OffensiveCon25 - YouTube
https://youtube.com/playlist?list=PLYvhPWR_XYJk0p40BrX7K2z-_j_tJmvhc&si=O2qDBmsP_nweIBl_
Finding and Exploiting 20-year-old bugs in Web Browsers - Google スライド
https://docs.google.com/presentation/d/1pAosPlKUw4uI5lfg7FVheTZAtI5mUy8iDeE4znprV34/edit?usp=sharing
OffensiveCon25 - Dino Dai Zovi - Keynote - How Offensive Security Made Me Better at Defense - YouTube
https://youtu.be/60BcjiChncE
OffensiveCon25 - Joernchen - Parser Differentials: When Interpretation Becomes a Vulnerability - YouTube
https://www.youtube.com/watch?v=Dq_KVLXzxH8
Bypassing kASLR via Cache Timing | r0keb
https://r0keb.github.io/posts/Bypassing-kASLR-via-Cache-Timing/
kASLR Internals and Evolution | r0keb
https://r0keb.github.io/posts/kASLR-Internals-and-Evolution/
EntrySign @ OffensiveCon - Google スライド
http://entrysign.top
The Windows Subsystem for Linux is now open source - Windows Developer Blog
https://blogs.windows.com/windowsdeveloper/2025/05/19/the-windows-subsystem-for-linux-is-now-open-source/
Hazy Hawk Exploits DNS Records to Hijack CDC, Corporate Domains for Malware Delivery
https://thehackernews.com/2025/05/hazy-hawk-exploits-dns-records-to.html
Introduction to Windows shellcode development – Part 1 – Security Café
https://securitycafe.ro/2015/10/30/introduction-to-windows-shellcode-development-part1/
Introduction to Windows shellcode development – Part 2 – Security Café
https://securitycafe.ro/2015/12/14/introduction-to-windows-shellcode-development-part-2/
SSD Advisory - Multiple Foscam X5 Vulnerabilities - SSD Secure Disclosure
https://ssd-disclosure.com/ssd-advisory-multiple-foscam-x5-vulnerabilities/
RVTools hit in supply chain attack to deliver Bumblebee malware
https://www.bleepingcomputer.com/news/security/rvtools-hit-in-supply-chain-attack-to-deliver-bumblebee-malware/
