GitHub - nevesnunes/z80-sans: OpenType font that disassembles Z80 instructions
https://github.com/nevesnunes/z80-sans
US says Chinese hackers breached multiple telecom providers
https://www.bleepingcomputer.com/news/security/us-says-chinese-hackers-breached-multiple-telecom-providers/
Redline, Meta infostealer malware operations seized by police
https://www.bleepingcomputer.com/news/legal/redline-meta-infostealer-malware-operations-seized-by-police/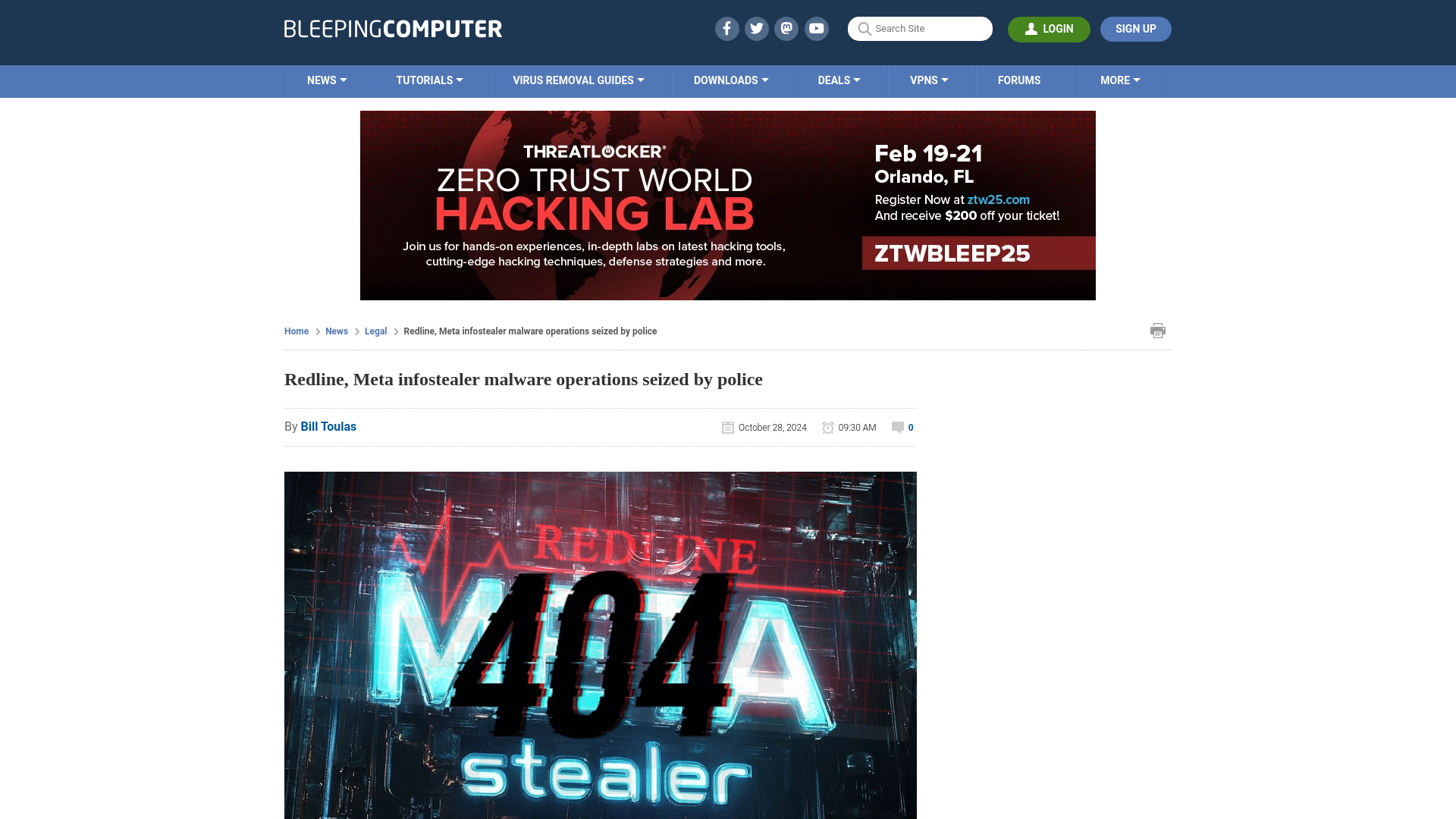
Inside the Open Directory of the “You Dun” Threat Group – The DFIR Report
https://thedfirreport.com/2024/10/28/inside-the-open-directory-of-the-you-dun-threat-group/
GitHub - xaitax/Chrome-App-Bound-Encryption-Decryption: Tool to decrypt App-Bound encrypted keys in Chrome 127+, using the IElevator COM interface with path validation and encryption protections.
