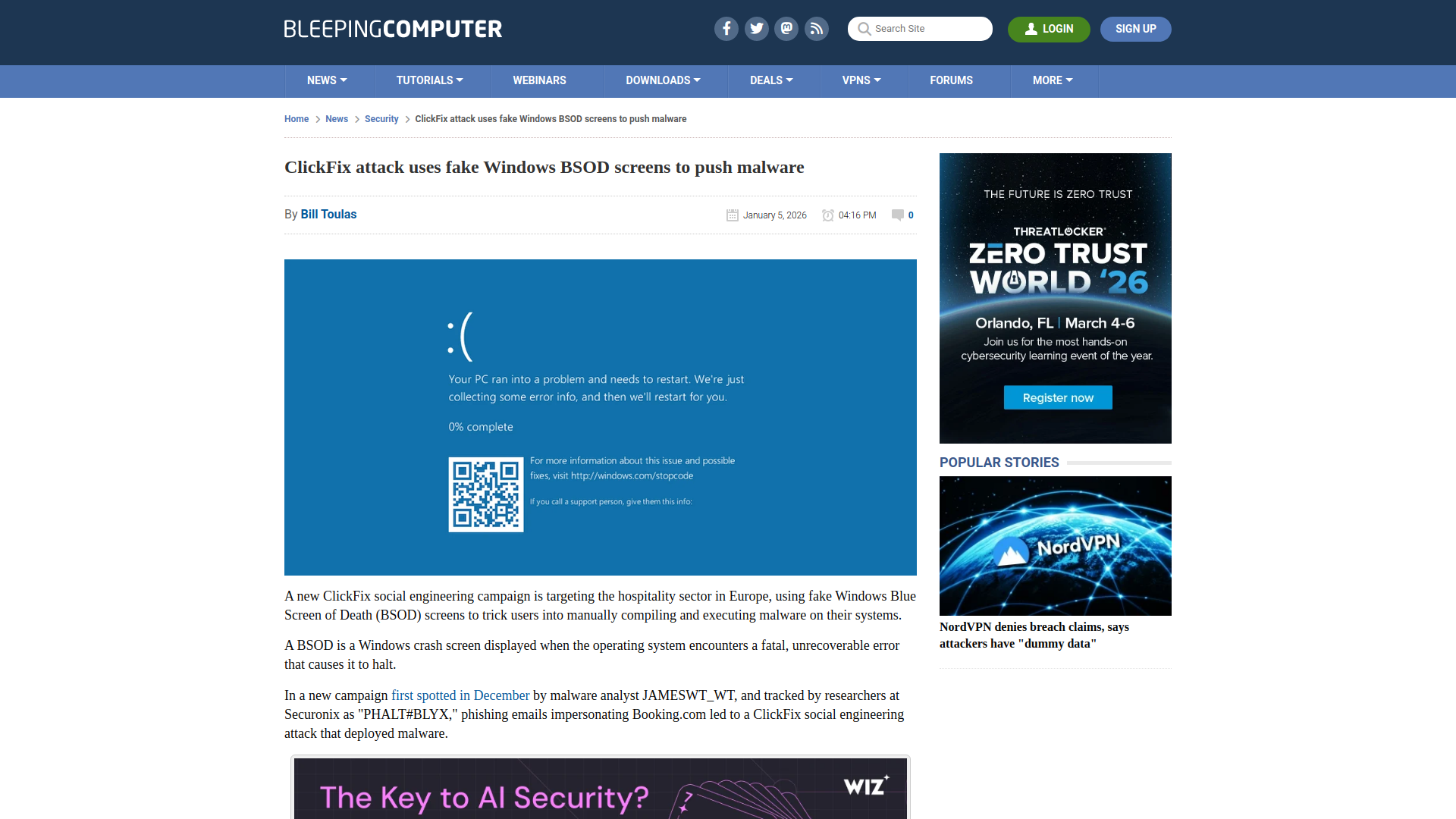
Sedgwick confirms breach at government contractor subsidiary
https://www.bleepingcomputer.com/news/security/sedgwick-confirms-breach-at-government-contractor-subsidiary/
Sign in to your account
https://purview.microsoft.com/audit/auditsearch
Two Chrome Extensions Caught Stealing ChatGPT and DeepSeek Chats from 900,000 Users
https://thehackernews.com/2026/01/two-chrome-extensions-caught-stealing.html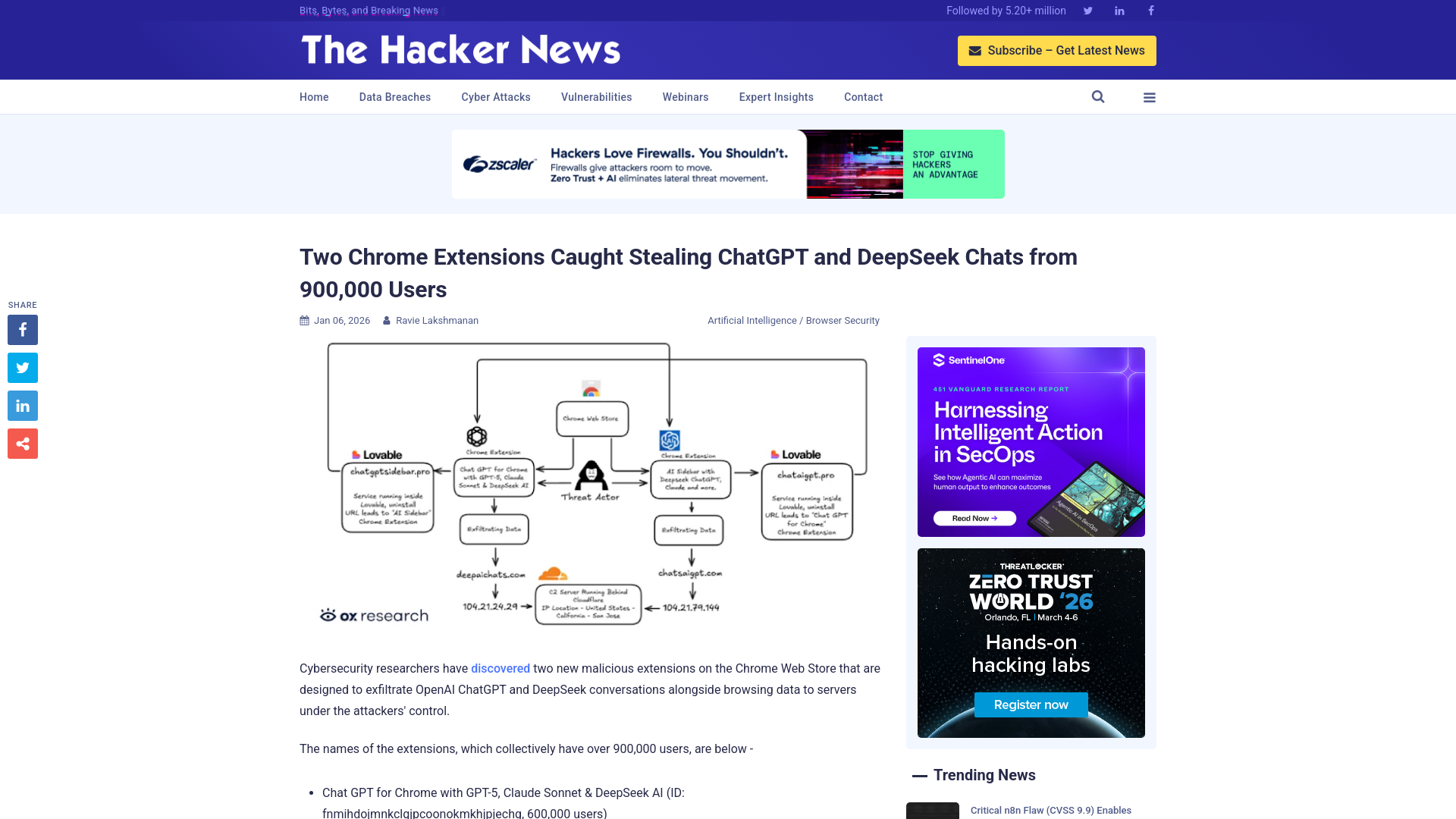
Workday Case
http://WorkdayCase.com
Kimwolf botnet leverages residential proxies to hijack 2M+ Android devices
https://securityaffairs.com/186559/malware/kimwolf-botnet-leverages-residential-proxies-to-hijack-2m-android-devices.html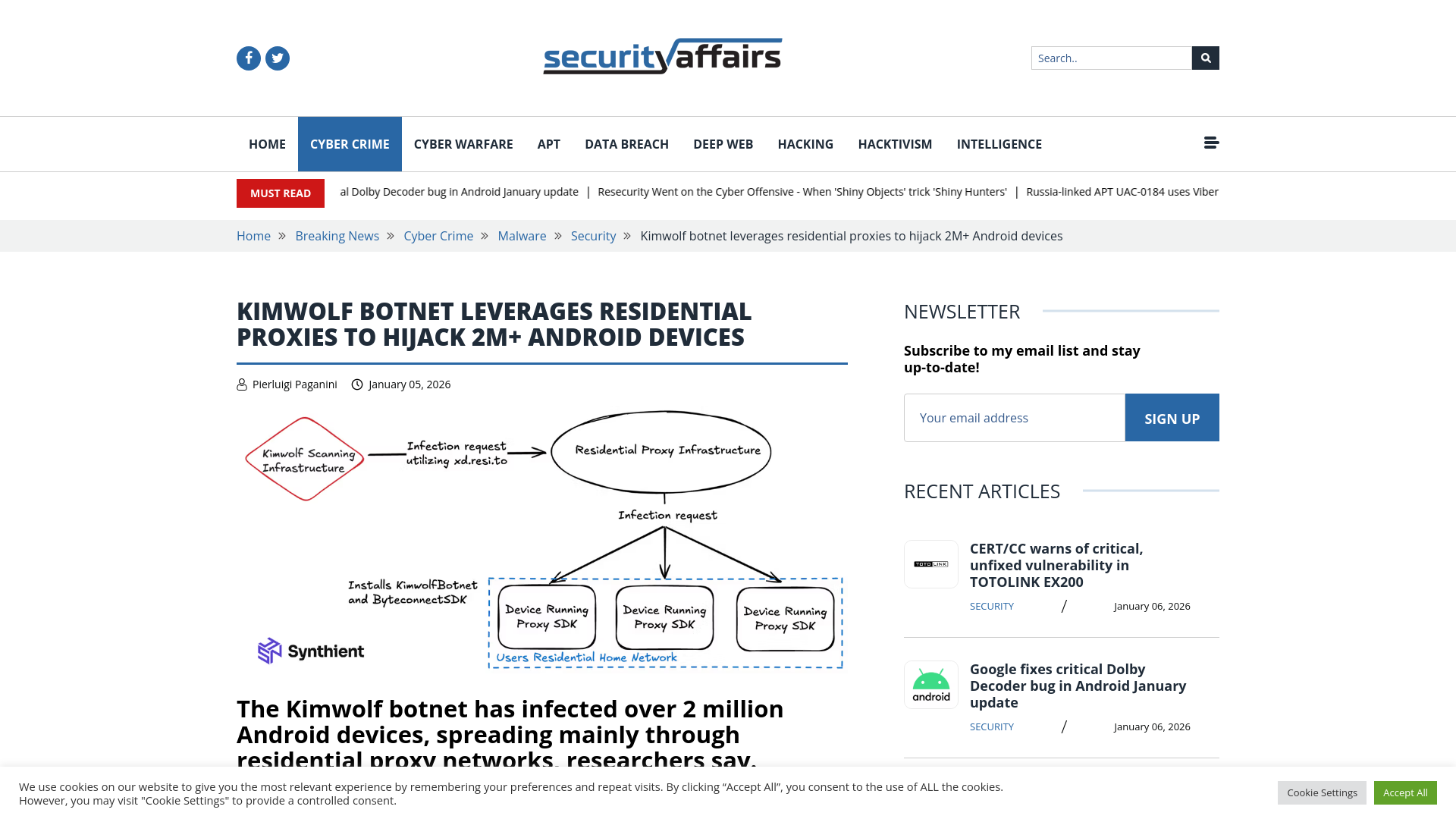
