The unreasonable success of Fuzzing - Google スライド
https://docs.google.com/presentation/d/1vw9lywrMnNojiOIu-xU5KXZz7WzE0MYNQF6V7n6vyY8/edit?usp=drivesdk
Announcing the 11th Annual Flare-On Challenge | Google Cloud Blog
https://cloud.google.com/blog/topics/threat-intelligence/announcing-eleventh-annual-flare-on-challenge
APT_REPORT/International Strategic/Russia/Disjointed_Cyber_Warfare_Internal_Conflicts_among_.pdf at master · blackorbird/APT_REPORT · GitHub
https://github.com/blackorbird/APT_REPORT/blob/master/International%20Strategic/Russia/Disjointed_Cyber_Warfare_Internal_Conflicts_among_.pdf
FuzzingFromFirstPrinciples.pdf
https://zerodayengineering.com/research/slides/FuzzingFromFirstPrinciples.pdf
Exploit code released for critical Ivanti RCE flaw, patch now
https://www.bleepingcomputer.com/news/security/exploit-code-released-for-critical-ivanti-rce-flaw-patch-now/
Post-CrowdStrike Fallout: Microsoft Redesigning EDR Vendor Access to Windows Kernel - SecurityWeek
https://www.securityweek.com/post-crowdstrike-fallout-microsoft-redesigning-edr-vendor-access-to-windows-kernel/
