In-Depth Technical Analysis of the Bybit Hack | NCC Group
https://www.nccgroup.com/us/research-blog/in-depth-technical-analysis-of-the-bybit-hack/
Critical PHP RCE vulnerability mass exploited in new attacks
https://www.bleepingcomputer.com/news/security/critical-php-rce-vulnerability-mass-exploited-in-new-attacks/
North Korean Lazarus hackers infect hundreds via npm packages
https://www.bleepingcomputer.com/news/security/north-korean-lazarus-hackers-infect-hundreds-via-npm-packages/
CISA tags critical Ivanti EPM flaws as actively exploited in attacks
https://www.bleepingcomputer.com/news/security/cisa-tags-critical-ivanti-epm-flaws-as-actively-exploited-in-attacks/
Popular JavaScript Library 'Axios' Exposes Millions to Server-Side Vulnerabilities (CVE-2025-27152)
https://securityonline.info/popular-javascript-library-axios-exposes-millions-to-server-side-vulnerabilities-cve-2025-27152/
how2itsec: Windows Persistence Map v0.1
https://how2itsec.blogspot.com/2025/03/windows-persistence-map-v01.html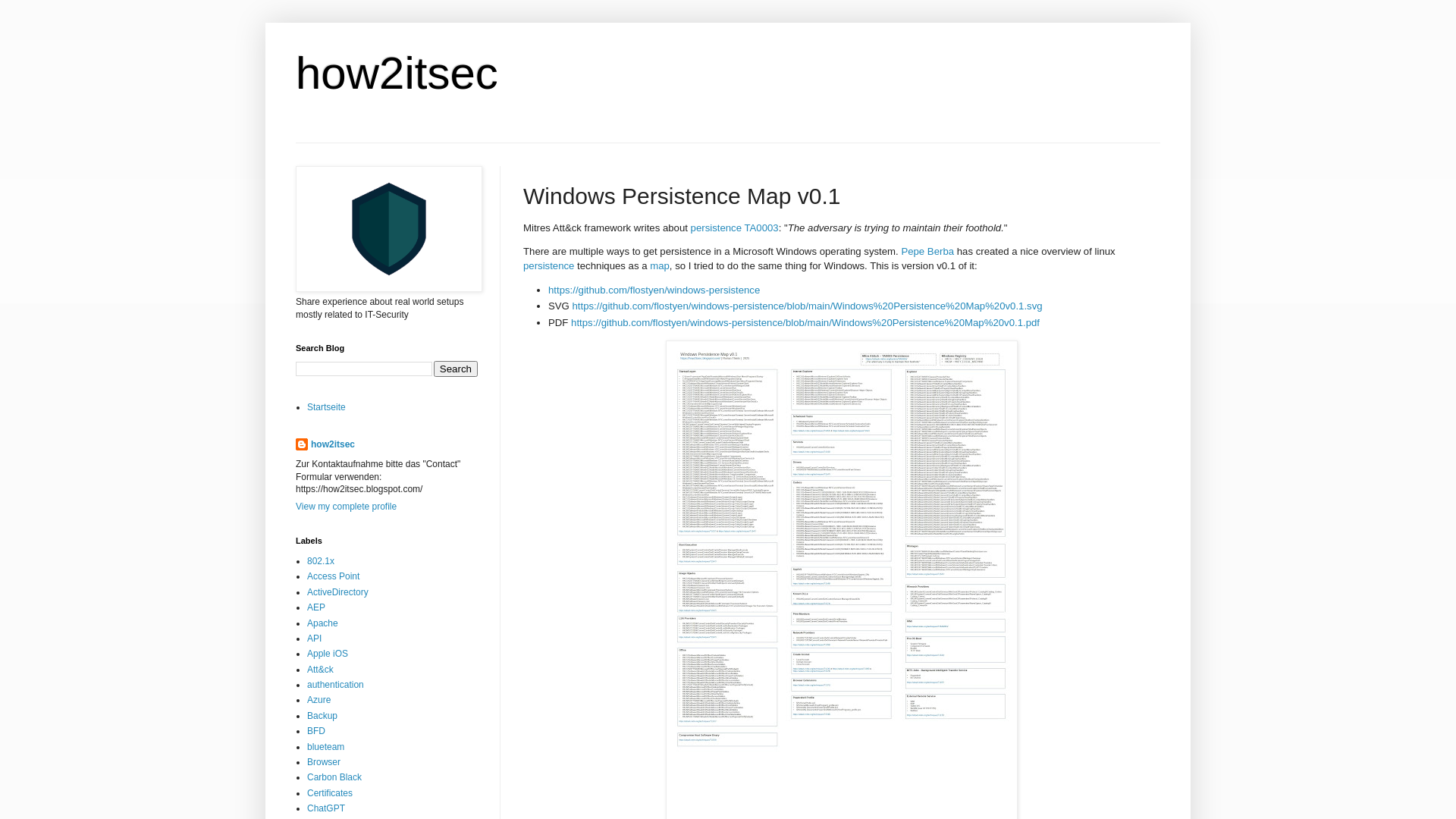
Microsoft replacing Remote Desktop app with Windows App in May
https://www.bleepingcomputer.com/news/microsoft/microsoft-replacing-remote-desktop-app-with-windows-app-in-may/
AI Assisted Fake GitHub Repositories Fuel SmartLoader and LummaStealer Distribution | Trend Micro (US)
https://www.trendmicro.com/en_us/research/25/c/ai-assisted-fake-github-repositories.html
Blind Eagle Hacks Colombian Institutions Using NTLM Flaw, RATs and GitHub-Based Attacks
https://thehackernews.com/2025/03/blind-eagle-hacks-colombian.html
1,600 Victims Hit by South American APT's Malware - SecurityWeek
