PlushDaemon compromises network devices for adversary-in-the-middle attacks
https://www.welivesecurity.com/en/eset-research/plushdaemon-compromises-network-devices-for-adversary-in-the-middle-attacks/
Rhadamanthys Loader Deobfuscation | cyber.wtf
https://cyber.wtf/2025/11/19/rhadamanthys-loader-deobfuscation/
Meet ShinySp1d3r: New Ransomware-as-a-Service created by ShinyHunters
https://www.bleepingcomputer.com/news/security/meet-shinysp1d3r-new-ransomware-as-a-service-created-by-shinyhunters/
Mantra Information Security
https://blog.mantrainfosec.com/blog/18/prepared-statements-prepared-to-be-vulnerable
New WrtHug campaign hijacks thousands of end-of-life ASUS routers
https://www.bleepingcomputer.com/news/security/new-wrthug-campaign-hijacks-thousands-of-end-of-life-asus-routers/
Cloudflare outage on November 18, 2025
https://blog.cloudflare.com/18-november-2025-outage/
Native Sysmon functionality coming to Windows | Microsoft Community Hub
https://techcommunity.microsoft.com/blog/windows-itpro-blog/native-sysmon-functionality-coming-to-windows/4468112
Hackers Actively Exploiting 7-Zip Symbolic Link–Based RCE Vulnerability (CVE-2025-11001)
