Bypass Windows 10 User Group Policy (and more) with this One Weird Trick | by David Wells | Tenable TechBlog | Medium
https://medium.com/tenable-techblog/bypass-windows-10-user-group-policy-and-more-with-this-one-weird-trick-552d4bc5cc1b
Insecure software makers are the real cyber villains – CISA • The Register
https://www.theregister.com/2024/09/20/cisa_sloppy_vendors_cybercrime_villains/
Extending Ghidra Part 1: Setting up a Development Environment
https://voidstarsec.com/blog/ghidra-dev-environment
Microsoft ends development of Windows Server Update Services (WSUS)
https://www.bleepingcomputer.com/news/microsoft/microsoft-officially-deprecates-windows-server-update-services-wsus/
记录一次ida使用 ——— Zimbra CVE-2024-45519-知识星球
https://t.zsxq.com/xIYOU
Zimbra Releases/10.1.1 - Zimbra :: Tech Center
https://wiki.zimbra.com/wiki/Zimbra_Releases/10.1.1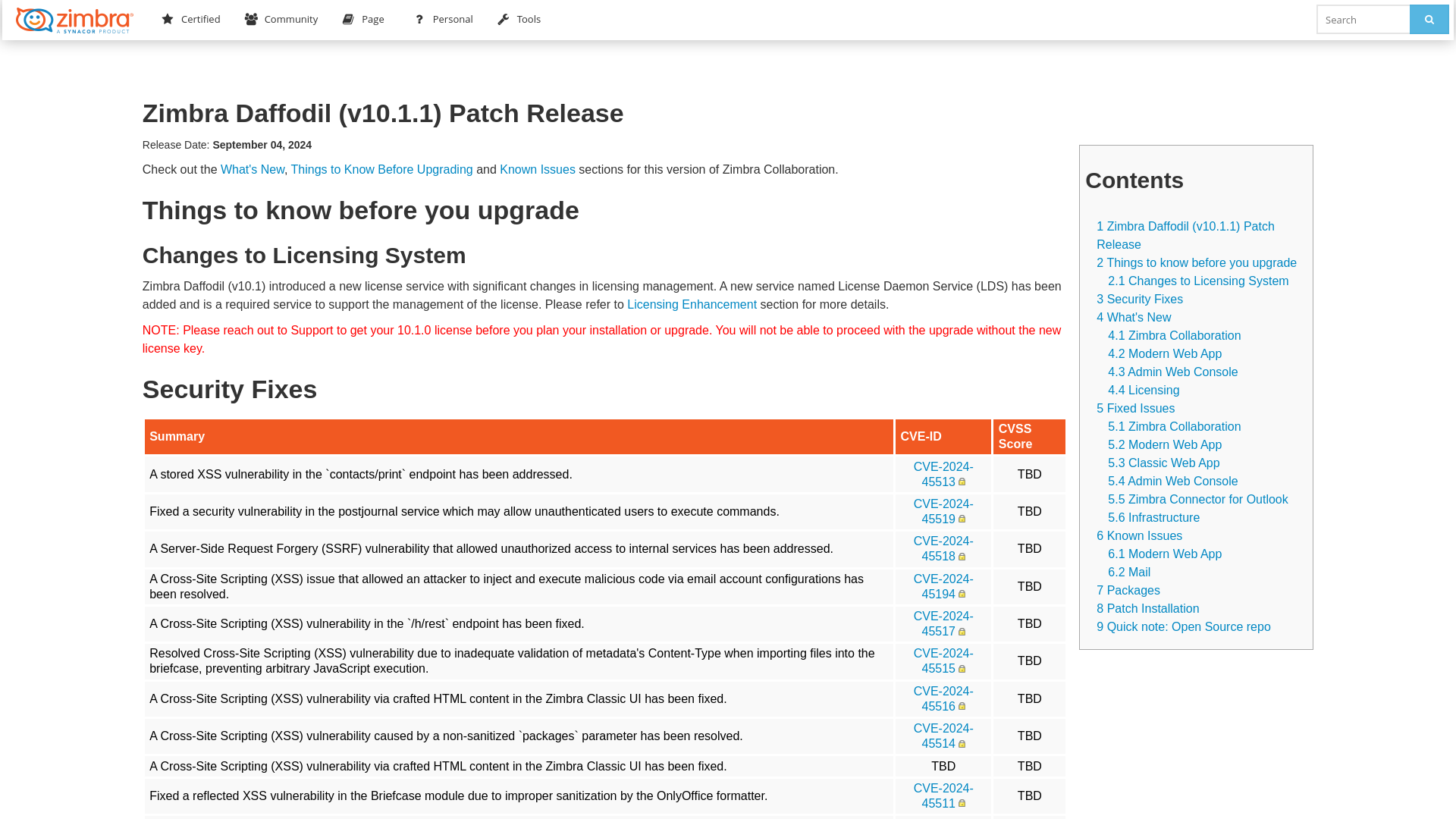
Log in to X / X
https://twitter.com/yukifartlek
Ukraine bans Telegram for government agencies, military, and critical infrastructure
https://securityaffairs.com/168674/cyber-warfare-2/ukraine-nccc-banned-telegram-military-government.html
