SAMLStorm: Critical Authentication Bypass in xml-crypto and Node.js libraries — WorkOS
https://workos.com/blog/samlstorm
Critical RCE flaw in Apache Tomcat actively exploited in attacks
https://www.bleepingcomputer.com/news/security/critical-rce-flaw-in-apache-tomcat-actively-exploited-in-attacks/
MalwareBazaar | SHA256 7444d08579781b3d7b233e9fd3e7f9b31a85837c29adf2f4ae7965a628078639 (SnakeKeylogger)
https://bazaar.abuse.ch/sample/7444d08579781b3d7b233e9fd3e7f9b31a85837c29adf2f4ae7965a628078639/
Fake "Security Alert" issues on GitHub use OAuth app to hijack accounts
https://www.bleepingcomputer.com/news/security/fake-security-alert-issues-on-github-use-oauth-app-to-hijack-accounts/
Decrypting Encrypted files from Akira Ransomware (Linux/ESXI variant 2024) using a bunch of GPUs – Tinyhack.com
https://tinyhack.com/2025/03/13/decrypting-encrypted-files-from-akira-ransomware-linux-esxi-variant-2024-using-a-bunch-of-gpus/
Off the Beaten Path: Recent Unusual Malware
https://unit42.paloaltonetworks.com/unusual-malware/
LockBit Ransomware v4.0 | Chuong Dong
https://chuongdong.com/reverse%20engineering/2024/03/15/Lockbit4Ransomware/
GitHub Action Compromise Puts CI/CD Secrets at Risk in Over 23,000 Repositories
https://thehackernews.com/2025/03/github-action-compromise-puts-cicd.html
Malicious Adobe, DocuSign OAuth apps target Microsoft 365 accounts
https://www.bleepingcomputer.com/news/security/malicious-adobe-docusign-oauth-apps-target-microsoft-365-accounts/
Bypassing Authentication Like It’s The ‘90s - Pre-Auth RCE Chain(s) in Kentico Xperience CMS
https://labs.watchtowr.com/bypassing-authentication-like-its-the-90s-pre-auth-rce-chain-s-in-kentico-xperience-cms/
Microsoft: March Windows updates mistakenly uninstall Copilot
https://www.bleepingcomputer.com/news/microsoft/microsoft-march-windows-updates-mistakenly-uninstall-copilot/
Microsoft: New RAT malware used for crypto theft, reconnaissance
https://www.bleepingcomputer.com/news/security/microsoft-new-rat-malware-used-for-crypto-theft-reconnaissance/
GitHub - s0md3v/XSStrike: Most advanced XSS scanner.
https://github.com/s0md3v/XSStrike