https://thehackernews.com/2025/11/hackers-actively-exploiting-7-zip.html
ServiceNow AI Agents Can Be Tricked Into Acting Against Each Other via Second-Order Prompts
https://thehackernews.com/2025/11/servicenow-ai-agents-can-be-tricked.html
Anatomy of an Akira Ransomware Attack: When a Fake CAPTCHA Led to 42 Days of Compromise
https://unit42.paloaltonetworks.com/fake-captcha-to-compromise/
Add Flowise Custom MCP RCE exploit (CVE-2025-8943) by Chocapikk · Pull Request #20705 · rapid7/metasploit-framework · GitHub
https://github.com/rapid7/metasploit-framework/pull/20705
China recruiting spies in the UK with 'sites like LinkedIn' • The Register
https://www.theregister.com/2025/11/19/mi5_linkedin_china_spy_warning/
Fortinet Warns of New FortiWeb CVE-2025-58034 Vulnerability Exploited in the Wild
https://thehackernews.com/2025/11/fortinet-warns-of-new-fortiweb-cve-2025.html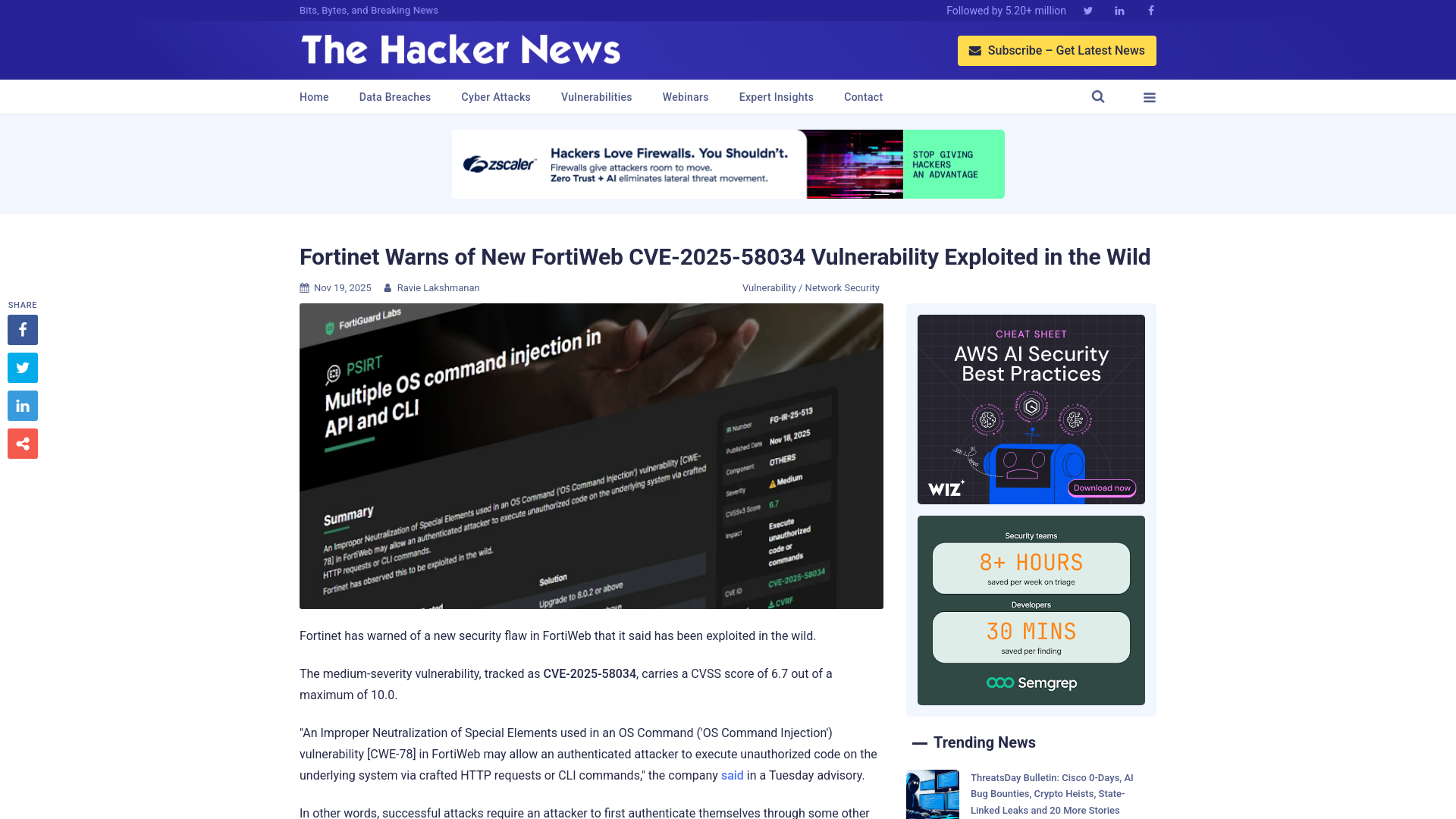
Microsoft is adding Sysmon into Windows. | The Verge
https://www.theverge.com/news/822023/microsoft-sysmon-windows-integration
GitHub - DarkCoderSc/OptixGate: Open-source multi-purpose remote access tool for Microsoft Windows
https://github.com/DarkCoderSc/OptixGate
WhatsApp Vulnerability Exposes 3.5 Billion Users' Phone Numbers
