Apple fixes zero-day exploited in 'extremely sophisticated' attacks
https://www.bleepingcomputer.com/news/apple/apple-fixes-zero-day-exploited-in-extremely-sophisticated-attacks/
Brave now lets you inject custom JavaScript to tweak websites
https://www.bleepingcomputer.com/news/software/brave-now-lets-you-inject-custom-javascript-to-tweak-websites/
Police arrests 4 Phobos ransomware suspects, seizes 8Base sites
https://www.bleepingcomputer.com/news/legal/police-arrests-4-phobos-ransomware-suspects-seizes-8base-sites/
XE Hacker Group Exploits VeraCore Zero-Day to Deploy Persistent Web Shells
https://thehackernews.com/2025/02/xe-hacker-group-exploits-veracore-zero.html
GitHub - s0md3v/wappalyzer-next: wappalyzer alternative based on wappalyzer browser extension
https://github.com/s0md3v/wappalyzer-next
Reverse Engineering: I Found a Game Exploit That Lets Hackers Take Over Your PC
https://shalzuth.com/Blog/IFoundAGameExploit
Reminder: 7-Zip & MoW - SANS Internet Storm Center
https://isc.sans.edu/diary/31668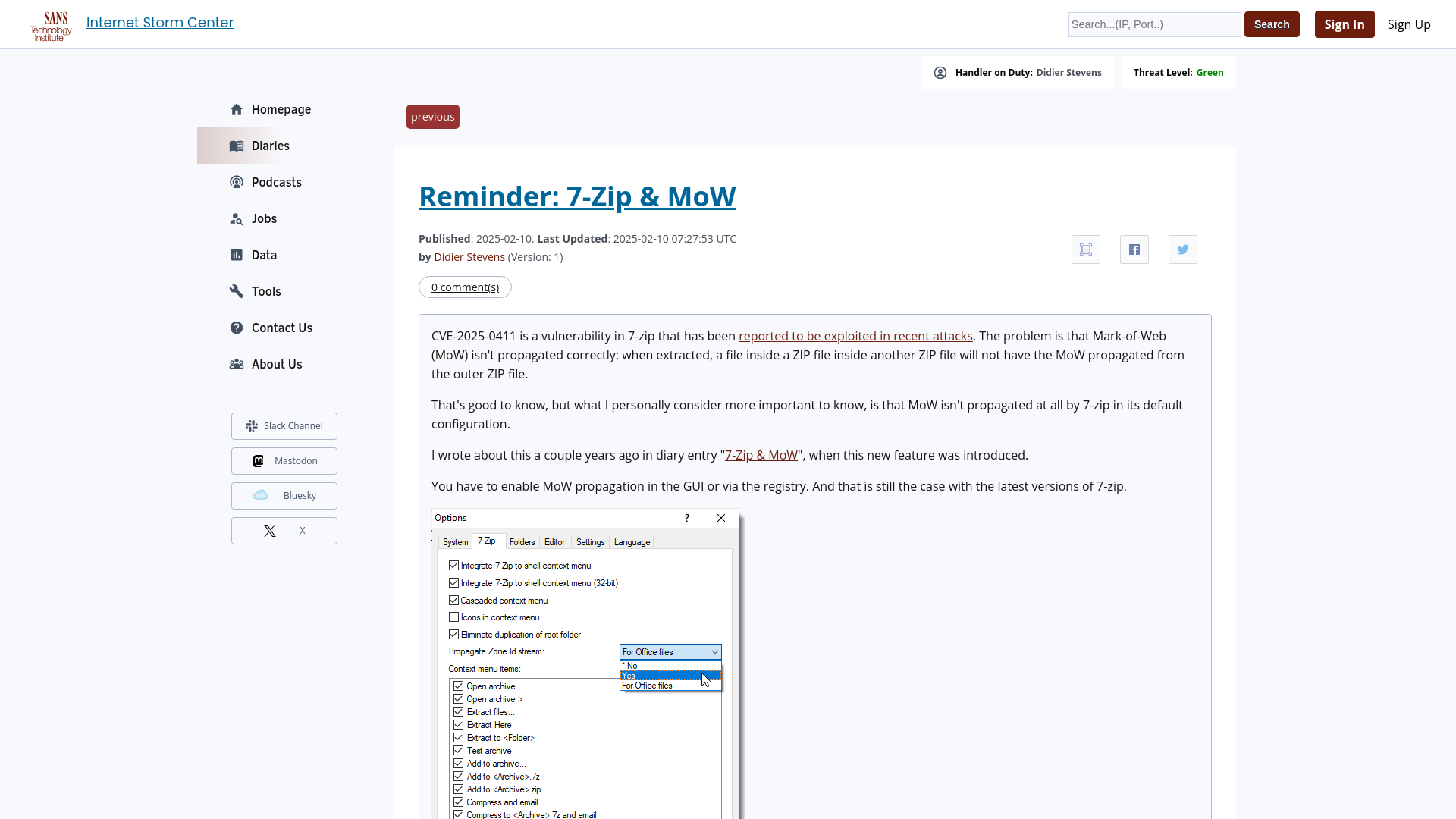
n0rdy - What Okta Bcrypt incident can teach us about designing better APIs
https://n0rdy.foo/posts/20250121/okta-bcrypt-lessons-for-better-apis/
Malicious ML models discovered on Hugging Face platform
https://www.reversinglabs.com/blog/rl-identifies-malware-ml-model-hosted-on-hugging-face
DragonRank Exploits IIS Servers with BadIIS Malware for SEO Fraud and Gambling Redirects
https://thehackernews.com/2025/02/dragonrank-exploits-iis-servers-with.html
