Dutch police seizes 250 servers used by “bulletproof hosting” service
https://www.bleepingcomputer.com/news/security/dutch-police-seizes-250-servers-used-by-bulletproof-hosting-service/
Indeterminism
https://www.computer.org/csdl/magazine/sp/2025/05/11204774/2aPD9aCBSyQ
Microsoft: Windows bug blocks Microsoft 365 desktop app installs
https://www.bleepingcomputer.com/news/microsoft/microsoft-windows-bug-blocks-microsoft-365-desktop-app-installs/
Jaguar Land Rover hack cost around $2.4 billion and counting • The Register
http://dlvr.it/TPJHty
Dragon Breath Uses RONINGLOADER to Disable Security Tools and Deploy Gh0st RAT
https://thehackernews.com/2025/11/dragon-breath-uses-roningloader-to.html
Binary Ninja - Binary Ninja 5.2 (Io)
https://binary.ninja/2025/11/13/binary-ninja-5.2-io.html
New EVALUSION ClickFix Campaign Delivers Amatera Stealer and NetSupport RAT
https://thehackernews.com/2025/11/new-evalusion-clickfix-campaign.html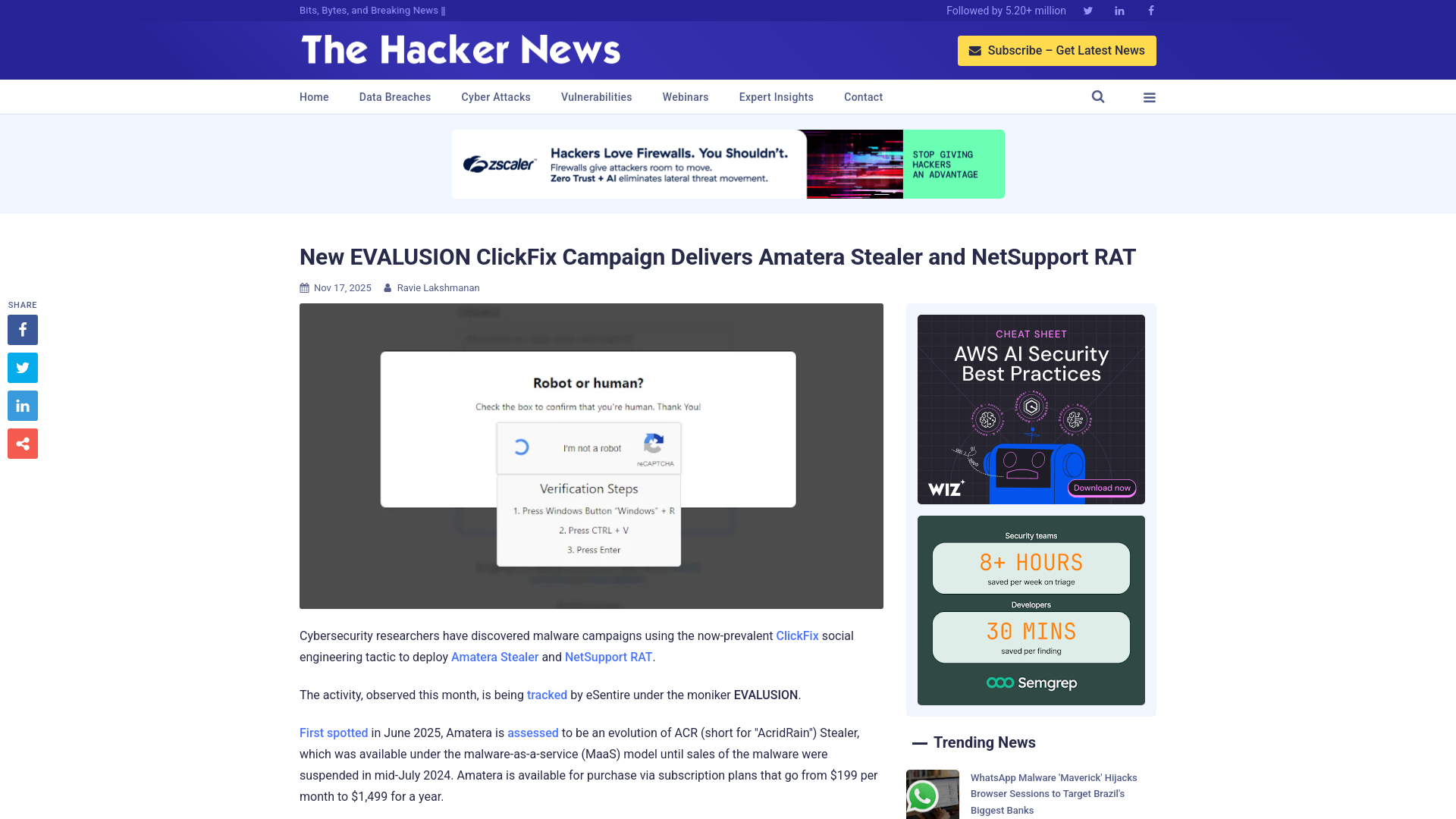
Unremovable Spyware on Samsung Devices Comes Pre-installed on Galaxy Series Devices
https://cybersecuritynews.com/spyware-on-samsung-devices/
ITOA: Image to ASCII Converter
https://itoa.hex.dance/
Microsoft: Azure hit by 15 Tbps DDoS attack using 500,000 IP addresses
https://www.bleepingcomputer.com/news/microsoft/microsoft-aisuru-botnet-used-500-000-ips-in-15-tbps-azure-ddos-attack/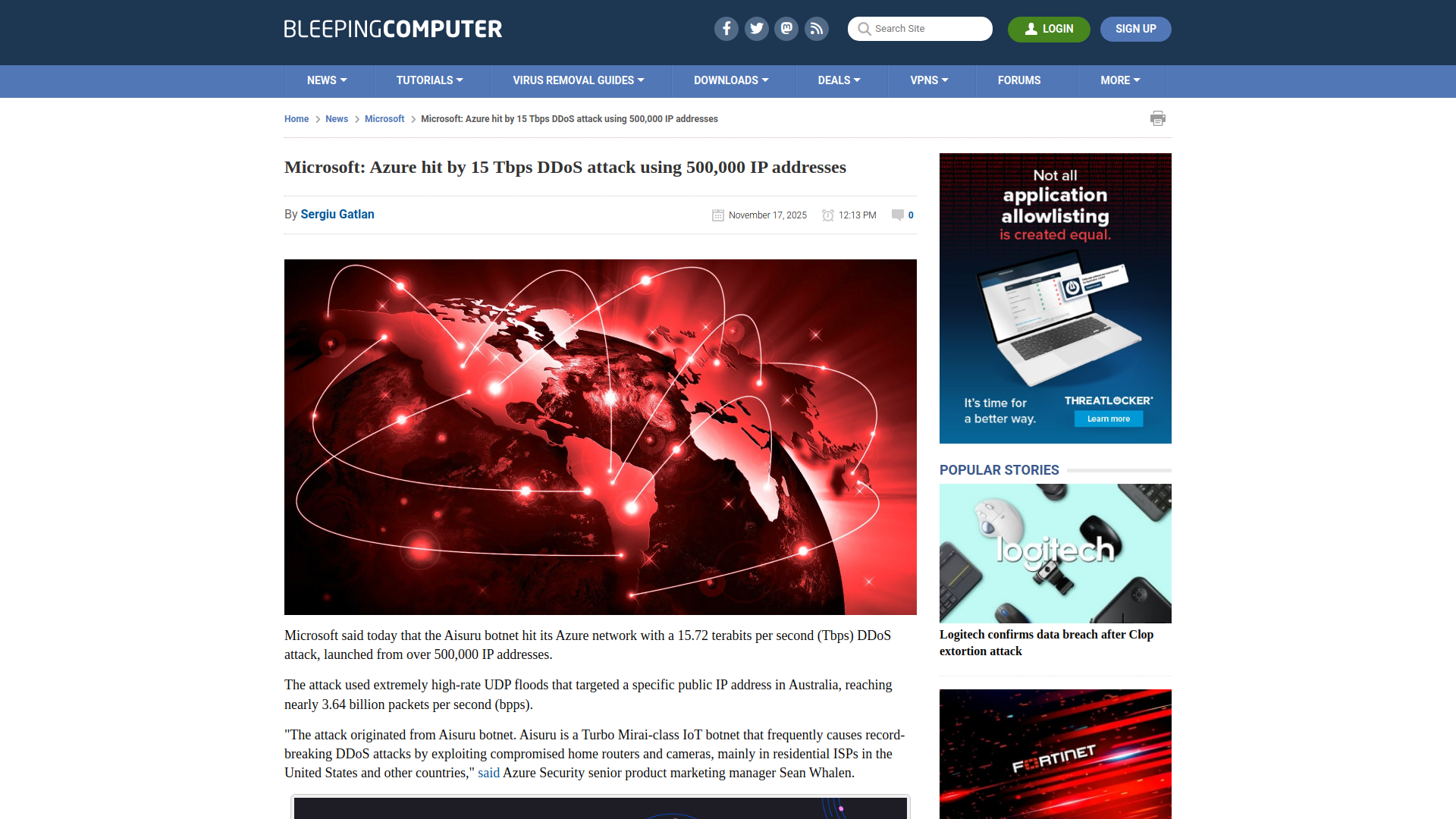
AI pentest scoping playbook | devansh
https://devansh.bearblog.dev/ai-pentest-scoping/
Pennsylvania AG confirms data breach after INC Ransom attack
https://www.bleepingcomputer.com/news/security/pennsylvania-ag-confirms-data-breach-after-inc-ransom-attack/
Exploit Development: Building Your Own Fuzzer with BASH - Hackers Arise
https://hackers-arise.com/post/exploit-development-building-your-own-fuzzer-with-bash