Exploitation Walkthrough and Techniques - Ivanti Connect Secure RCE (CVE-2025-0282)
https://labs.watchtowr.com/exploitation-walkthrough-and-techniques-ivanti-connect-secure-rce-cve-2025-0282/
Exploring malicious Windows drivers (Part 1): Introduction to the kernel and drivers
https://blog.talosintelligence.com/exploring-malicious-windows-drivers-part-1-introduction-to-the-kernel-and-drivers/
Exploring malicious Windows drivers (Part 2): the I/O system, IRPs, stack locations, IOCTLs and more
https://blog.talosintelligence.com/exploring-malicious-windows-drivers-part-2/
GitHub - ColeHouston/Sunder: Windows rootkit designed to work with BYOVD exploits
https://github.com/ColeHouston/Sunder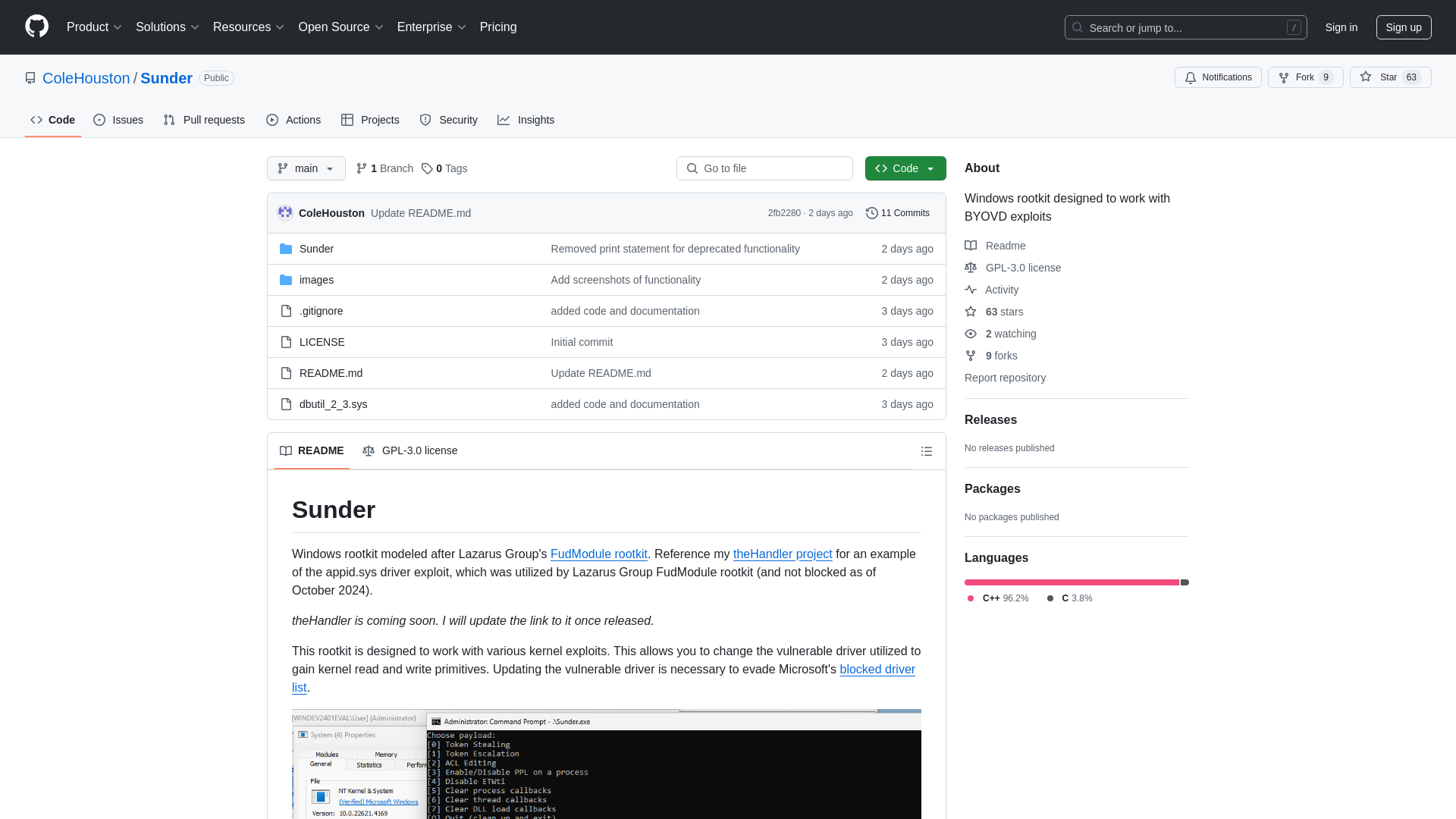
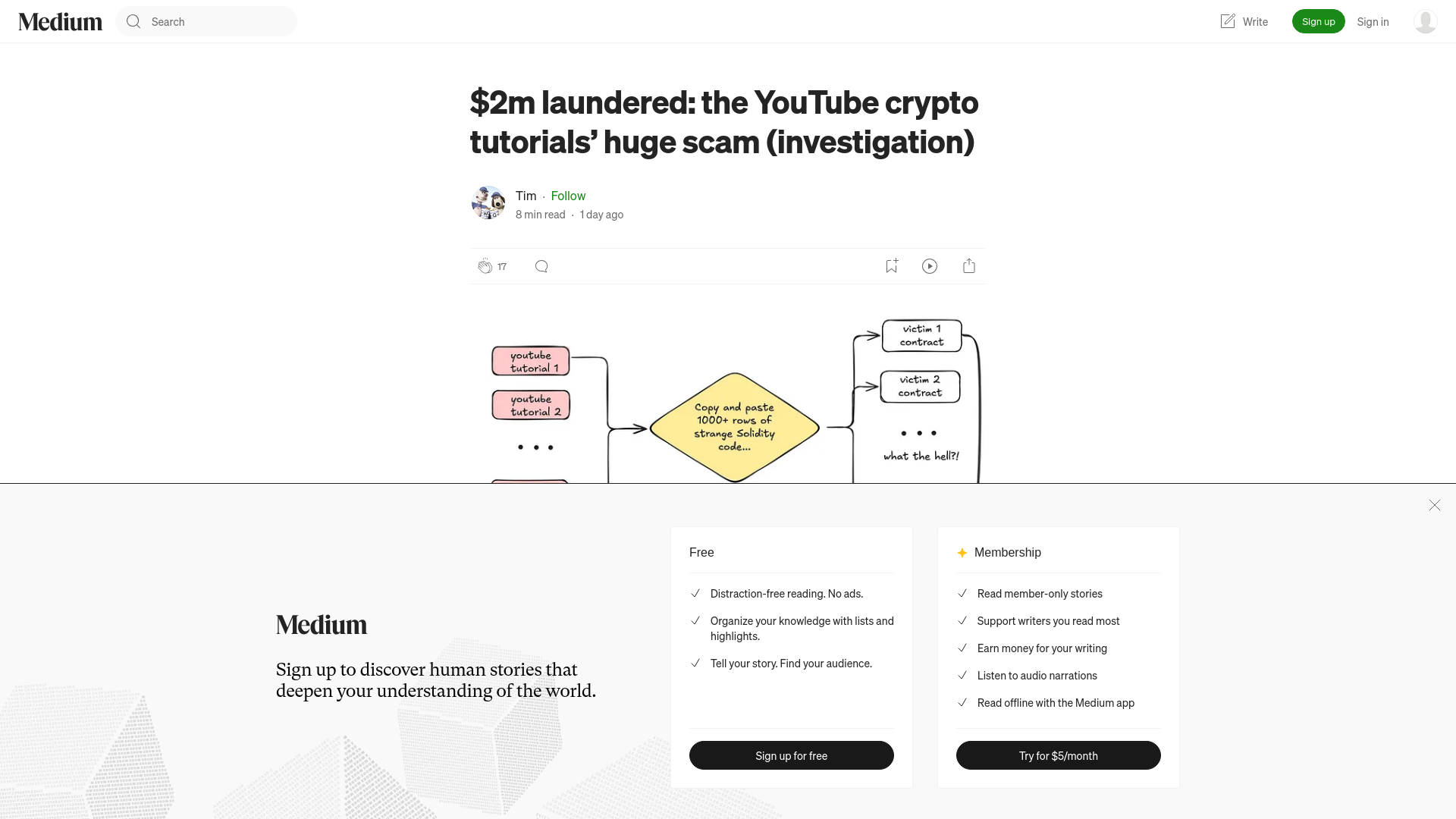
$2m laundered: the YouTube crypto tutorials’ huge scam (investigation) | by Tim | Jan, 2025 | Medium
https://medium.com/@tim.sh/2m-laundered-the-youtube-crypto-tutorials-huge-scam-investigation-8f4a0a3c92d8