Malware Reports - Online Malware Analysis Sandbox
http://app.any.run/submissions/#tag:povertystealer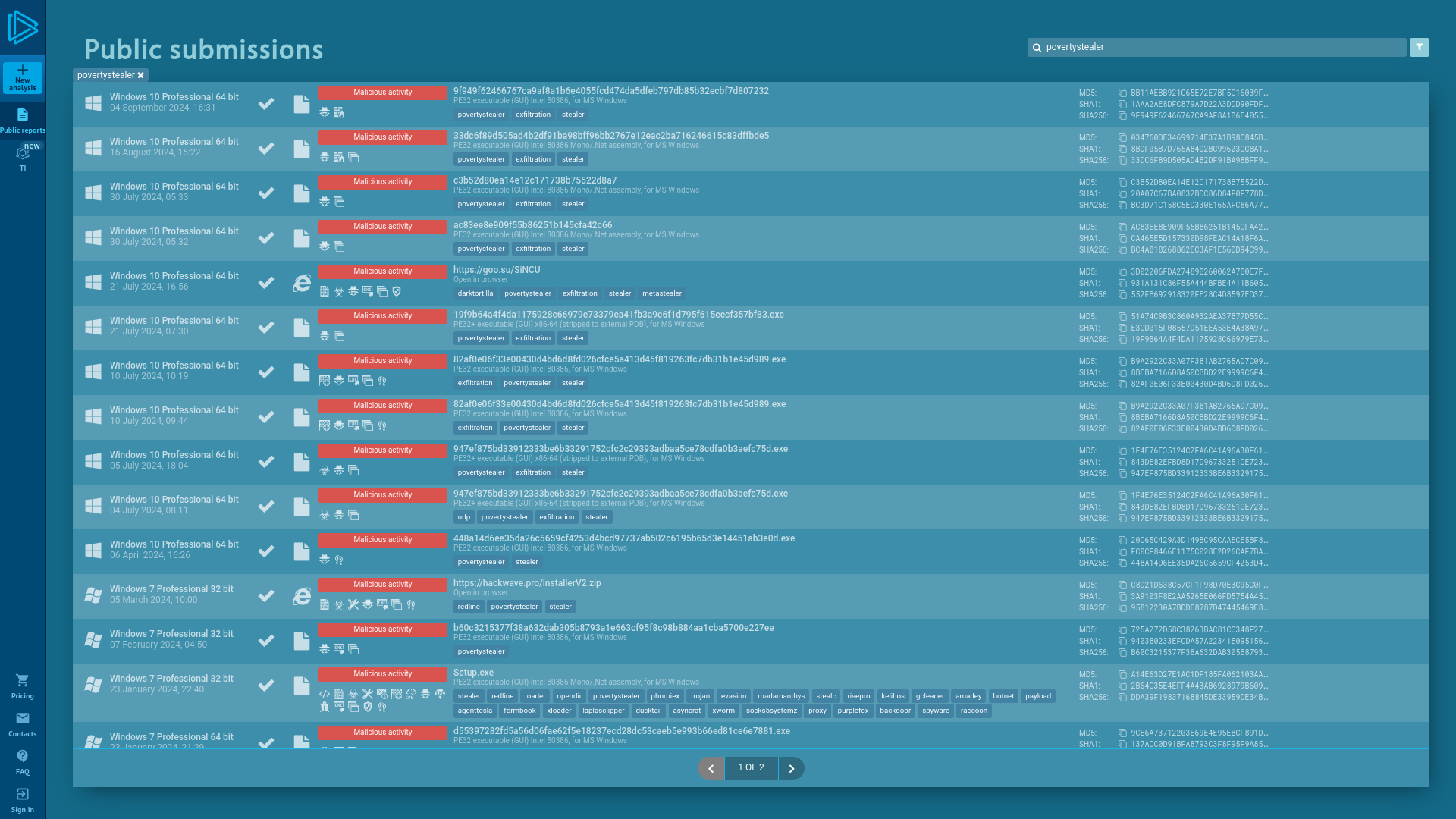
./RE — Shell Shocked: The Oyster Backdoor Update
https://binhex.ninja/re-malware-analysis-blog/shell-shocked-the-oyster-backdoor-update
US cracks down on spyware vendor Intellexa with more sanctions
https://www.bleepingcomputer.com/news/security/us-cracks-down-on-spyware-vendor-intellexa-with-more-sanctions/
Malware Development : Part-2. “Infected Innovation: The Malware… | by RED TEAM | Medium
https://sid4hack.medium.com/malware-development-part-2-459109c50126
Malware Development : Part 1. Where do I start, and what are all the… | by RED TEAM | Medium
https://sid4hack.medium.com/malware-development-part-1-ea9e26088662
US Sanctions Intellexa Executives as Surveillance Spyware Crackdown Expands - SecurityWeek
https://www.securityweek.com/us-sanctions-intellexa-executives-as-surveillance-spyware-crackdown-expands/
Recently patched Windows flaw CVE-2024-43461 was actively exploited as a zero-day before July 2024