Accidentally uncovering a seven years old vulnerability in the Linux kernel
https://allelesecurity.com/accidentally-uncovering-a-seven-years-old-vulnerability-in-the-linux-kernel/
form-action Content-Security-Policy Bypass And Other Tactics For Dealing With The CSP – Project NZT-48
https://nzt-48.org/form-action-content-security-policy-bypass-and-other-tactics-for-dealing-with-the-csp
cpcontacts.queticollc.comcpanel.gaskks88amp.progaskks88amp.proafrizalzona. - Pastebin.com
https://pastebin.com/cBuGRXuN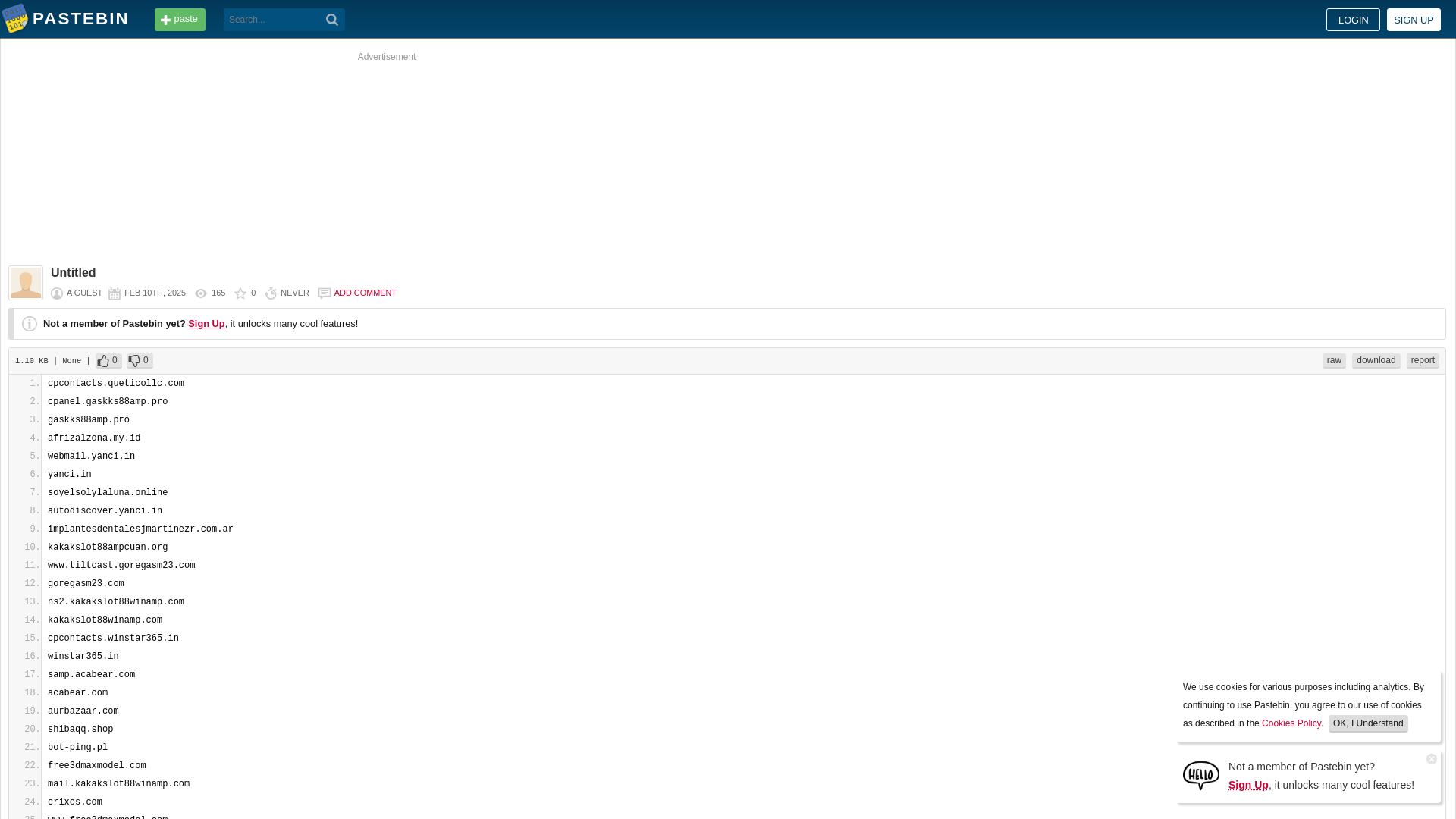
Cyberattack disrupts Lee newspapers' operations across the US
https://www.bleepingcomputer.com/news/security/cyberattack-disrupts-lee-newspapers-operations-across-the-us/
Clone2Leak: Your Git Credentials Belong To Us - GMO Flatt Security Research