https://github.com/xaitax/Chrome-App-Bound-Encryption-Decryption
New tool bypasses Google Chrome’s new cookie encryption system
https://www.bleepingcomputer.com/news/security/new-tool-bypasses-google-chromes-new-cookie-encryption-system/
Anatomy of an LLM RCE
https://www.cyberark.com/resources/threat-research-blog/anatomy-of-an-llm-rce
Europol warns about counterfeit goods and the criminals behind them | Malwarebytes
https://www.malwarebytes.com/blog/news/2024/10/europol-warns-about-counterfeit-goods-and-the-criminals-behind-them
Fog ransomware targets SonicWall VPNs to breach corporate networks
https://www.bleepingcomputer.com/news/security/fog-ransomware-targets-sonicwall-vpns-to-breach-corporate-networks/
BeaverTail Malware Resurfaces in Malicious npm Packages Targeting Developers
https://thehackernews.com/2024/10/beavertail-malware-resurfaces-in.html
Russian Espionage Group Targets Ukrainian Military with Malware via Telegram
https://thehackernews.com/2024/10/russian-espionage-group-targets.html
How I Accessed Microsoft’s ServiceNow — Exposing ALL Microsoft Employee emails, Chat Support Transcripts & Attachments | by Moblig | Oct, 2024 | Medium
https://medium.com/@moblig/how-i-accessed-microsofts-servicenow-exposing-all-microsoft-employee-emails-chat-support-5f8d535eb63b
Black Basta affiliates used Microsoft Teams in recent attacks