Unpatched Firmware Flaw Exposes TOTOLINK EX200 to Full Remote Device Takeover
https://thehackernews.com/2026/01/unpatched-firmware-flaw-exposes.html
RONINGLOADER: DragonBreath’s New Path to PPL Abuse — Elastic Security Labs
https://www.elastic.co/security-labs/roningloader
ProfileHound: Post-Escalation Tool Designed to Achieve Red Team Objectives
https://gbhackers.com/profilehound-post-escalation-tool/
Top 10 web hacking techniques of 2025: call for nominations | PortSwigger Research
https://portswigger.net/research/top-10-web-hacking-techniques-of-2025-nominations-open
EDR Evasion with Hardware Breakpoints: Blindside Technique
https://cymulate.com/blog/blindside-a-new-technique-for-edr-evasion-with-hardware-breakpoints/
Palo Alto Networks Senior Threat Intelligence Researcher (Unit 42) | SmartRecruiters
https://jobs.smartrecruiters.com/PaloAltoNetworks2/744000101662974
Cyllex - Advanced APT Emulation Framework
https://cyllex.io/
GitHub - S3N4T0R-0X0/APTs-Adversary-Simulation: This repository contains detailed adversary simulation APT campaigns targeting various critical sectors. Each simulation includes custom tools, C2 servers, backdoors, exploitation techniques, stagers, bootloaders, and other malicious artifacts that mirror those used in real world attacks .
