CVE-2024-11477: 7-Zip Vulnerability Allows Remote Code Execution, Update Now!
https://securityonline.info/cve-2024-11477-7-zip-vulnerability-allows-remote-code-execution-update-now/
The Nearest Neighbor Attack: How A Russian APT Weaponized Nearby Wi-Fi Networks for Covert Access | Volexity
https://www.volexity.com/blog/2024/11/22/the-nearest-neighbor-attack-how-a-russian-apt-weaponized-nearby-wi-fi-networks-for-covert-access/
Ruby 3.4 Universal RCE Deserialization Gadget Chain / nastystereo.com
https://nastystereo.com/security/ruby-3.4-deserialization.html
Meta removes over 2 million accounts pushing pig butchering scams
https://www.bleepingcomputer.com/news/security/meta-removes-over-2-million-accounts-pushing-pig-butchering-scams/
https://api.bgpview.io/asn/AS12345
https://api.bgpview.io/asn/AS12345
DOJ: Man hacked networks to pitch cybersecurity services
https://www.bleepingcomputer.com/news/security/doj-man-hacked-networks-to-pitch-cybersecurity-services/
Salt Typhoon hackers backdoor telcos with new GhostSpider malware
https://www.bleepingcomputer.com/news/security/salt-typhoon-hackers-backdoor-telcos-with-new-ghostspider-malware/
China's telco attacks mean 'thousands' of boxes compromised • The Register
https://go.theregister.com/feed/www.theregister.com/2024/11/25/salt_typhoon_mark_warner_warning/
Home / nastystereo.com
http://nastystereo.com
Microsoft 365 outage impacts Exchange Online, Teams, Sharepoint
https://www.bleepingcomputer.com/news/microsoft/microsoft-365-outage-impacts-exchange-online-teams-sharepoint/
Microlise Confirms Data Breach as Ransomware Group Steps Forward - SecurityWeek
https://www.securityweek.com/microlise-confirms-data-breach-as-ransomware-group-steps-forward/
GitHub - Evi1Grey5/MacOS-S: MacOS S
https://github.com/Evi1Grey5/MacOS-S
しばらくお待ちください...
https://payhip.com/b/2qPZ1
Kaspersky advanced threat forecasts for 2025 | Securelist
https://securelist.com/ksb-apt-predictions-2025/114582/
Recent Zyxel Firewall Vulnerability Exploited in Ransomware Attacks - SecurityWeek
https://www.securityweek.com/recent-zyxel-firewall-vulnerability-exploited-in-ransomware-attacks/