https://cybersecuritynews.com/whatsapp-vulnerability-exposes-3-5-billion-users/
Python-Based WhatsApp Worm Spreads Eternidade Stealer Across Brazilian Devices
https://thehackernews.com/2025/11/python-based-whatsapp-worm-spreads.html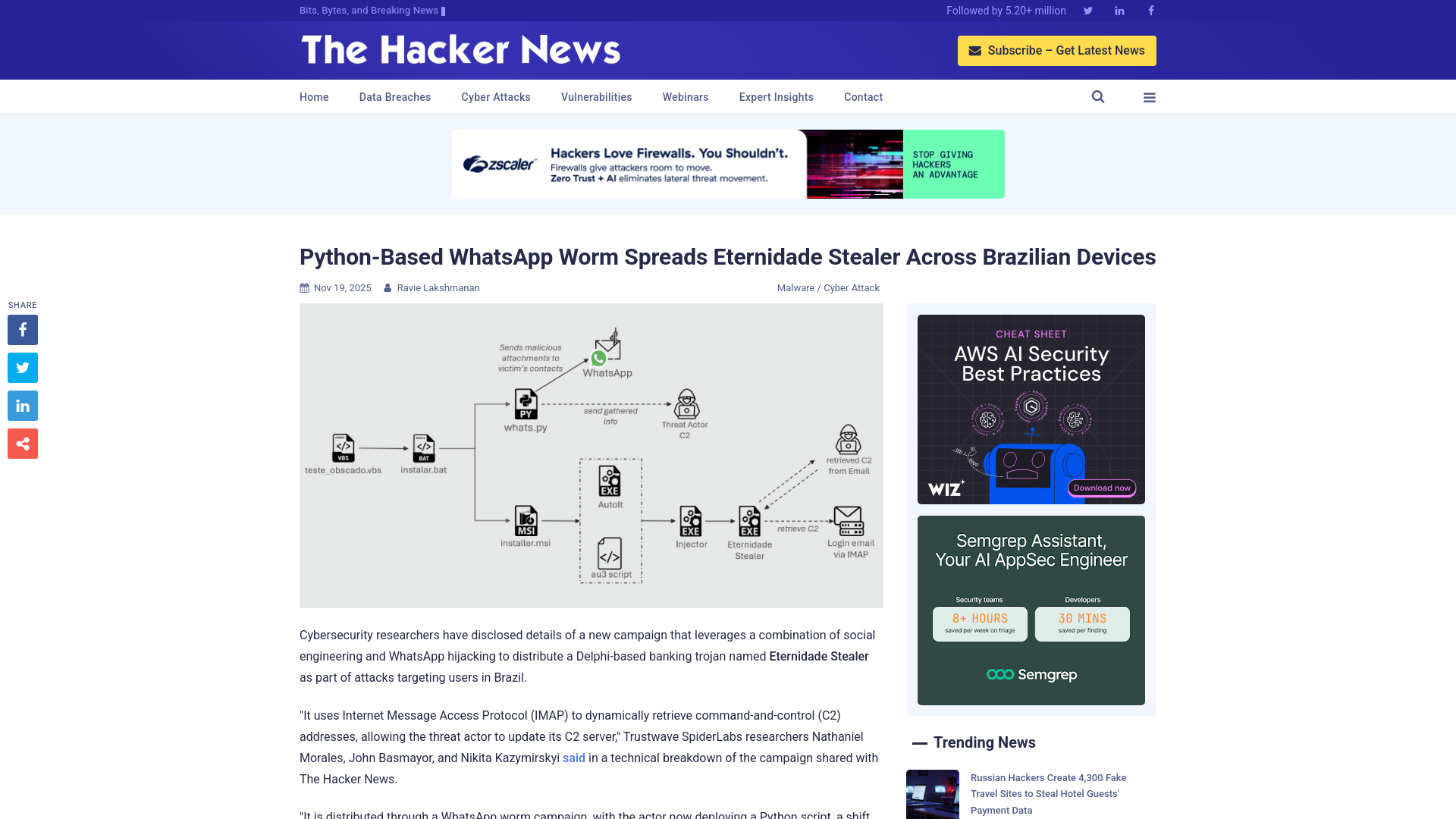
‘PlushDaemon’ hackers hijack software updates in supply-chain attacks
https://www.bleepingcomputer.com/news/security/plushdaemon-hackers-hijack-software-updates-in-supply-chain-attacks/
Cloudflare blames this week's massive outage on database issues
https://www.bleepingcomputer.com/news/technology/cloudflare-blames-this-weeks-massive-outage-on-database-issues/
Digital Forensics: Repairing a Damaged Hard Drive and Extracting the Data – Hackers Arise
https://hackers-arise.com/digital-forensics-repairing-a-damaged-hard-drive-and-extracting-the-data/
California man admits to laundering crypto stolen in $230M heist
https://www.bleepingcomputer.com/news/security/california-man-admits-to-laundering-crypto-stolen-in-230m-heist/
MacOS Infection Vector: Using AppleScripts to bypass Gatekeeper
https://pberba.github.io/security/2025/11/11/macos-infection-vector-applescript-bypass-gatekeeper/