https://github.com/S3N4T0R-0X0/APTs-Adversary-Simulation
ARM64 Reversing And Exploitation – Part 10 – Intro to Arm Memory Tagging Extension (MTE) - 8kSec
https://8ksec.io/arm64-reversing-and-exploitation-part-10-intro-to-arm-memory-tagging-extension-mte/
VS Code Forks Recommend Missing Extensions, Creating Supply Chain Risk in Open VSX
https://thehackernews.com/2026/01/vs-code-forks-recommend-missing.html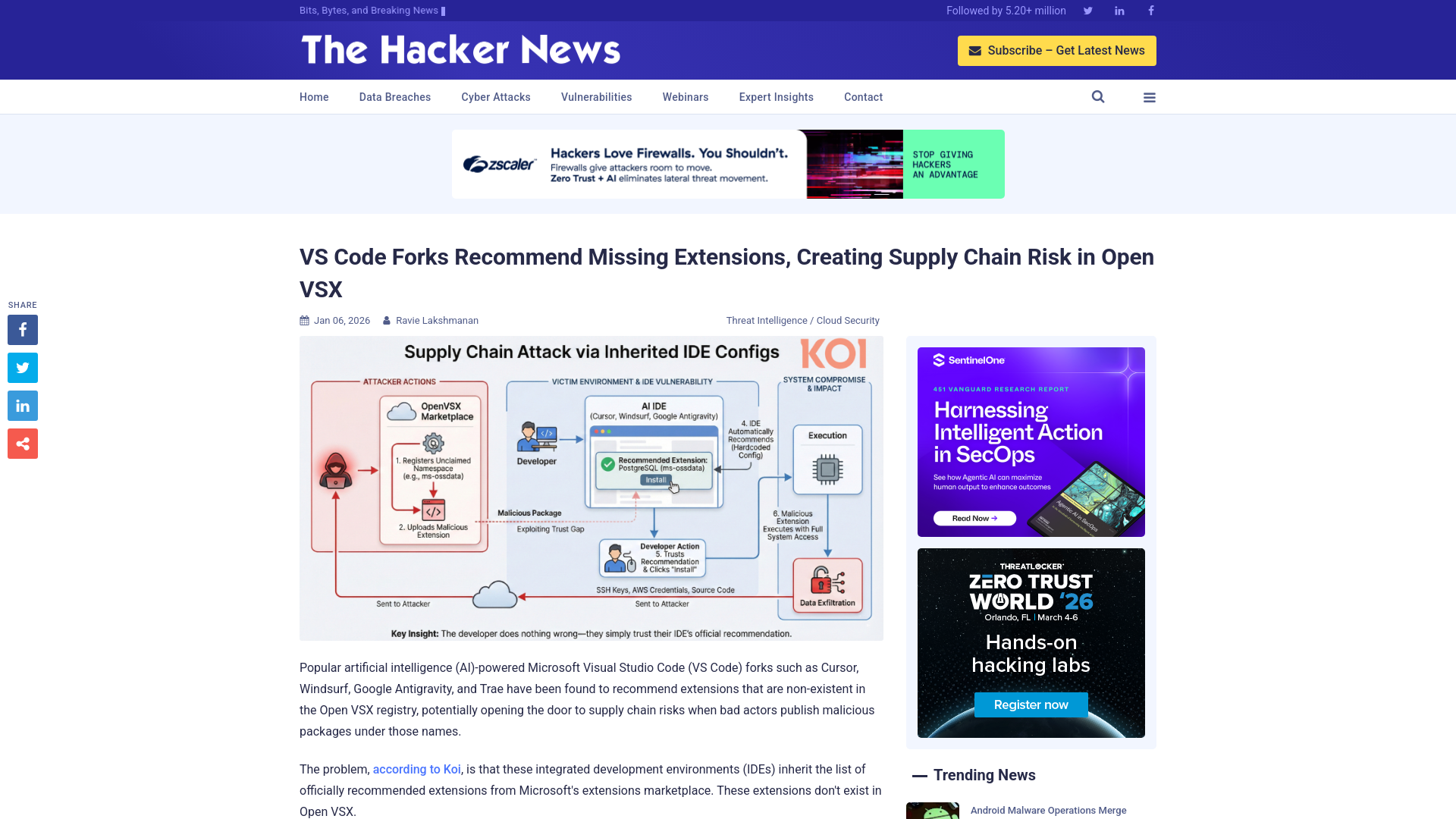
Taiwan says China's attacks on its energy sector increased tenfold
https://www.bleepingcomputer.com/news/security/taiwan-says-chinas-attacks-on-its-energy-sector-increased-tenfold/