Security Engineering - A Guide to Building Dependable Distributed Systems
https://www.cl.cam.ac.uk/archive/rja14/book.html
Microsoft Defender Weaknesses Found in Crypto Malware Analysis
https://www.safetydetectives.com/news/msdefender-malware-vulnerability/
Russia-linked threat actors threaten UK and its allies,minister to say
https://securityaffairs.com/171357/intelligence/russia-linked-threat-actors-threaten-uk.html
ATIP – Introducing AI-Powered Threat Reporting and Analysis
https://blog.unpac.me/2024/11/25/atip-introducing-ai-powered-threat-reporting-and-analysis/
Quick & Dirty Obfuscated JavaScript Analysis - SANS Internet Storm Center
https://isc.sans.edu/diary/31468
Google blocked 1000 pro China websites from services • The Register
https://go.theregister.com/feed/www.theregister.com/2024/11/25/google_beijing_propaganda/
PentesterLab Blog: How JWT Libraries Block Algorithm Confusion: Key Lessons for Code Review
https://pentesterlab.com/blog/jwt-algorithm-confusion-code-review-lessons
The Blueprint to Your First $1,000+ Bounty - YouTube
https://youtu.be/8DnphDtFt3Y
When Guardians Become Predators: How Malware Corrupts the Protectors
https://www.trellix.com/blogs/research/when-guardians-become-predators-how-malware-corrupts-the-protectors/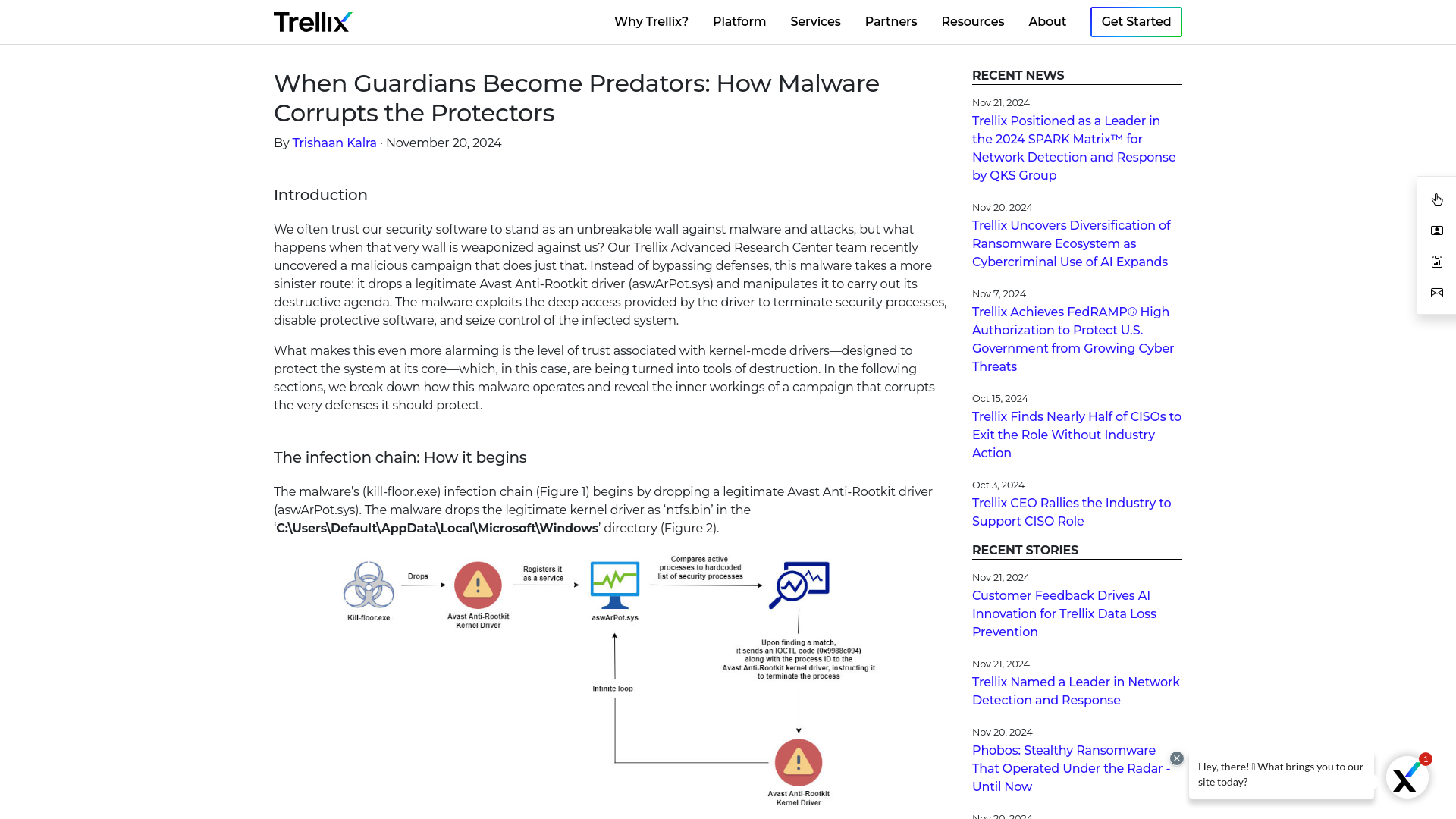
Windows - Data Protection API Revisited | Penetration Testing - Red Teaming - Purple Teaming - Security Training | Tier Zero Security, New Zealand
https://tierzerosecurity.co.nz/2024/11/26/data-protection-windows-api-revisited.html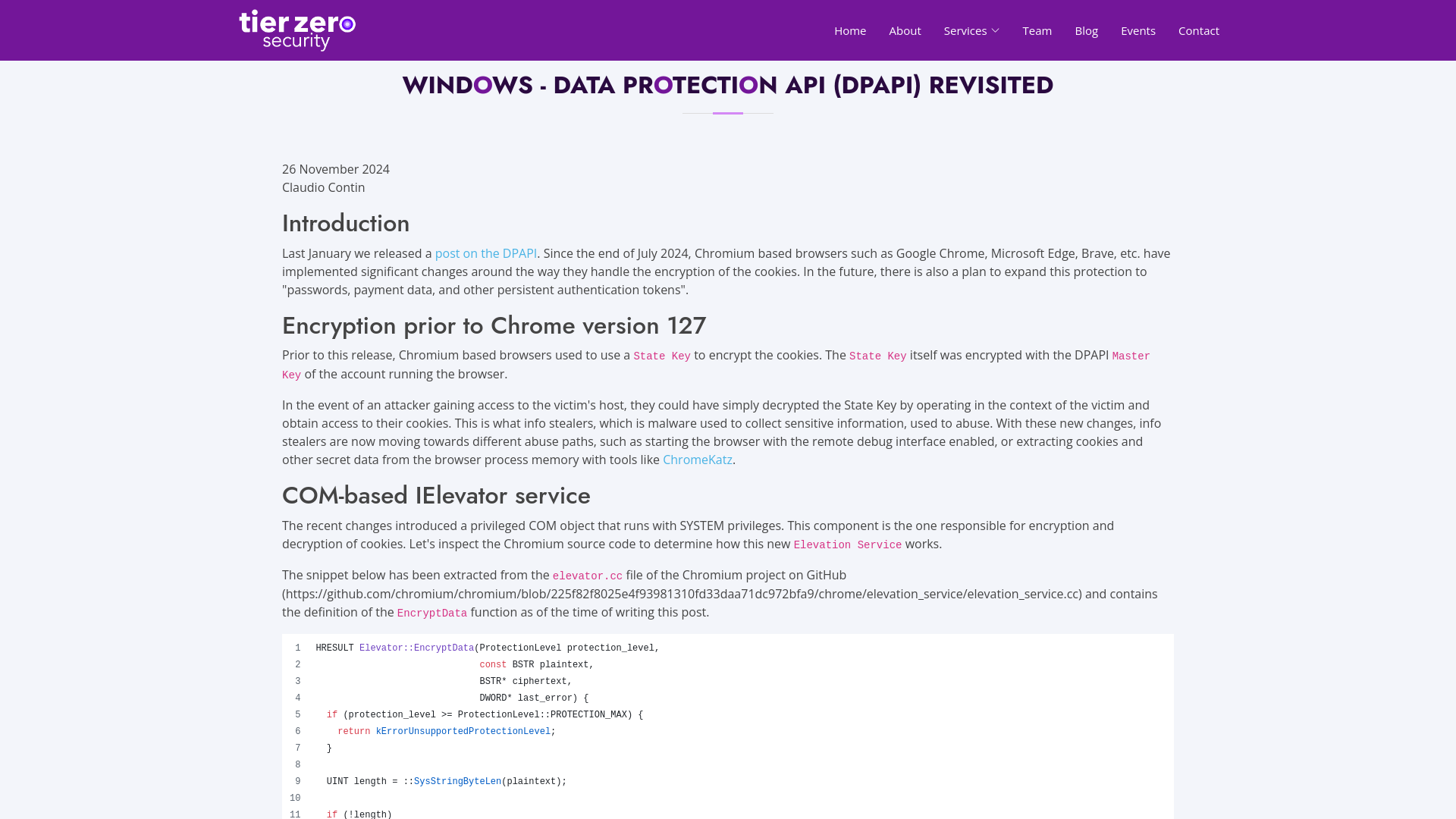
Russian Cyberspies Hacked Building Across Street From Target for Wi-Fi Attack - SecurityWeek
https://www.securityweek.com/russian-cyberspies-hacked-building-across-street-from-target-for-wi-fi-attack/
Researchers Uncover Malware Using BYOVD to Bypass Antivirus Protections
https://thehackernews.com/2024/11/researchers-uncover-malware-using-byovd.html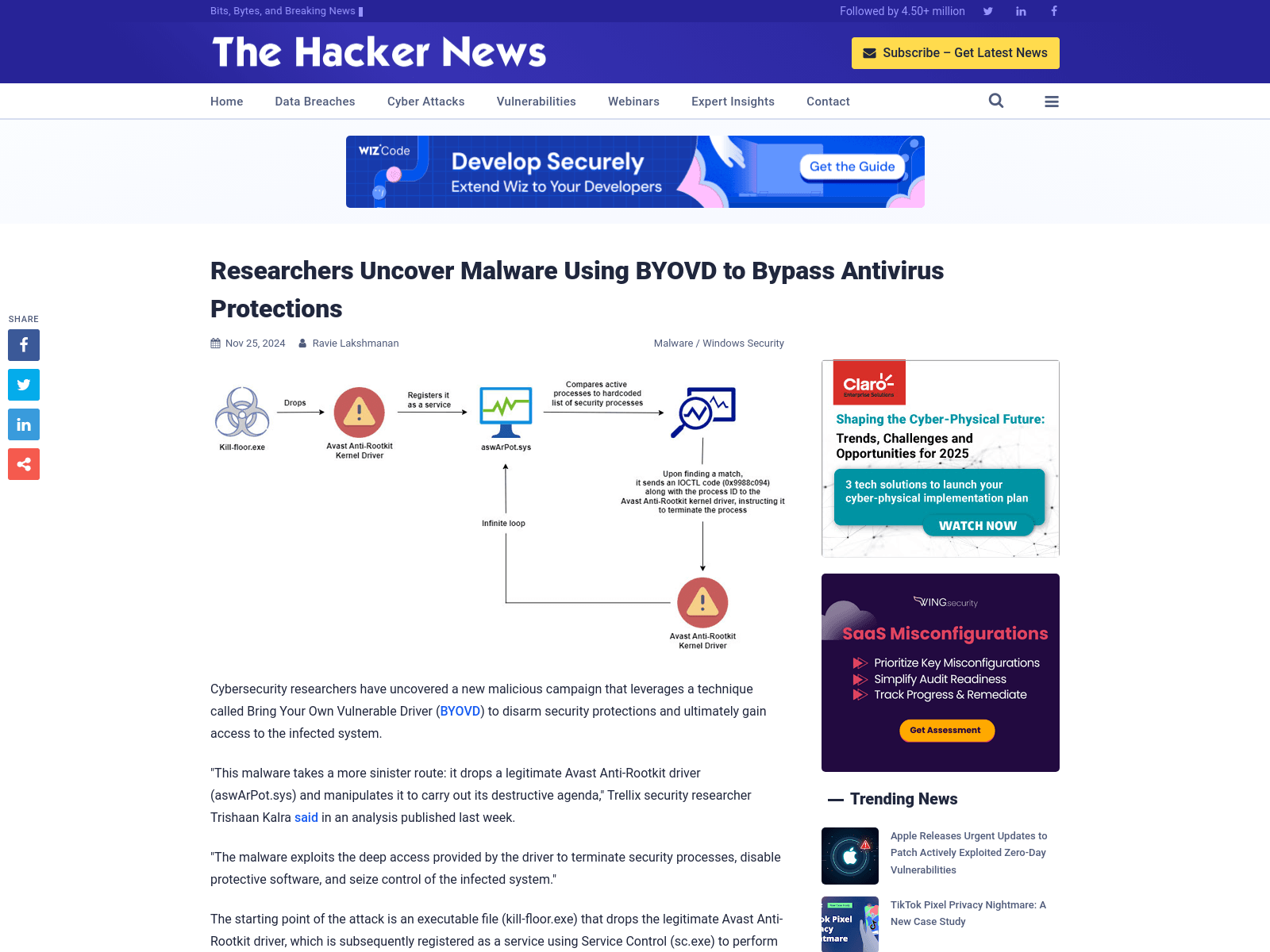
ShadowHound: A SharpHound Alternative Using Native PowerShell – Security Friends' Research Blog
https://blog.fndsec.net/2024/11/25/shadowhound/