Another BRICKSTORM: Stealthy Backdoor Enabling Espionage into Tech and Legal Sectors | Google Cloud Blog
https://cloud.google.com/blog/topics/threat-intelligence/brickstorm-espionage-campaign
State-Sponsored Hackers Exploiting Libraesva Email Security Gateway Vulnerability
https://thehackernews.com/2025/09/state-sponsored-hackers-exploiting.html
Bypassing EDR using an In-Memory PE Loader - G3tSyst3m’s Infosec Blog
https://g3tsyst3m.com/fileless%20techniques/Bypassing-EDR-using-an-In-Memory-PE-Loader/
PyPI urges users to reset credentials after new phishing attacks
https://www.bleepingcomputer.com/news/security/pypi-urges-users-to-reset-credentials-after-new-phishing-attacks/
UK arrests suspect for RTX ransomware attack causing airport disruptions
https://www.bleepingcomputer.com/news/security/uk-arrests-suspect-for-rtx-ransomware-attack-causing-airport-disruptions/
Kali Linux 2025.3 Release (Vagrant & Nexmon) | Kali Linux Blog
https://www.kali.org/blog/kali-linux-2025-3-release/
A Look at PolarEdge Adjacent Infrastructure
https://censys.com/blog/a-look-at-polaredge-adjacent-infrastructure
How One Bad Password Ended a 158-Year-Old Business
https://thehackernews.com/2025/09/how-one-bad-password-ended-158-year-old.html
GitHub notifications abused to impersonate Y Combinator for crypto theft
https://www.bleepingcomputer.com/news/security/github-notifications-abused-to-impersonate-y-combinator-for-crypto-theft/
Chinese Hackers RedNovember Target Global Governments Using Pantegana and Cobalt Strike
https://thehackernews.com/2025/09/chinese-hackers-rednovember-target.html
Hackers Exploit Pandoc CVE-2025-51591 to Target AWS IMDS and Steal EC2 IAM Credentials
https://thehackernews.com/2025/09/hackers-exploit-pandoc-cve-2025-51591.html
GitHub - ScorpionesLabs/DVS: D(COM) V(ulnerability) S(canner) AKA Devious swiss army knife - Lateral movement using DCOM Objects
https://github.com/ScorpionesLabs/DVS
Police seizes $439 million stolen by cybercrime rings worldwide
https://www.bleepingcomputer.com/news/security/police-seizes-439-million-stolen-by-cybercrime-rings-worldwide/