https://flatt.tech/research/posts/clone2leak-your-git-credentials-belong-to-us/
CVE-2024-49138 Windows CLFS heap-based buffer overflow analysis - Part 1 - hn security
https://security.humanativaspa.it/cve-2024-49138-windows-clfs-heap-based-buffer-overflow-analysis-part-1/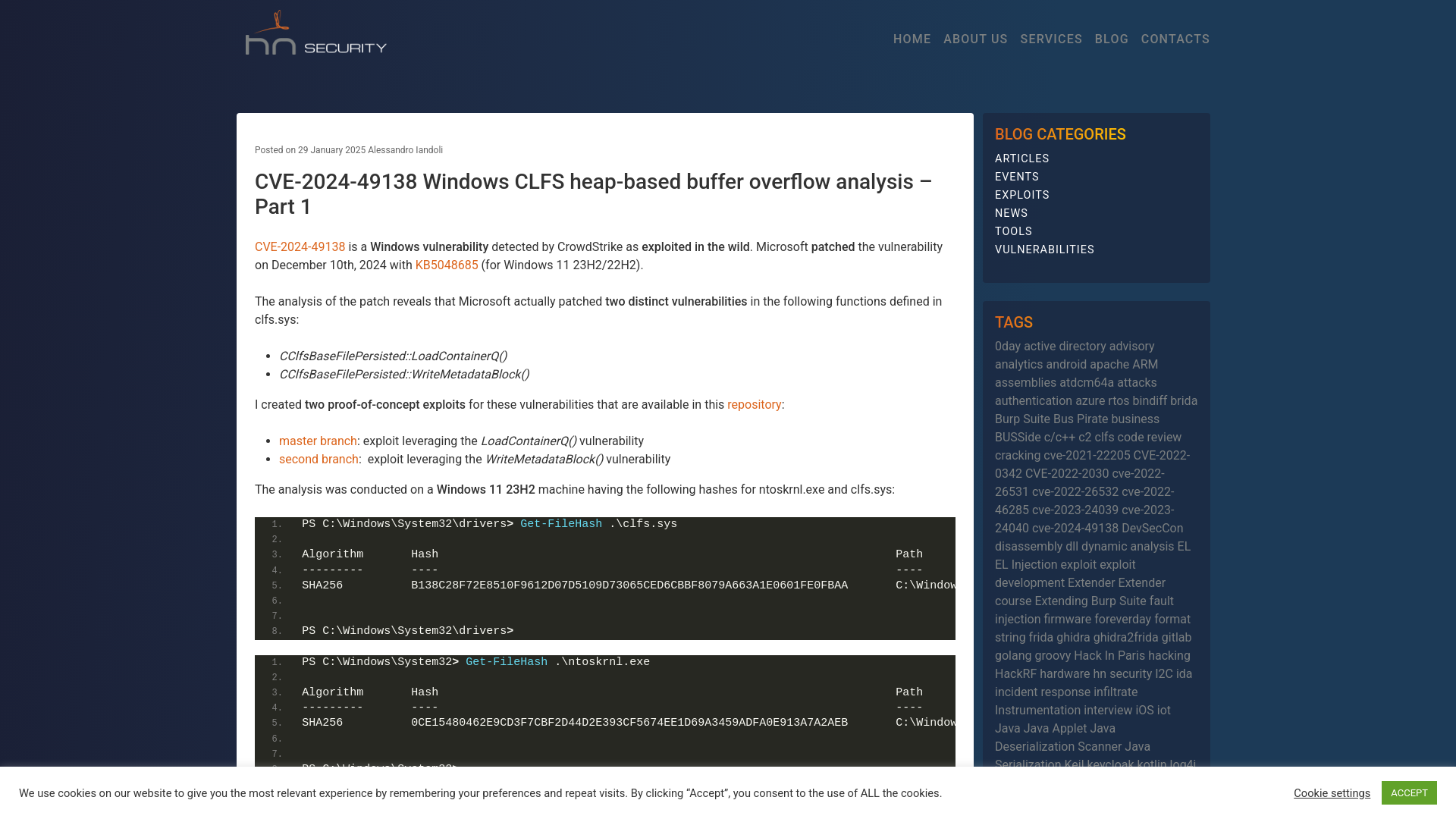
Indiana Man Sentenced to 20 Years in Prison for Hacking, $37 Million Crypto Theft - SecurityWeek
https://www.securityweek.com/indiana-man-sentenced-to-20-years-in-prison-for-hacking-37-million-crypto-theft/
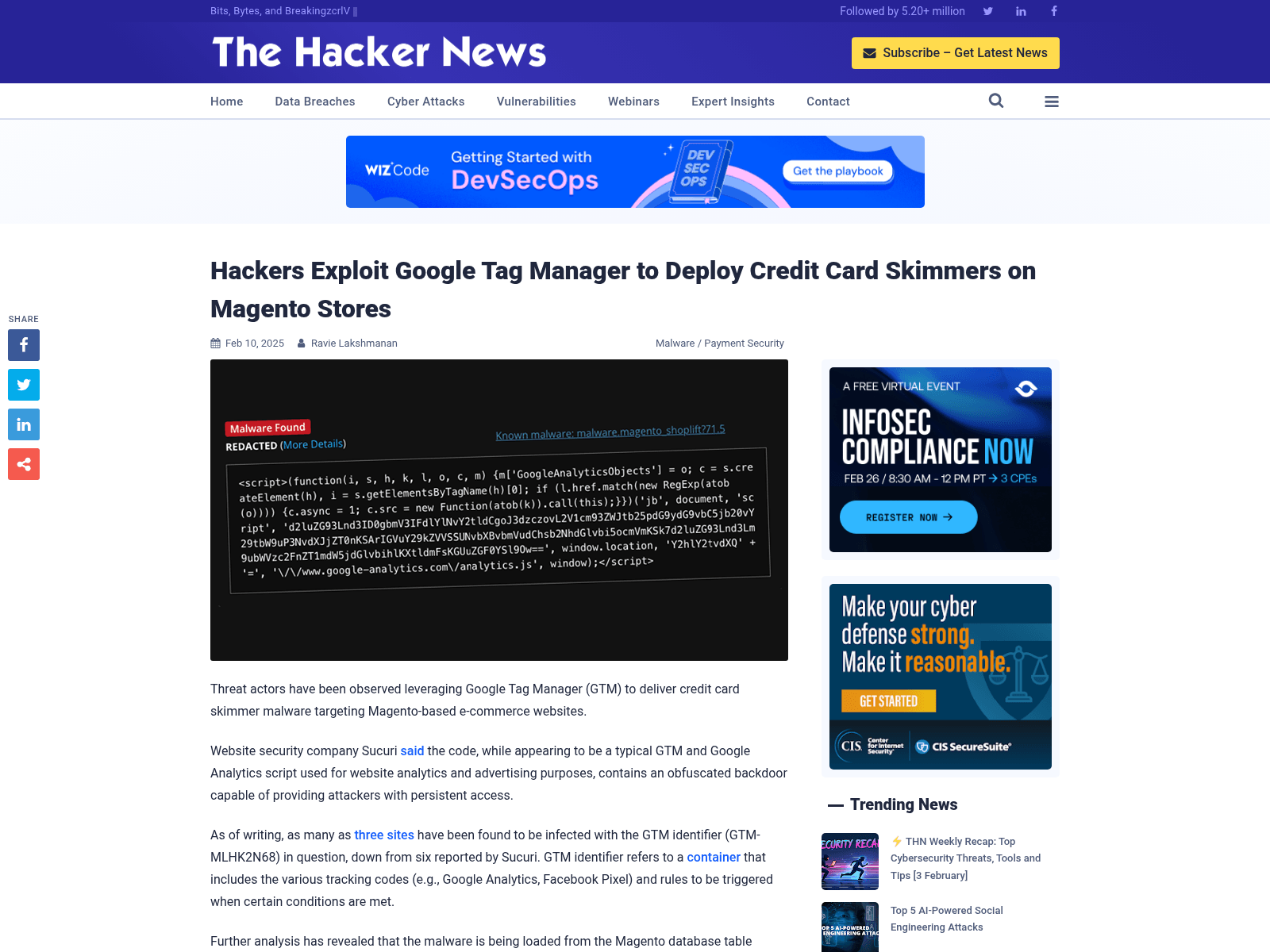
Hackers Exploit Google Tag Manager to Deploy Credit Card Skimmers on Magento Stores
https://thehackernews.com/2025/02/hackers-exploit-google-tag-manager-to.html