https://securityaffairs.com/168467/hacking/windows-cve-2024-43461-actively-exploited-before-july-2024.html
D-Link fixes critical RCE, hardcoded password flaws in WiFi 6 routers
https://www.bleepingcomputer.com/news/security/d-link-fixes-critical-rce-hardcoded-password-flaws-in-wifi-6-routers/
Exploiting Microsoft Kernel Applocker Driver (CVE-2024-38041)
https://csa.limited/blog/20240916-Exploiting-Microsoft-Kernel-Applocker-Driver.html
About the security content of macOS Sequoia 15 - Apple Support
https://support.apple.com/en-us/121238
![Amazon.com: Hackers - Collector's Edition 4K Ultra HD + Blu-ray [4K UHD] : Jonny Lee Miller, Angelina Jolie, Fisher Stevens, Lorraine Bracco, Jesse Bradford, Iain Softley, Michael Peyser, Ralph Winter, Rafael Moreu: Movies & TV](/image/screenshot/f7196dbdb64bdafb8845d362209bc34a.png)
Microsoft Says Recent Windows Vulnerability Exploited as Zero-Day - SecurityWeek
https://www.securityweek.com/microsoft-says-recent-windows-vulnerability-exploited-as-zero-day/
Cybercriminals Exploit HTTP Headers for Credential Theft via Large-Scale Phishing Attacks
https://thehackernews.com/2024/09/cybercriminals-exploit-http-headers-for.html