https://www.securityweek.com/1600-victims-hit-by-south-american-apts-malware/
Lazarus 그룹의 윈도우 웹 서버 대상 공격 사례 분석 - ASEC
https://asec.ahnlab.com/ko/86631/
MassJacker malware uses 778,000 wallets to steal cryptocurrency
https://www.bleepingcomputer.com/news/security/massjacker-malware-uses-778-000-wallets-to-steal-cryptocurrency/
Moxa Issues Fix for Critical Authentication Bypass Vulnerability in PT Switches
https://thehackernews.com/2025/03/moxa-issues-fix-for-critical.html
RogueSliver: disrupt campaigns using the Sliver C2 framework
https://meterpreter.org/roguesliver-disrupt-campaigns-using-the-sliver-c2-framework/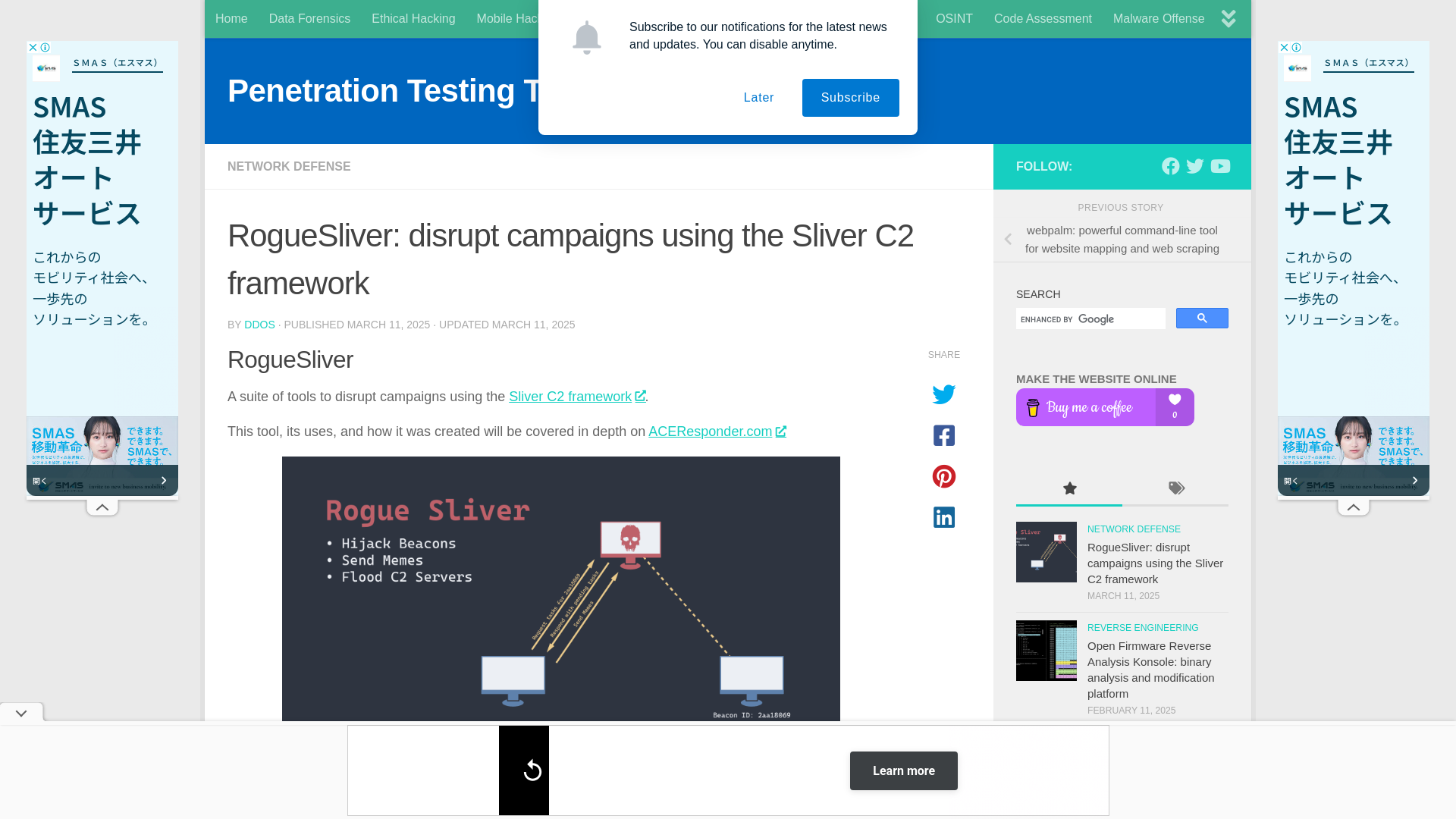
BSidesCharm 2022 Schedule – BSidesCharm
https://bsidescharm.org/schedule/
MalwareBazaar | 20-241-85-64
https://bazaar.abuse.ch/browse/tag/20-241-85-64/
Edimax Says No Patches Coming for Zero-Day Exploited by Botnets - SecurityWeek