https://securityaffairs.com/170311/cyber-crime/black-basta-ransomware-microsoft-teams.html
Free, France’s second largest ISP, confirms data breach after leak
https://www.bleepingcomputer.com/news/security/free-frances-second-largest-isp-confirms-data-breach-after-leak/
Zero Day Initiative — Unpatched Powerful SSRF in Exchange OWA – Getting Response Through Attachments
https://www.thezdi.com/blog/2023/11/1/unpatched-powerful-ssrf-in-exchange-owa-getting-response-through-attachments
Chinese Hackers Use CloudScout Toolset to Steal Session Cookies from Cloud Services
https://thehackernews.com/2024/10/chinese-hackers-use-cloudscout-toolset.html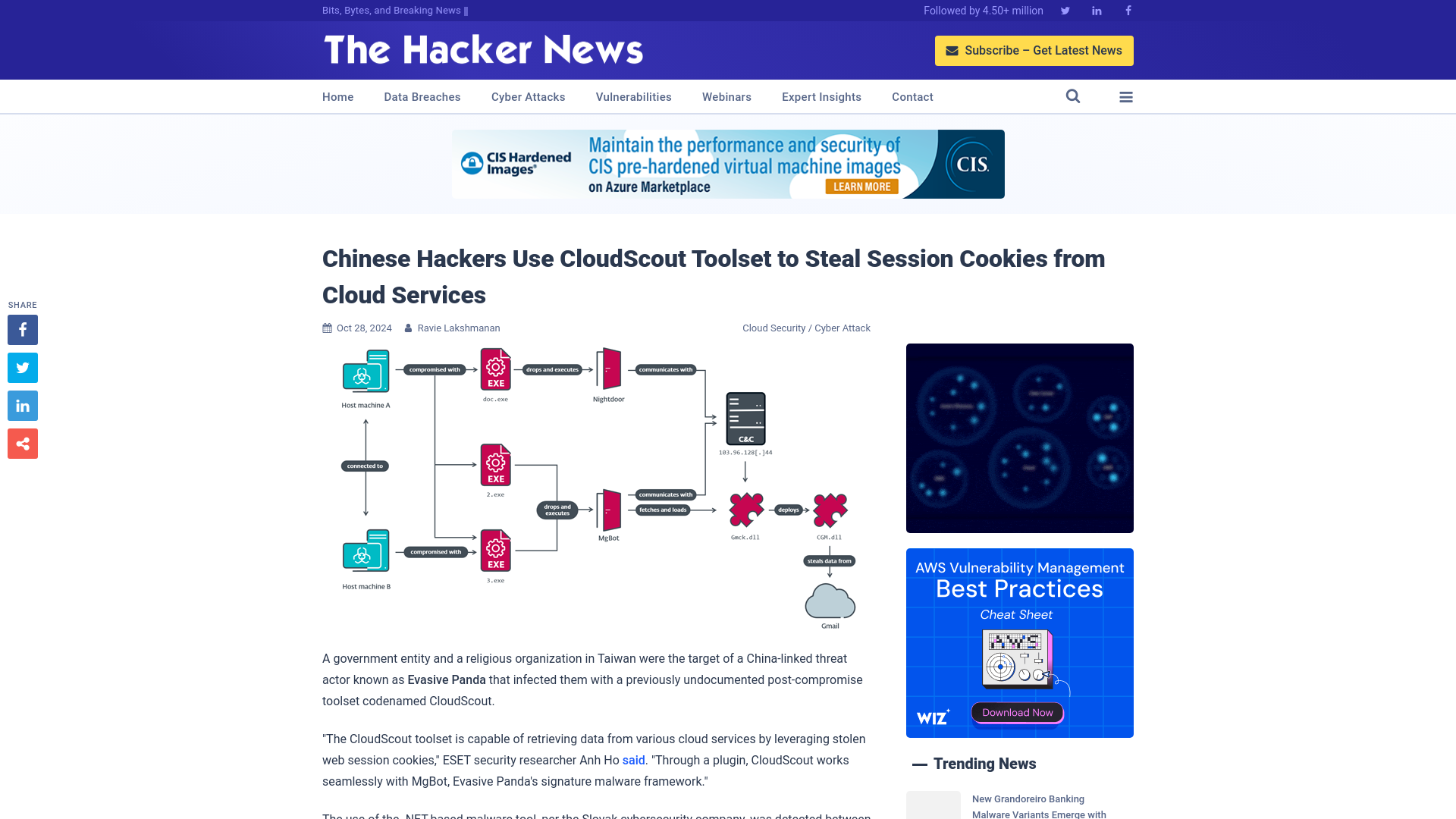
Researchers Uncover OS Downgrade Vulnerability Targeting Microsoft Windows Kernel
https://thehackernews.com/2024/10/researchers-uncover-os-downgrade.html
VMWare vCenter Server CVE-2024-38812 DCERPC Vulnerability | SonicWall
https://blog.sonicwall.com/en-us/2024/10/vmware-vcenter-server-cve-2024-38812-dcerpc-vulnerability/
A crime ring compromised Italian state databases reselling stolen info
https://securityaffairs.com/170328/data-breach/a-crime-ring-compromised-italian-state-databases.html
Recon Royale - Hacker's Arena
http://recon-royale.com
Cybercriminals Use Webflow to Deceive Users into Sharing Sensitive Login Credentials
https://thehackernews.com/2024/10/cybercriminals-use-webflow-to-deceive.html