Direct System Calls For Hackers (EDR Evasion) - YouTube
https://www.youtube.com/watch?v=0_CvTgvR-7M
Windows vulnerability abused braille “spaces” in zero-day attacks
https://www.bleepingcomputer.com/news/security/windows-vulnerability-abused-braille-spaces-in-zero-day-attacks/
CVE-2024-8190: Investigating CISA KEV Ivanti Cloud Service Appliance Command Injection Vulnerability – Horizon3.ai
https://www.horizon3.ai/attack-research/cisa-kev-cve-2024-8190-ivanti-csa-command-injection/
Google Fixes GCP Composer Flaw That Could've Led to Remote Code Execution
https://thehackernews.com/2024/09/google-fixes-gcp-composer-flaw-that.html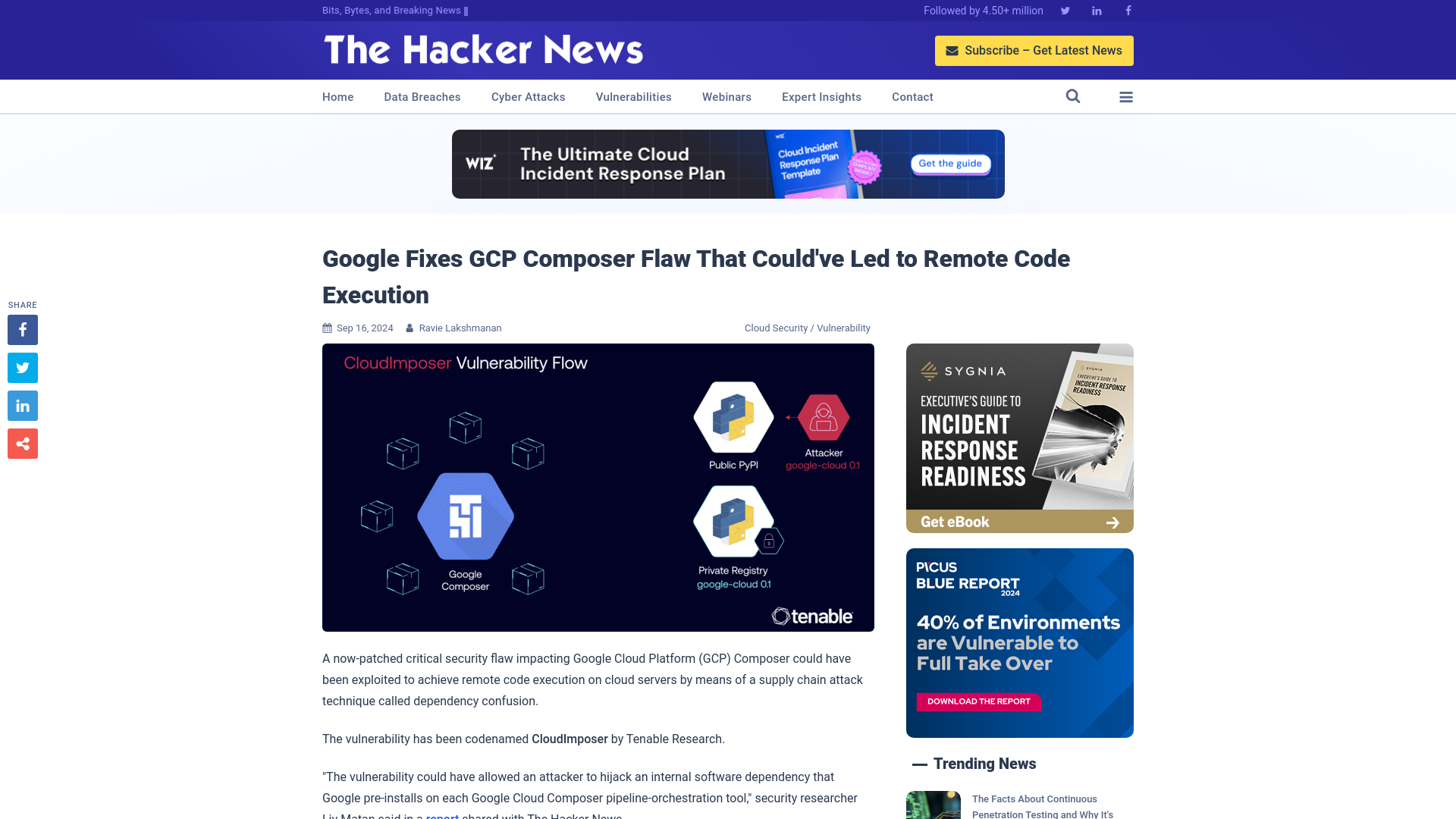
Microsoft confirms second 0-day exploited by Void Banshee APT (CVE-2024-43461) - Help Net Security
https://www.helpnetsecurity.com/2024/09/16/cve-2024-43461-exploited/
Apple Patches Major Security Flaws with iOS 18 Refresh - SecurityWeek
https://www.securityweek.com/apple-patches-major-security-flaws-with-ios-18-refresh/
OALabsLive - Twitch
https://www.twitch.tv/oalabslive