https://www.securityweek.com/edimax-says-no-patches-coming-for-zero-day-exploited-by-botnets/
Steganography Explained: How XWorm Hides Inside Images
https://thehackernews.com/2025/03/steganography-explained-how-xworm-hides.html
SAP Patches High-Severity Vulnerabilities in Commerce, NetWeaver - SecurityWeek
https://www.securityweek.com/sap-patches-high-severity-vulnerabilities-in-commerce-netweaver/
From Deployment to Compromise: Understanding Credential Storage in Microsoft Deployment Toolkit | Jason Mull
https://jasonmull.com/articles/offensive/2025-01-11-understanding-credential-storage-mdt/
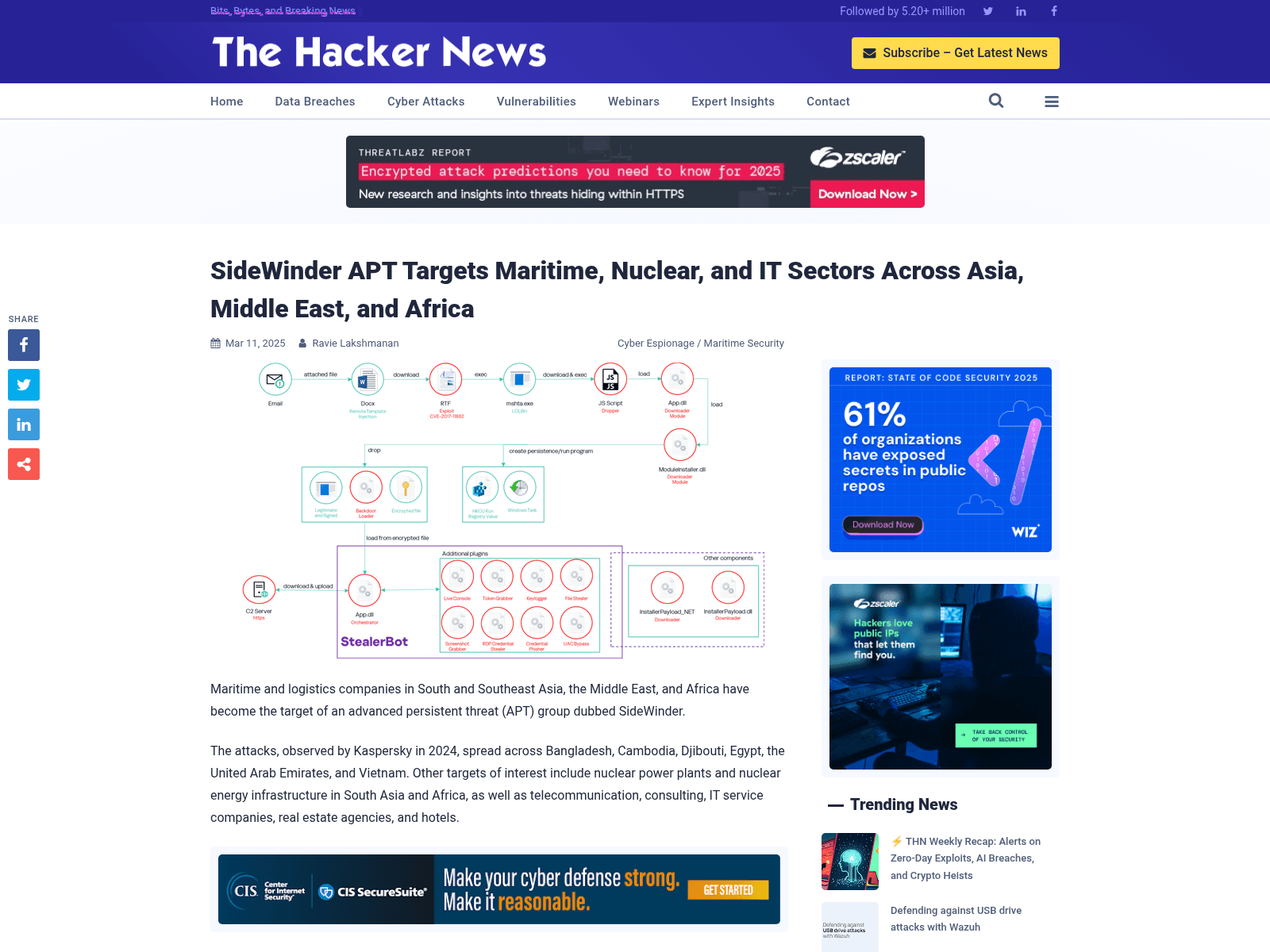
SideWinder APT Targets Maritime, Nuclear, and IT Sectors Across Asia, Middle East, and Africa
https://thehackernews.com/2025/03/sidewinder-apt-targets-maritime-nuclear.html