Announcing the Official Parity Release of Volatility 3! - The Volatility Foundation - Promoting Accessible Memory Analysis Tools Within the Memory Forensics Community
https://volatilityfoundation.org/announcing-the-official-parity-release-of-volatility-3/
curl | Report #3148937 - `Curl_socketpair()` fallback vulnerable to man-in-the-middle attack | HackerOne
https://hackerone.com/reports/3148937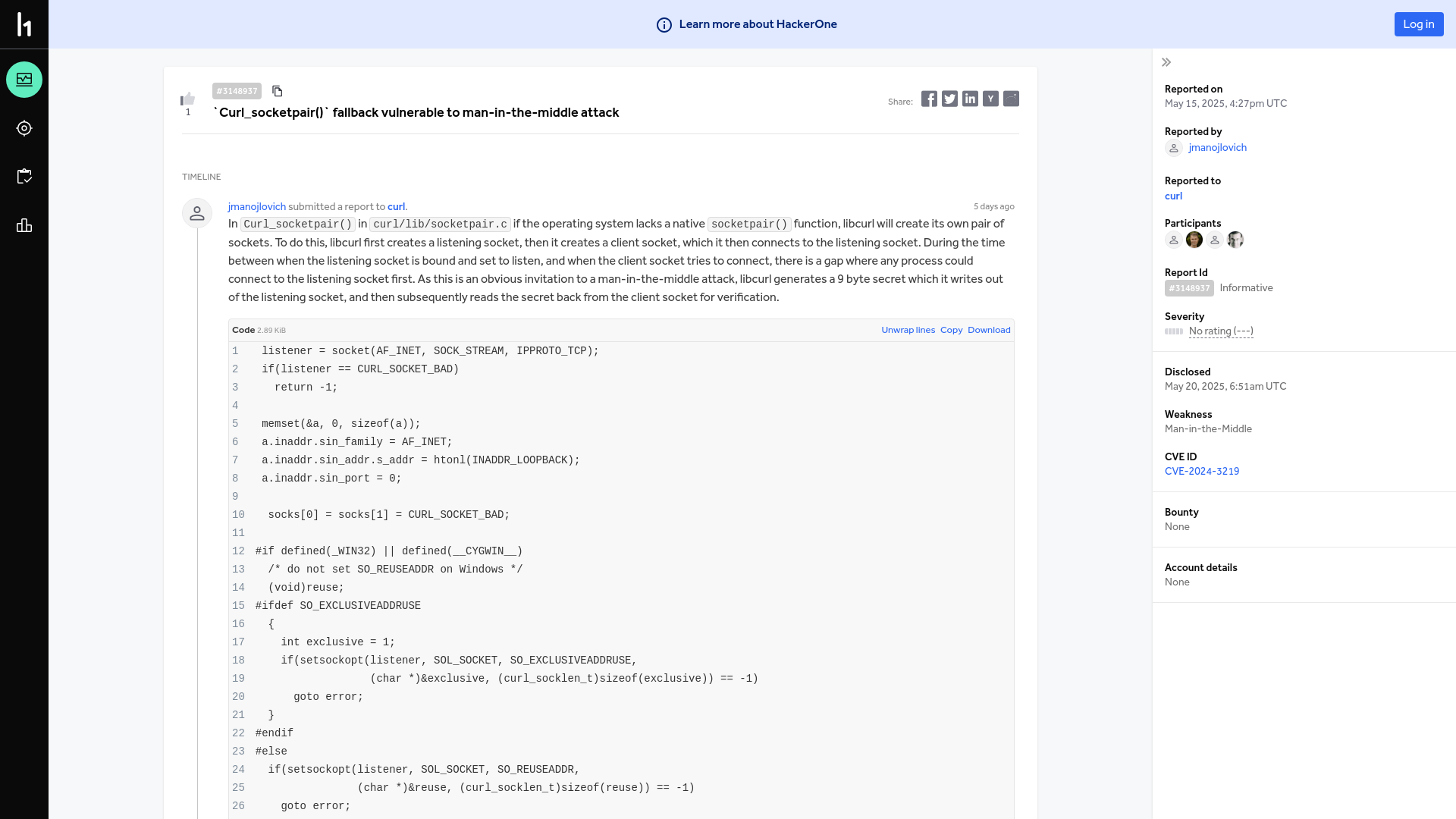
Malicious PyPI Packages Exploit Instagram and TikTok APIs to Validate User Accounts
https://thehackernews.com/2025/05/malicious-pypi-packages-exploit.html
Go-Based Malware Deploys XMRig Miner on Linux Hosts via Redis Configuration Abuse
https://thehackernews.com/2025/05/go-based-malware-deploys-xmrig-miner-on.html
Japan passed a law allowing preemptive offensive cyber actions
https://securityaffairs.com/178056/laws-and-regulations/japan-passed-a-law-allowing-preemptive-offensive-cyber-actions.html
Volatility 3 — Volatility 3 2.8.0 documentation
https://volatility3.readthedocs.io/en/stable/
Enhance your application security with administrator protection - Windows Developer Blog
https://blogs.windows.com/windowsdeveloper/2025/05/19/enhance-your-application-security-with-administrator-protection/
BRICKSTORM Backdoor Analysis: A Persistent Espionage Threat To International Industries / X
https://x.com/i/broadcasts/1MYxNwXqWoLKw
VanHelsing ransomware builder leaked on hacking forum
https://www.bleepingcomputer.com/news/security/vanhelsing-ransomware-builder-leaked-on-hacking-forum/
SK Telecom says malware breach lasted 3 years, impacted 27 million numbers
https://www.bleepingcomputer.com/news/security/sk-telecom-says-malware-breach-lasted-3-years-impacted-27-million-numbers/