Decrypting and Replaying VPN Cookies | by James H | Sep, 2024 | Medium
https://rotarydrone.medium.com/decrypting-and-replaying-vpn-cookies-4a1d8fc7773e
SolarWinds fixed critical RCE CVE-2024-28991 in Access Rights Manager
https://securityaffairs.com/168456/security/solarwinds-fixed-rce-cve-2024-28991.html
Leak.sx | leaked accounts
https://leak.sx
GitHub - watchtowrlabs/CVE-2024-40711: Pre-Auth Exploit for CVE-2024-40711
https://github.com/watchtowrlabs/CVE-2024-40711
SolarWinds Patches Critical Vulnerability in Access Rights Manager - SecurityWeek
https://www.securityweek.com/solarwinds-patches-critical-vulnerability-in-access-rights-manager/
Data Stolen in Ransomware Attack That Hit Seattle Airport - SecurityWeek
https://www.securityweek.com/data-stolen-in-ransomware-attack-that-hit-seattle-airport/
Apple Drops Spyware Case Against NSO Group, Citing Risk of Threat Intelligence Exposure
https://thehackernews.com/2024/09/apple-drops-spyware-case-against-nso.html
New Zero-Day Emerges After Microsoft Patch Tuesday: CVE-2024-43461 Targets Windows MSHTML