Ukraine bans Telegram on military, govt devices over security risks
https://www.bleepingcomputer.com/news/security/ukraine-bans-telegram-on-military-govt-devices-over-security-risks/
Heap exploitation, glibc internals and nifty tricks. - Quarkslab's blog
https://blog.quarkslab.com/heap-exploitation-glibc-internals-and-nifty-tricks.html
Intro to Embedded RE Part 1: Tools and Series Overview
https://voidstarsec.com/blog/intro-to-embedded-part-1
OP KAERB: Europol dismantled phishing scheme targeting mobile users
https://securityaffairs.com/168692/cyber-crime/op-kaerb-europol-dismantled-phishing-scheme.html
Hacktivist Group Twelve Targets Russian Entities with Destructive Cyber Attacks
https://thehackernews.com/2024/09/hacktivist-group-twelve-targets-russian.html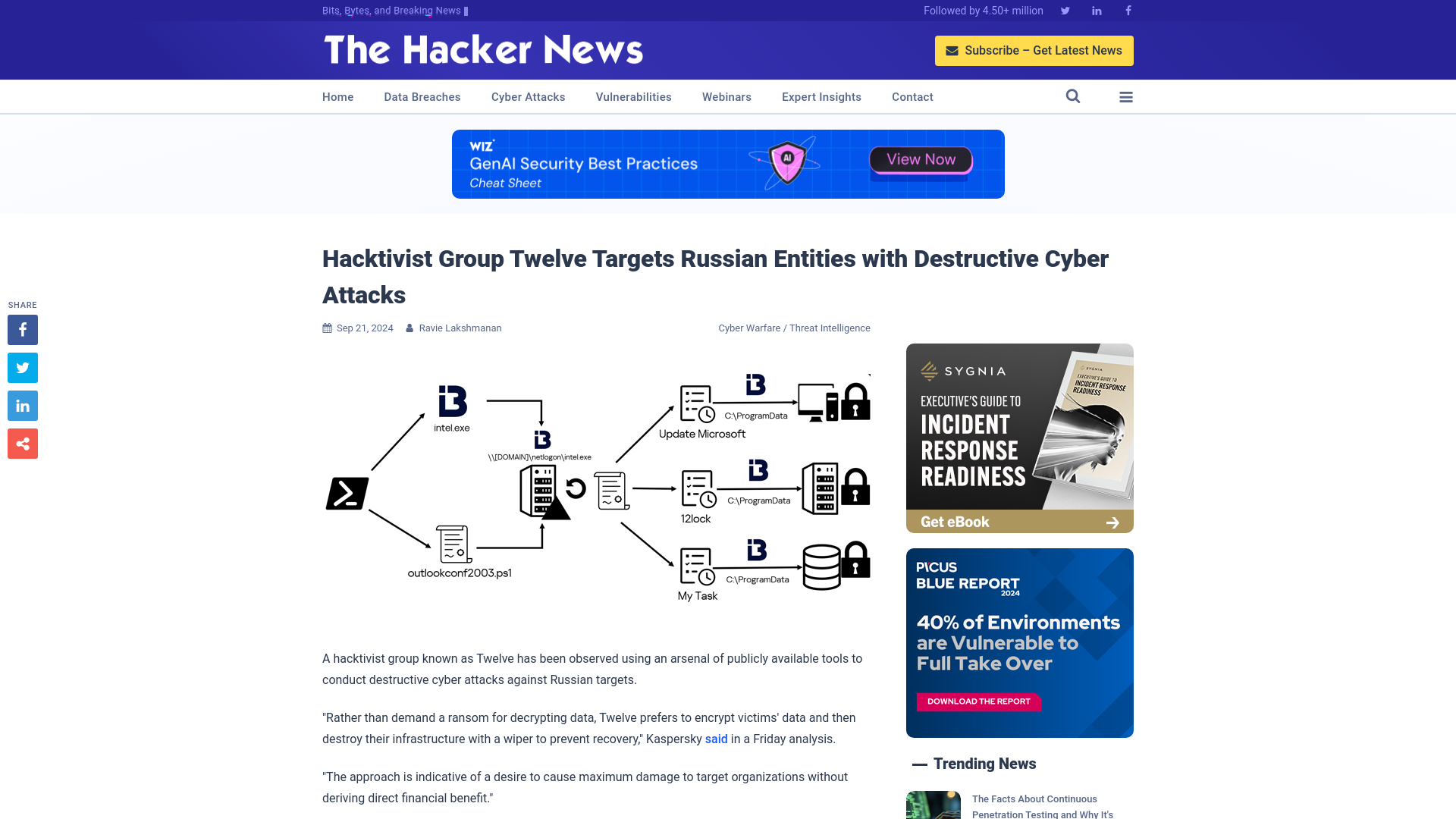
Hackers stole over $44 million from Asian crypto platform BingX
https://securityaffairs.com/168703/cyber-crime/hackers-stole-44m-from-bingx.html
LinkedIn Halts AI Data Processing in UK Amid Privacy Concerns Raised by ICO
https://thehackernews.com/2024/09/linkedin-halts-ai-data-processing-in-uk.html