Supply chain attack on popular GitHub Action exposes CI/CD secrets
https://www.bleepingcomputer.com/news/security/supply-chain-attack-on-popular-github-action-exposes-ci-cd-secrets/
フィッシング対策協議会 Council of Anti-Phishing Japan | 報告書類 | 月次報告書 | 2025/02 フィッシング報告状況
https://www.antiphishing.jp/report/monthly/202502.html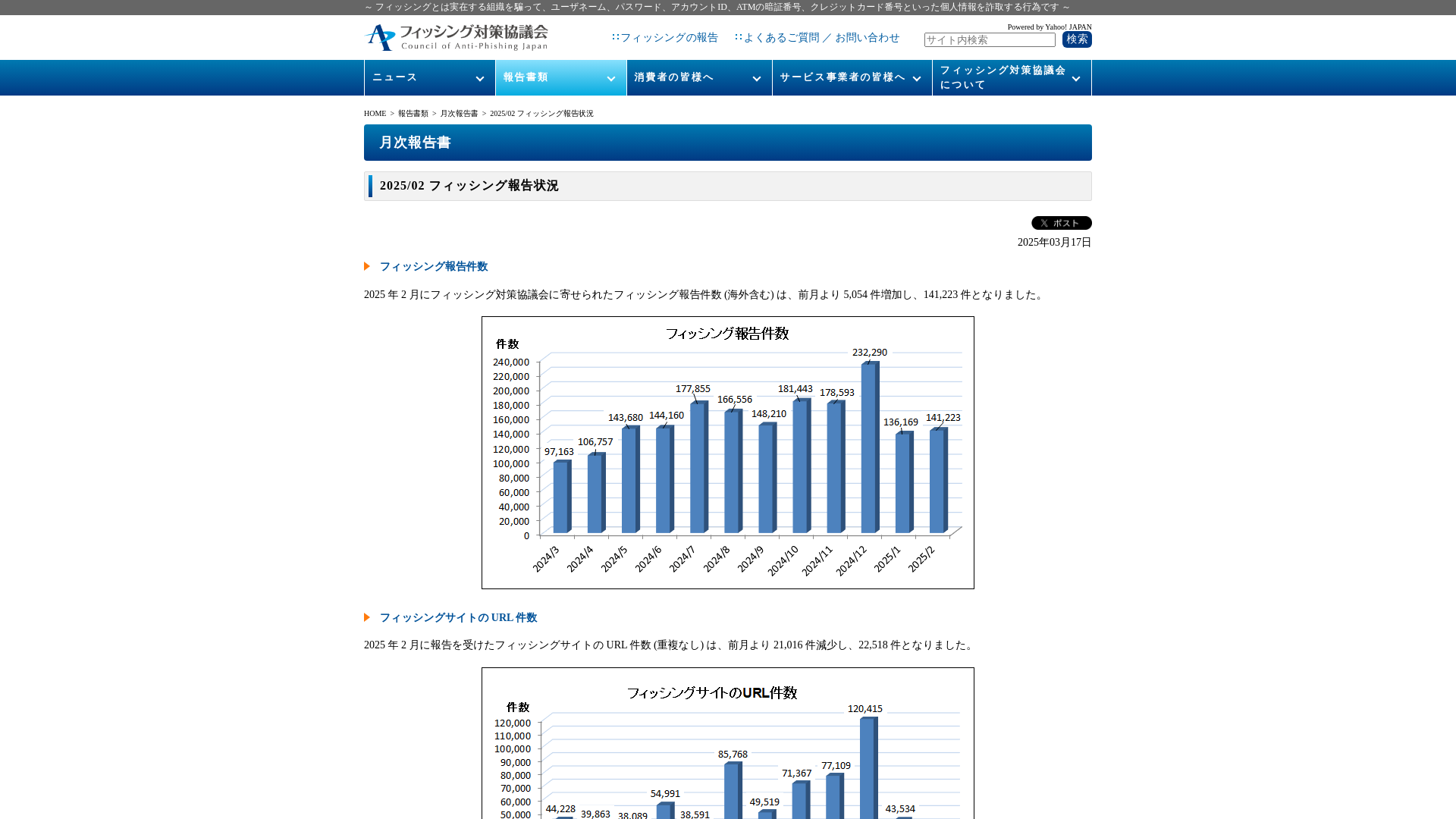
Cross-site Scripting - YouTube
http://youtube.com/watch?v=vZoRn_j5jBM
Cybercriminals Exploit CSS to Evade Spam Filters and Track Email Users' Actions
https://thehackernews.com/2025/03/cybercriminals-exploit-css-to-evade.html
Apache Tomcat Vulnerability Actively Exploited Just 30 Hours After Public Disclosure
https://thehackernews.com/2025/03/apache-tomcat-vulnerability-comes-under.html
This is How a Simple IDOR Earned Me a Max Bug Bounty Payout - YouTube
https://youtu.be/Cw-hlmW89kA
NIST Announces HQC as Fifth Standardized Post Quantum Algorithm - SecurityWeek
https://www.securityweek.com/nist-announces-hqc-as-fifth-standardized-post-quantum-algorithm/
100 Car Dealerships Hit by Supply Chain Attack - SecurityWeek
https://www.securityweek.com/100-car-dealerships-hit-by-supply-chain-attack/
Nvidia Patches Vulnerabilities That Could Let Hackers Exploit AI Services - SecurityWeek
https://www.securityweek.com/nvidia-riva-vulnerabilities-allow-unauthorized-use-of-ai-services/
Denmark warns of increased state-sponsored campaigns targeting the European telcos
https://securityaffairs.com/175479/intelligence/denmark-warns-of-increased-state-sponsored-campaigns-targeting-the-european-telcos.html
Researcher trolls Microsoft over bug disclosure annoyance • The Register
https://go.theregister.com/feed/www.theregister.com/2025/03/17/microsoft_bug_report_troll/
OKX suspends DEX aggregator after Lazarus hackers try to launder funds
https://www.bleepingcomputer.com/news/security/okx-suspends-dex-aggregator-after-lazarus-hackers-try-to-launder-funds/
CVE-2025-24016: Unsafe Deserialization Vulnerability in Wazuh Leading to Remote Code Execution
https://cvereports.com/cve-2025-24016-unsafe-deserialization-vulnerability-in-wazuh-leading-to-remote-code-execution/