Red Team Tactics: Combining Direct System Calls and sRDI to bypass AV/EDR | Outflank
https://www.outflank.nl/blog/2019/06/19/red-team-tactics-combining-direct-system-calls-and-srdi-to-bypass-av-edr/
Brave's Cookiecrumbler tool taps community to help block cookie notices
https://www.bleepingcomputer.com/news/security/braves-cookiecrumbler-tool-taps-community-to-help-block-cookie-notices/
Coinbase fixes 2FA log error making people think they were hacked
https://www.bleepingcomputer.com/news/security/coinbase-fixes-2fa-log-error-making-people-think-they-were-hacked/
RedExt — Offensive Chrome extension framework | by ShadowByte | Medium
https://medium.com/@darkrain2009/redext-browser-extension-based-command-control-framework-1eec1402f146
Introduction to Portable Executables (.exe Files) - Kronark - YouTube
https://www.youtube.com/watch?v=f1J07OCLwDk
Top Threat Hunting Examples: Real-World Tactics
https://hunt.io/glossary/threat-hunting-examples
WooCommerce admins targeted by fake security patches that hijack sites
https://www.bleepingcomputer.com/news/security/woocommerce-admins-targeted-by-fake-security-patches-that-hijack-sites/
Internet Bug Bounty | Report #3108869 - Denial of Service by memory exhaustion in net/imap | HackerOne
https://hackerone.com/reports/3108869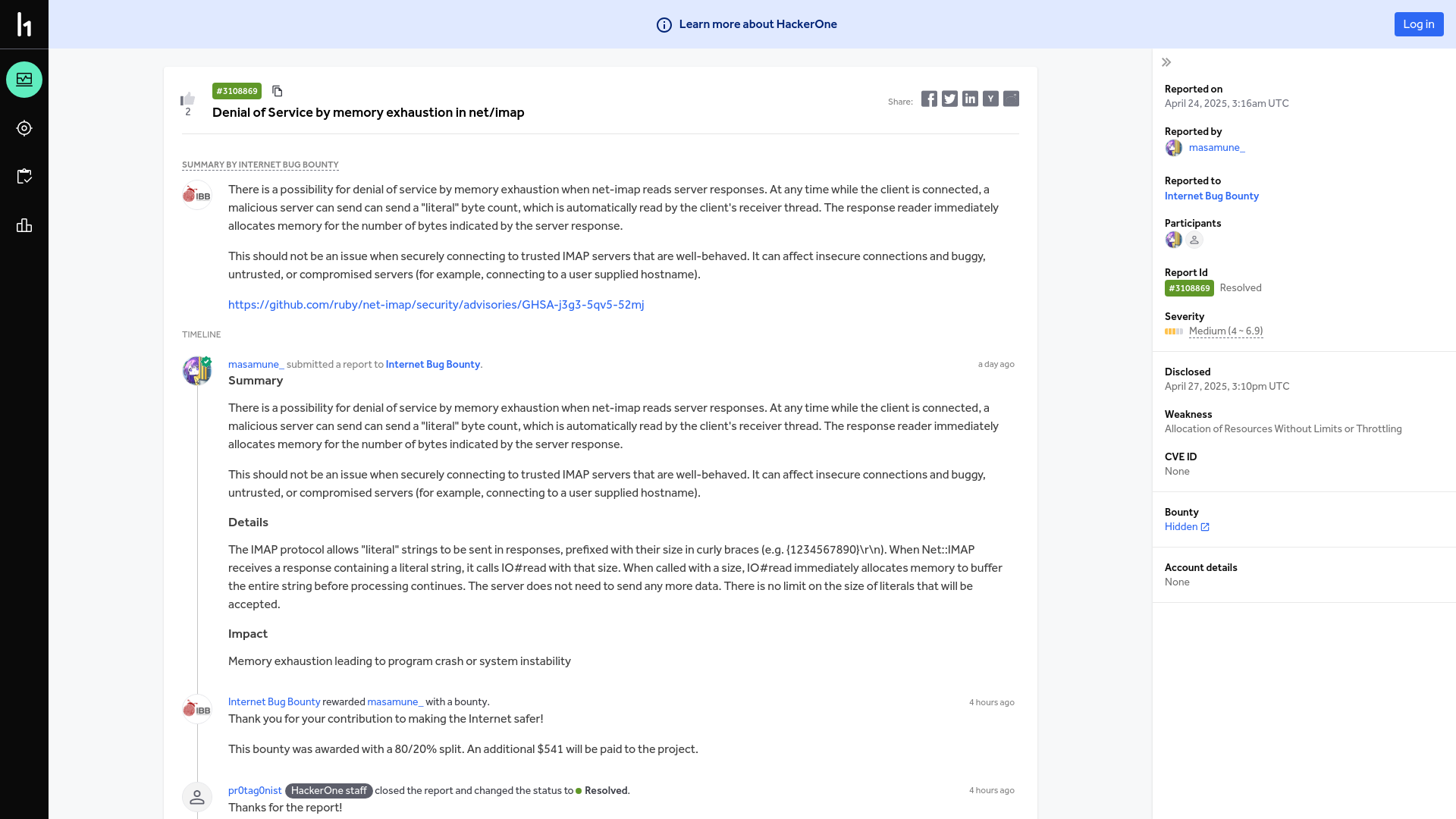
APT_REPORT/summary/2025/2025-dbir-data-breach-investigations-report.pdf at master · blackorbird/APT_REPORT · GitHub
https://github.com/blackorbird/APT_REPORT/blob/master/summary/2025/2025-dbir-data-breach-investigations-report.pdf
Introduction to Portable Executables (.exe Files) - Kronark - YouTube
https://youtube.com/watch?v=f1J07OCLwDk
Masking Malicious Memory Artifacts – Part III: Bypassing Defensive Scanners
https://www.forrest-orr.net/post/masking-malicious-memory-artifacts-part-iii-bypassing-defensive-scanners