GitHub | Report #3124517 - Arbitrary Read of Another Users private repository without Authorization | HackerOne
https://hackerone.com/reports/3124517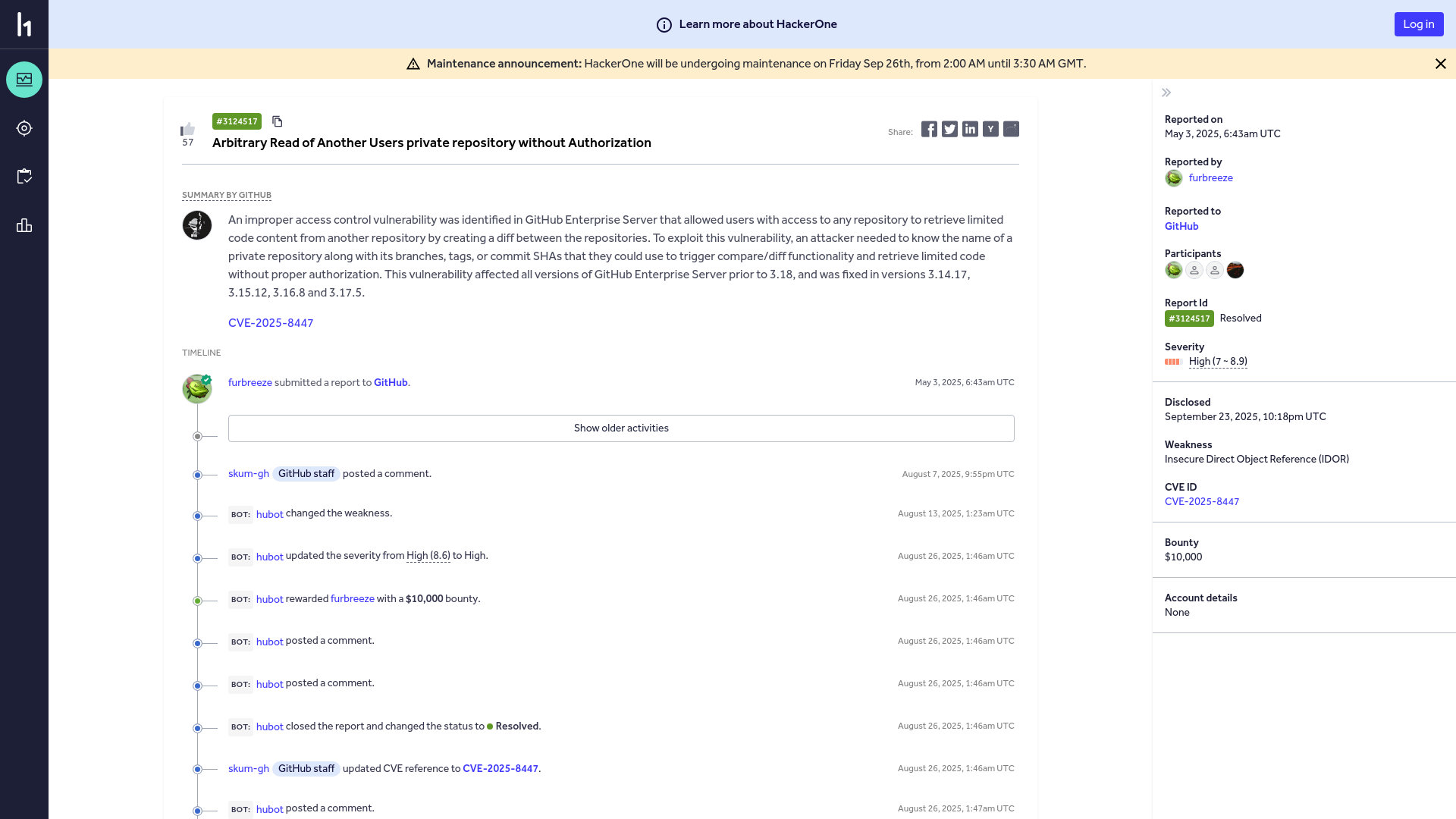
Google: Brickstorm malware used to steal U.S. orgs' data for over a year
https://www.bleepingcomputer.com/news/security/google-brickstone-malware-used-to-steal-us-orgs-data-for-over-a-year/
UNC5221 Uses BRICKSTORM Backdoor to Infiltrate U.S. Legal and Technology Sectors
https://thehackernews.com/2025/09/unc5221-uses-brickstorm-backdoor-to.html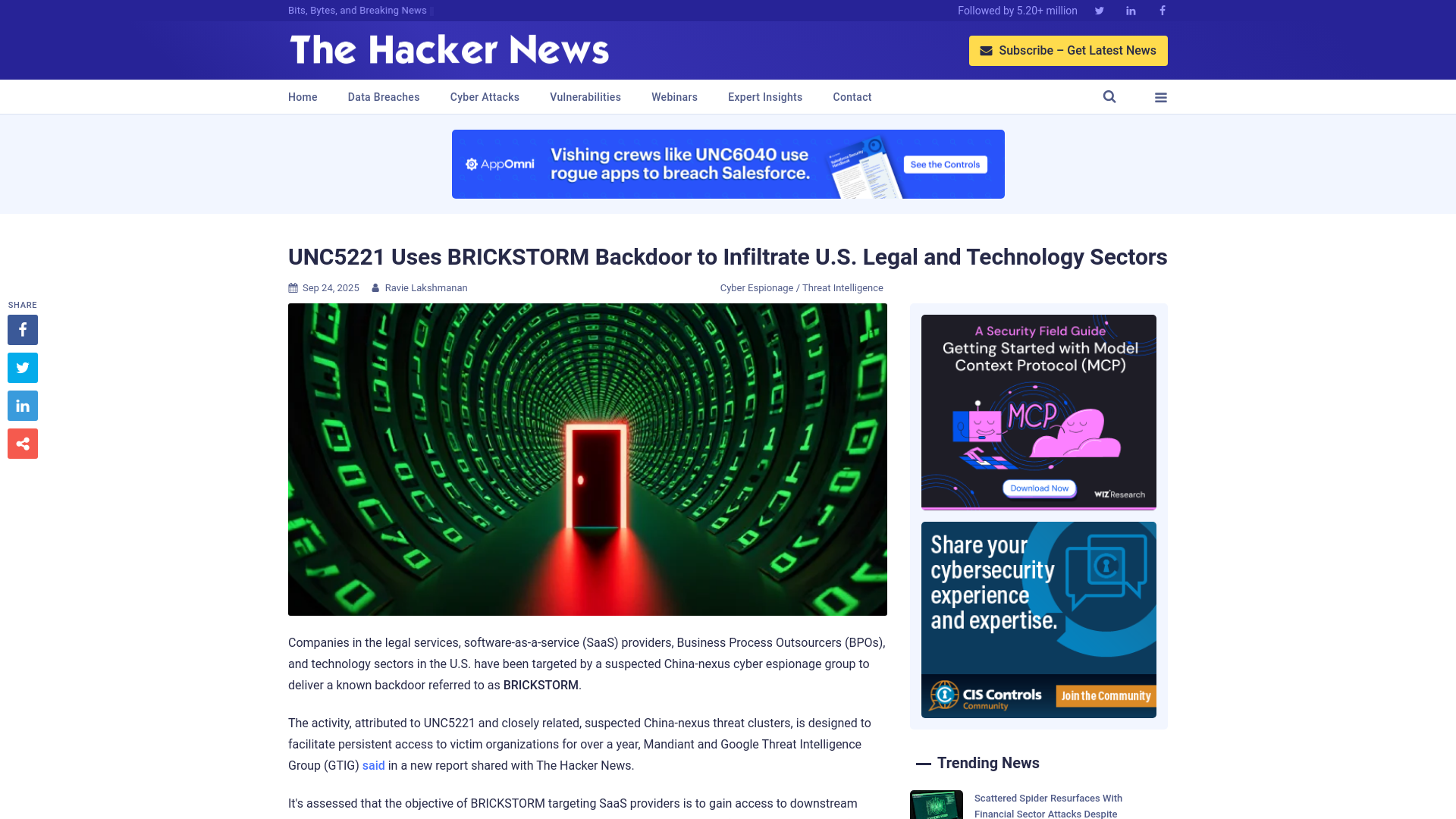
Obscura, an obscure new ransomware variant
https://www.bleepingcomputer.com/news/security/obscura-an-obscure-new-ransomware-variant/
Two Critical Flaws Uncovered in Wondershare RepairIt Exposing User Data and AI Models
https://thehackernews.com/2025/09/two-critical-flaws-uncovered-in.html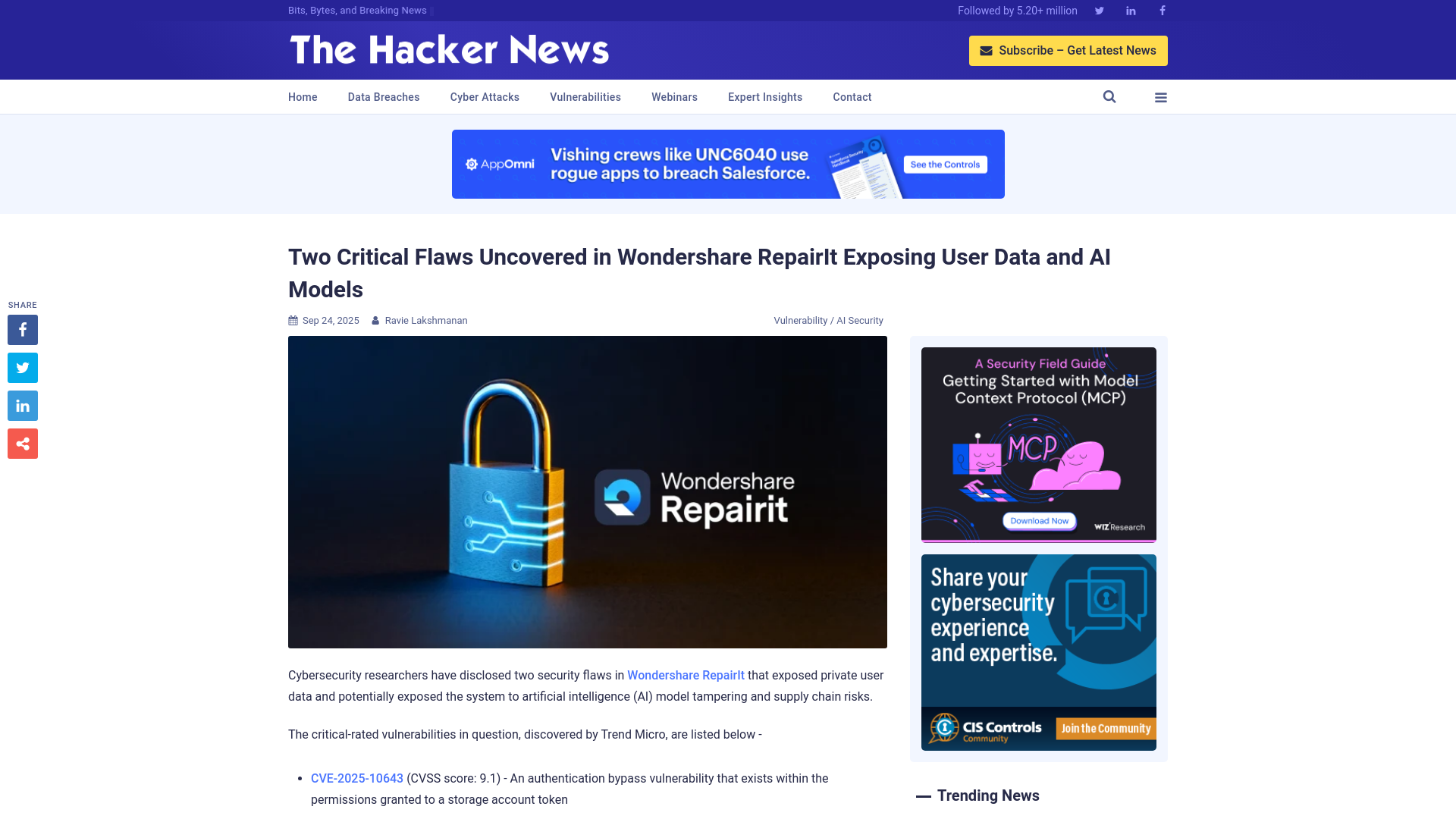
Cisco warns of IOS zero-day vulnerability exploited in attacks
https://www.bleepingcomputer.com/news/security/cisco-warns-of-ios-zero-day-vulnerability-exploited-in-attacks/