https://securityonline.info/new-zero-day-emerges-after-microsoft-patch-tuesday-cve-2024-43461-targets-windows-mshtml/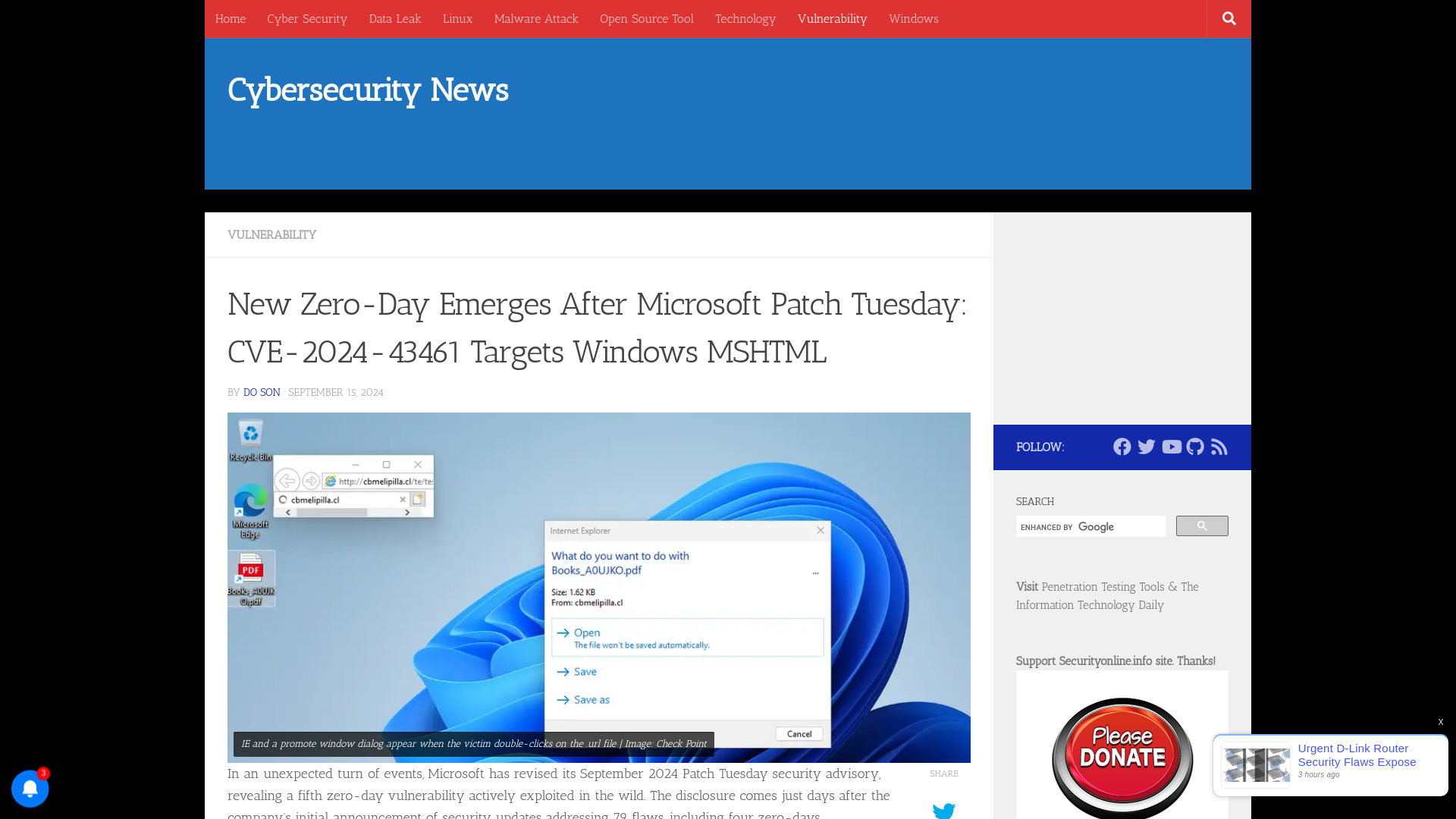
Intelligence X
https://intelx.io
Ivanti CSA Vulnerability Exploited in Attacks Days After DIsclosure - SecurityWeek
https://www.securityweek.com/ivanti-csa-vulnerability-exploited-in-attacks-days-after-disclosure/
CISA warns of Windows flaw used in infostealer malware attacks
https://www.bleepingcomputer.com/news/security/cisa-warns-of-windows-flaw-used-in-infostealer-malware-attacks/
Releases · hasherezade/pe-bear
https://github.com/hasherezade/pe-bear/releases
Chrome switching to NIST-approved ML-KEM quantum encryption
https://www.bleepingcomputer.com/news/security/chrome-switching-to-nist-approved-ml-kem-quantum-encryption/
Managing PE Files With Overlays - SANS Internet Storm Center
https://isc.sans.edu/diary/31268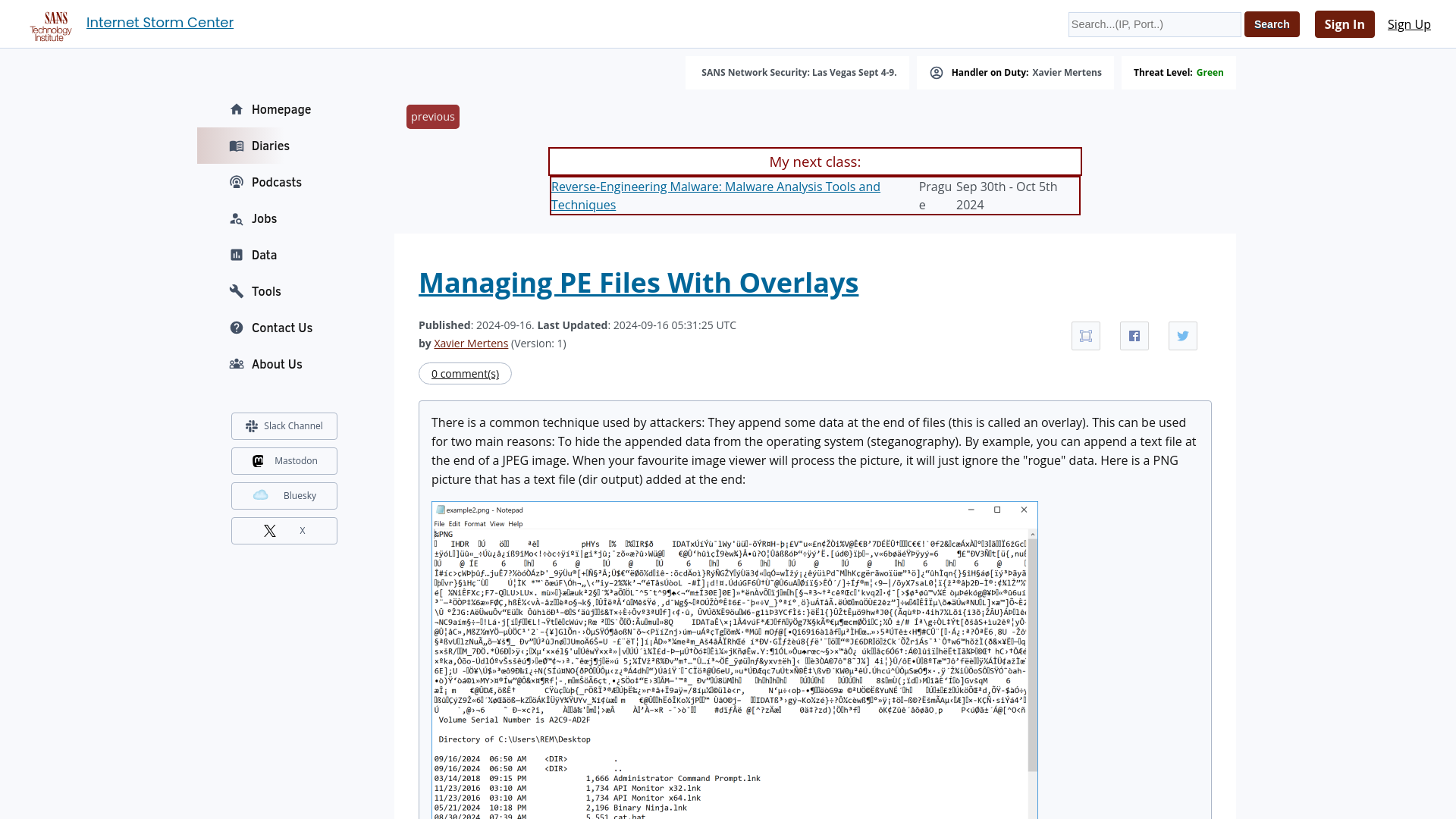
[Cracking Windows Kernel with HEVD] Chapter 0: Where do I start?
https://mdanilor.github.io/posts/hevd-0/![[Cracking Windows Kernel with HEVD] Chapter 0: Where do I start?](/image/screenshot/33b8b0f2b5b6444ed4feac257967bd94.png)